Cyber Threat Report Template
Here are some of the images for Cyber Threat Report Template that we found in our website database.

400 000 Free Cybersecurity Background Cybersecurity Images Pixabay

K Cyber

November 2018 Battle in Cyberspace Via Satellite

Helping to shape the RMIT Centre for Cyber Security Research and

900 Free Cybersecurity Certifications Cybersecurity Images Pixabay

What Is Cybersecurity? Forage

Biggest Cybersecurity Trends For 2023 ClearVPN Blog

Tutto su cyberspace Cyber Security 360

Cyber Security Technology And Online Data Protection In An Innov

Ai In Cybersecurity Summit
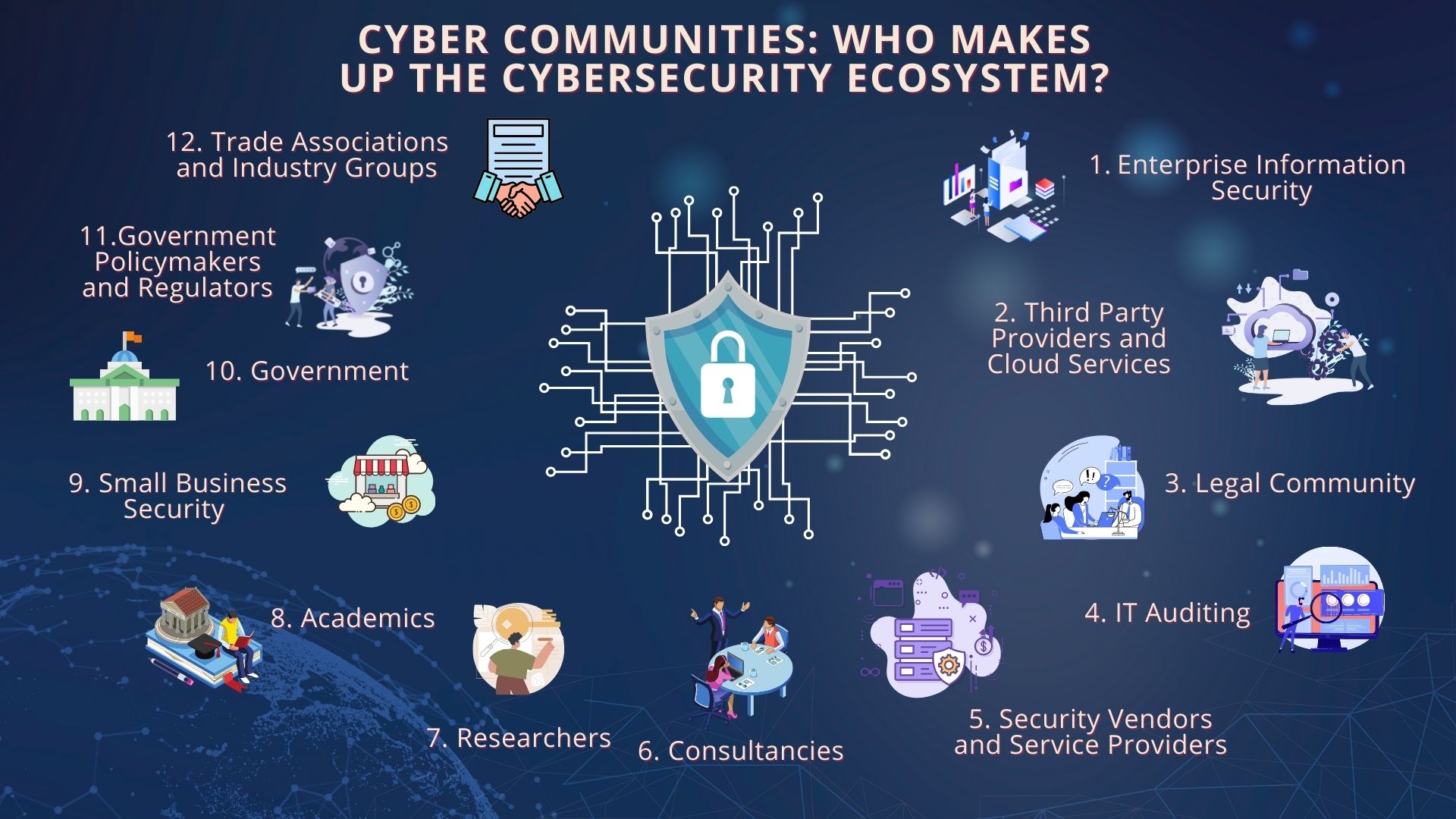
Cybersecurity Ecosystem: 12 Cyber Essential Communities

