Device Certificate Authentication
Here are some of the images for Device Certificate Authentication that we found in our website database.
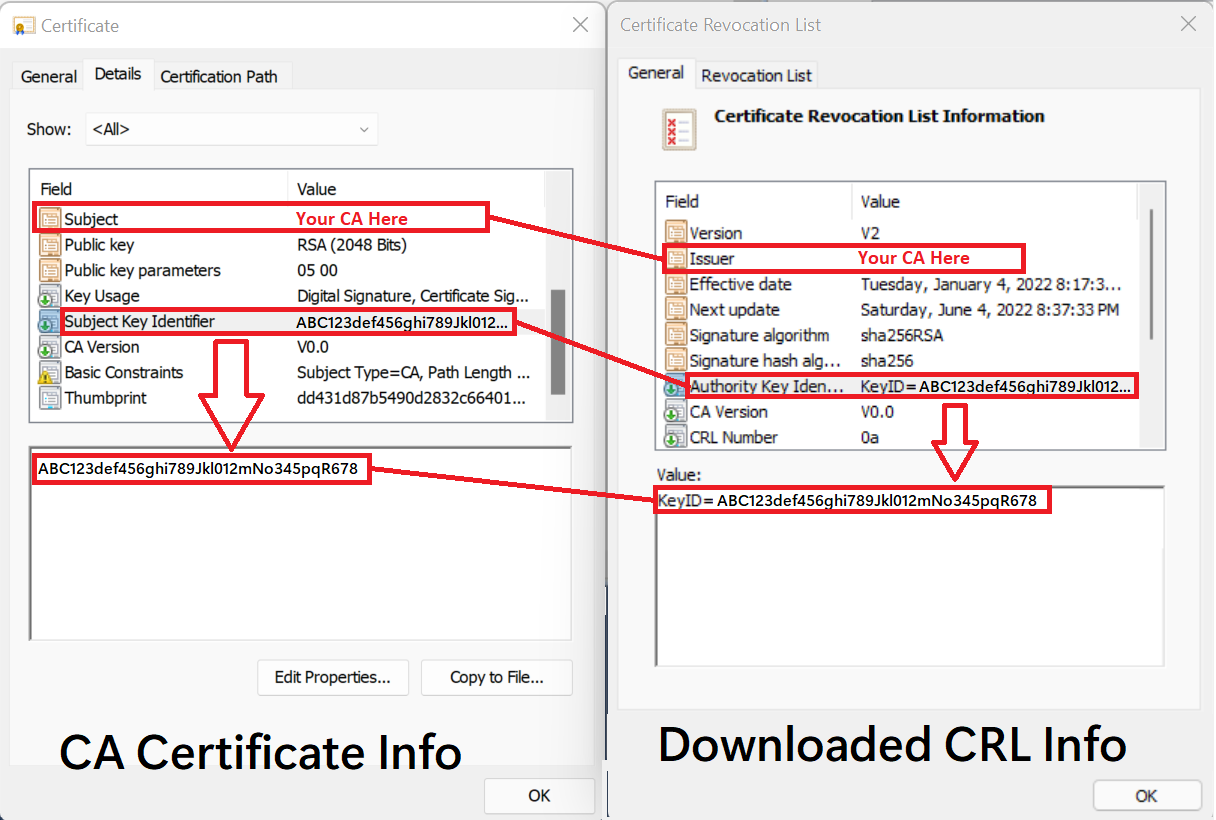
Managing trusted certificate CRL settings Cumulocity documentation
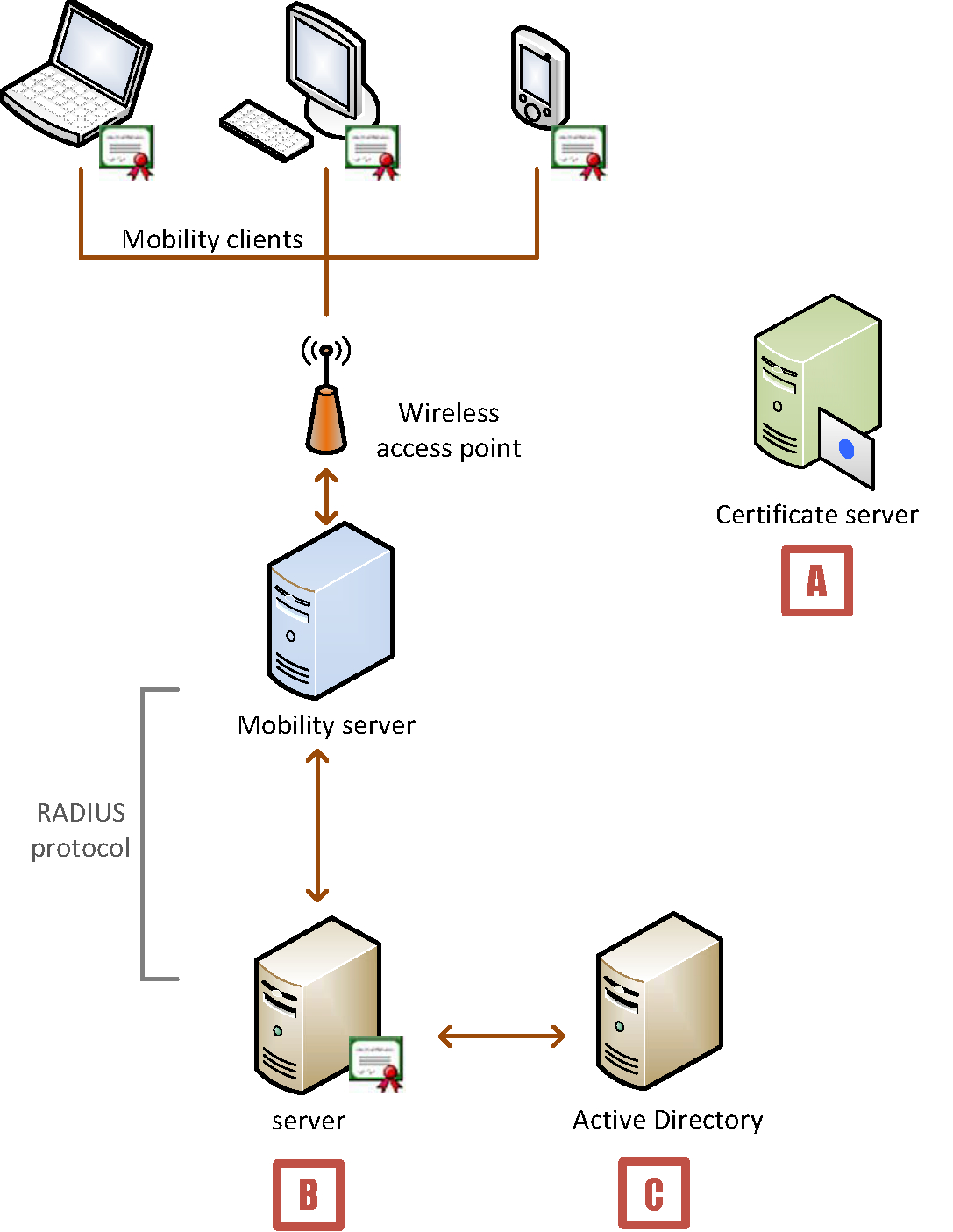
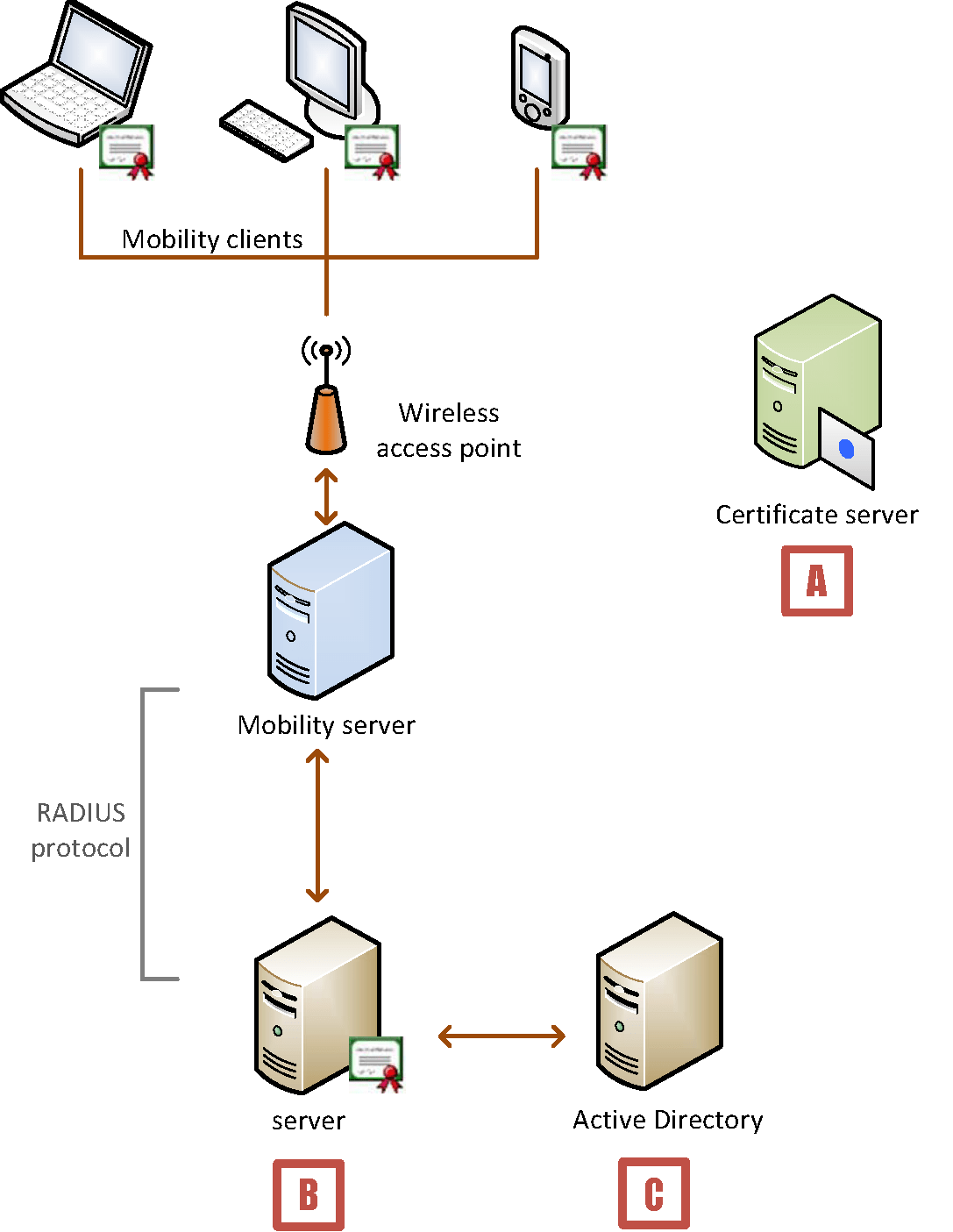
Device Authentication Sample Deployment (Windows) intended for
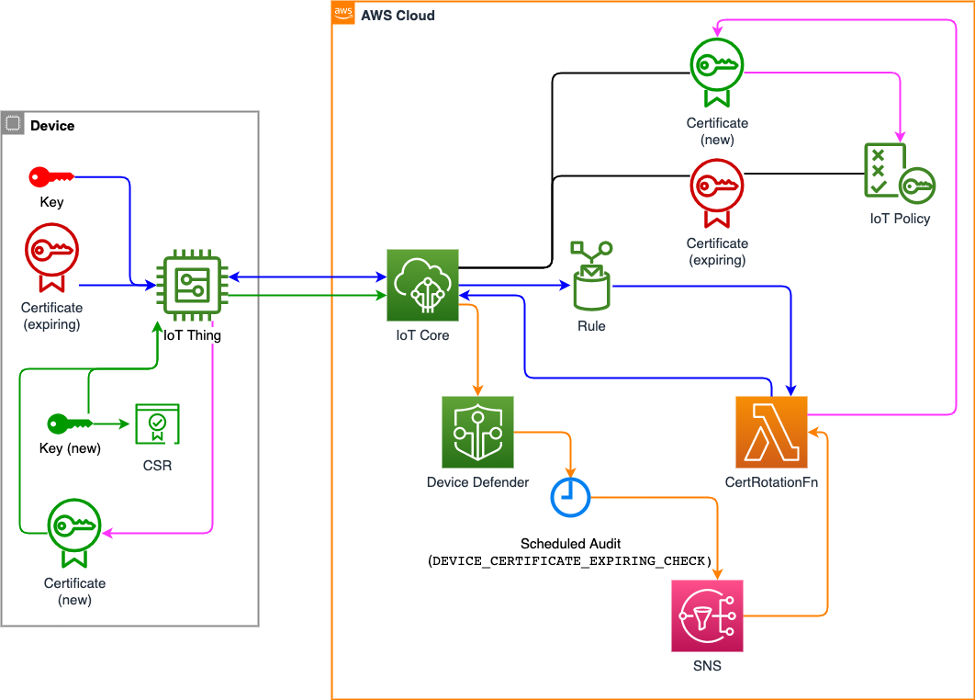
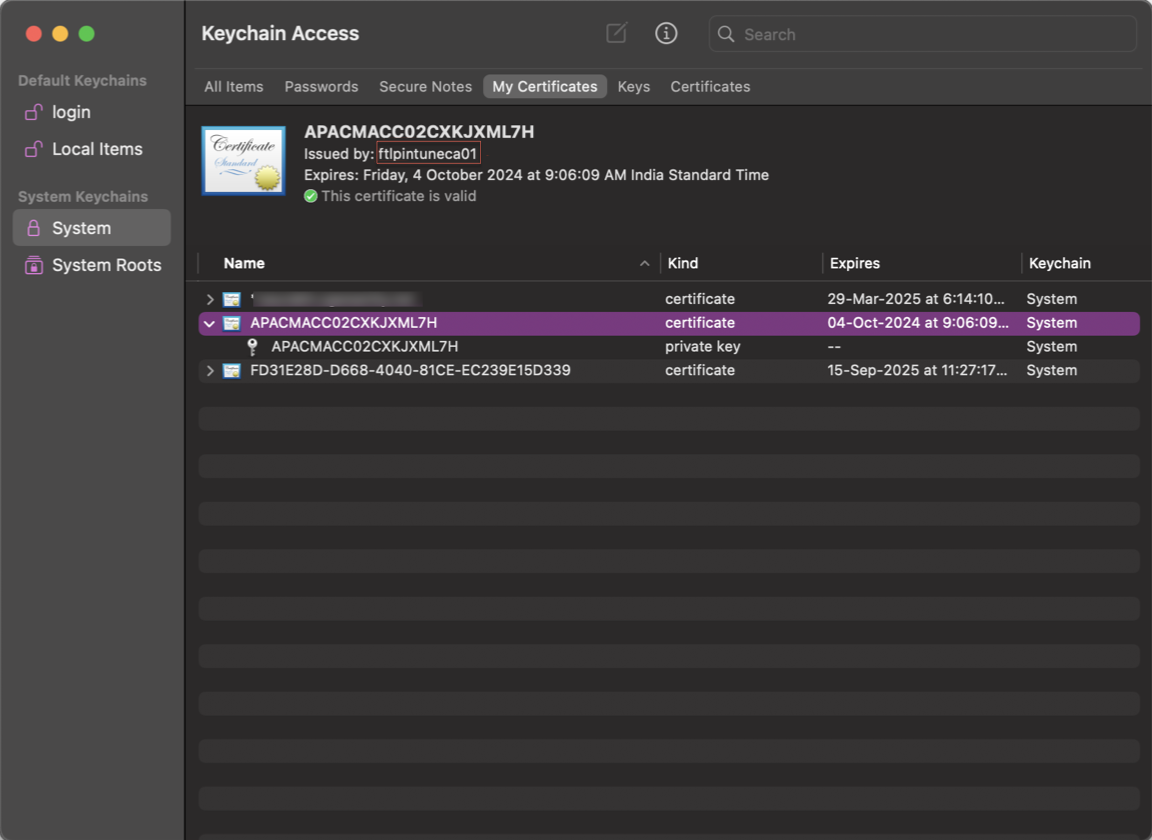
Device x509 certificate rotation

What is Certificate Based Authentication? How it Works

How to Configure Firepower 7 0 AnyConnect VPN Certificate

How to Configure Firepower 7 0 AnyConnect VPN Certificate

