Cyber Resilience Certification
Here are some of the images for Cyber Resilience Certification that we found in our website database.

teiss Insider Threat Internal threats: the importance of culture to

Helping to shape the RMIT Centre for Cyber Security Research and

7000x8000 Resolution Cybersecurity Core 7000x8000 Resolution Wallpaper

Plus de 10 000 images de Cyber Security Beginner To Advance et de Cyber

Cyber security technology concept in the shape of sphere with hexagon

Cyber Threats

Cyber Range Innovazione laboratori Fondazione LINKS

The Complete Blockchain Developer Resource List Blockchain Council

The Evolution Of Cyber Security Threats: Understanding And Preventing
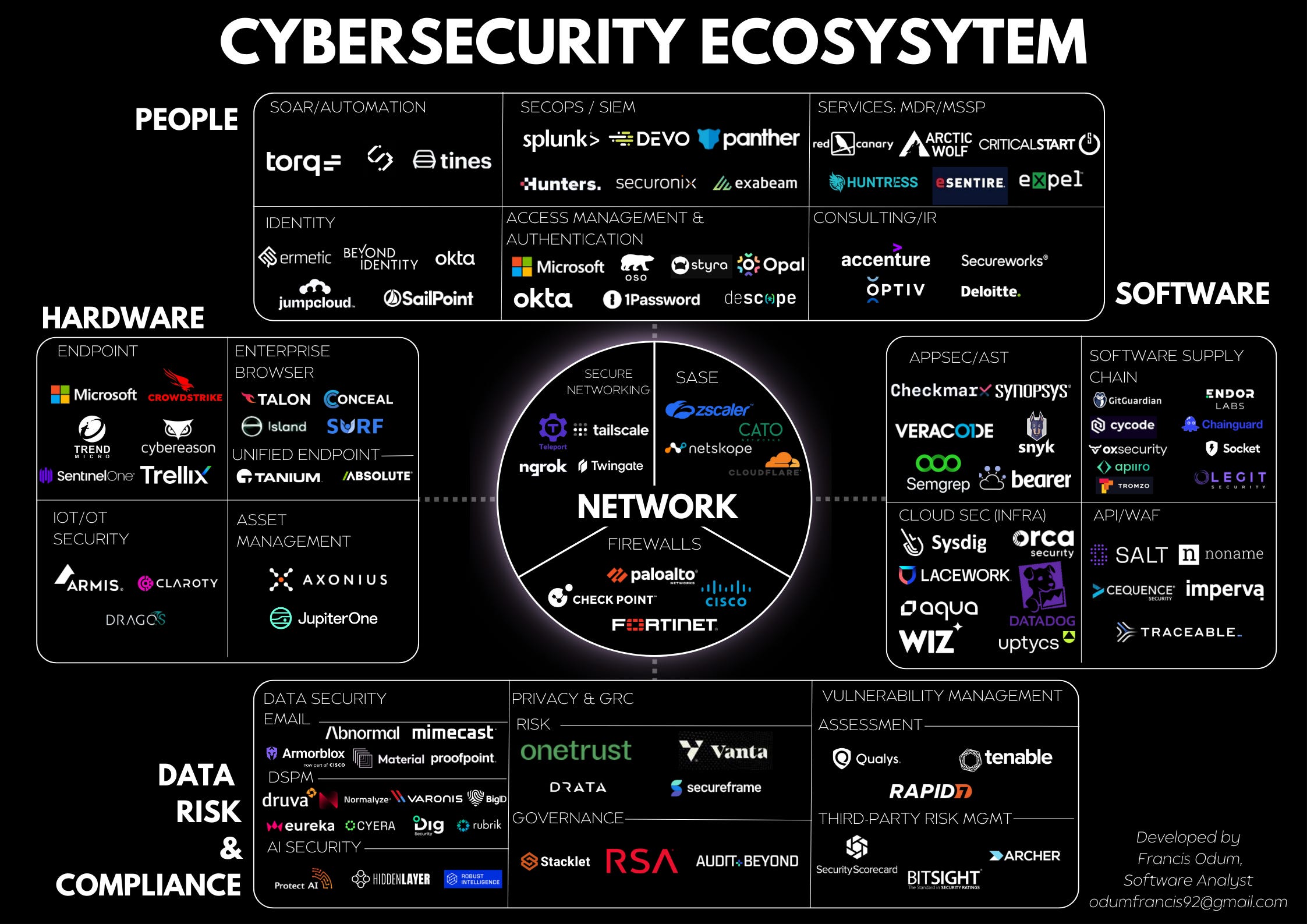
Building Regional Cyber Coalitions

What Is Cybersecurity? Forage

Plus de 1 images de Ism et de Rgpd Pixabay

7 things startups need to know about cybersecurity CIO

Cybersecurity: Thách thức an ninh mạng trong kỷ nguyên số Chuyển phát

New cybersecurity technology 2022 Security Magazine

Cybersecurity Tips for Small Businesses

K Cyber

National Cybersecurity Center aims to combat cyber threat in Nepal

What Is Ai Cybersecurity

Pin on Infographics

Understanding the 3 Phases of Cybersecurity Architecture Ardoq

As Cybercrime Keeps Upping Its Game Cybersecurity Must Answer With

Cyber Solutions Stock Photos Images and Backgrounds for Free Download

Premium Photo Cybersecurity
Research Note: CrowdStrike Falcon Privileged Access NAND Research

Cyber Security

Cyber Essentials requirements: What are the new changes? Cyber Magazine

Bolstering cybersecurity readiness in the cloud Information Age

10 Best Cybersecurity Courses Certifications (Free Paid)

The complete guide on social media marketing for cyber security

Premium Photo The Face of Cybersecurity Protecting the Digital World

Types of Cyber Security Threats NEIT

How to Find a Good Cybersecurity Service Provider

India becoming target of increased cybersecurity attack says report by

NZ businesses complacent over cyber security threats report RNZ News