Cyber Security Agreement Template
Here are some of the images for Cyber Security Agreement Template that we found in our website database.

Security Agreement Template PDF

Security Agreement Template PDF Security Interest Bankruptcy

Cyber Security Agreement PDF

Huawei Cyber Security Agreement PDF
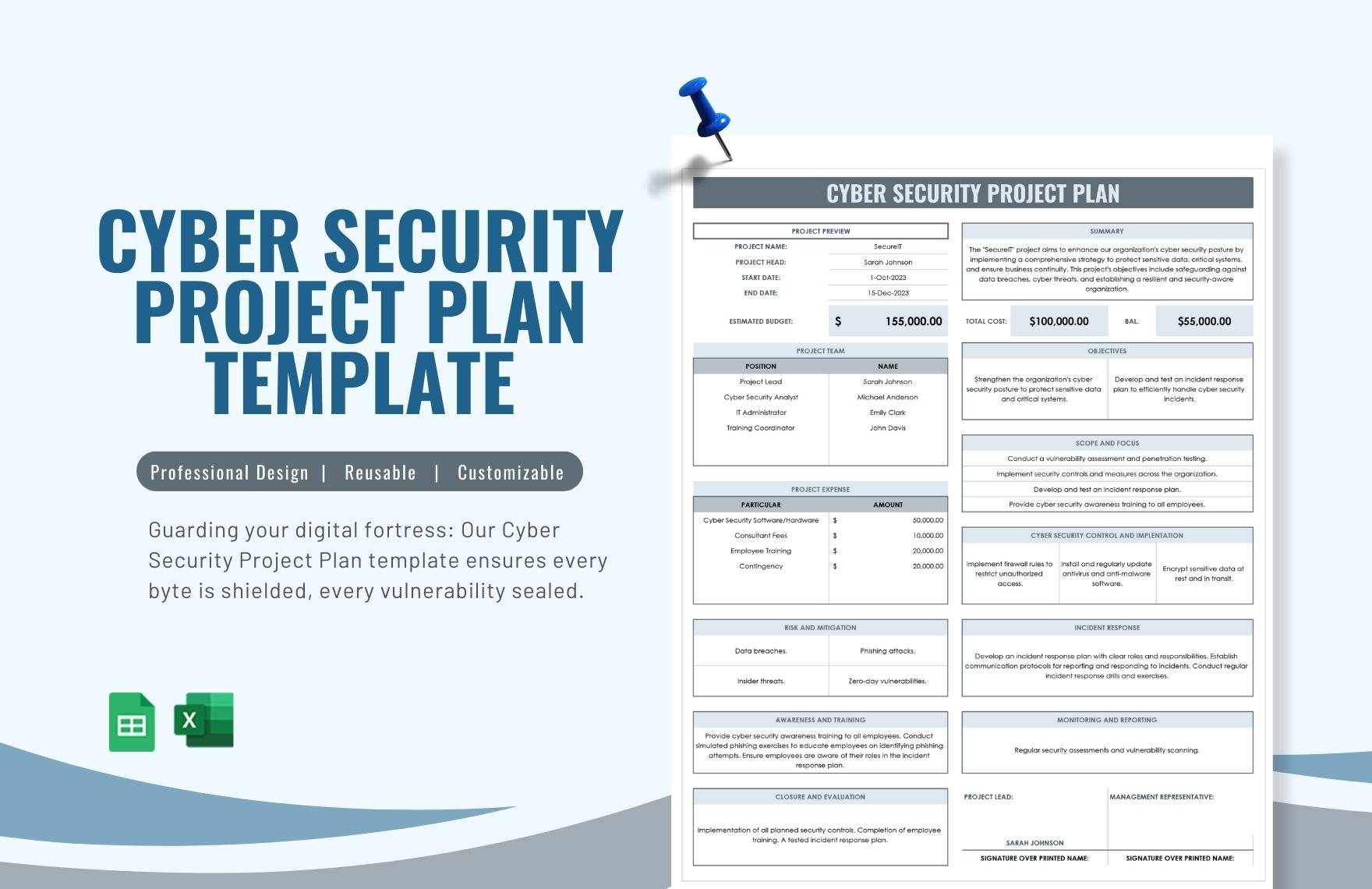
Free Cyber Security Templates to Edit Online