How to Configure Firepower 7 0 AnyConnect VPN Certificate
Workstation Authentication Certificate Template Rebeccachulew com
Device certificate check with Device Posture service
Device certificate check with Device Posture service
Device certificate check with Device Posture service
Understand Microsoft Entra certificate based authentication Certificate
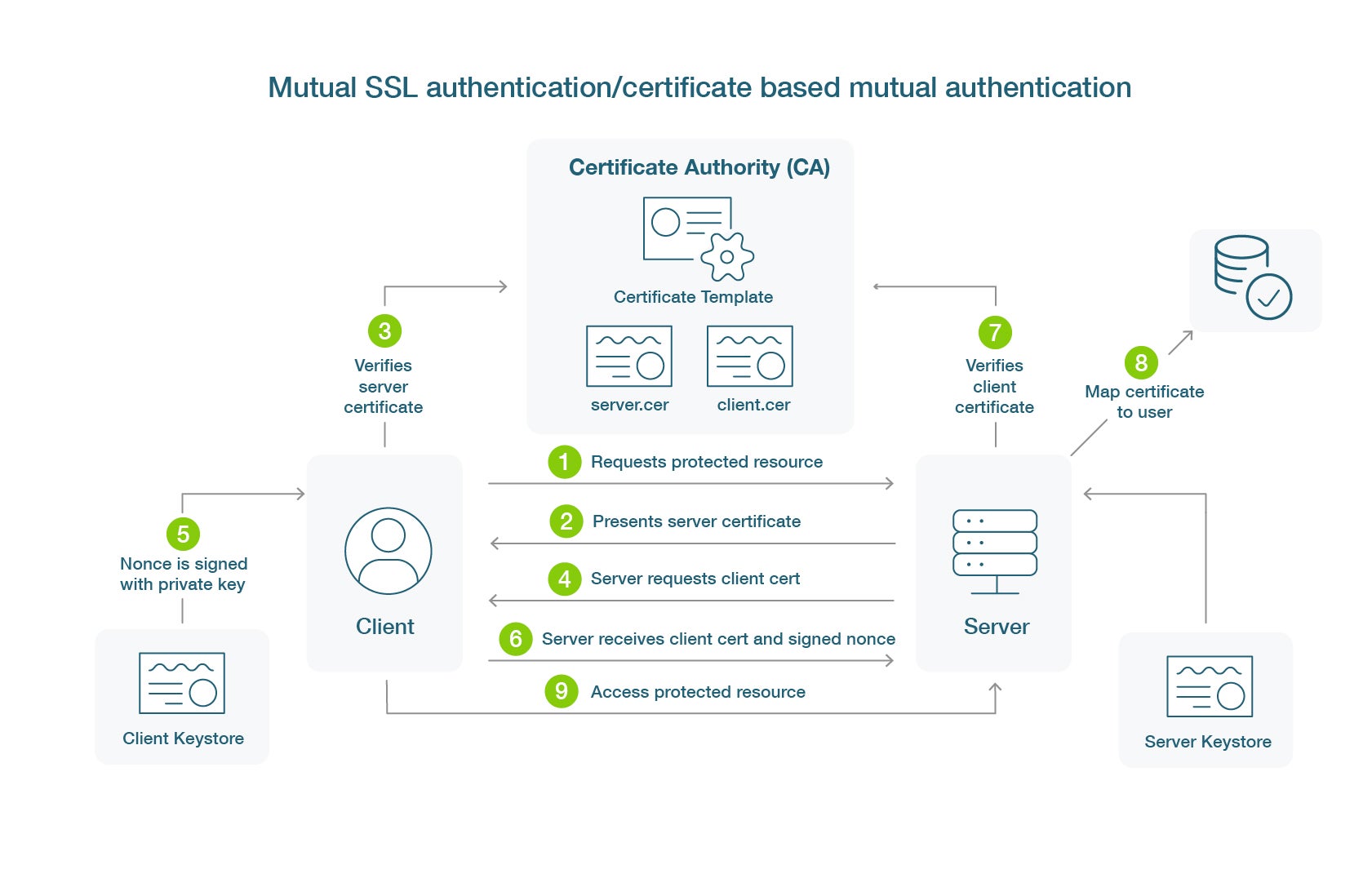
What is Certificate Based Authentication Yubico
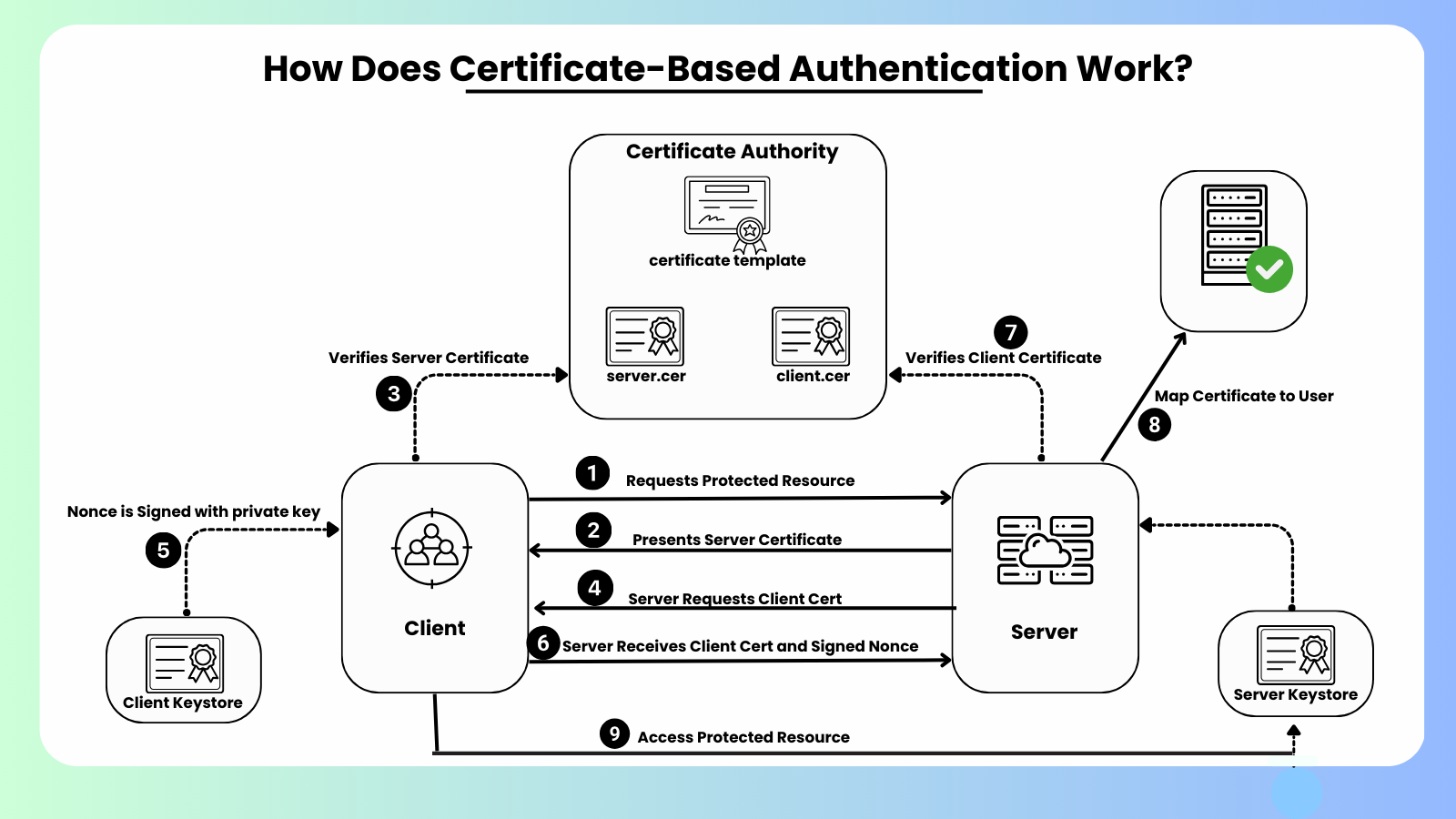
What Is Certificate Based Authentication? How It Works Cybernoz
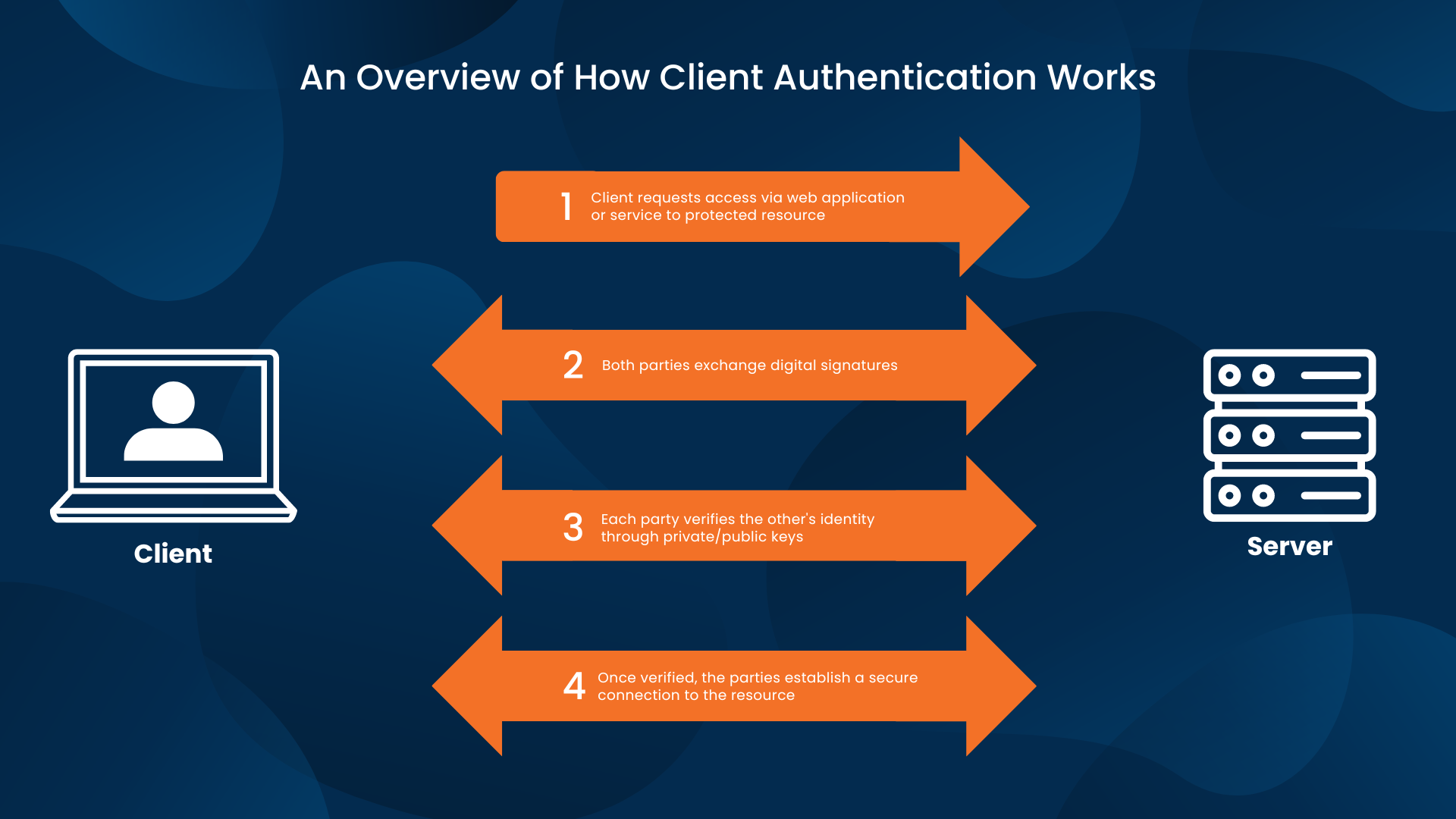
Okta Certificate Based Authentication prntbl concejomunicipaldechinu

