Cyber Intelligence Certificate
Here are some of the images for Cyber Intelligence Certificate that we found in our website database.

Cyber Threat Intelligence Certificate Credly

Cyber Intelligence Graduate Certificate (Online) JMU
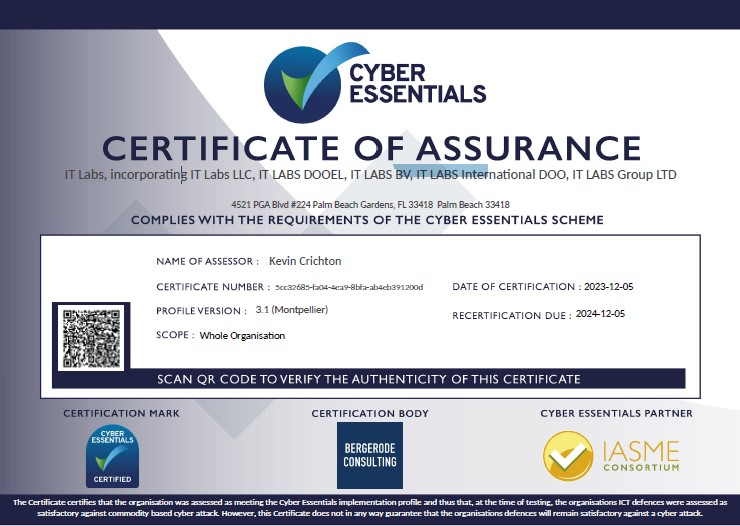
Cyber Essentials Certificate IT Labs

iSchool Launches the Cyber Intelligence Certificate Program News Events

Certificate in Cyber Threat Intelligence

James Madison University Online on LinkedIn: Cyber Intelligence

Certificate Threat Intelligence anjuparapat Cyber Academy Indonesia

Learn to analyze intelligence and spot trends Expand your career

Certificate in Cybersecurity Threat Intelligence

Certificate IV in Information Technology Cyber Security Artificial

Cyber Essentials Certificate Universal Fabrications (Coventry) Ltd
Certificate in Cybersecurity Master Network Security Threat Management
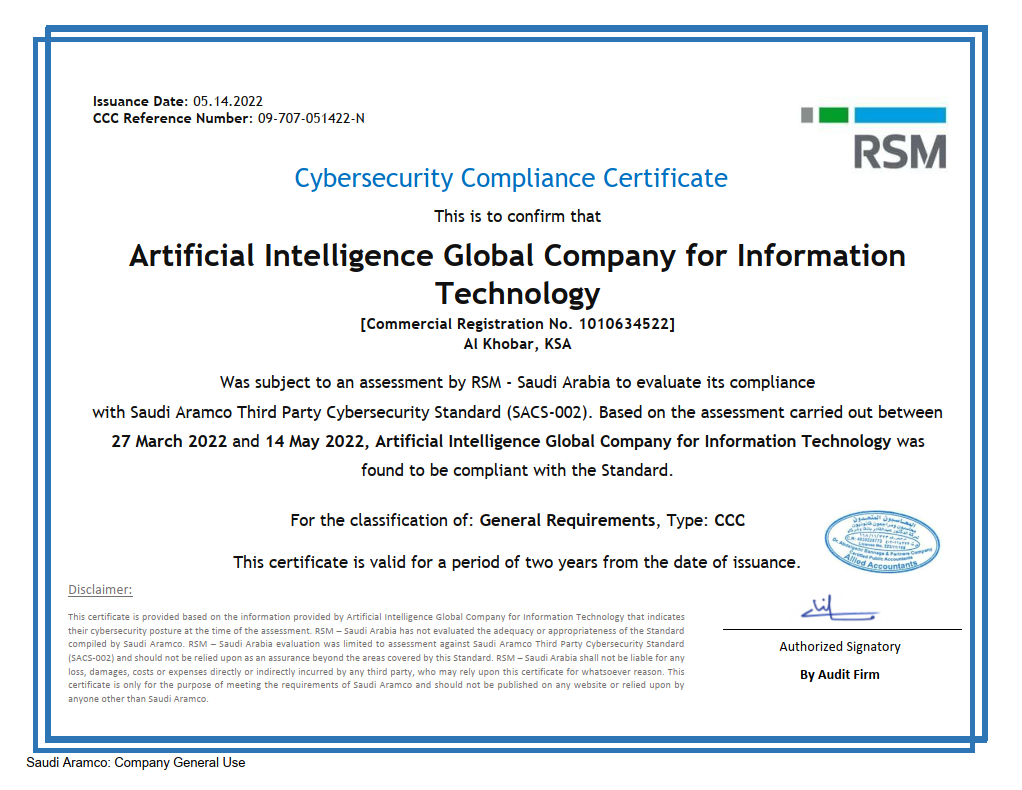
AIGC obtains the Cyber Security Compliance Certificate Artificial

AIGC obtains the Cyber Security Compliance Certificate Artificial

Completion certificate for Cybersecurity and Ethical Hacking E Degree

Cyber Essentials Certification Renewal EPiC

Charles Bishop Jr Cyber Operations: Cyber Law and Policy Emphasis

Completion certificate for Cybersecurity and Ethical Hacking E Degree

Graduate Programs in Science and Technology JMU

Narasinha Dutt College

Complete this entire course to earn a CompTIA PenTest Certification