Cybersecurity SLA (Service Level Agreement) Template in Word PDF

Security Agreement Sample Free Agreement Templates

Cyber Security Agreement Template

Cyber Security Agreement Template

Security Agreement Template Fill Out Sign Online and Download PDF

Cyber Security Agreement Template

Cyber Security Agreement Template Form Fill Online Printable

Cyber Security Agreement Template

Cyber Security Agreement Template

Cyber Security Agreement Template

Cyber Security Agreement Template

Cyber Security Agreement Template
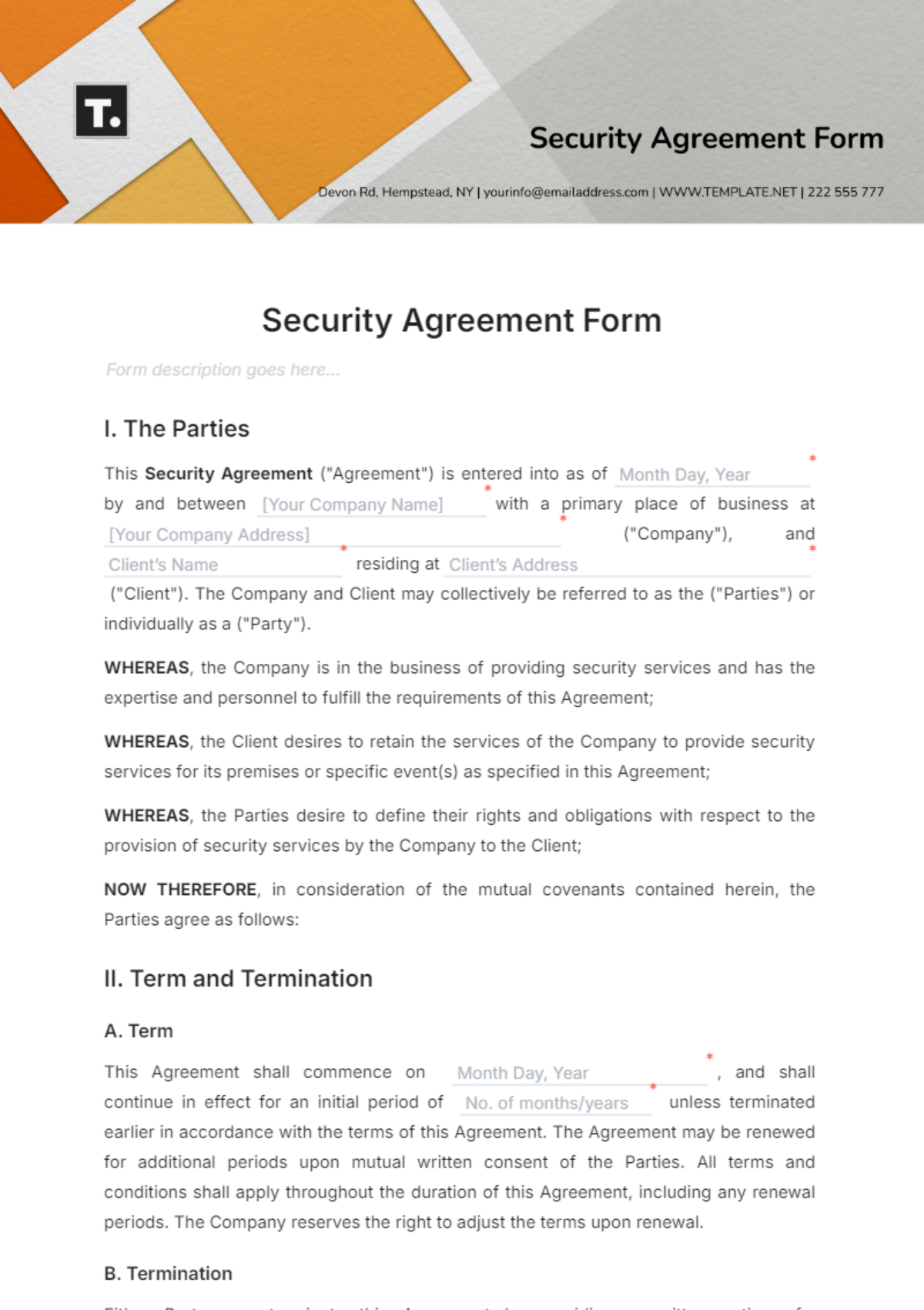
Free Security Agreement Form Template to Edit Online

