Cyber Risk Register Template
Here are some of the images for Cyber Risk Register Template that we found in our website database.

Cyber

10 Ways to Improve Your Cyber Security in 2023 Nexstor

The role of AI in cyber security

What Is Cybersecurity? Forage

Helping to shape the RMIT Centre for Cyber Security Research and

What is Red Teaming Cyber Security? How Does it Work? Sapphire

The role of Artificial Intelligence in Cyber Security CIO News

Cyber Security and Segregation of Duties Security Boulevard

Is New Hampshire ready to adopt a privacy and cybersecurity law? NH

Cyber Security Analyst Responsibilities NEIT

Evolving Cyber Threat Landscape Management in 2023

Top Cyber Security Threats to Organizations CIO Insight

What Is Cybersecurity? Definition And Types of Cyber Security
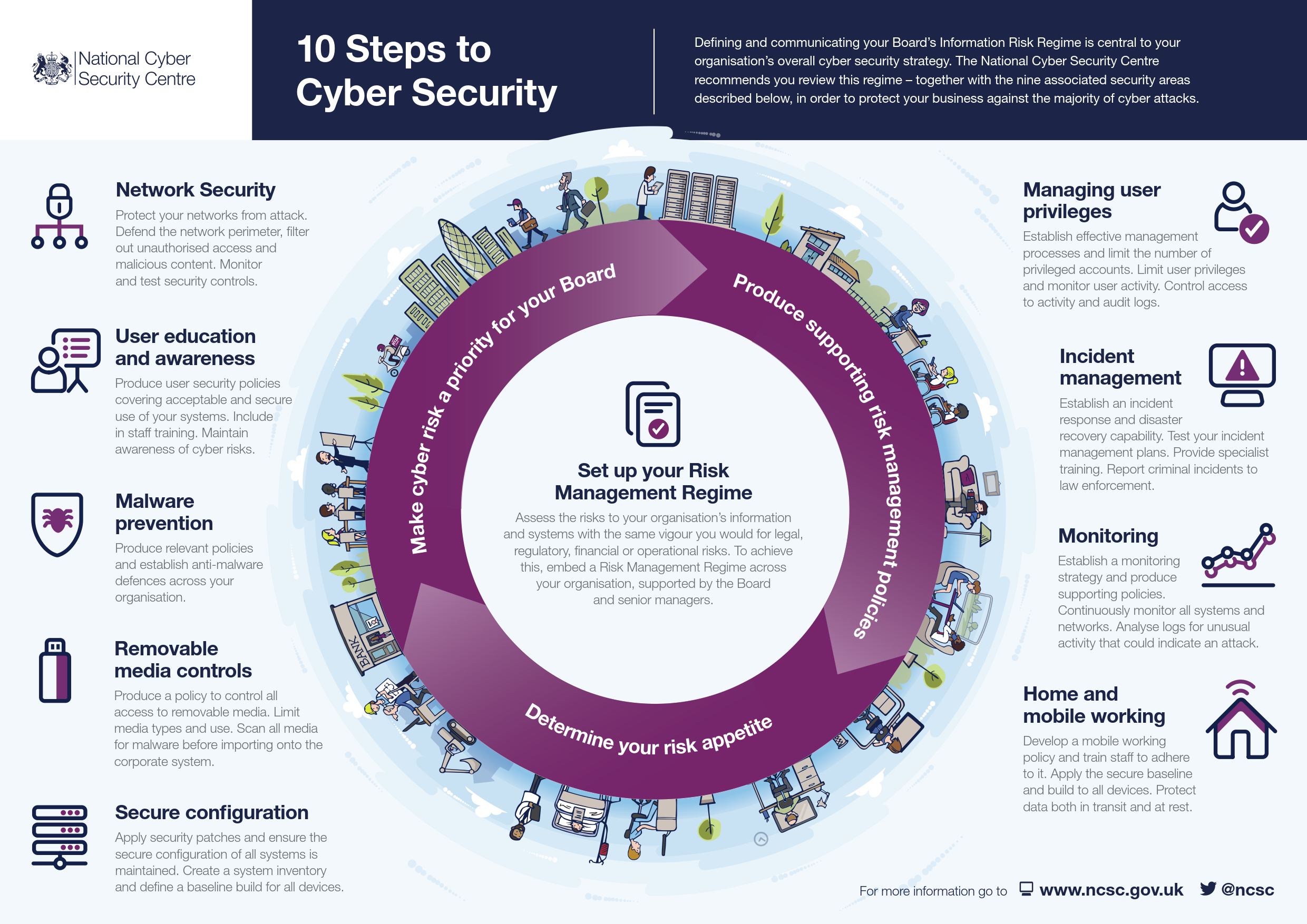
Infographic: Ten steps to cyber security SAFETY4SEA