Okta Certificate Based Authentication prntbl concejomunicipaldechinu
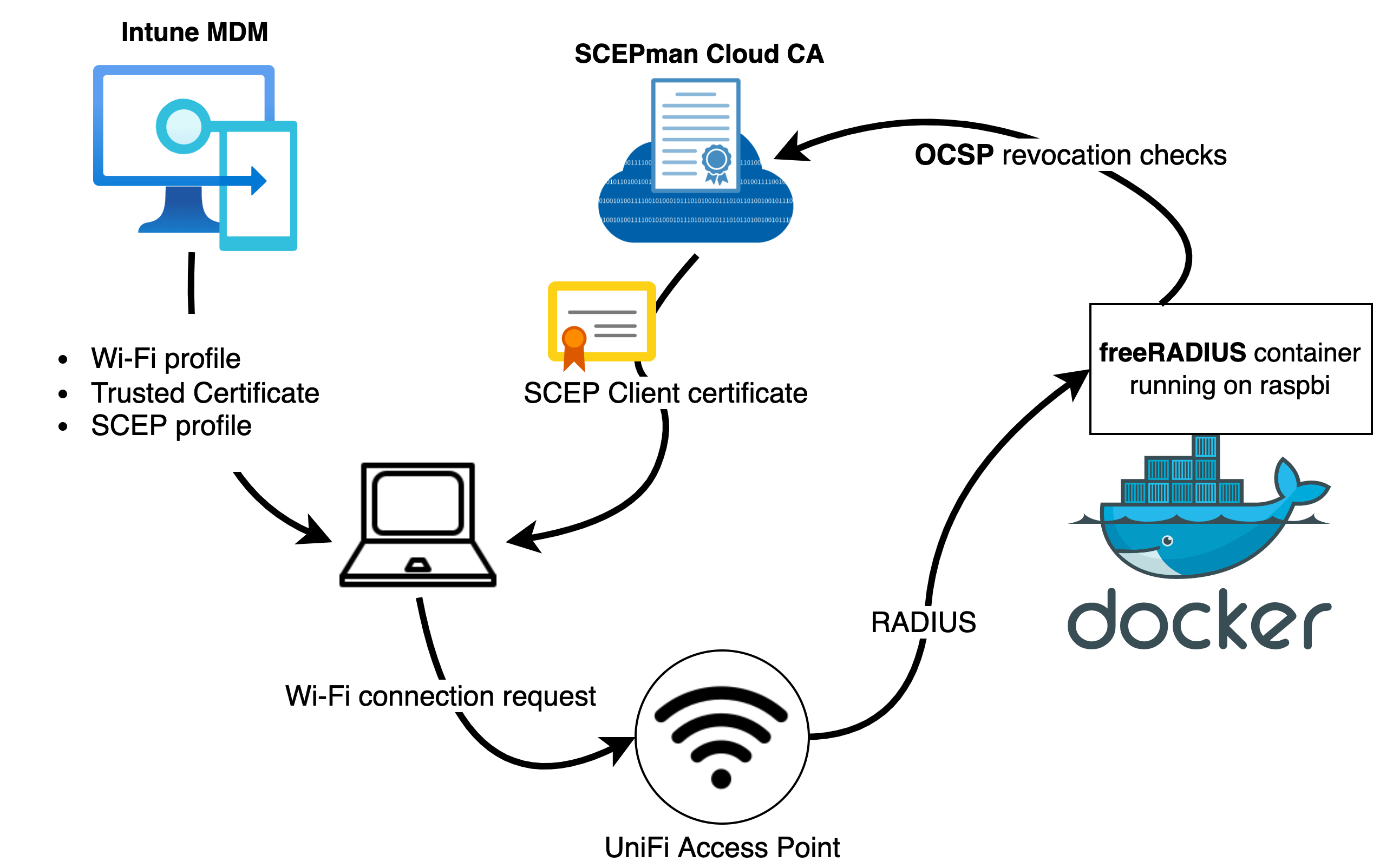
Freeradius Certificate Authentication prntbl concejomunicipaldechinu
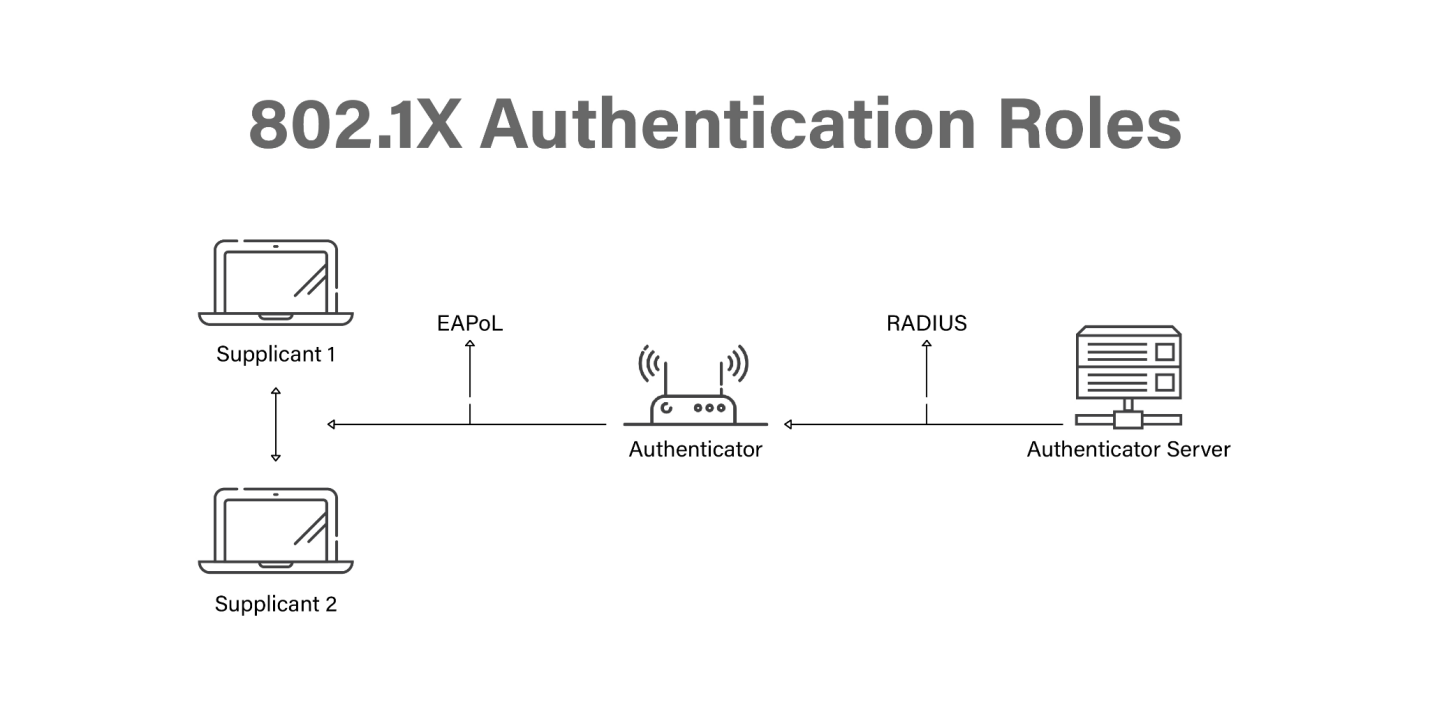
Freeradius Certificate Authentication prntbl concejomunicipaldechinu
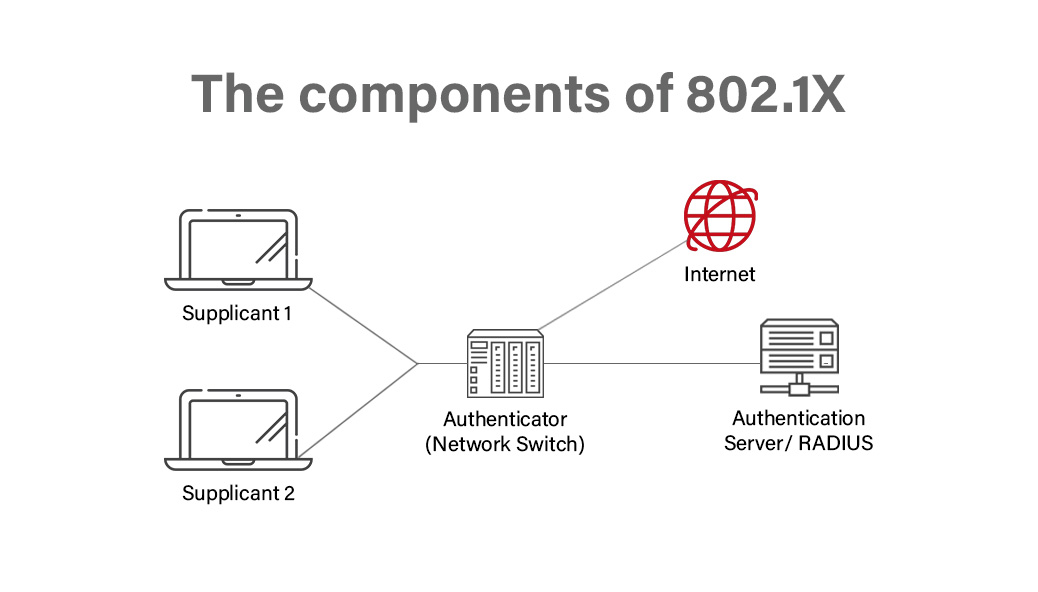
Freeradius Certificate Authentication prntbl concejomunicipaldechinu

Freeradius Certificate Authentication prntbl concejomunicipaldechinu
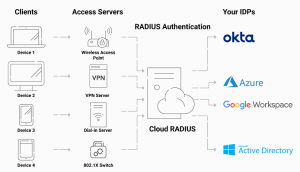
RADIUS Certificate Based Authentication Explained
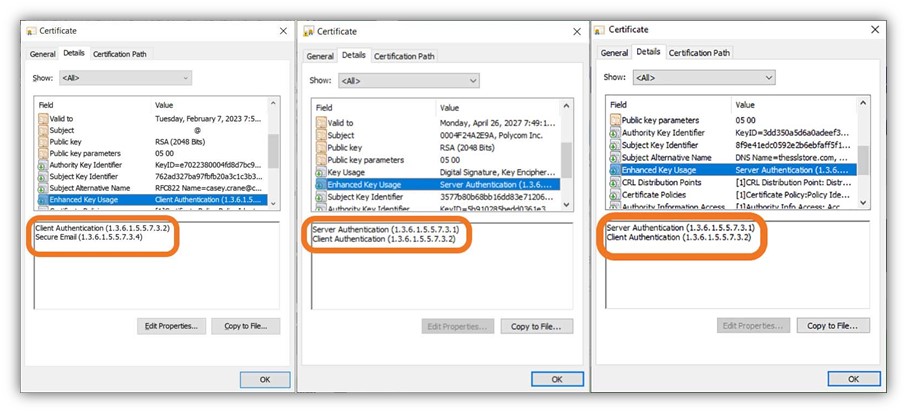
What Is a Device Certificate? Device Certificates Explained Hashed