Security Templates in Word FREE Download Template net

Cyber Security Audit Agreement Template (Word PDF) Free Trial

Cyber Security Presentation Template

Cyberton Cyber Security Powerpoint Template

Free Agriculture Security Agreement Template to Edit Online
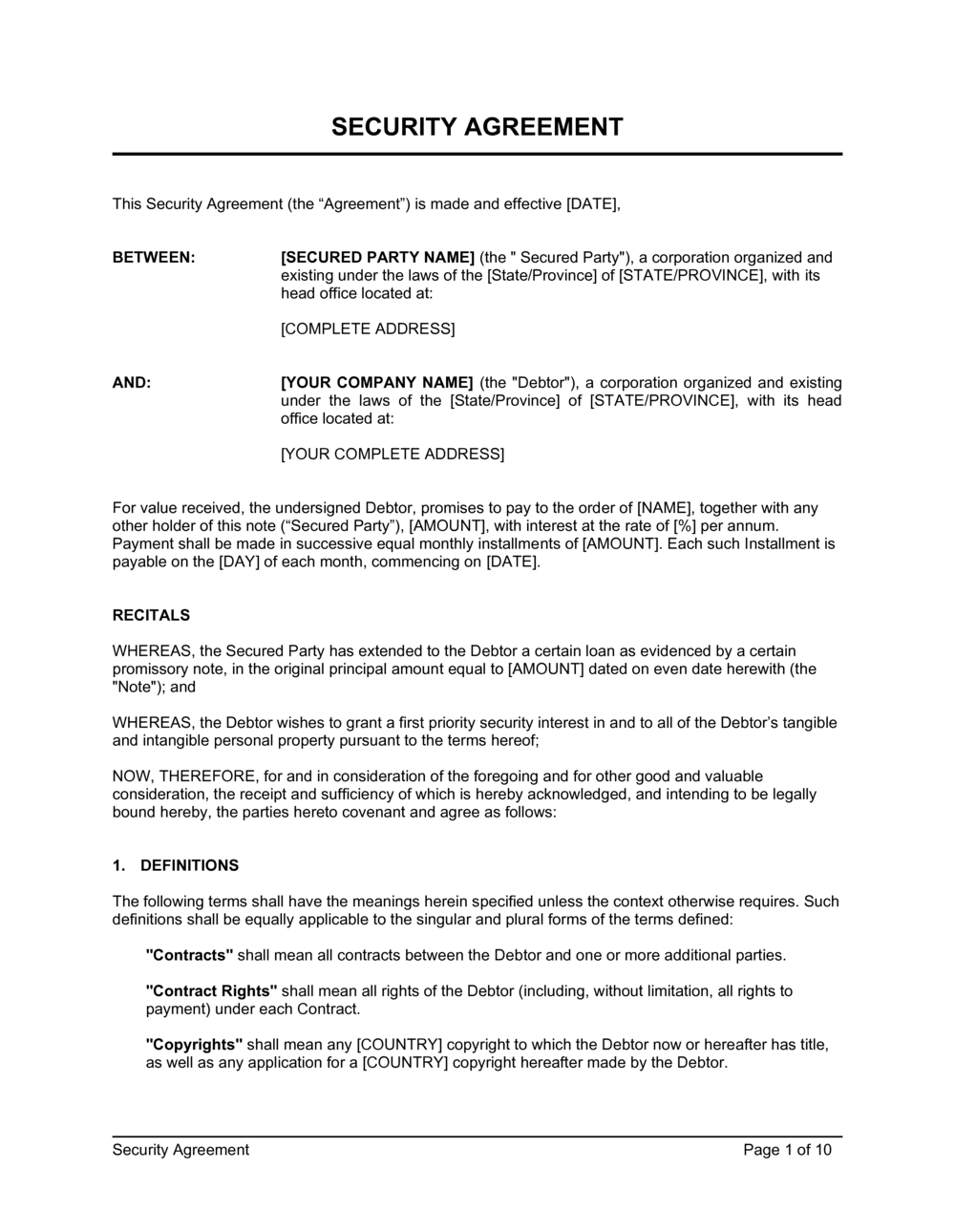
Security Service Agreement Template