Cyber Security: saiba o que faz um profissional de cibersegurança

Cyber Security ICA Agency Alliance Inc

New cybersecurity technology 2022 Security Magazine

Cybersecurity founded on 3 pillars: Technology process and people

3 000 Free Cybersecurity Strategy Cybersecurity Images Pixabay

Cybersecurity Plan: 3 Keys for CISOs Trend Micro (US)

How To Promote Cyber Security Awareness Our Top Tips
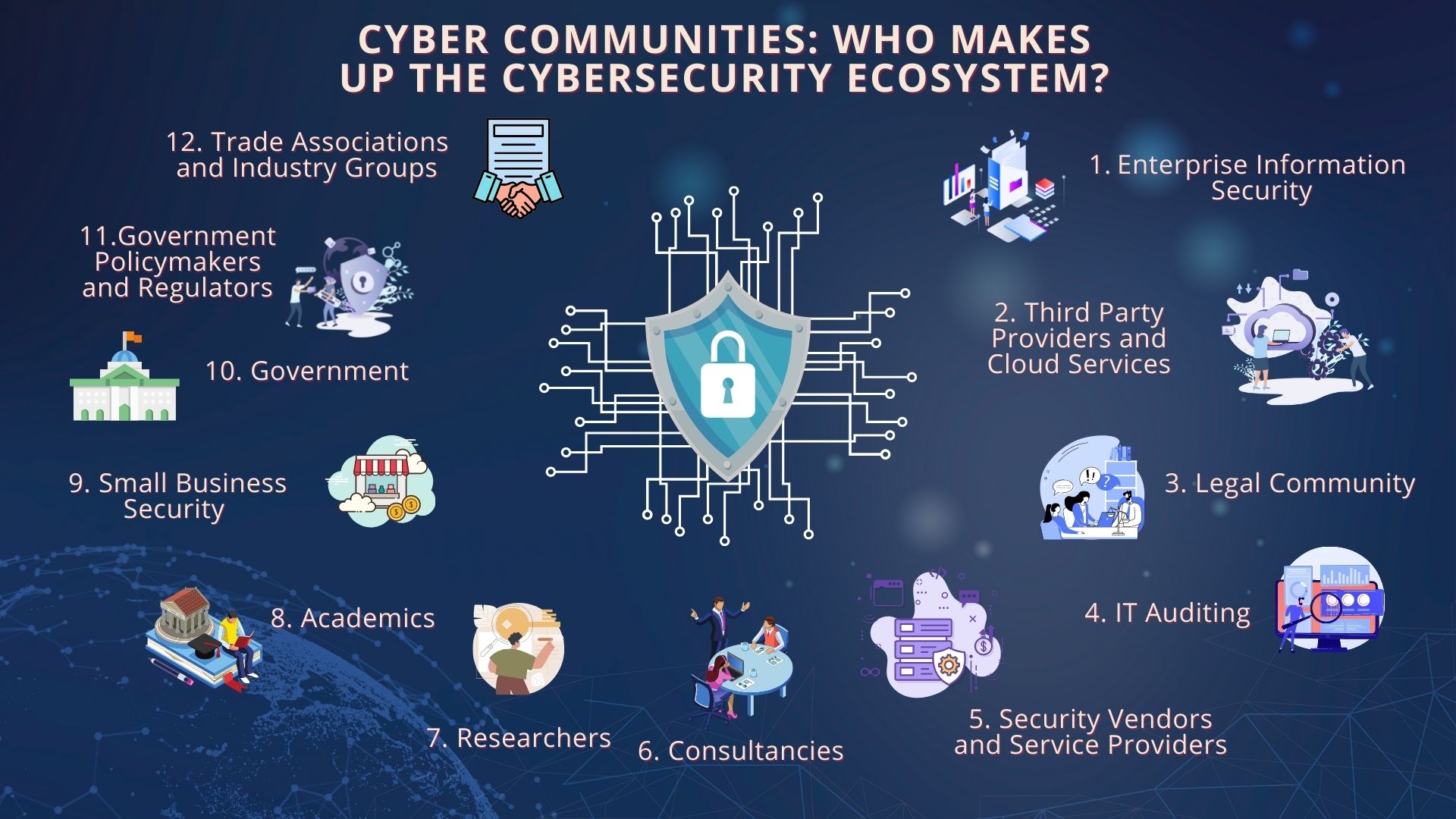
Cybersecurity Ecosystem Strategy Of Security vrogue co

