Cyber Threat Hunting Certification
Here are some of the images for Cyber Threat Hunting Certification that we found in our website database.

Cyber Threat Hunting Training Certification by Hacker Associate

Cyber Threat hunting training CTH Training CTH 1191
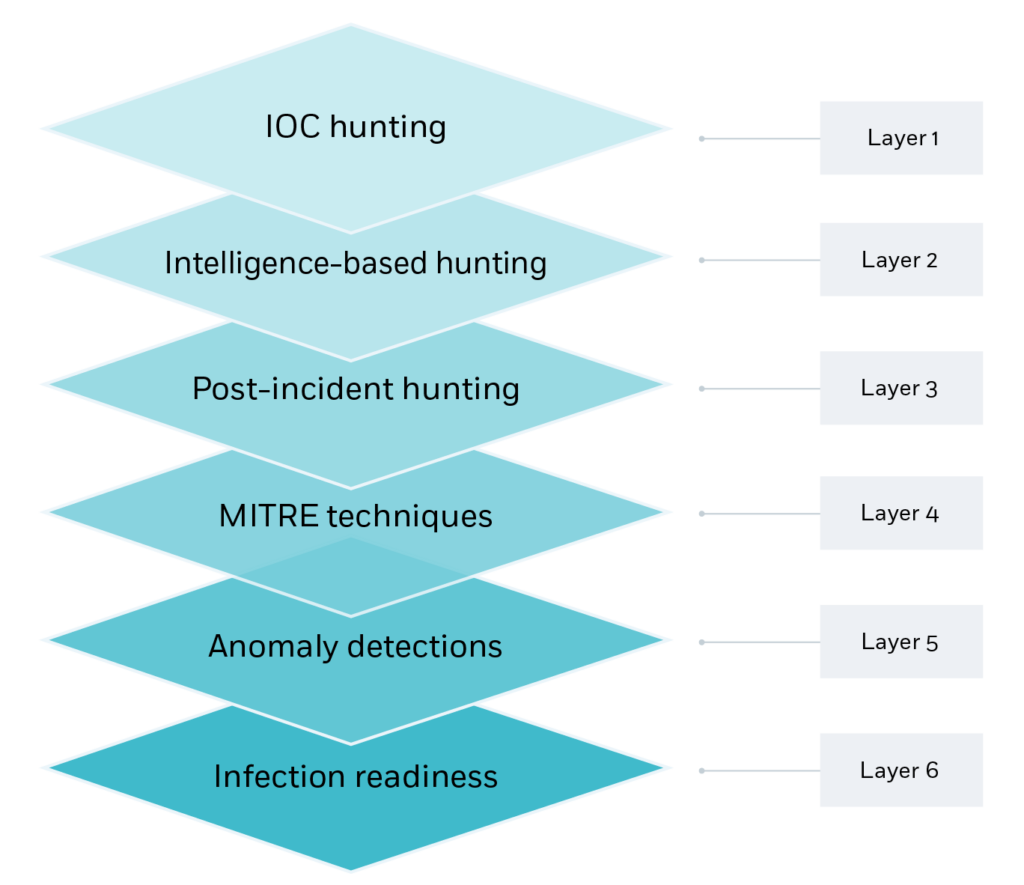
What is threat hunting? CyberProof

INE Enhances Threat Hunting Certification for Modern Cybersecurity

Cyber Threat Hunting (Coursera) MOOC List

Cyber threat hunting skills

Cyber Threat Hunting Model Types PPT Slide

Defending the Digital Frontier: Essential Cyber Threat Hunting Tools

What Is Cyber Threat Hunting?