ICOS inaugura una BU dedicata alla cyber security Top Trade

Importance of Cyber Security in Business AeoLogic Blog

atodorov org you can logoff but you can never leave

Cyber Security and Segregation of Duties Security Boulevard

Insights: Top 8 cyber travel tips to keep in mind

Cybersecurity Concerns With Ai

Arti Cyber Temukan Pengertian dan Makna Cyber dalam Dunia Digital

Cyber Threats

New cybersecurity technology 2022 Security Magazine
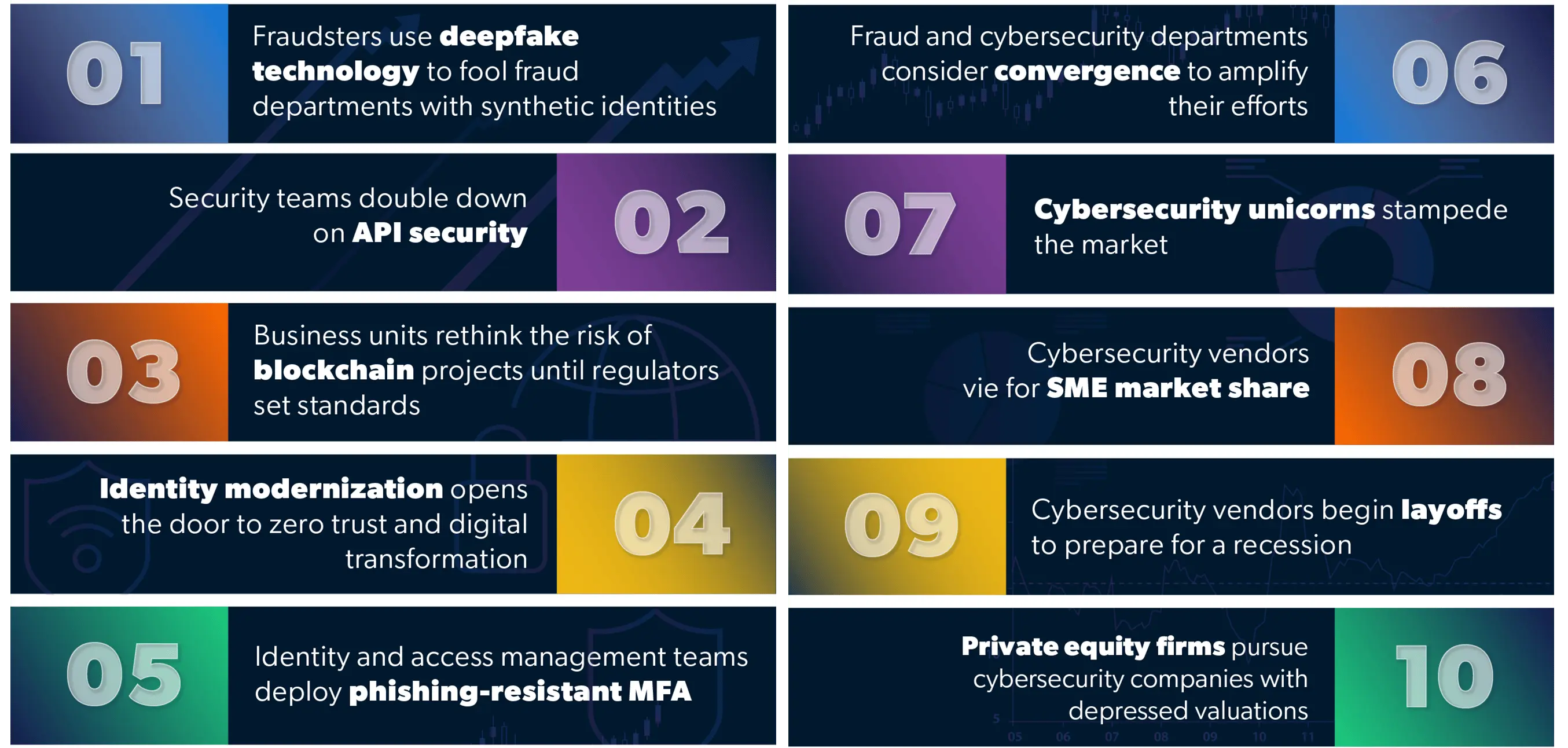
Top 3 Cybersecurity Trends for SME Business Leaders in 2024

