Endpoint Security Policy Template
Here are some of the images for Endpoint Security Policy Template that we found in our website database.

Endpoint Security Policy Template PDF
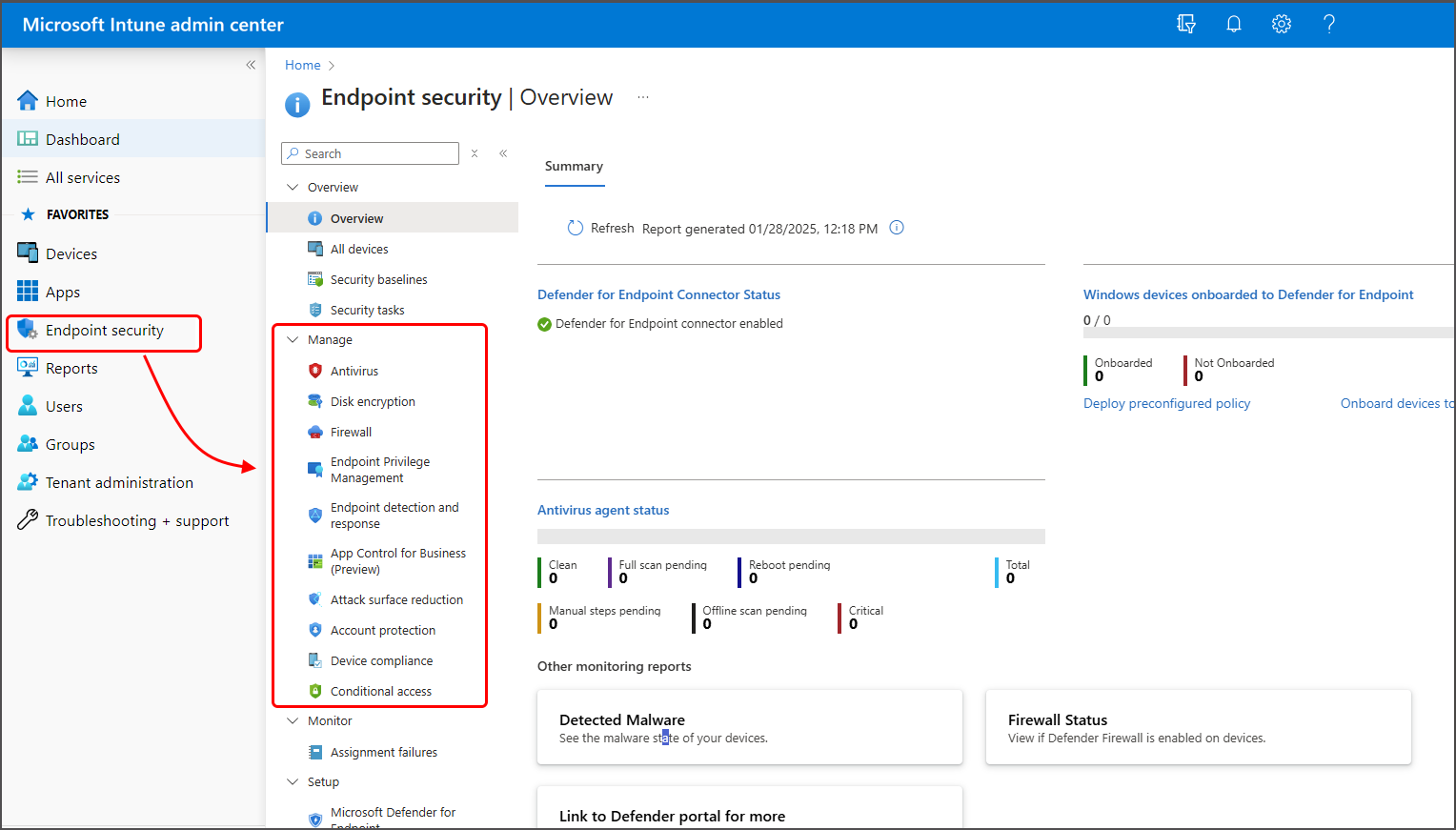
Endpoint Security Policy Template

Endpoint Security Policy Template
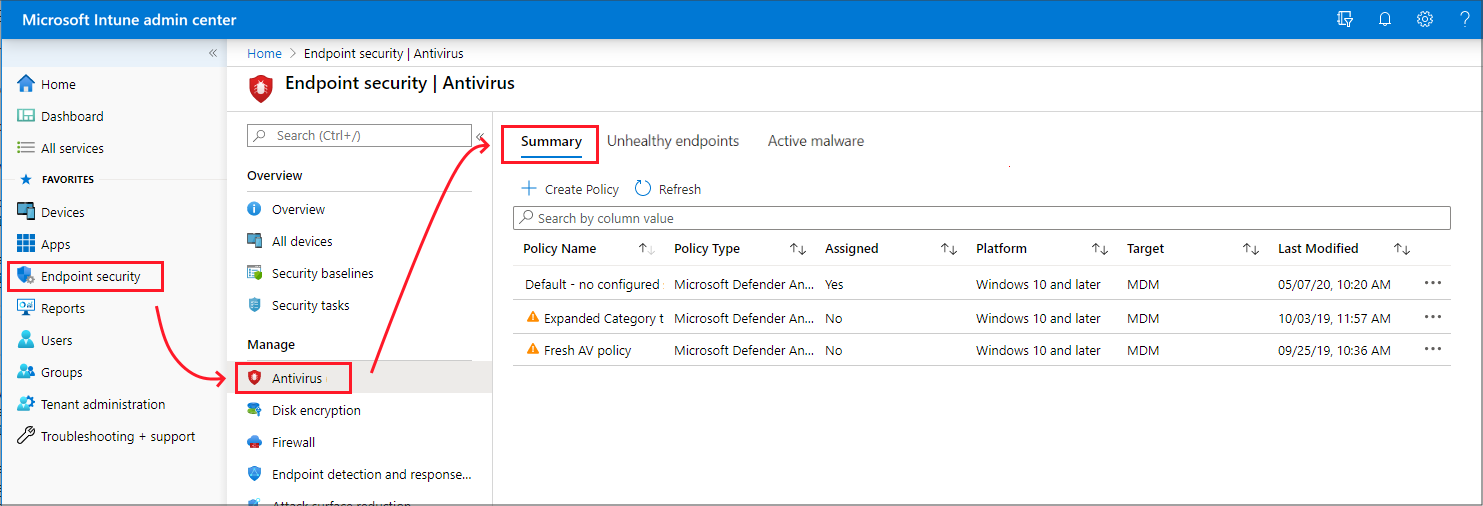
Endpoint Security Policy Template
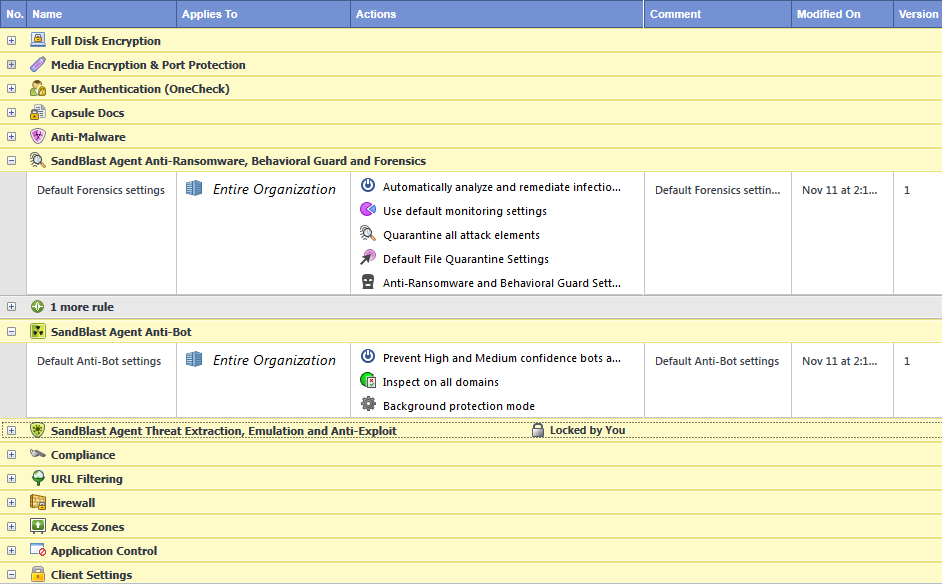
Endpoint Security Policy Template

Endpoint Security Policy Template
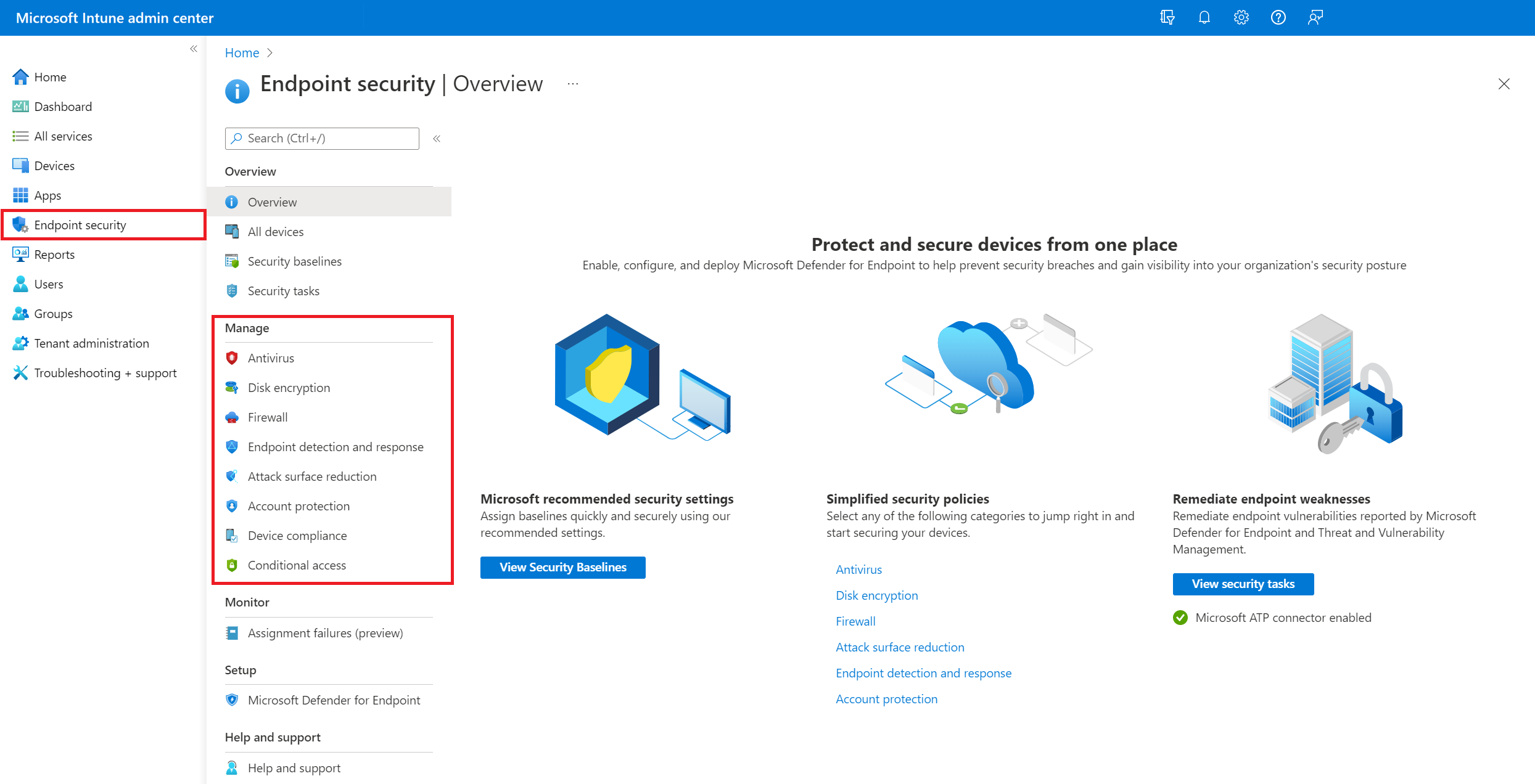
Endpoint Security Policy Template

Endpoint Security Policy Template
Endpoint Security Policy Template
Endpoint Security Policy Template

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online
Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Security Policy Templates to Edit Online

Free Downloadable Endpoint Security Policy Template

Free Downloadable Endpoint Security Policy Template

Free Downloadable Endpoint Security Policy Template
Free Downloadable Endpoint Security Policy Template

Free Downloadable Endpoint Security Policy Template

Free Downloadable Endpoint Security Policy Template

Free Cloud Security Policy Layout Template to Edit Online
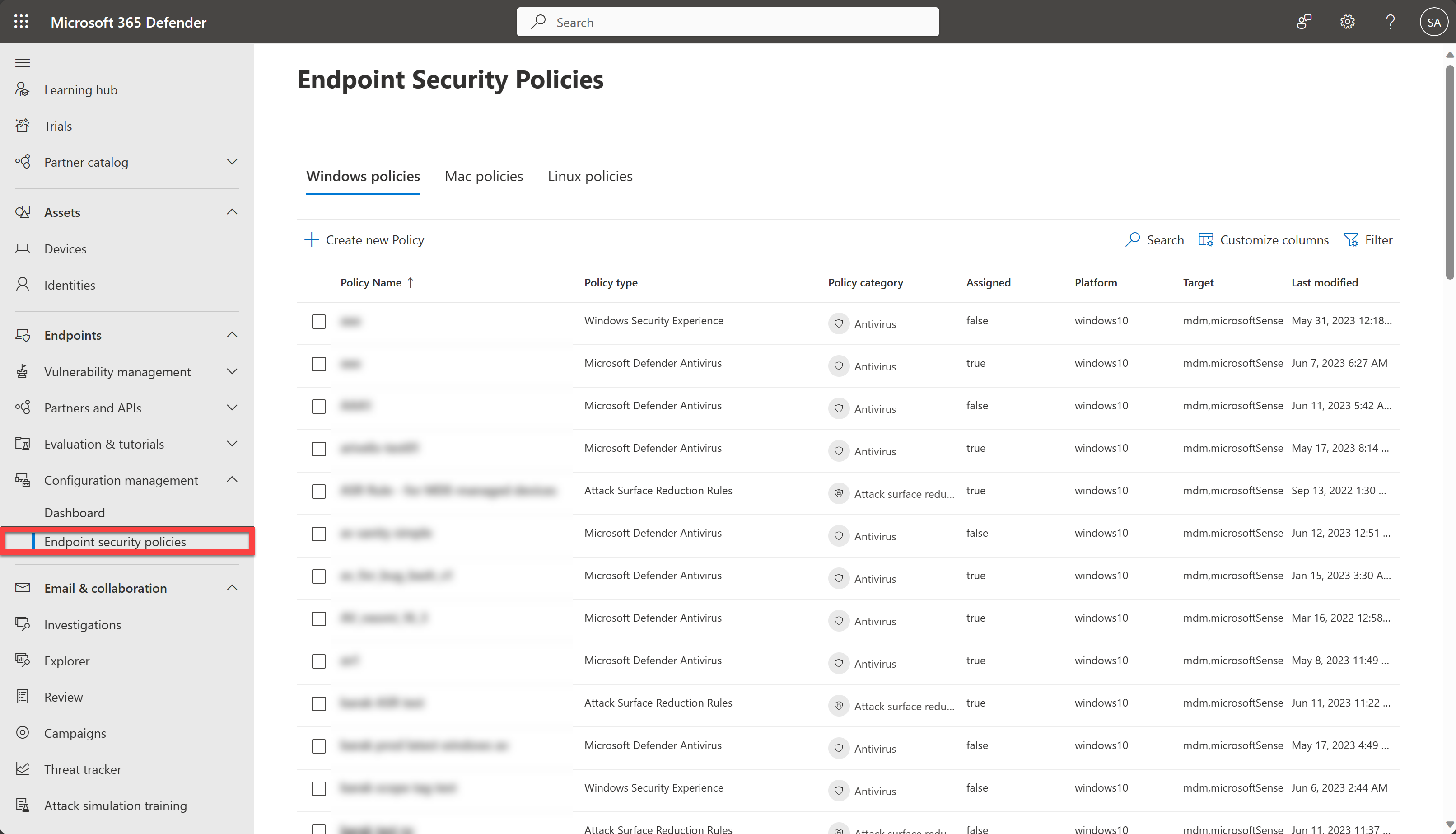
Manage endpoint security policies in Microsoft Defender for Endpoint

Free PCI Compliance Policy Template to Edit Online

Free PCI Compliance Policy Template to Edit Online
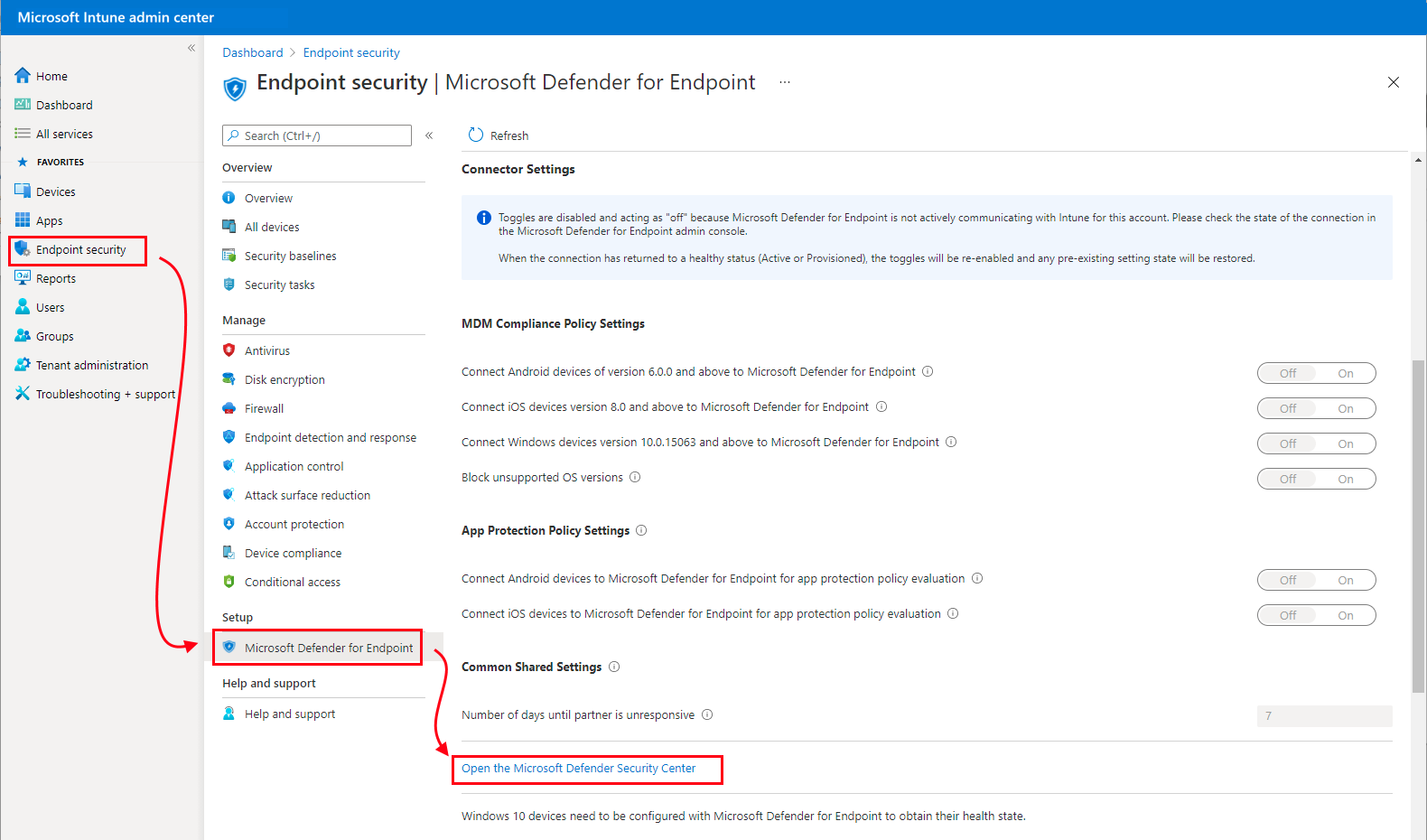
Microsoft Defender For Endpoint Restrict App Execution Ciaops Free

Cybersecurity Organizations Agencies Security Associations

Endpoint Security Tutorial #2 Microsoft Security Compliance Toolkit
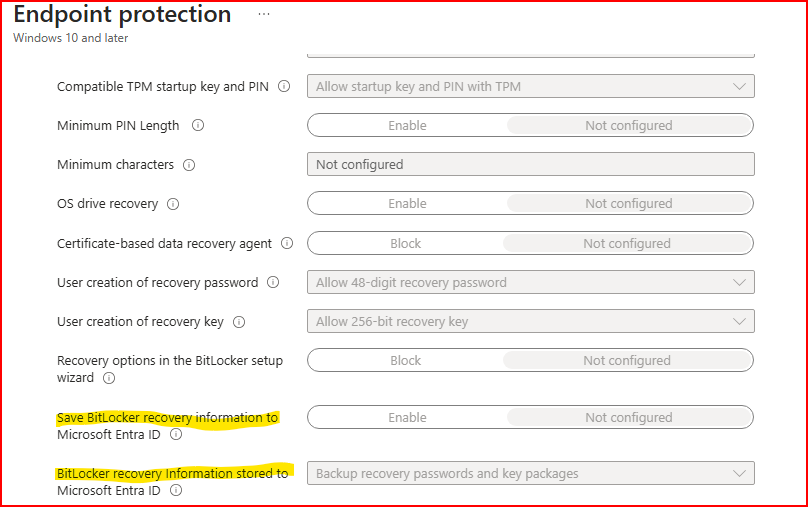
How to configuring Disk Encryption Recovery Backup in Entra ID Using
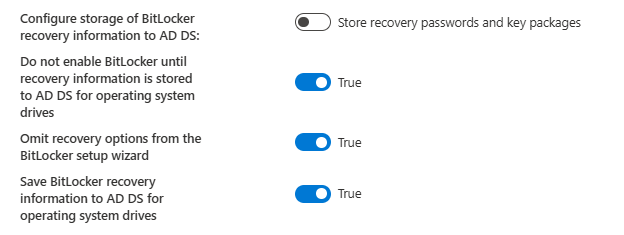
How to configuring Disk Encryption Recovery Backup in Entra ID Using
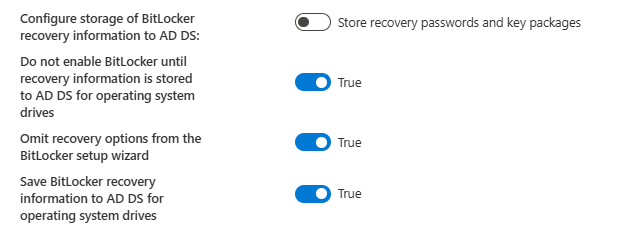
How to configuring Disk Encryption Recovery Backup in Entra ID Using
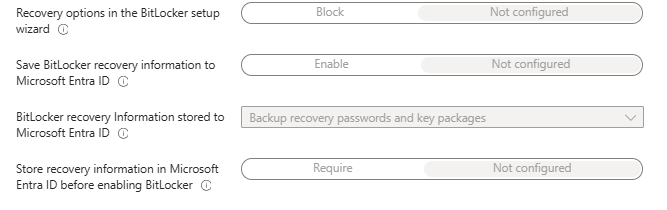
How to configuring Disk Encryption Recovery Backup in Entra ID Using