Security Service Agreement Template

FREE 12 Sample Security Agreement Templates in Google Docs MS Word

Cyber Security Plan Template

Cyber Security Business Plan Template

Security Agreement Template
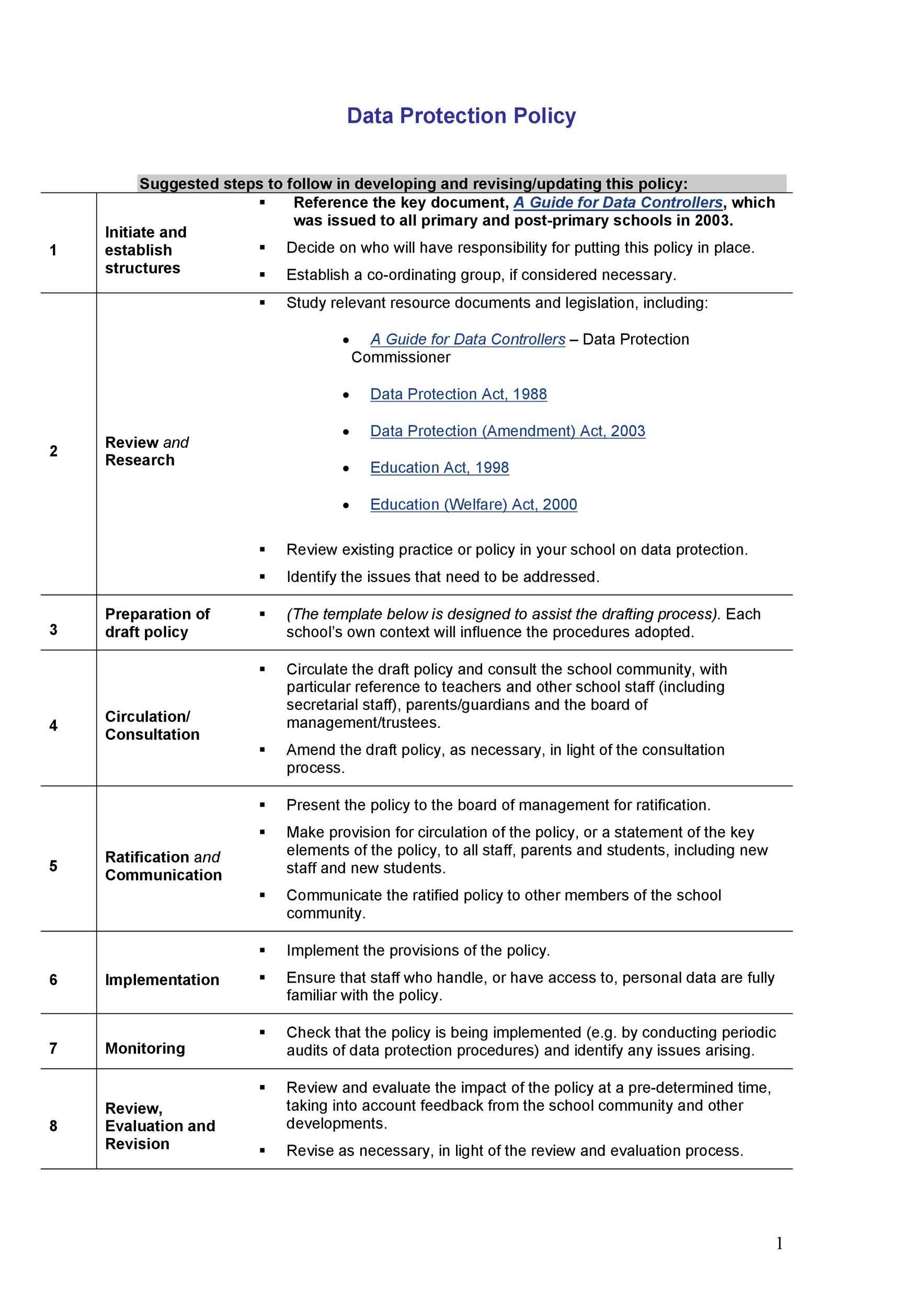
Cyber Security Sop Template prntbl concejomunicipaldechinu gov co

Cyber Security Sop Template prntbl concejomunicipaldechinu gov co

Cyber Security Sop Template prntbl concejomunicipaldechinu gov co

Cyber Security Sop Template prntbl concejomunicipaldechinu gov co

Cyber Security Sop Template prntbl concejomunicipaldechinu gov co

Free Security Agreement Template
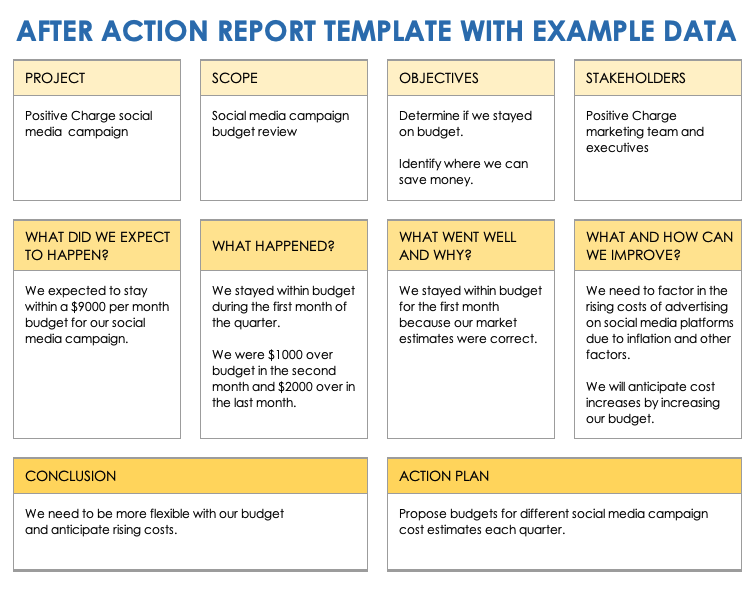
Cyber Security Sop Template prntbl concejomunicipaldechinu gov co

Free Security Agreement Template
Tenet Cyber Security Services Elementor Pro Template Kit