Are You Falling for Cyber Baiting? BestCybersecurityNews Medium

Cyber security

The basics of cyber security Artofit

Rescued Sri Lankan cyber slaves arrive home

Cyber

China #39 s Cyber Espionage and ICC Cybersecurity Breach

Cybersecurity 2 0 DHL Japan

Apa itu Cyber Security? Pengertian Jenis dan Tekniknya Link Net

Cybercrime News

Pure play cybersecurity firms in your backyard CSO Online

Cyber risk: Why Cybersecurity Is Important IT Security Guru

Cybersecurity Concerns With Ai

What is Cybersecurity? Everything You Need to Know
Free Industrial Control System (ICS) Cyber Security Course

6 Key Cyber Security Frameworks You Should Be Aware Of

Understanding the 3 Phases of Cybersecurity Architecture Ardoq

BroadBand Nation: Cybersecurity Career Pathway (INFOGRAPHIC)
.png)
Importance of Cyber Security For Business in 2023

Cyber Risk Management and the Value of Cyber Insurance InfoGovANZ

Cybersecurity Expert: 5 Important Steps to be an Expert

The Path to a Successful Career in Cybersecurity Top Teen

Download Cyber Security Is A Key To Your Business Wallpapers com

Cybersecurity leads IT budgets WatchGuard Blog

Types of Cyber Security Threats NEIT

Siemens USA launches cybersecurity analytics lab to help protect

Cabinet to Approve First #39 National Cyber Security Policy 2021 #39 today
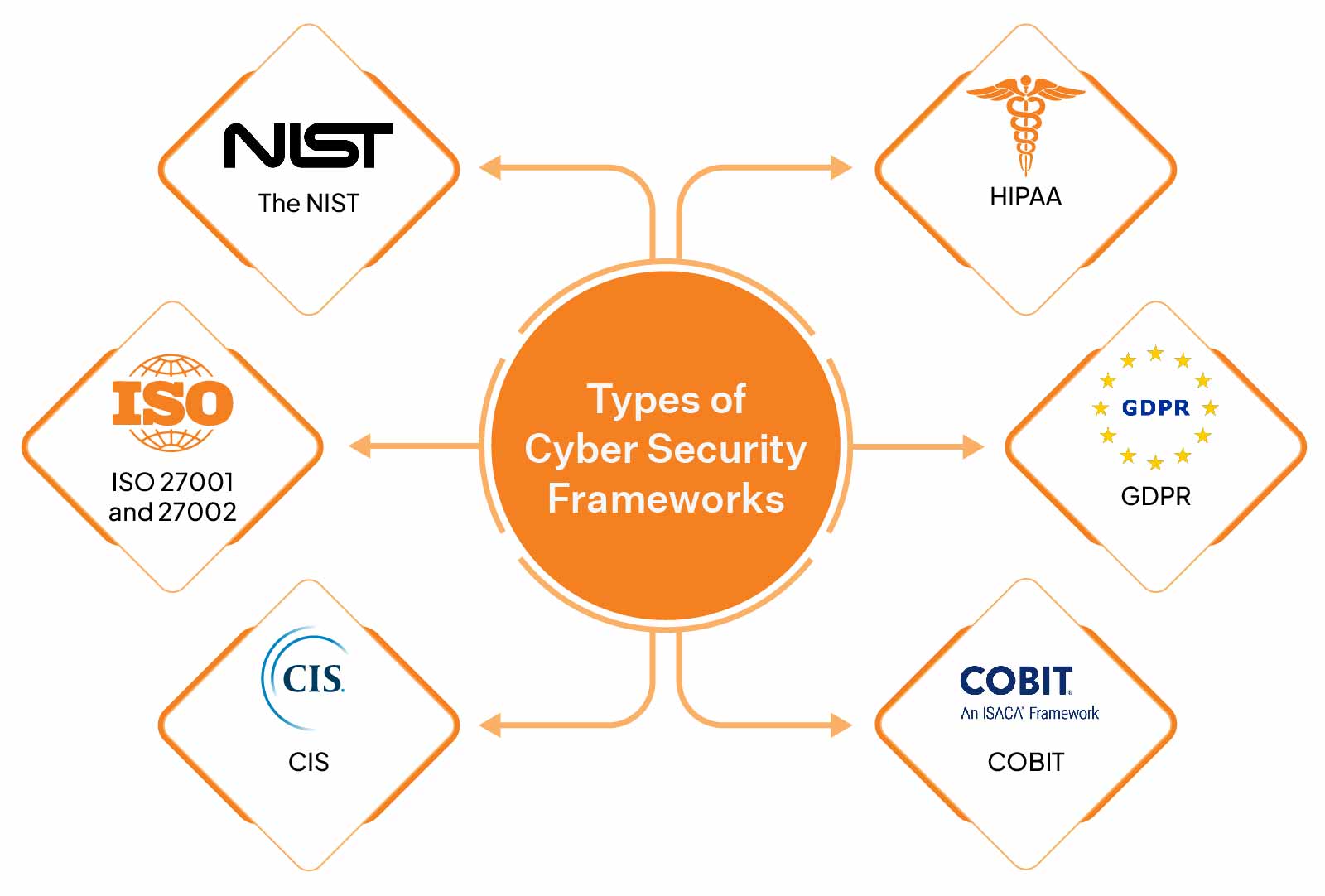
List of Top 6 Cybersecurity Frameworks Sprinto