The Top Five Cybersecurity Trends In 2023

Cyber Security Concept Data Protection And Secured Internet Access

Cabinet to Approve First #39 National Cyber Security Policy 2021 #39 today

What is Cyber Security? CG Technologies
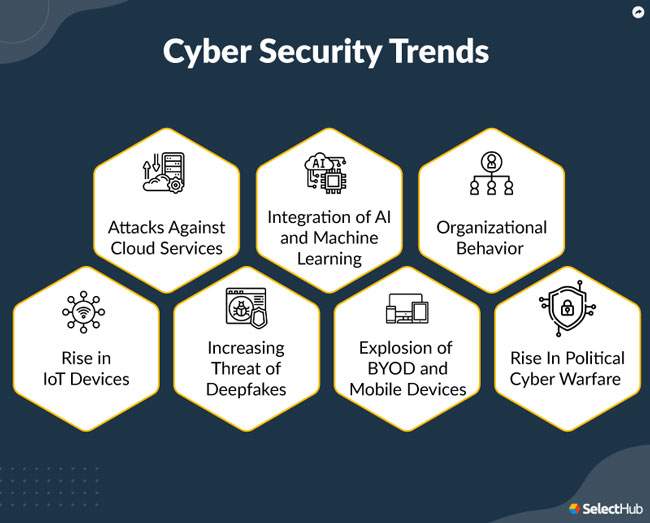
Cyber Security Trends for 2022 MOJOE

The 7 Layers of Cyber Security : Attacks on OSI model
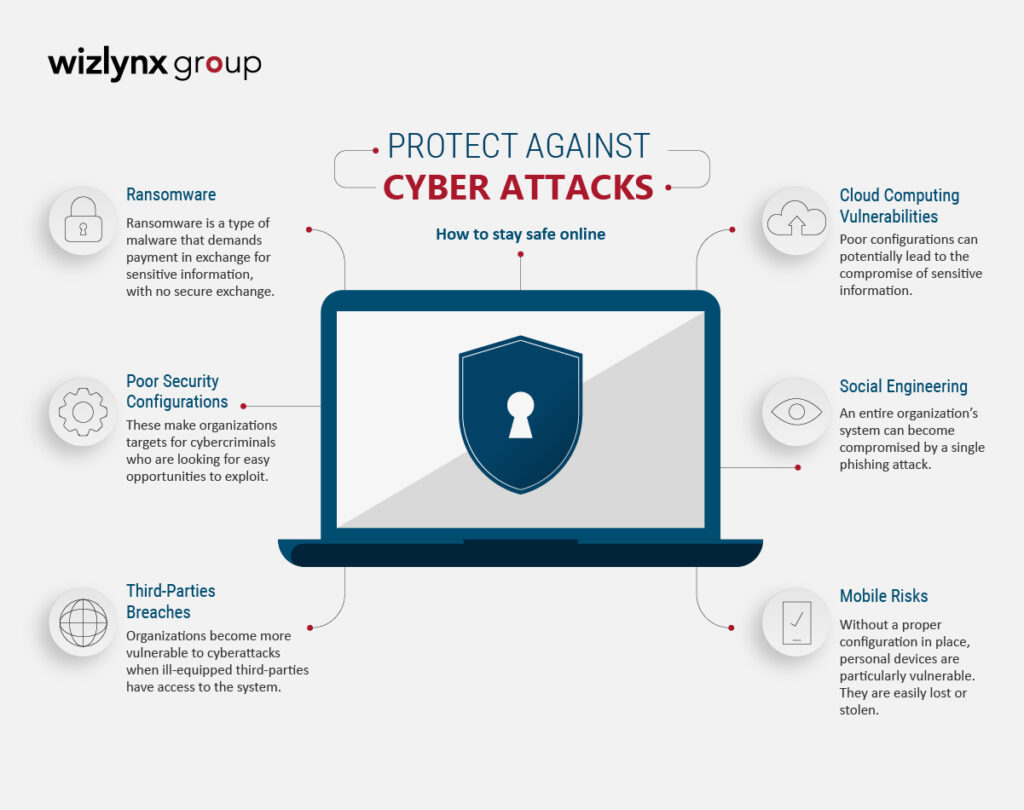
Cyber Security Threats and Solutions