Cyber Threat Hunting InfoSec Certificate PDF

Cyber Threat Hunting Learning Path Course Expert Training

Cyber Threat Hunting and Intelligence System for Smart Grid Cyber

Cyber Threat Hunting: Types Methodologies Best Practices

Cyber Threat Hunting Certification Training Boot Camp Infosec

Cyber Threat Hunting Certification Training Boot Camp Infosec

OffSec #39 s New Threat Hunting Course and Certification Equip

Unveiling The Mask: Understanding Threat Intelligence And Cyber Threat

4 Types Of Cyber Threat Hunting Tools In 2024 SISA Infosec

10 Best Cyber Threat Hunting Tools for 2024

Foundations of Threat Hunting and Detection Cyberyami

Threat Hunting In Cyber Security

What is Cyber Threat Hunting Video Blog Active Countermeasures

Premium Vector Cyber threat hunting Practice of proactively searching

Cyber Threat Hunting Training (CCTHP) PPTX

Cyber Threat Hunting 101 Guide Methods Tools Techniques Frameworks
Top 4 Benefits Of Cyber Threat Hunting Visualmodo
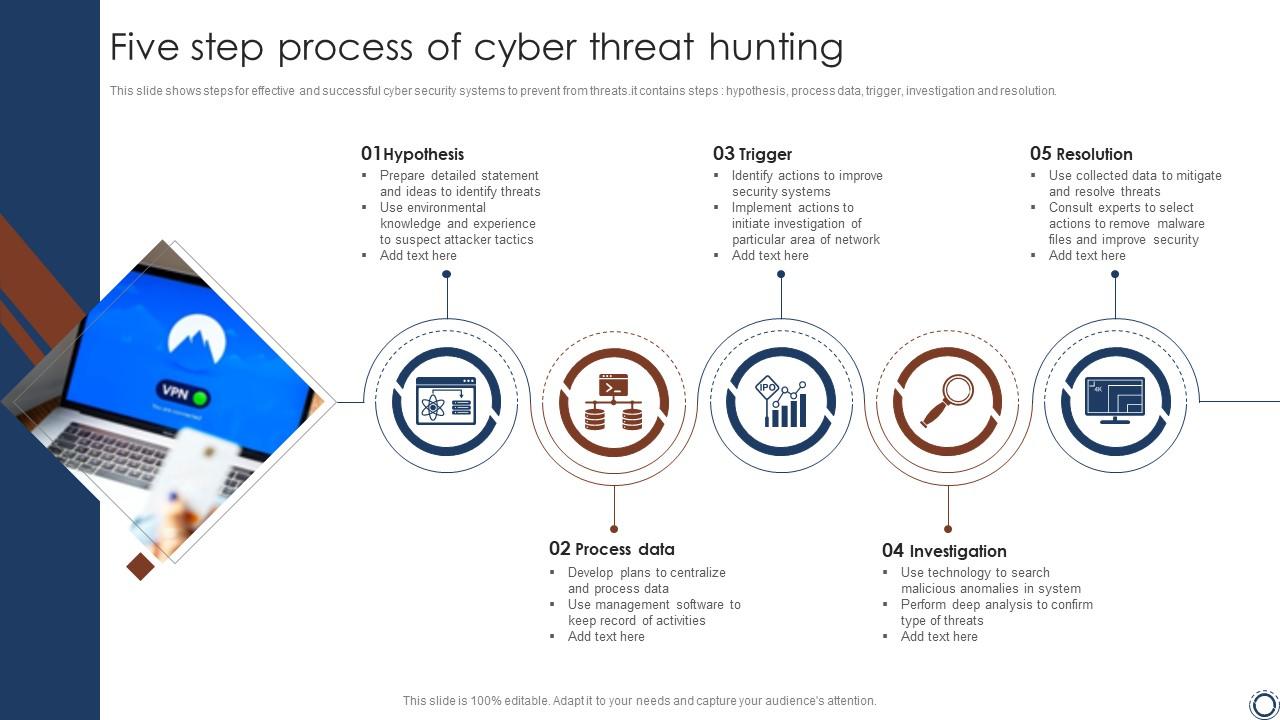
Five Step Process Of Cyber Threat Hunting PPT Slide

Threat Hunting Training Certification and Online Learning : r/SOCPrime

Mustafa Alp Özdemir on LinkedIn: Cyber Threat İntelligence and Threat

Cyber Threat Hunting Certification Training Boot Camp Infosec

Unified SASE role Cyber Threat Hunting Security Boulevard

Cyber Threat Hunting Certification Training Boot Camp Infosec

What Is Cyber Threat Hunting? 2019 Security Boulevard

Earned Threat Intelligence and Hunting certification from IBM Mufid

Threat Hunting: A Proactive Approach to Identifying and Neutralising

Aaron Furlong on LinkedIn: Just attained my Cyber Threat Hunting

SecurityTube 🎯 Ready to level up your threat hunting game? The

What is Cyber Threat Hunting? A brief guide Blog ICSS

KQL WINDOWS THREAT HUNTING WITH JohnDCyber by John D Cyber Medium

What is Cyber Threat Hunting and Why It s Crucial for Your

Review: eCTHPv2 Certification Mastering Threat Hunting with

What is Threat Hunting? The Complete Guide Updated 2025

Review: eCTHPv2 Certification Mastering Threat Hunting with

Review: eCTHPv2 Certification Mastering Threat Hunting with

Cyber Threat Hunting Hackers Hive

Phases of Threat Hunting

What Is Threat Hunting? A Guide to Proactive Cybersecurity

Earned eCTHP certification from INE for advanced threat hunting

Threat Hunting and Detection Engineering Certification Credly

Cyber Threat Hunting vs Incident Response: What s the Difference

Splunk Certified Cybersecurity Defense Analyst Splunk

CEH Certification Overview PenTesting Org

Top 10 Cyber Threat Intelligence Certifications for 2023 Security

What are the different types of cyber threat actors? Page 3 of 3

2 Thousand Endpoint Threat Royalty Free Images Stock Photos

OffSec Launches New Incident Response Course Certification to Help

Penough Dhaka