Free School Transport Agreement Template to Edit Online

Free Cyber Security Agreement Templates Revv

Free Cyber Security Agreement Templates Revv

Free Cyber Security Non Disclosure Agreement (NDA) PDF Word

Free Cyber Security Non Disclosure Agreement (NDA) PDF Word

Free Cyber Security Non Disclosure Agreement (NDA) PDF Word

Free Cyber Security Non Disclosure Agreement (NDA) PDF Word

Security Agreement download free documents for PDF Word and Excel

Security agreement template free to use

Free Hotel Agreement Templates Editable and Printable

Cyber Incident Response Plan Template

Cyber Security Templates Agreements Business Document Templates Revv

13 Cyber Security CV Examples for 2025 Resume Worded

Private Security Contract Template

10 FREE Security Agreement Samples to Download

Information Security Policy Template For Small Business prntbl

Loan Agreement With Collateral Template

Premium Photo Handshake of two businesswomen who enters into the

Daylig Arlan N DLP 3D CRAFTS Assemblage PDF Length Paper
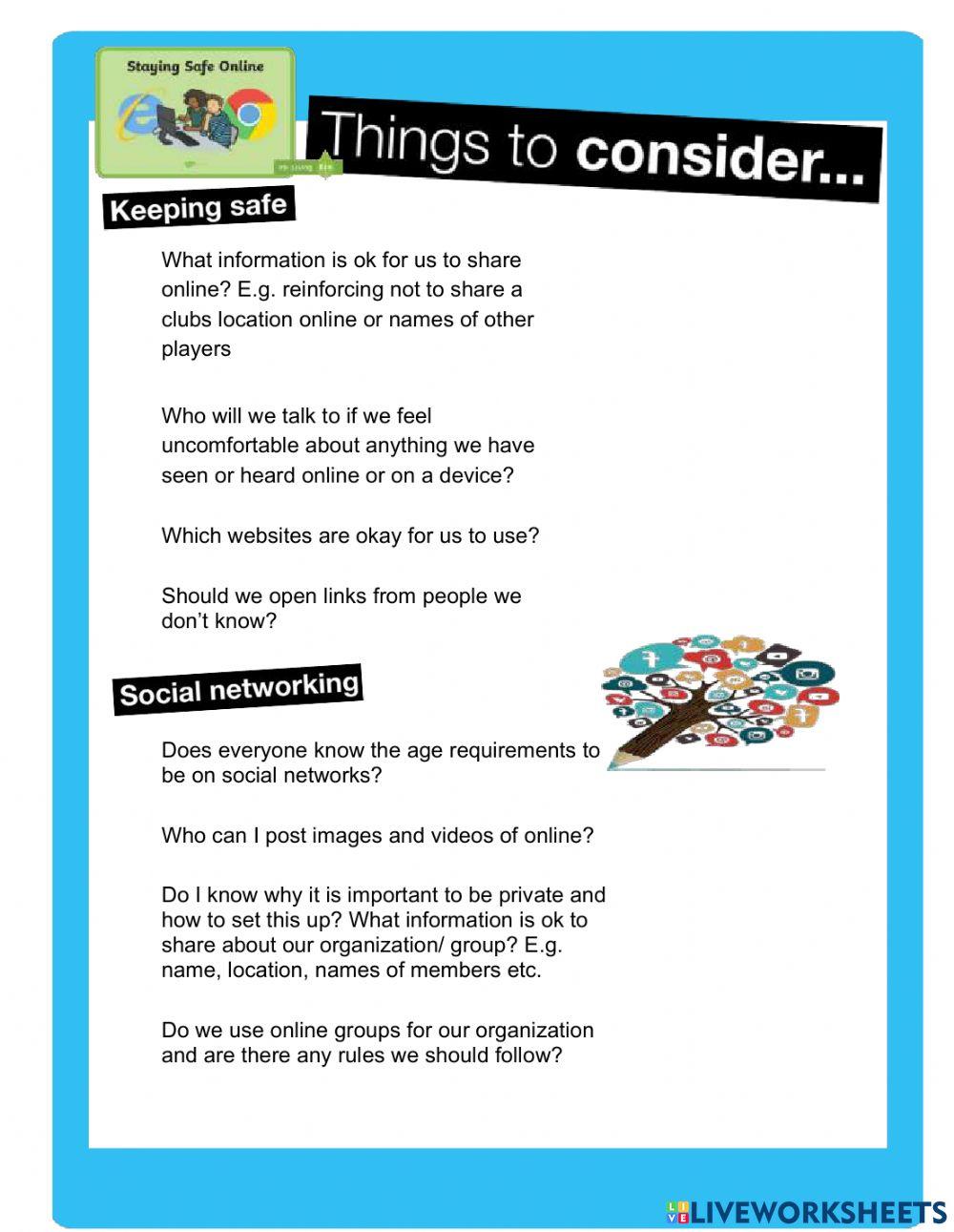
Cyber Security Agreement 2022 online exercise for Live Worksheets