375 daily Cyberattacks in 2020 says India #39 s cybersecurity coordinator
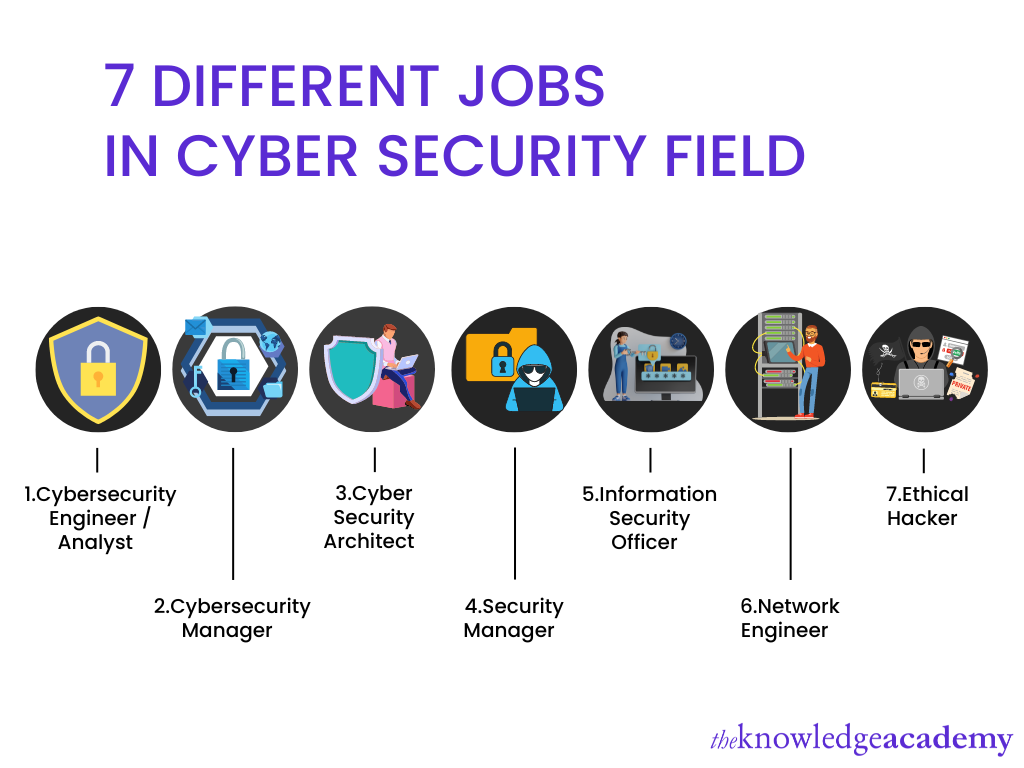