6 Steps to get into Cyber Security and Information Technology YouTube

Cybersecurity Trends How To Protect Your Business • Hamilton Business
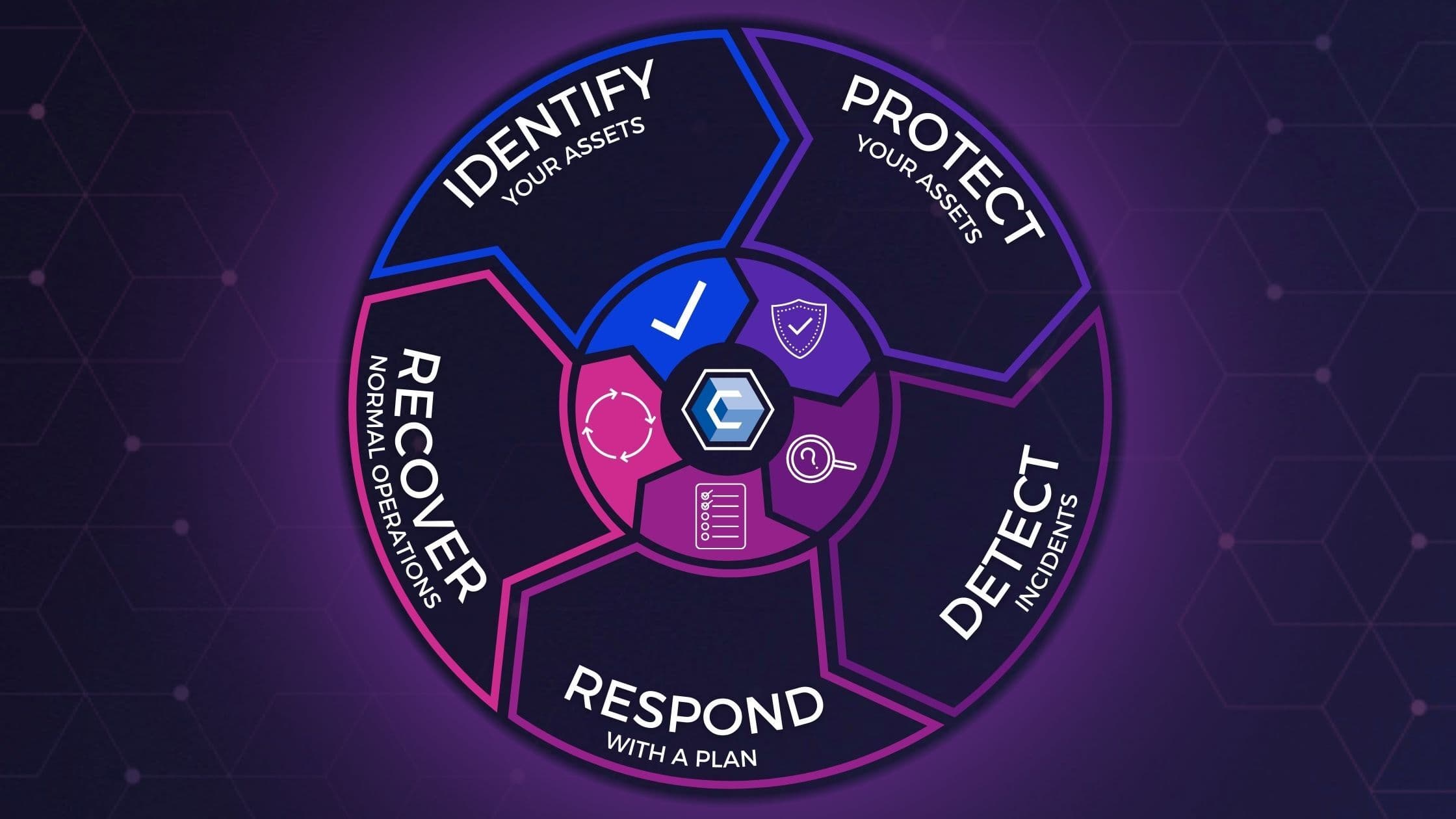
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

Cybersecurity evolution: a historical perspective The Plunge
.png)
What are the Different Types of Cyber Security?

First Use Of Data Flow Diagrams For Cybersecurity Flow Syste