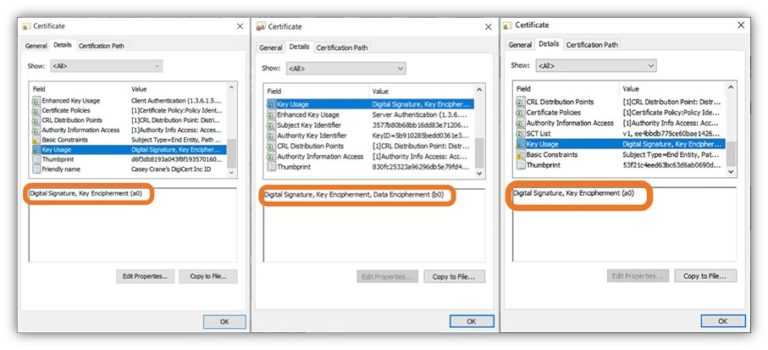
What Is a Device Certificate? Device Certificates Explained Hashed
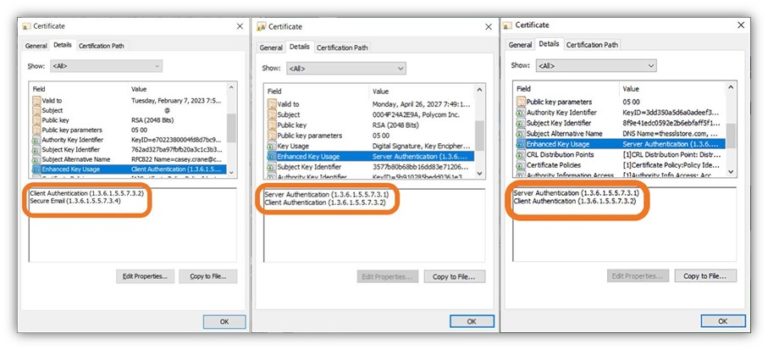
What Is a Device Certificate? Device Certificates Explained Hashed
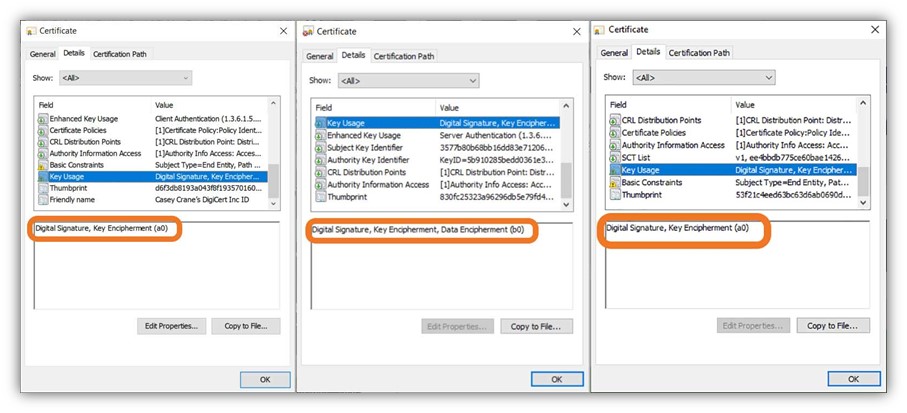
What Is a Device Certificate? Device Certificates Explained Hashed
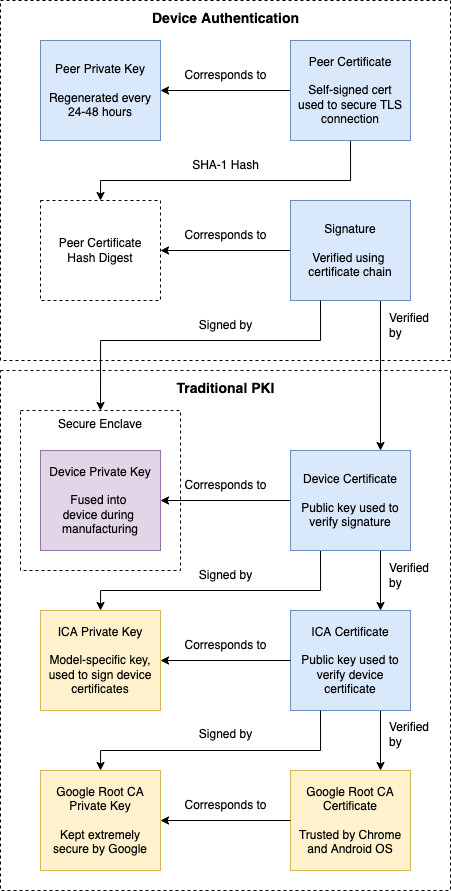
Chromecast Device Authentication Tristan Penman · Hacker at
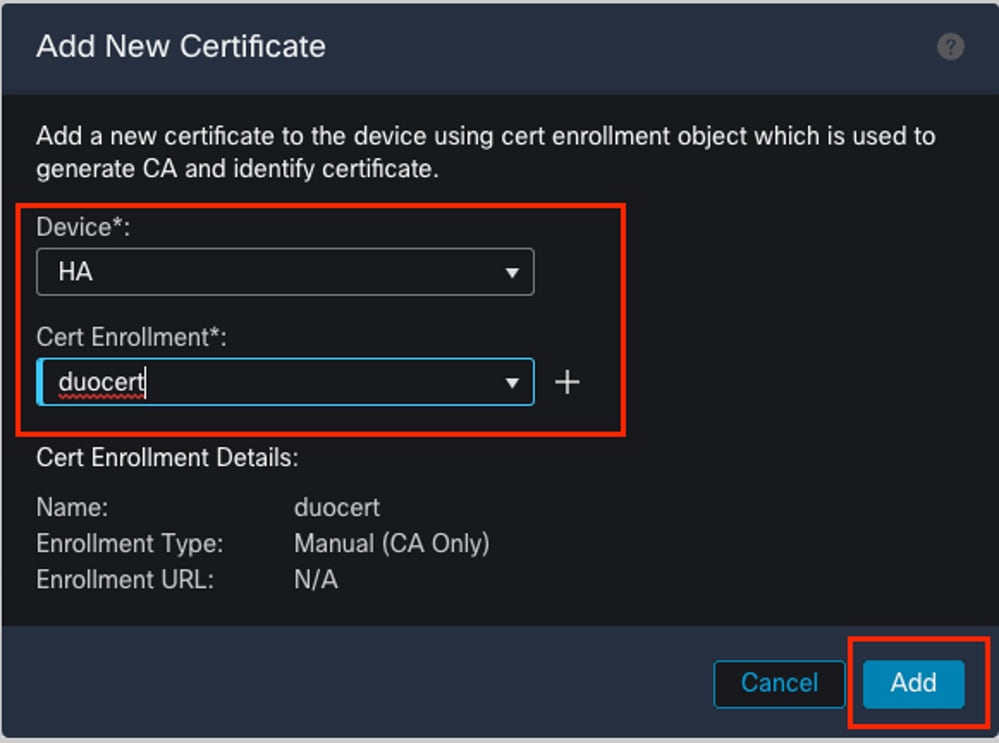
Configure Certificate Authentication DUO SAML Authentication Cisco
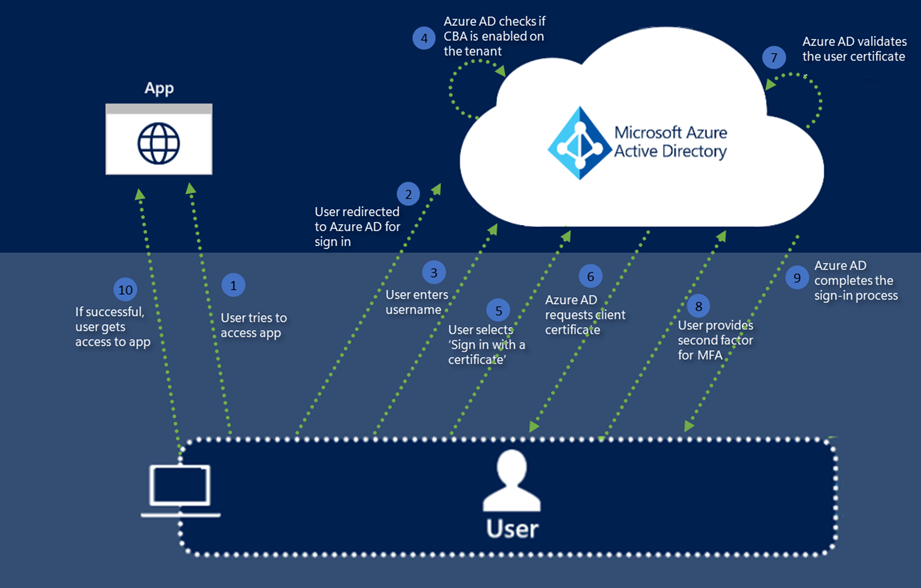
Authentication Certificate
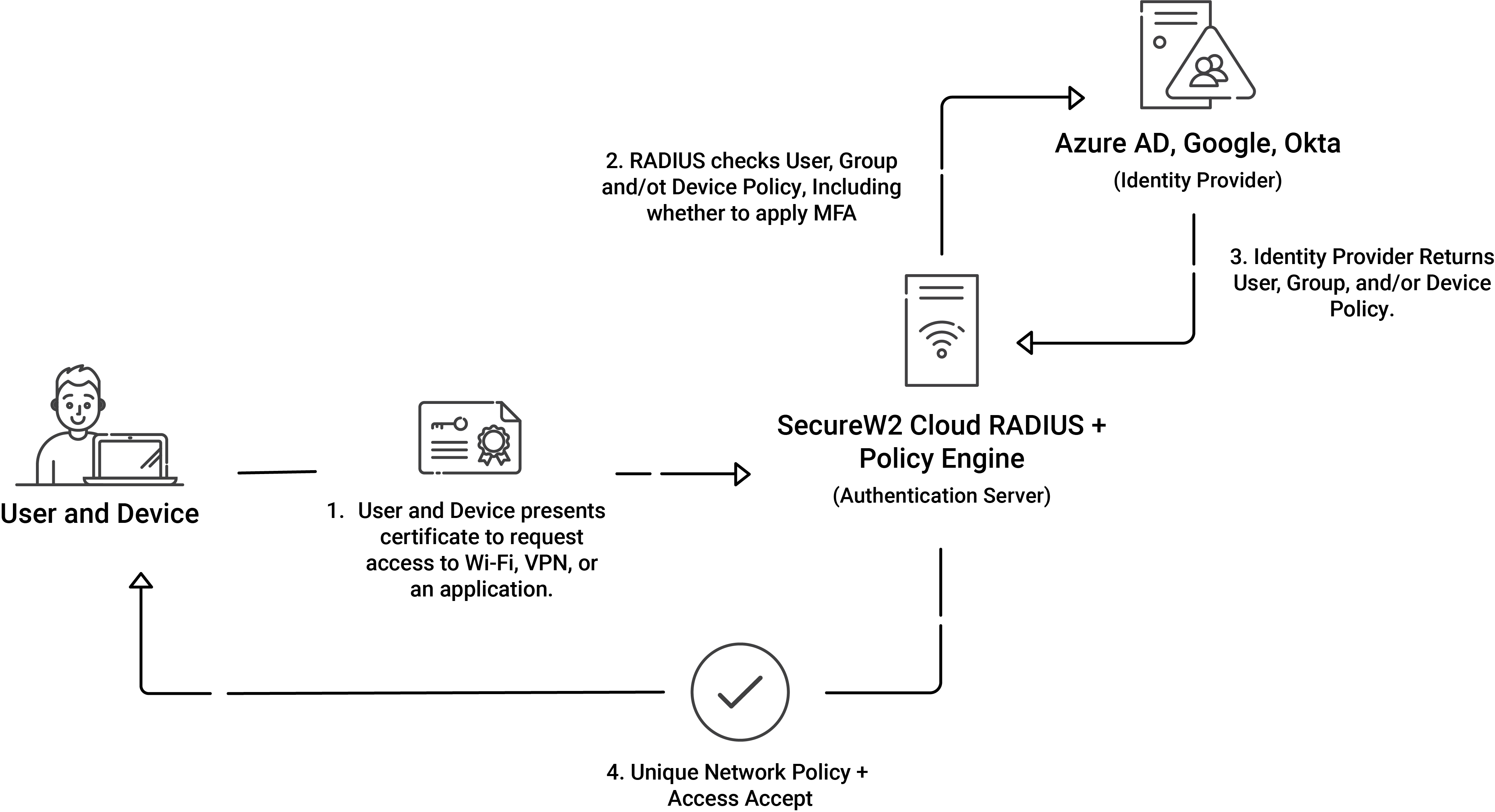
WEP WPA2 and WPA3: What these Wi Fi Settings Mean Cloud RADIUS

How to manage IoT device certificate rotation using AWS IoT The
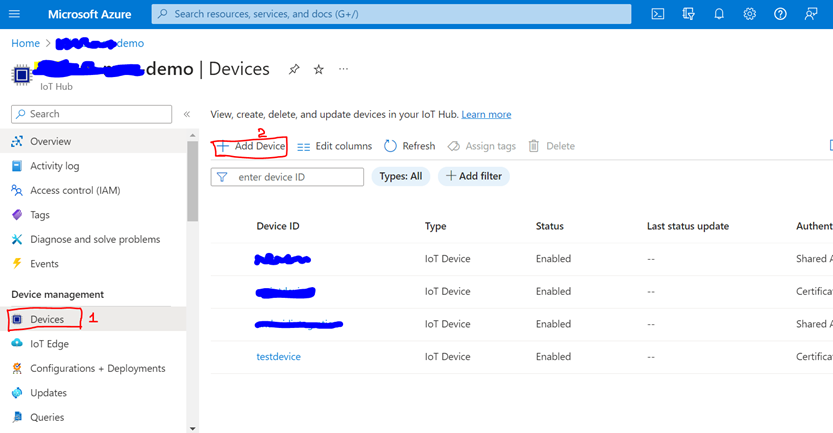
Azure IOT Hub Device Authentication with X 509 Certificate Kotlin
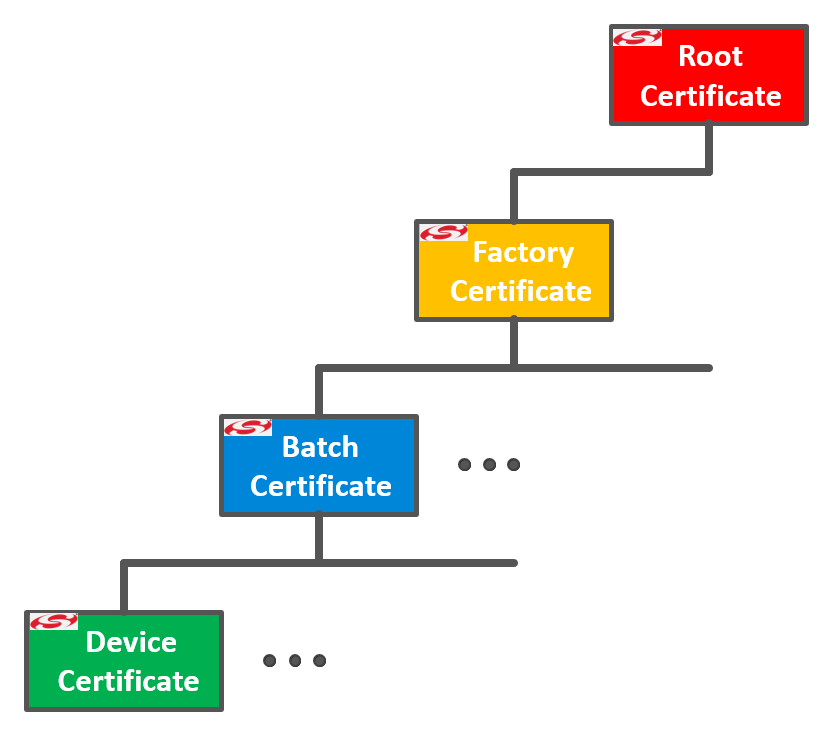
Device Certificate Options Authenticating Silicon Labs Devices using

PAN OS: Authentication Bypass in the Management Web Interface Barikat

Sequence diagram for authentication of a user compatible with OpenID
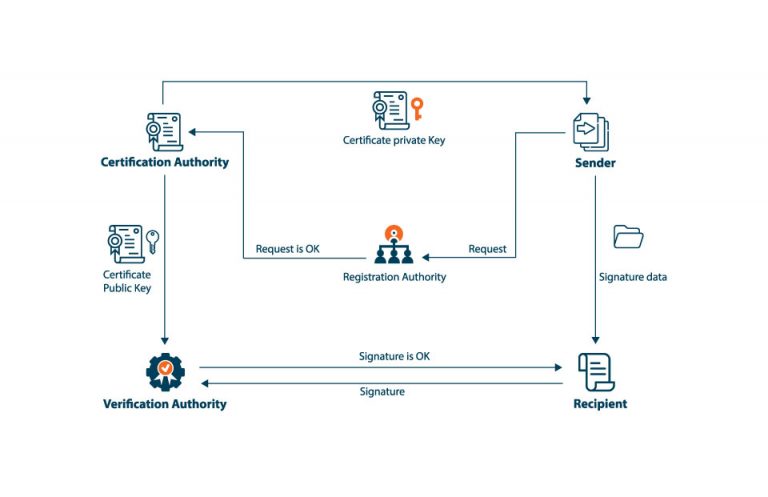
What is a Certificate Authority (CA) in PKI?
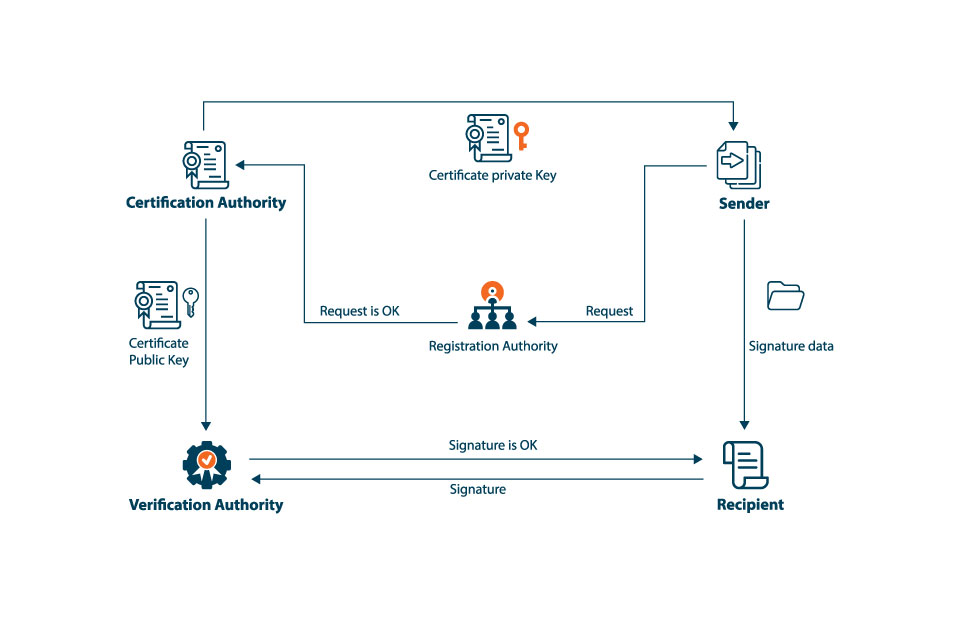
What is a Certificate Authority (CA) in PKI?

Configuring external authentication methods in Microsoft 365 with
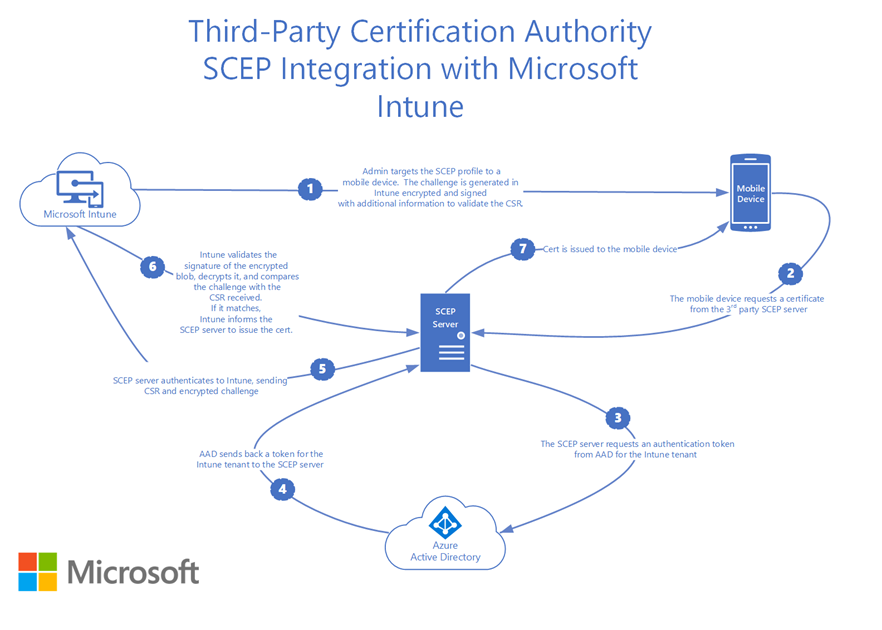
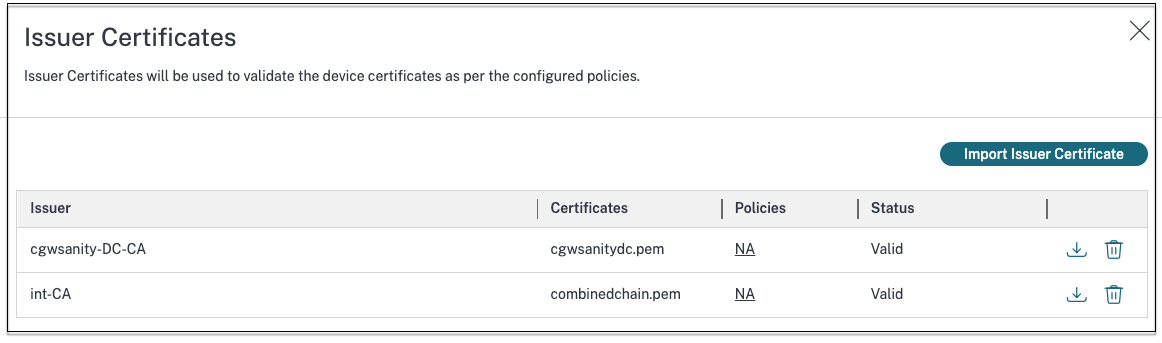
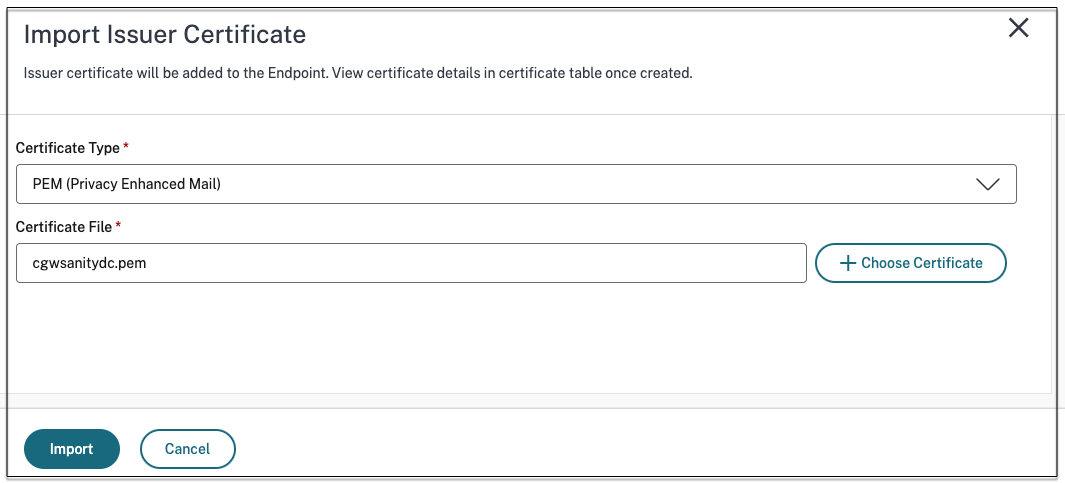
Deep dive of SCEP certificate request/renewal on Intune managed Windows

GlobalProtect Client Certificate Authentication PAN OS 10 0 6 YouTube
.png)
CloudExpro®
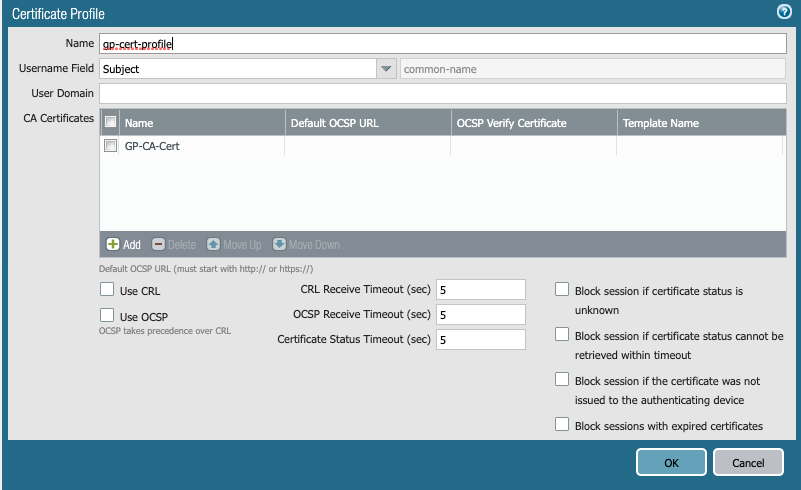
Screenshot displaying where to configure the Certificate Profile found
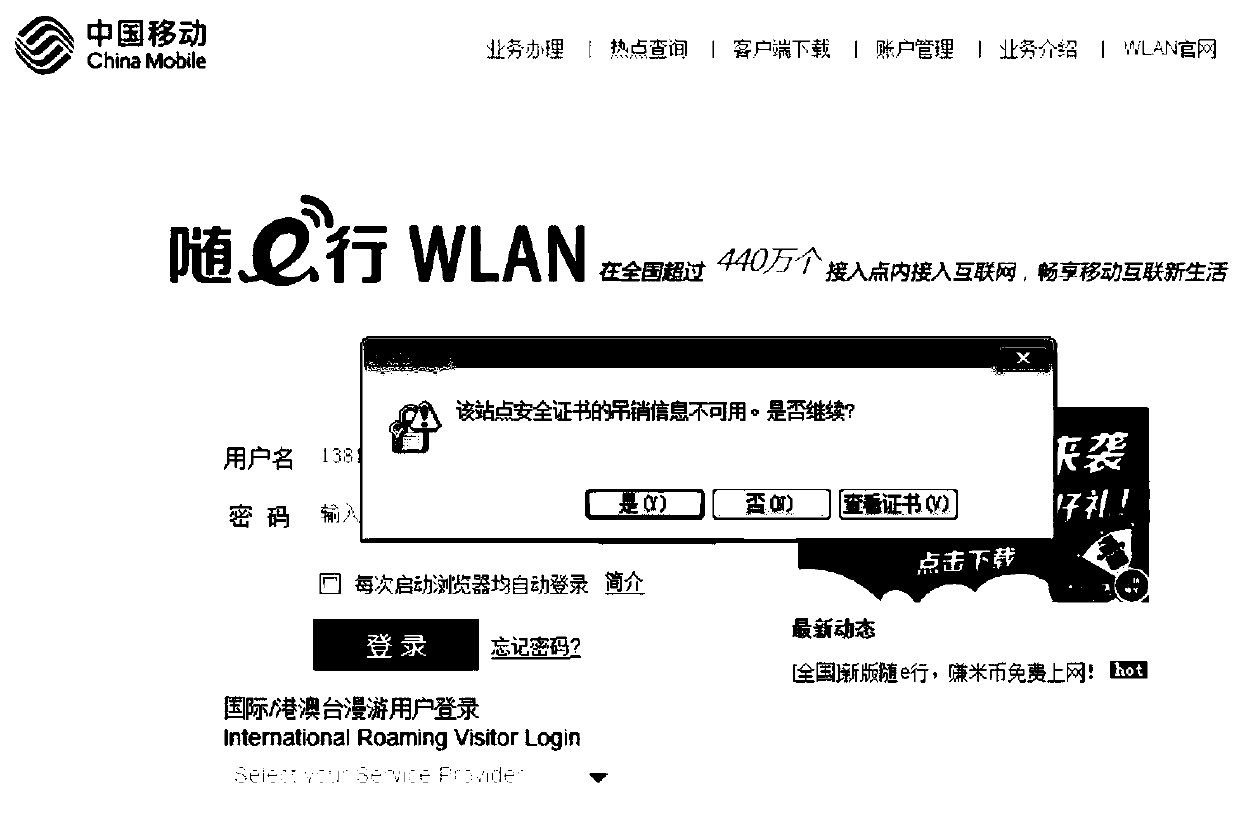
Method and device for certificate authentication Eureka Patsnap

This Or That Template prntbl concejomunicipaldechinu gov co
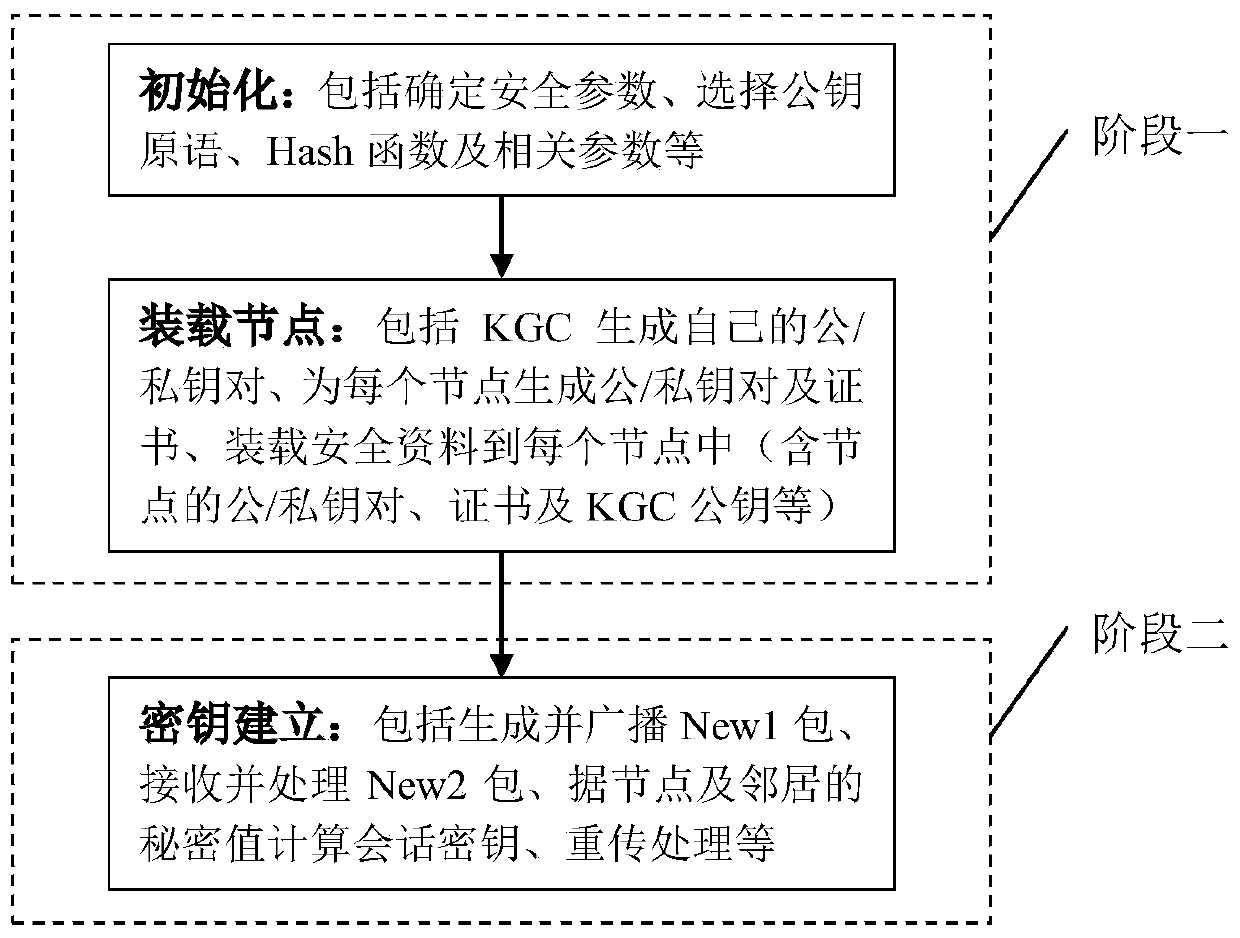
Sensor network authentication key establishment method based on light
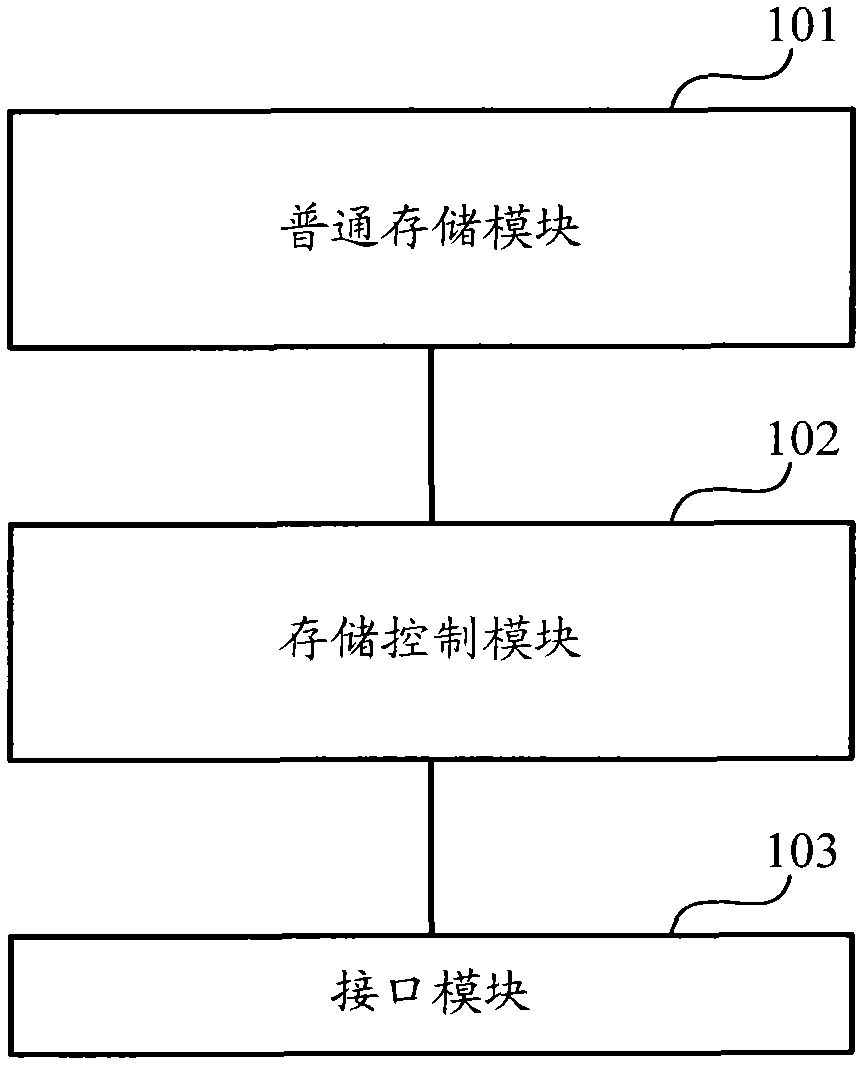
Certificate authentication device as well as access method and
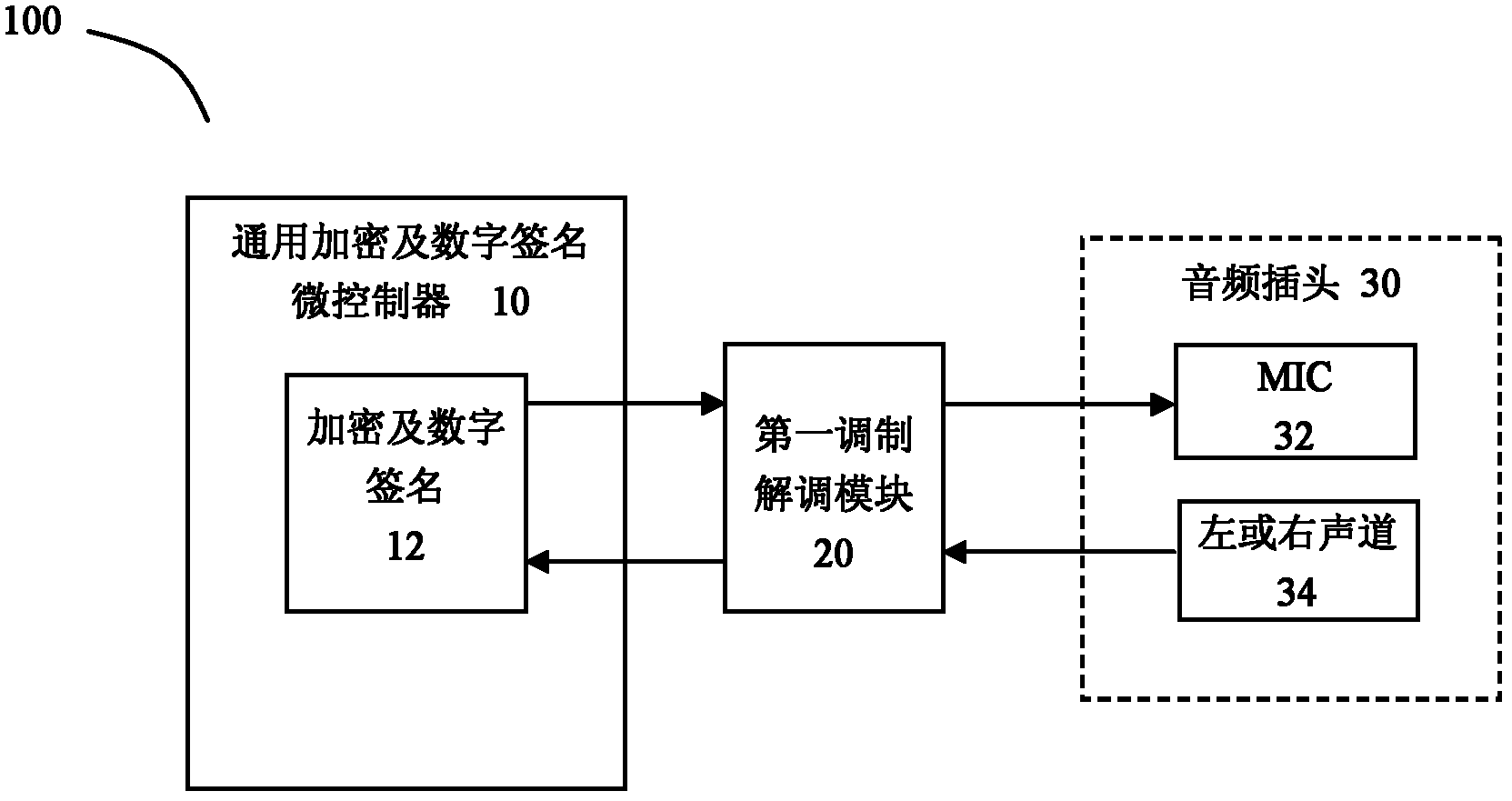
Digital certificate safety lock device and digital certificate
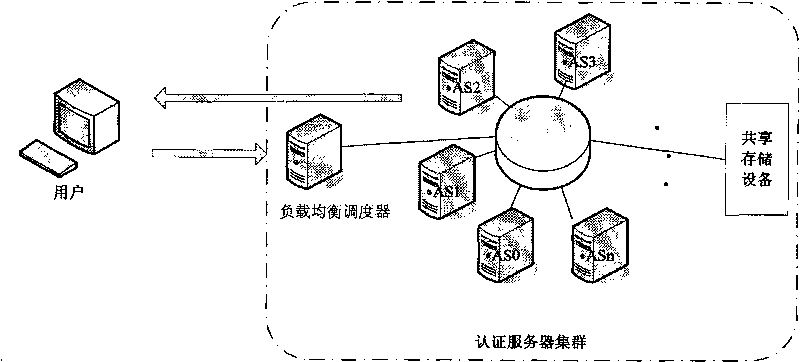
Method and device for changing states of authentication service
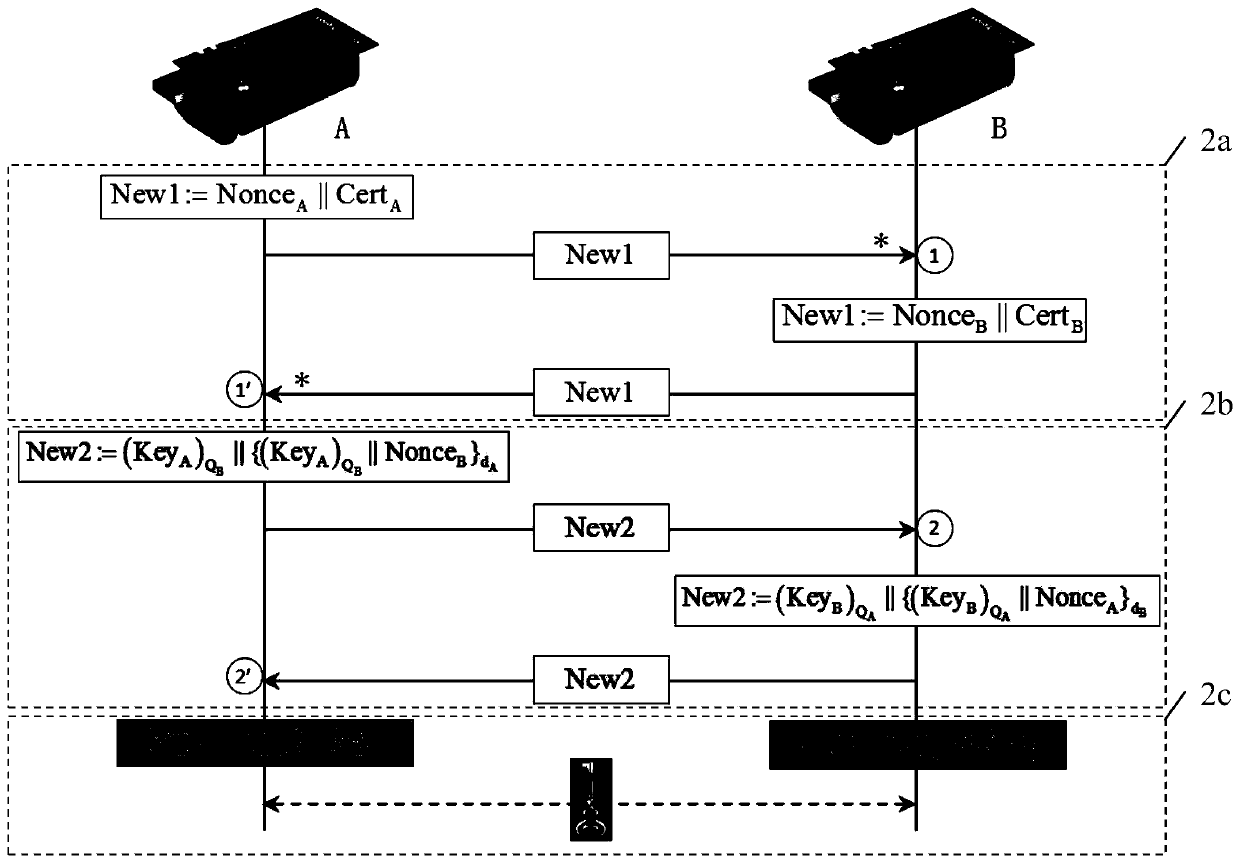
Sensor network authentication key establishment method based on light
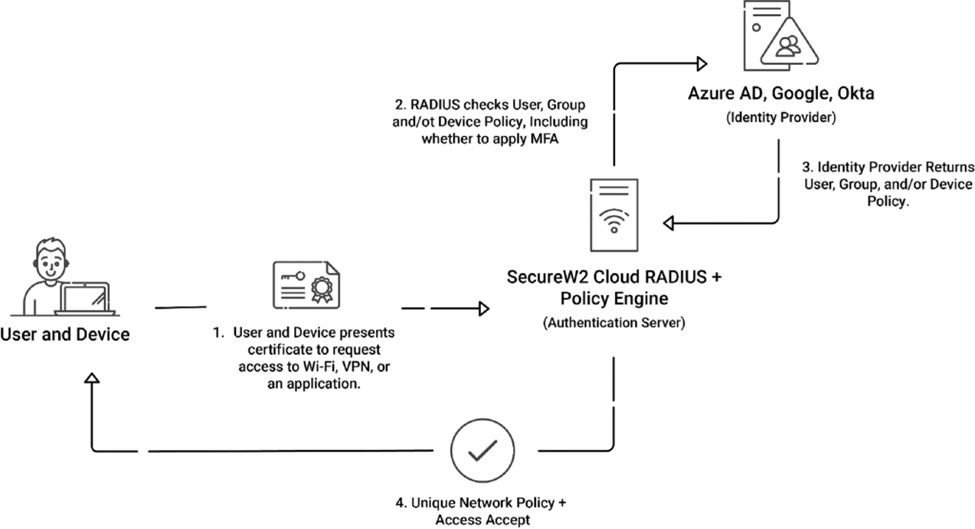
What is an AAA Server? How Does It Work? Cloud RADIUS
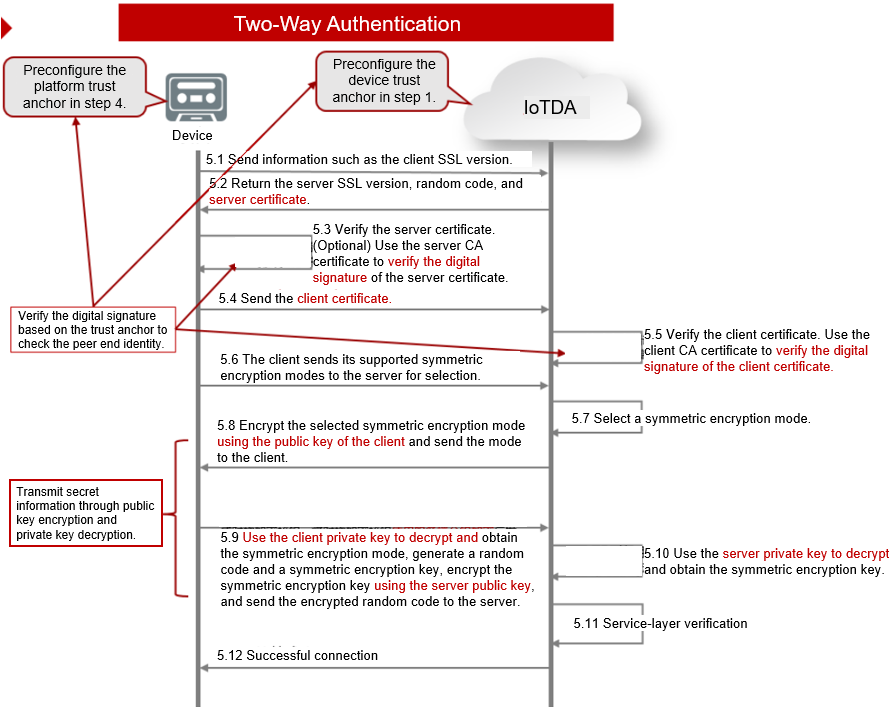
Connecting a Device That Uses the X 509 Certificate Based on MQTT fx
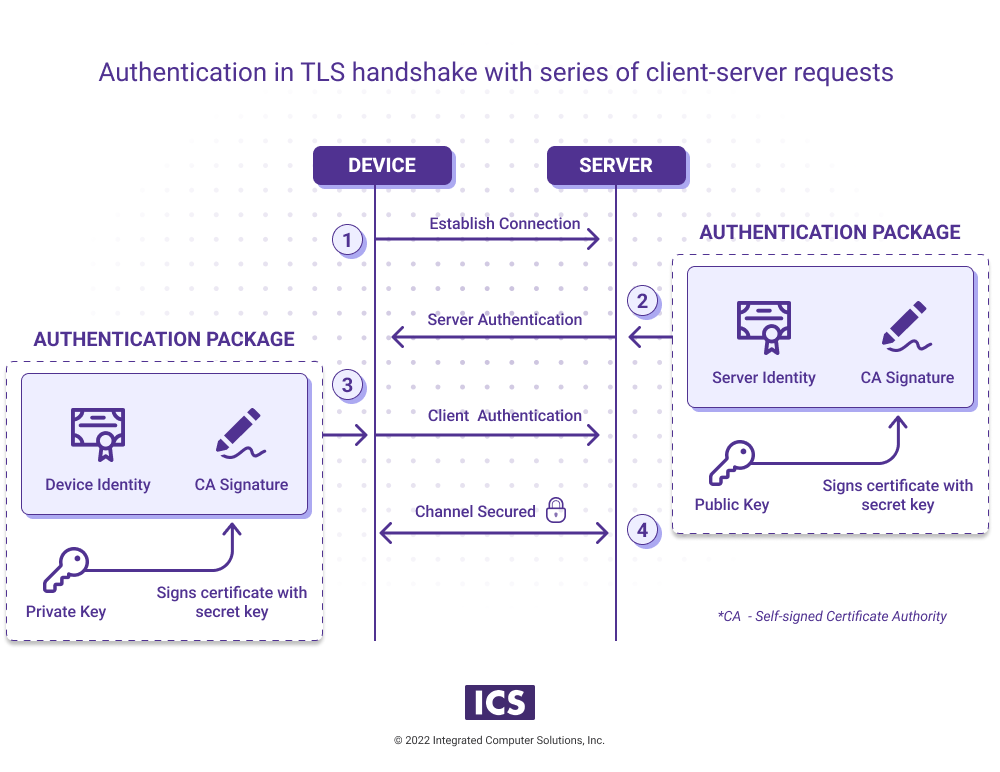
Protect Against Cyber Attacks by Securing Your IoT Devices ICS
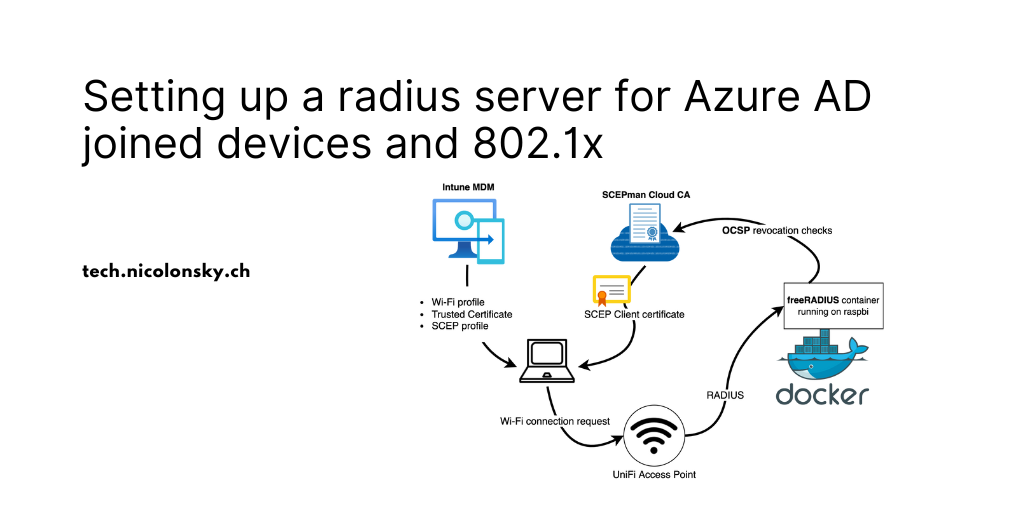
Setting up a radius server for Azure AD joined devices and 802 1x
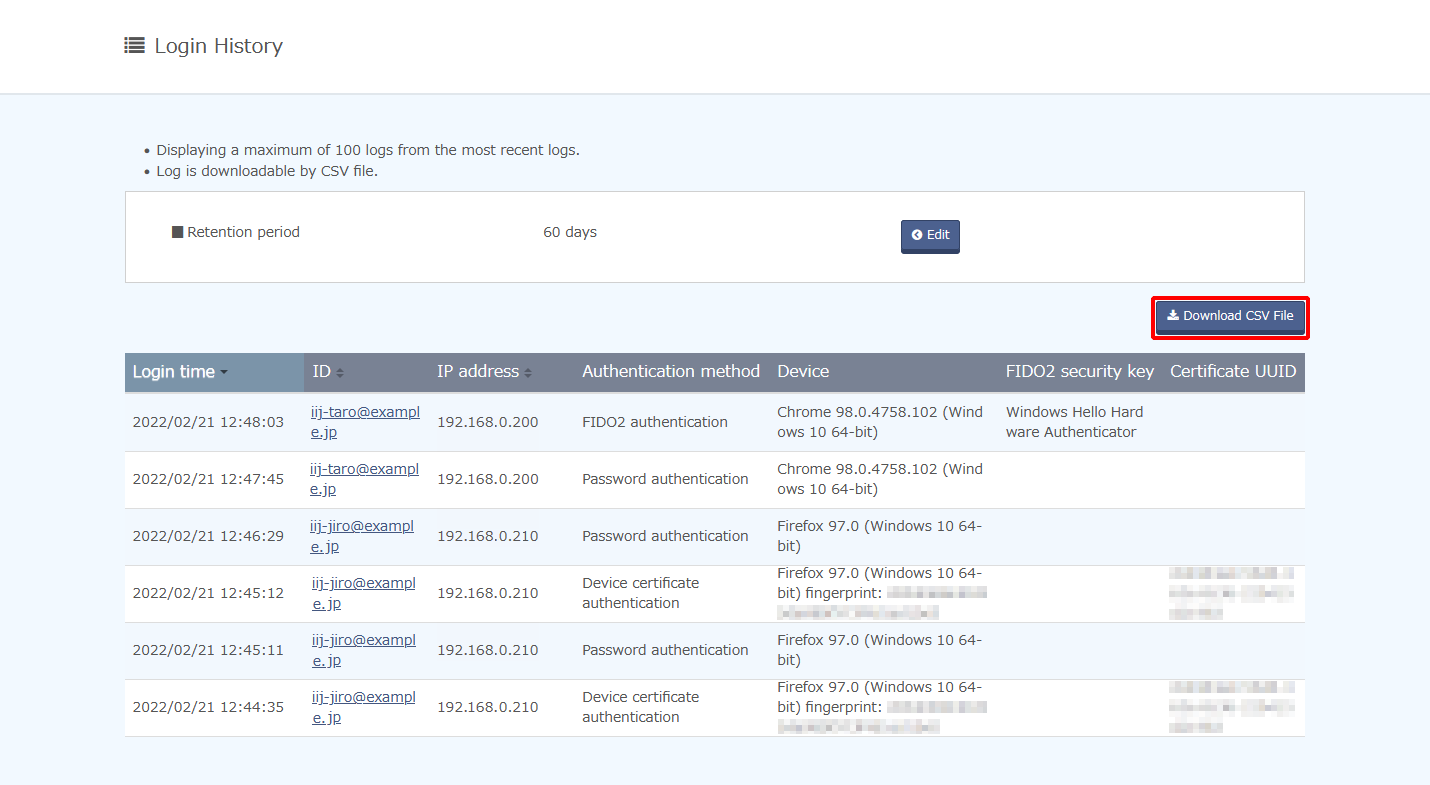
Downloading Login History as CSV Files

Provision Azure IoT Hub devices using DPS and X 509 certificates in ASP

Provision Azure IoT Hub devices using DPS and X 509 certificates in ASP