Cyber Security Roadmap For Beginners: A 2025 Guide
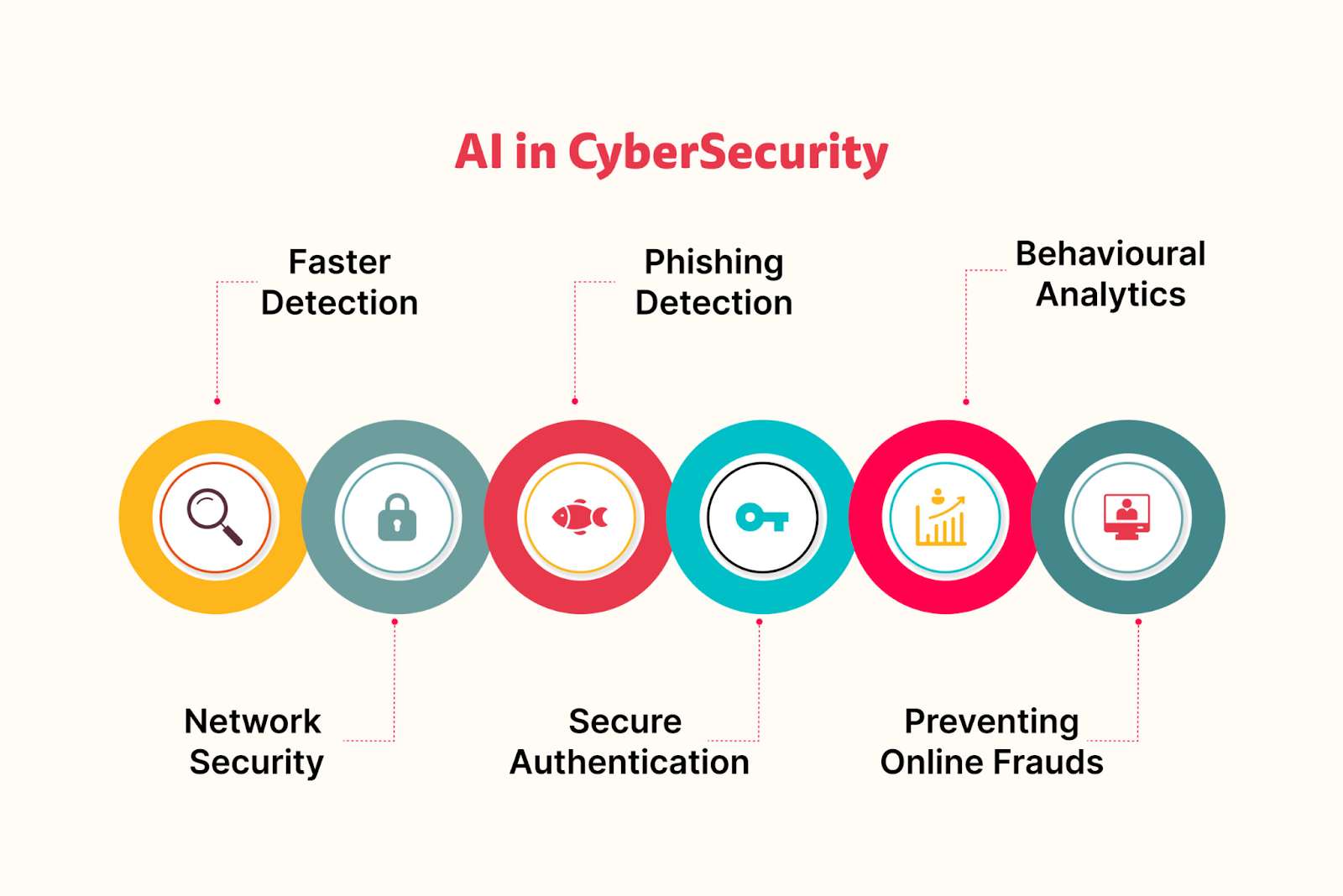
Cybersecurity Issues In Ai

