Encryption Policy Template
Here are some of the images for Encryption Policy Template that we found in our website database.
Encryption Policy TEMPLATE V1 PDF

Encryption Policy Template FINAL PREVOD PDF

Encryption Policy Template FRSecure
Data Encryption Policy Template ControlCase
IT Security Encryption Standard Policy Template in Word PDF Google

IT Security Encryption Standard Policy Template in Word PDF Google

IT Security Encryption Standard Policy Template in Word PDF Google

IT Security Encryption Standard Policy Template in Word PDF Google

IT Security Encryption Standard Policy Template in Word PDF Google
IT Security Encryption Standard Policy Template in Word PDF Google
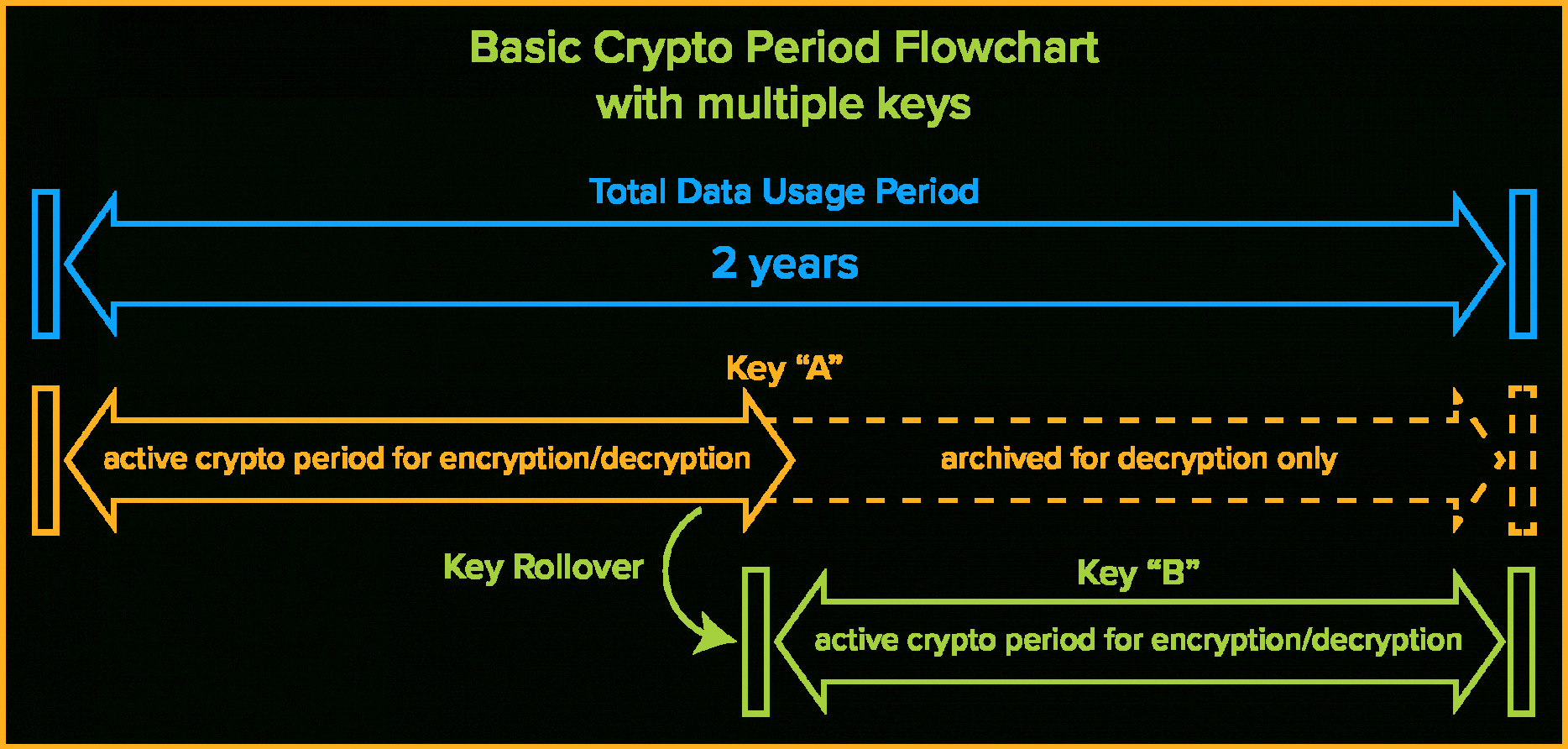
Encryption Key Management Policy Template

Encryption Policy Template

Encryption Policy Template

Encryption Policy Template

Encryption Policy Template
Digital Marketing Agency Data Encryption Policy Template in PDF Word
Digital Marketing Agency Data Encryption Policy Template in PDF Word
Digital Marketing Agency Data Encryption Policy Template in PDF Word

Digital Marketing Agency Data Encryption Policy Template in PDF Word

Digital Marketing Agency Data Encryption Policy Template in PDF Word

Digital Marketing Agency Data Encryption Policy Template in PDF Word
Digital Marketing Agency Data Encryption Policy Template in PDF Word
Digital Marketing Agency Data Encryption Policy Template in PDF Word
Digital Marketing Agency Data Encryption Policy Template in PDF Word

Encryption Policy Template

Encryption Policy Template
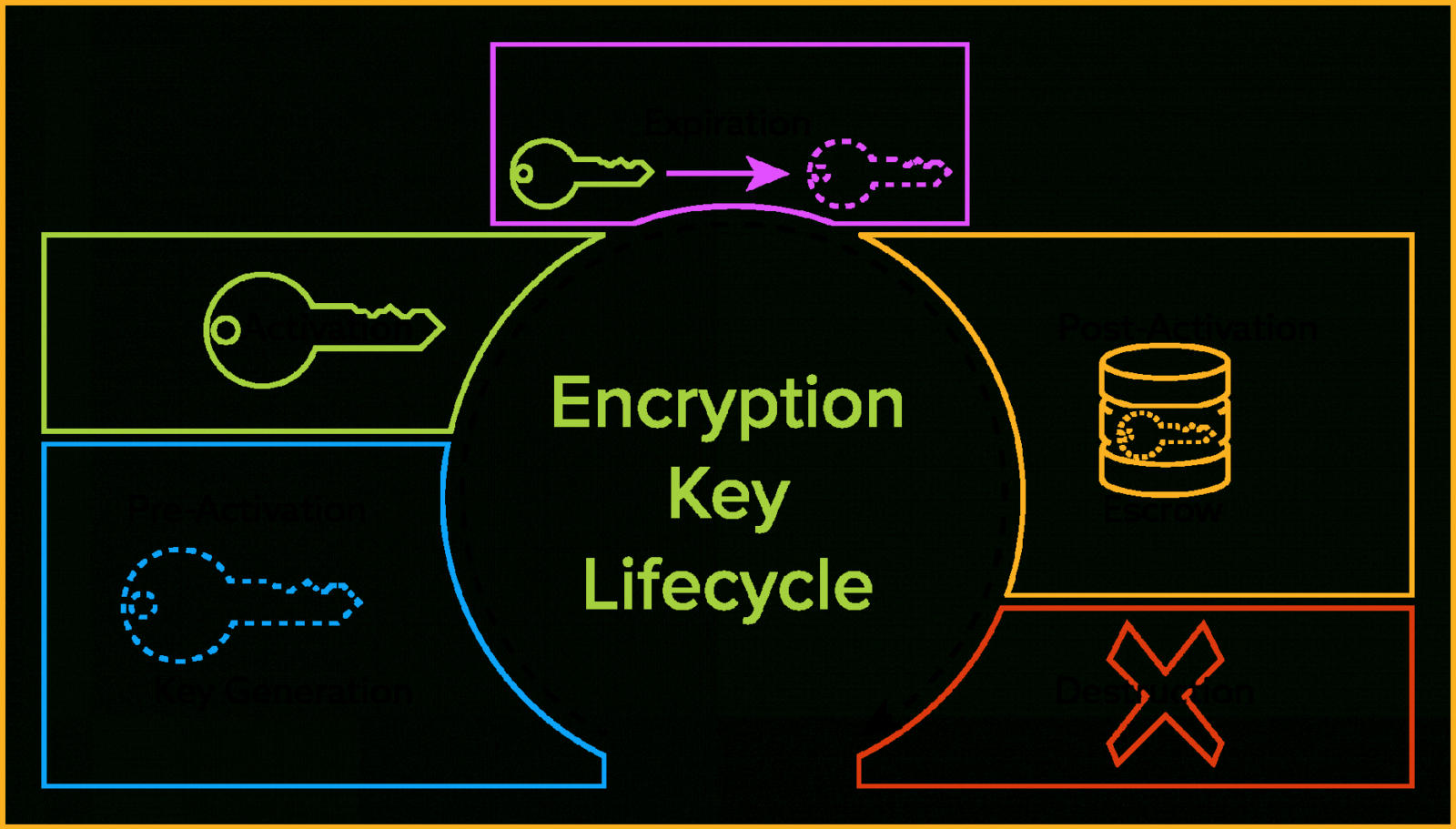
Encryption Policy Template
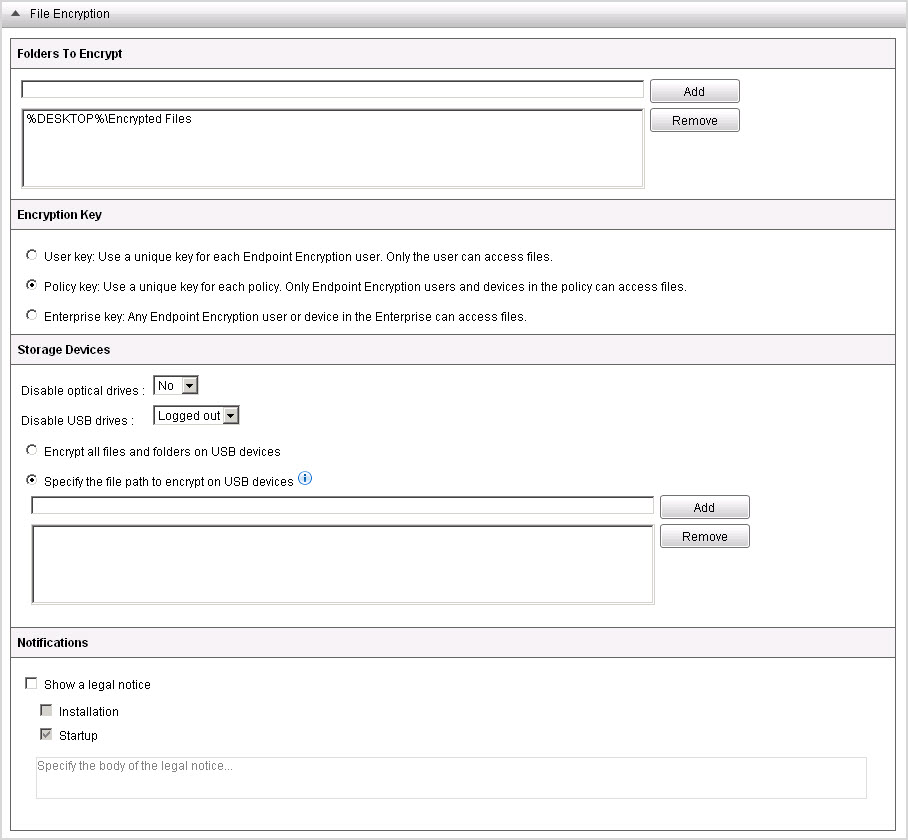
Encryption Policy Template

Encryption Policy Template
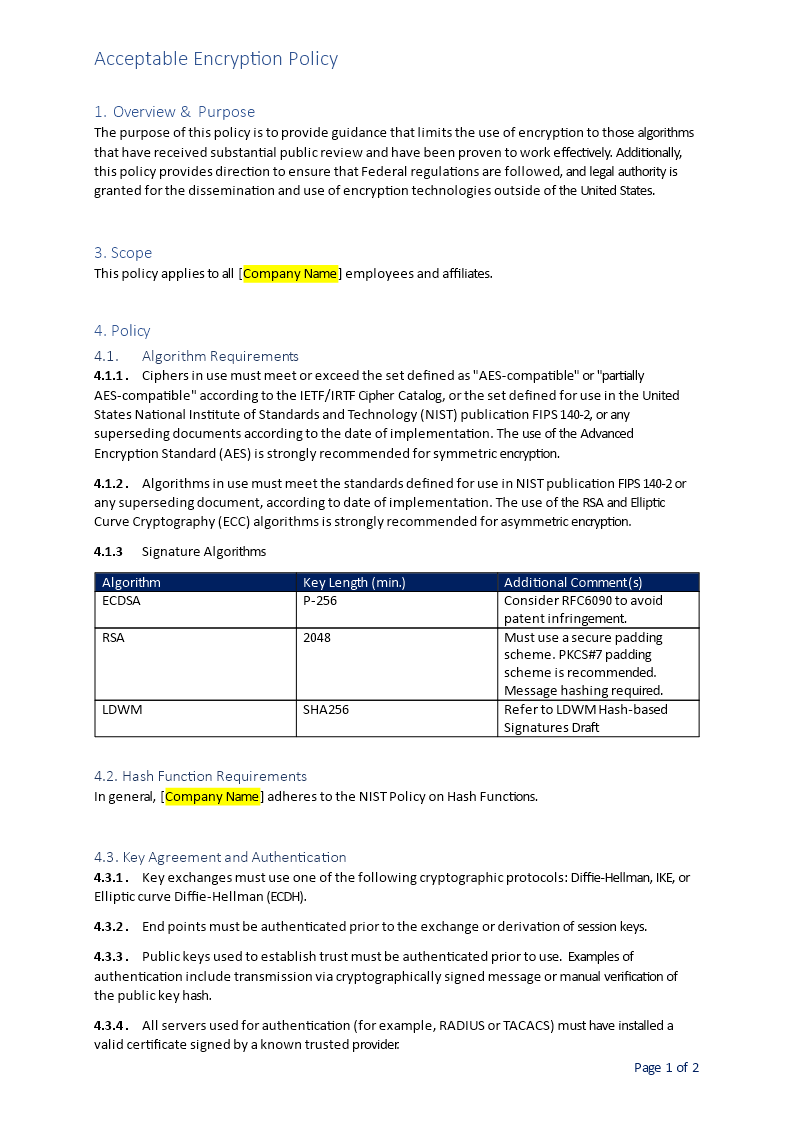
Acceptable Encryption Policy

Data Encryption Policy Template

Data Encryption Policy Template

Data Encryption Policy Template

Data Encryption Policy Template
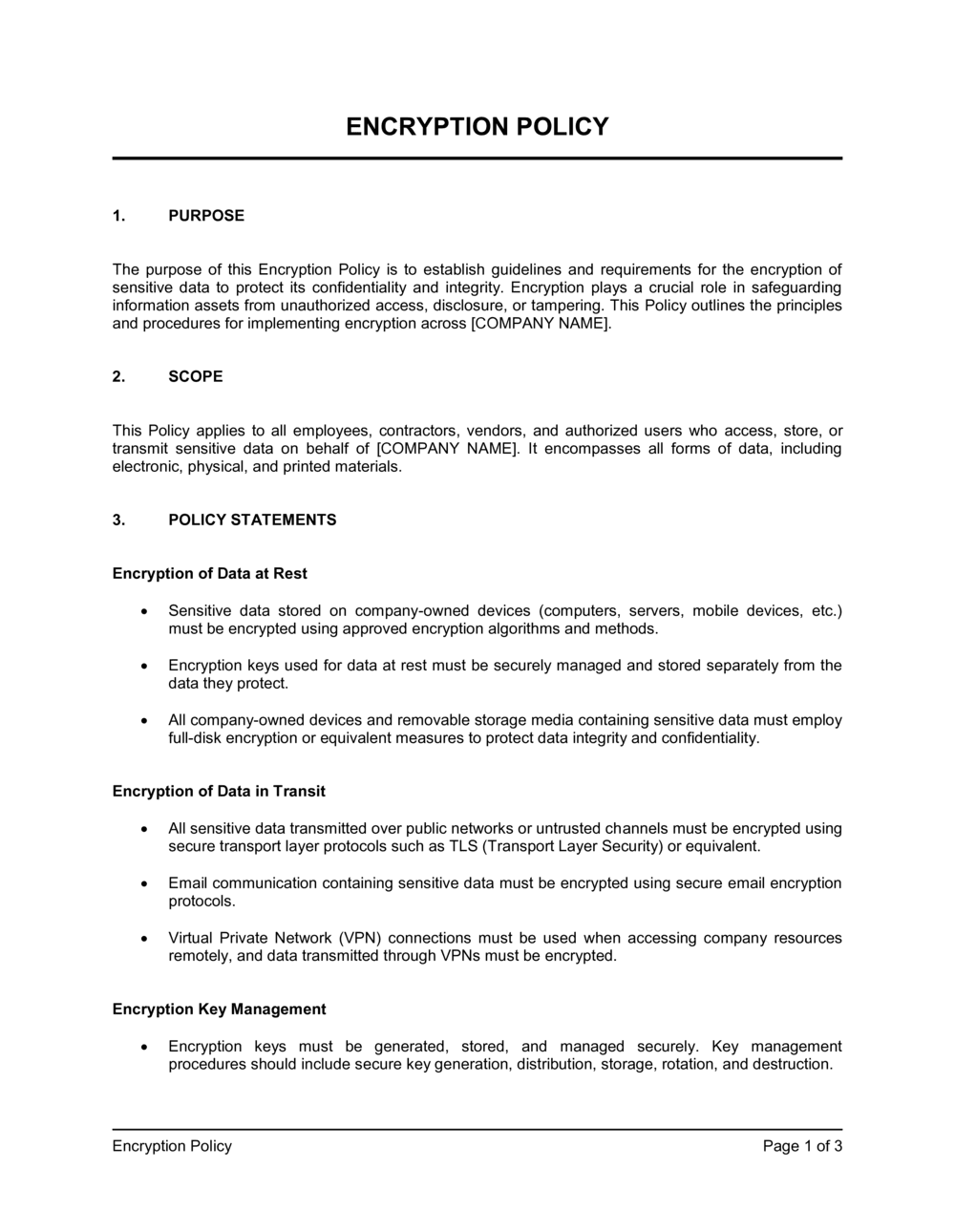
Encryption Policy Template (Word PDF) Free Trial

Encryption Key Management Policy Template

Data Encryption Policy Template Free Downloadable Sample

Free Data Encryption Policy Template Policy template Report template

Data Encryption Policy Template ControlCase

Encryption Policy Template FINAL / encryption policy template final pdf

ISO 27001 Cryptographic Control and Encryption Policy Template

ISO 27001 Cryptographic Control and Encryption Policy Template

ISO 27001 Cryptographic Control Encryption Policy Template Word

ISO 27001 Cryptographic Control Encryption Policy Template Word

ISO 27001 Cryptographic Control Encryption Policy Template Word

ISO 27001 Cryptographic Control Encryption Policy Template Word

ISO 27001 Cryptographic Control Encryption Policy Template Word

Laptop Encryption Policy Encryption Information Sensitivity

Sample Encryption Policy Free Download ProjectPractical com

Data Encryption Policy Update Automation Template Cflow

Management Review Template 4EasyReg

Encryption Policy APPS 2

Best Computer And Email Acceptable Use Policy Template Vondy

Cyber Security Sop Template prntbl concejomunicipaldechinu gov co

Cyber Security Sop Template prntbl concejomunicipaldechinu gov co
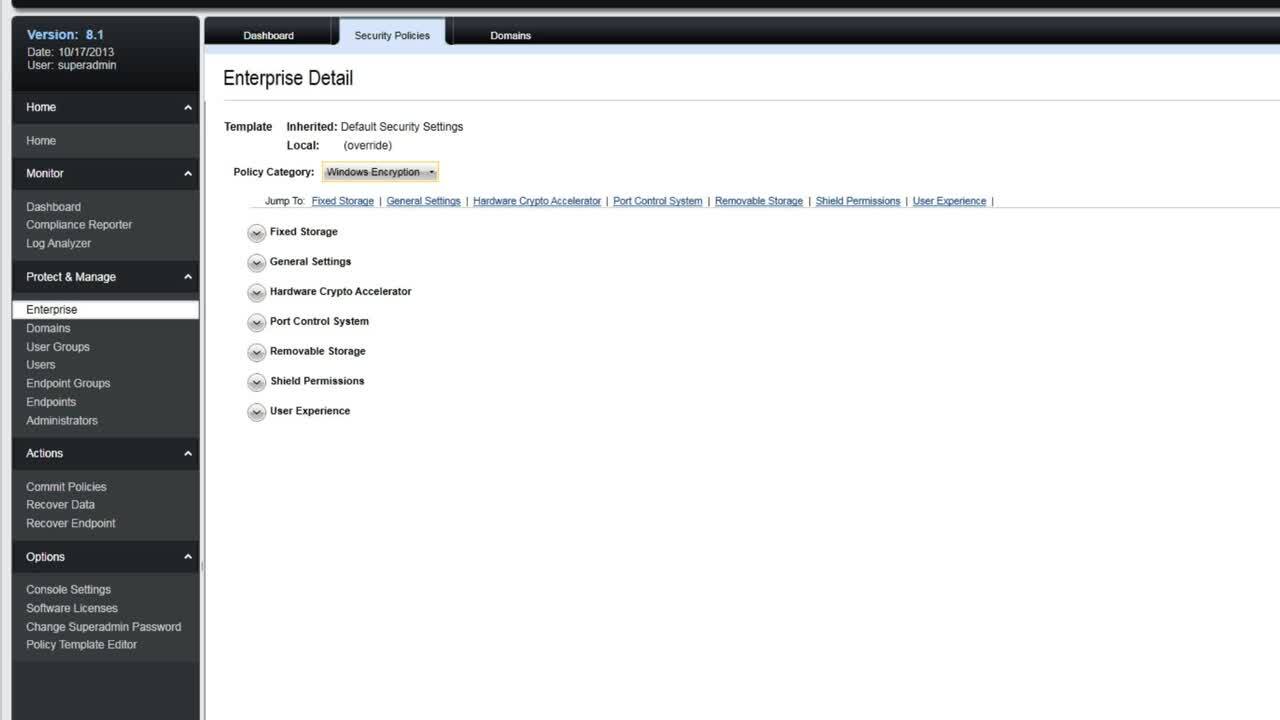
How to Configure Encryption Policies Part 1 Dell Tuvalu

24 Free Security Policy Templates Calypso Tree

ISO 27001 Cryptographic Control and Encryption Policy Template
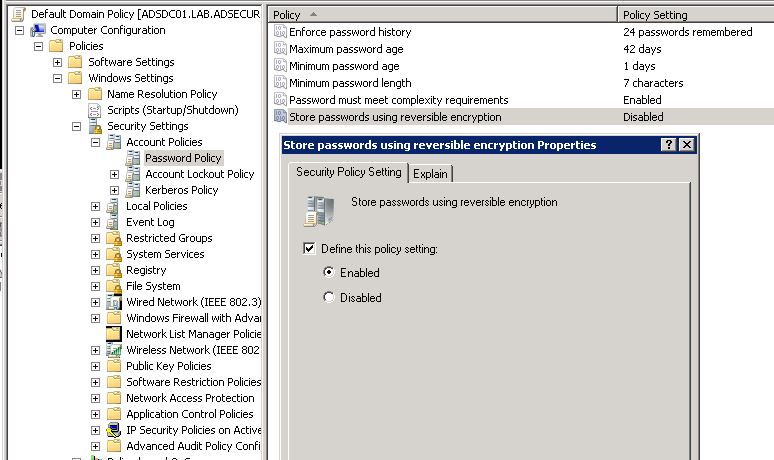
Dump Clear Text Passwords for All Admins in the Domain Using Mimikatz