Pin on Digital Marketing

The overview of some common types of cyber attacks Download

Computer Institute of Ramkhamhaeng University

Cyber Insurance Broker In Ontario Data Breach Ransomware Protection

An Introduction to Cyber Security: Basics Concepts and Frameworks

Download Join the Cyber Evolution Wallpapers com

How Does Cybersecurity Impact Identity Protection at Jean Fowler blog
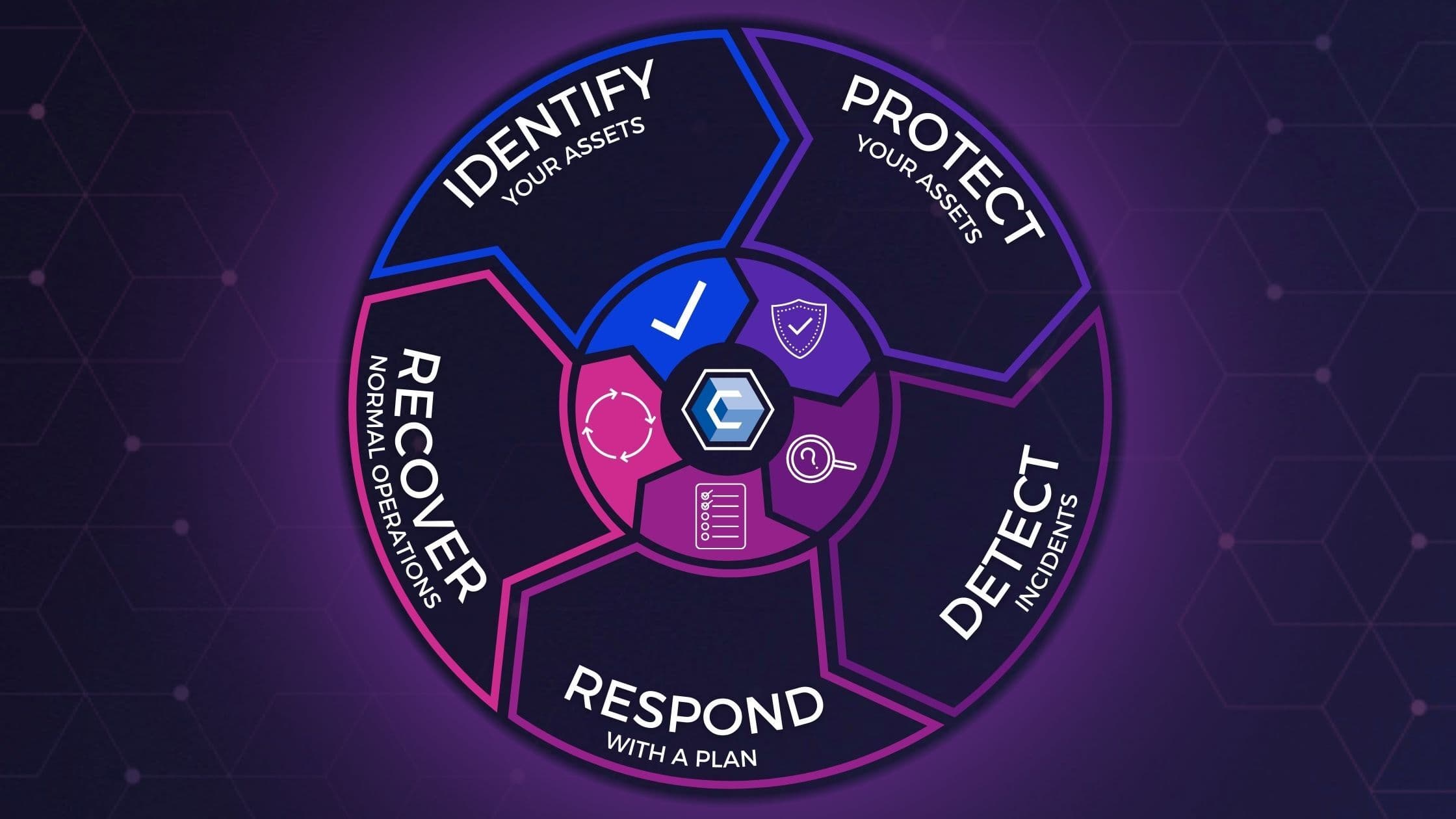
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES