Insider Threat Policy Template
Here are some of the images for Insider Threat Policy Template that we found in our website database.
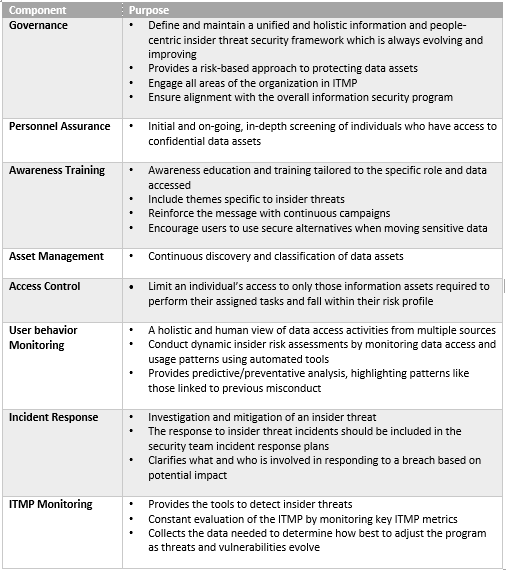
Insider Threat Policy Template
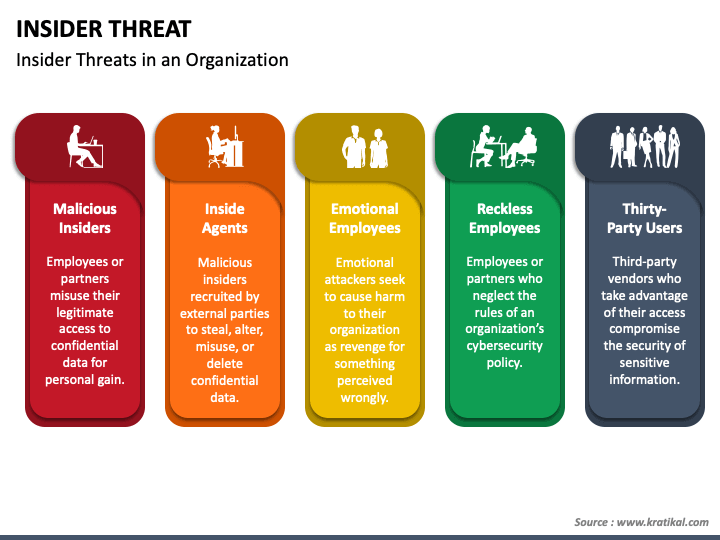
Insider Threat Policy Template

Insider Threat Policy Template

Insider Threat Policy Template

Insider Threat Policy Template
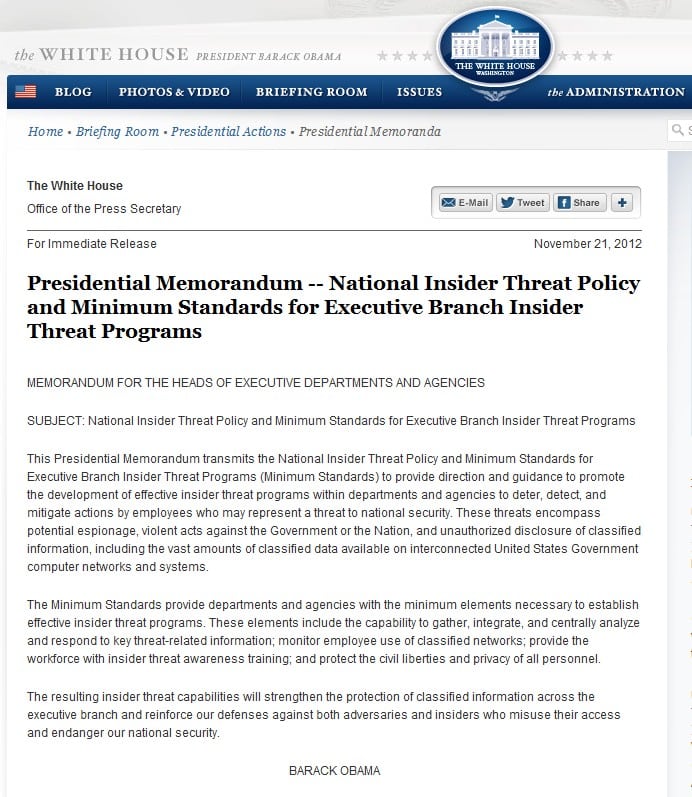
Insider Threat Policy Template
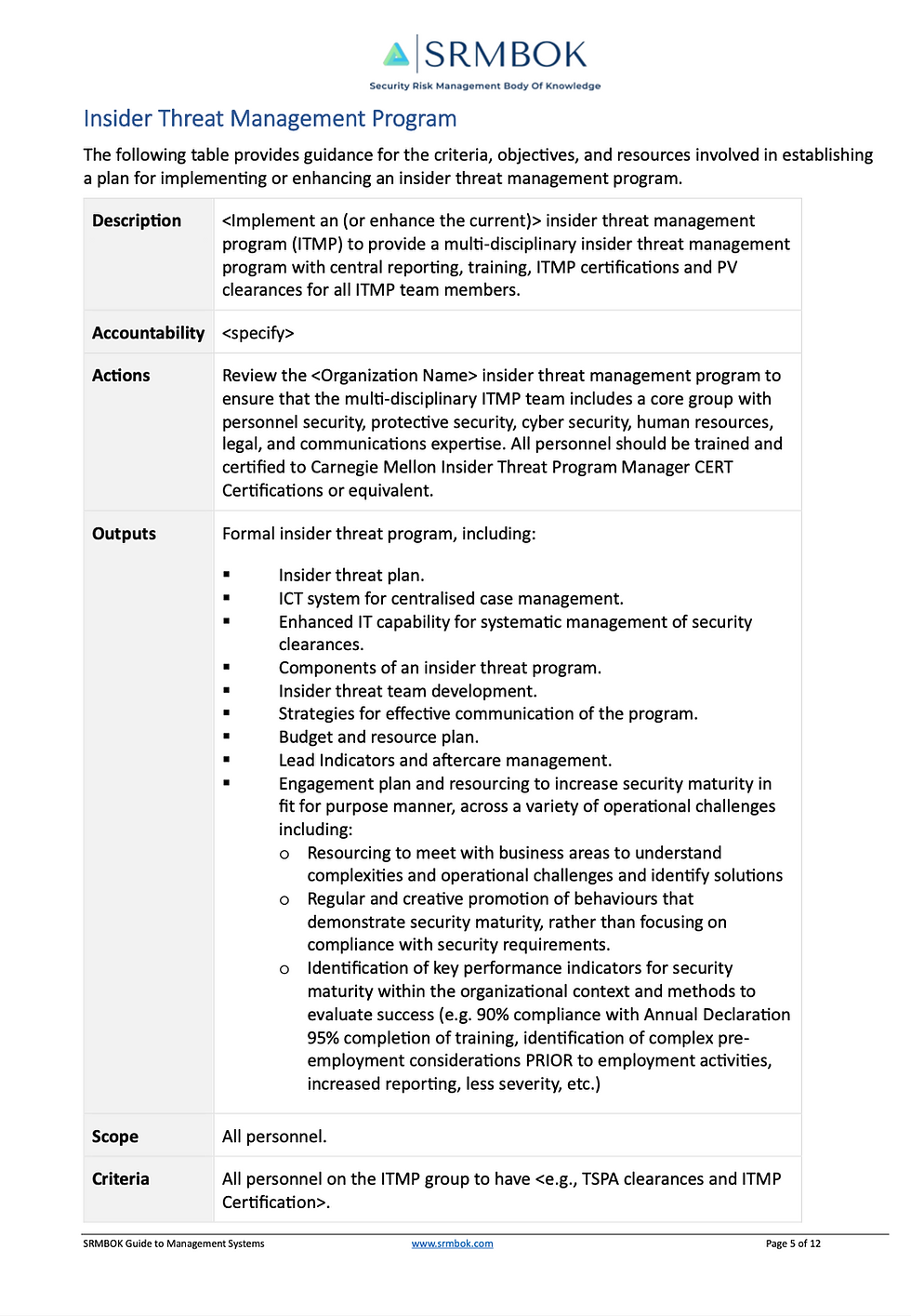
Insider Threat Program Plan Template

Insider Threat Ppt Powerpoint Ppt Template Bundles PPT PowerPoint
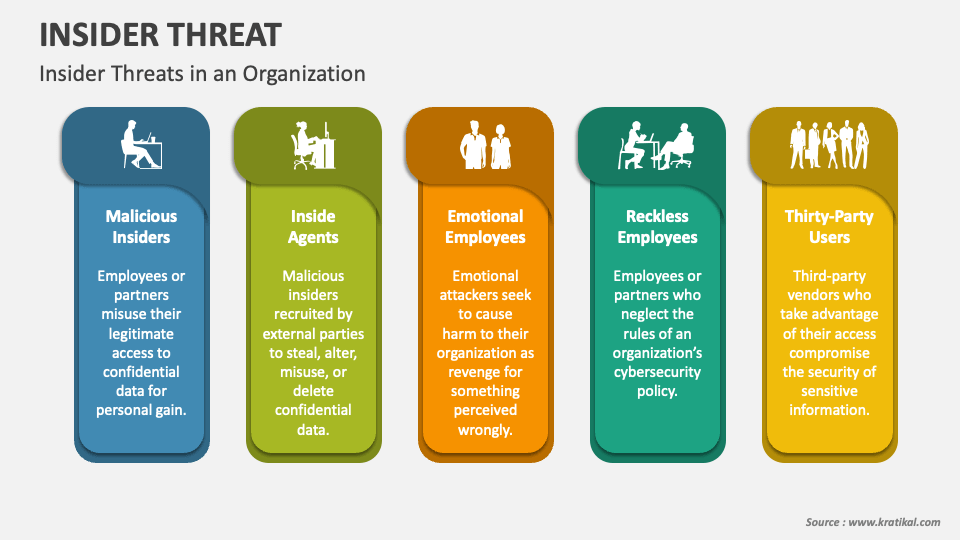
Insider Threat PowerPoint Presentation Slides PPT Template

Insider Threat Program Template

National Insider Threat Policy and Minimum Standards for Executive

Insider Threat Plan Template

Insider Threat Plan Template

Insider Threat Subcommittee

Insider Threats: Risks Identification and Prevention
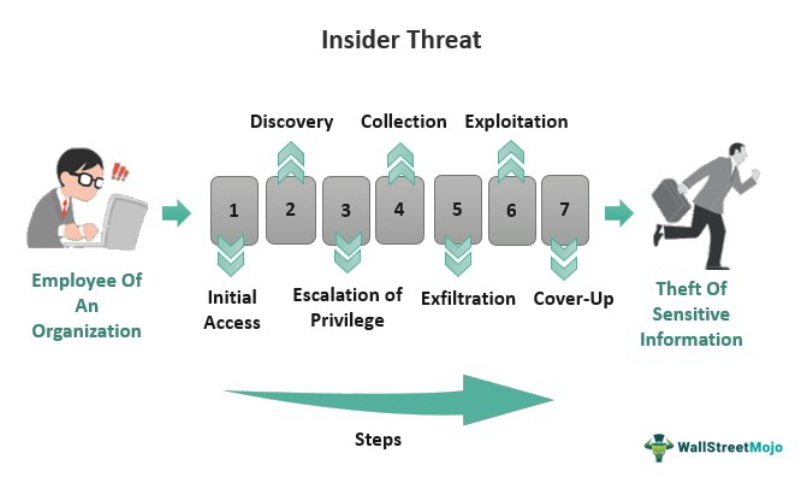
Insider Threat What Is It Indicators Examples Types Prevention

Cybersecurity Threat Intelligence Report Template in Word PDF Google
Insider Threat: Definition Types Examples Protection StrongDM
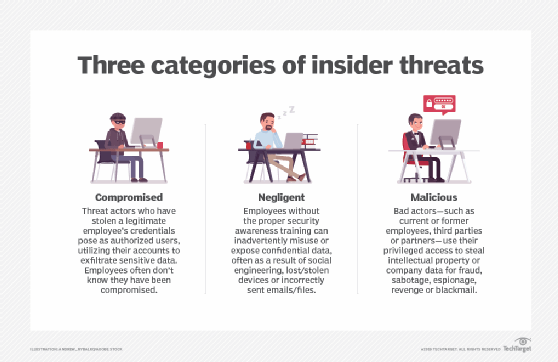
What is an Insider Threat?
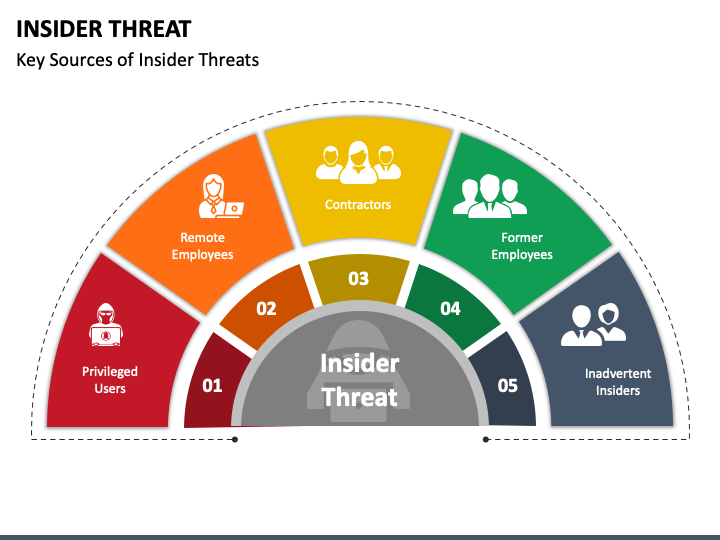
Insider Threat PowerPoint and Google Slides Template PPT Slides

Premium Vector September is national insider threat awareness month

Watchdog critical of DOD insider threat program FedScoop

Free Bomb Threat Emergency Response Plan Template to Edit Online

Fillable Online National Insider Threat Policy and the Minimum

How to Implement an Insider Threat Program

The Early Indicators Of An Insider Threat Digital Guardian

The Early Indicators Of An Insider Threat Digital Guardian

The Early Indicators Of An Insider Threat Digital Guardian
The Early Indicators Of An Insider Threat Digital Guardian
The Early Indicators Of An Insider Threat Digital Guardian

Insider Threat Reporting Templates CISA DC Shari G

Threat Analysis And Risk Assessment Template prntbl
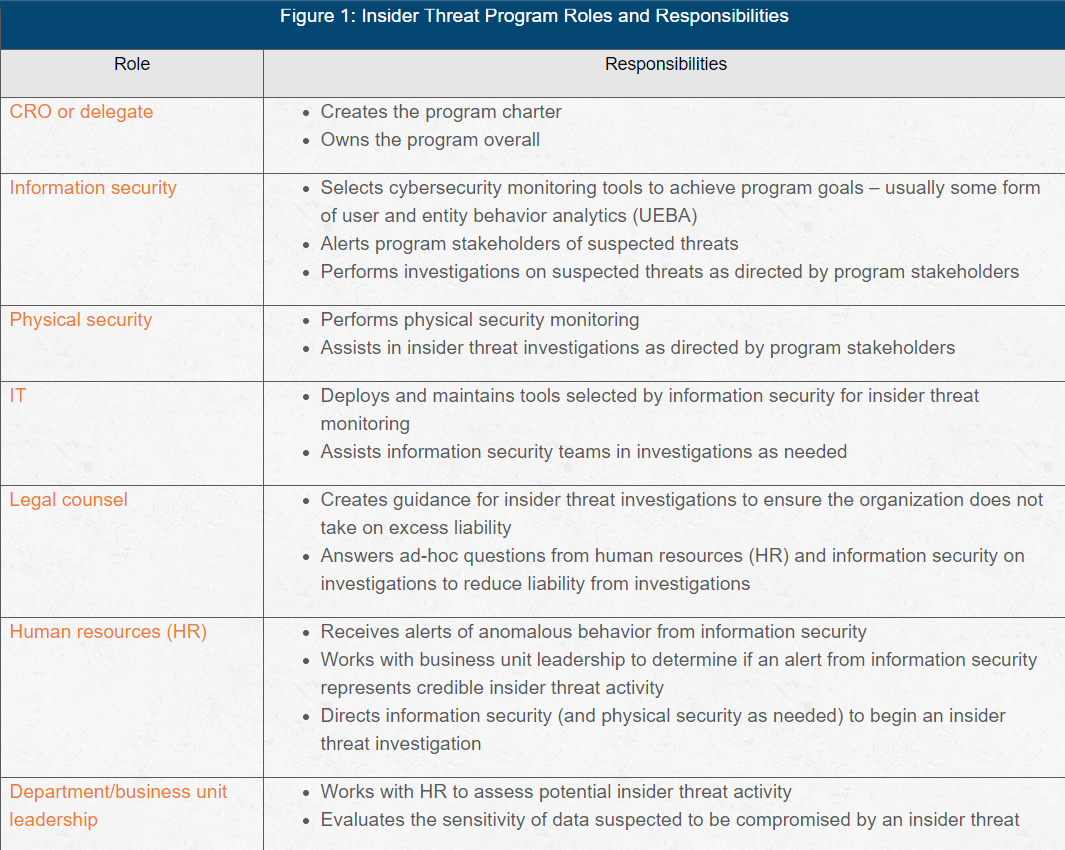
How to Establish an Effective Insider Threat Program
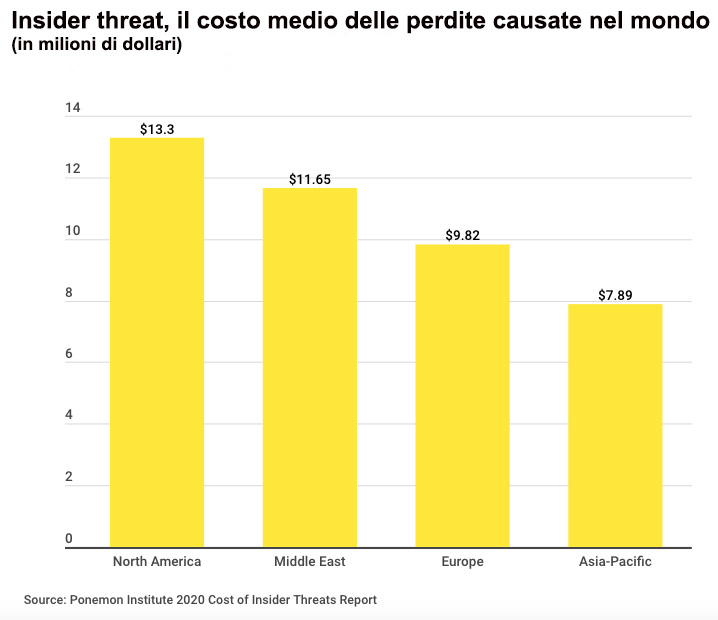
Insider Threat: cos è le tipologie ed alcuni famosi esempi
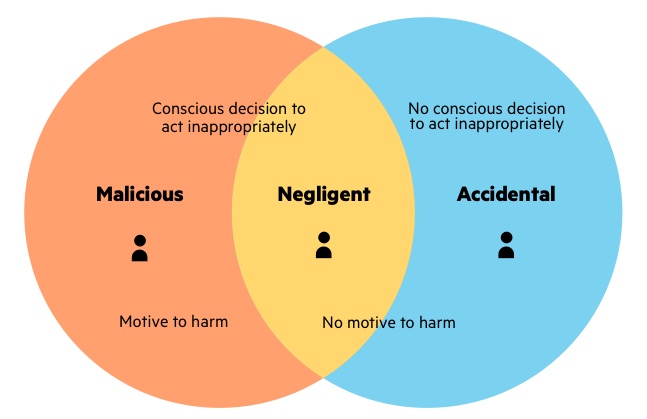
insider threat

Your Security Guide to Insider Threat Protection: 10 Best Practices to

Insider Threats Risks and Mitigation Strategies

Bomb Threat Checklist REDCAT SAFETY

Malicious Insider Threats: Examples and Techniques
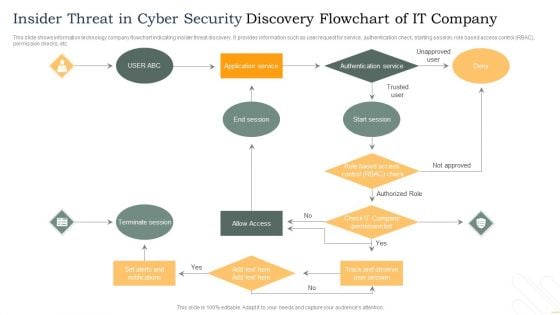
Process Flow For Detecting Insider Threat
Dashboard For Insider Threat Cases Management PPT Template

Threat and risks management absg2 PPT
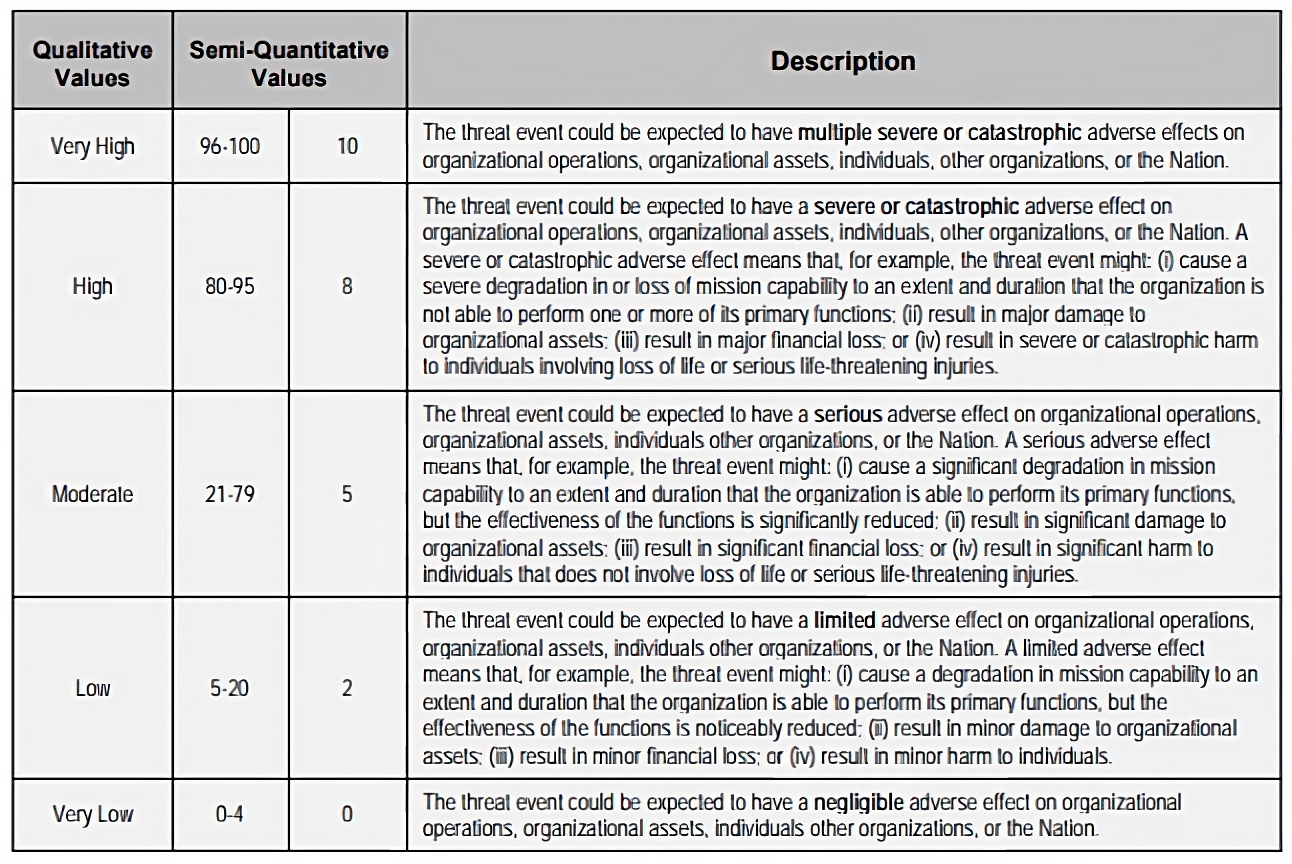
Nist Risk Assessment Template prntbl concejomunicipaldechinu gov co
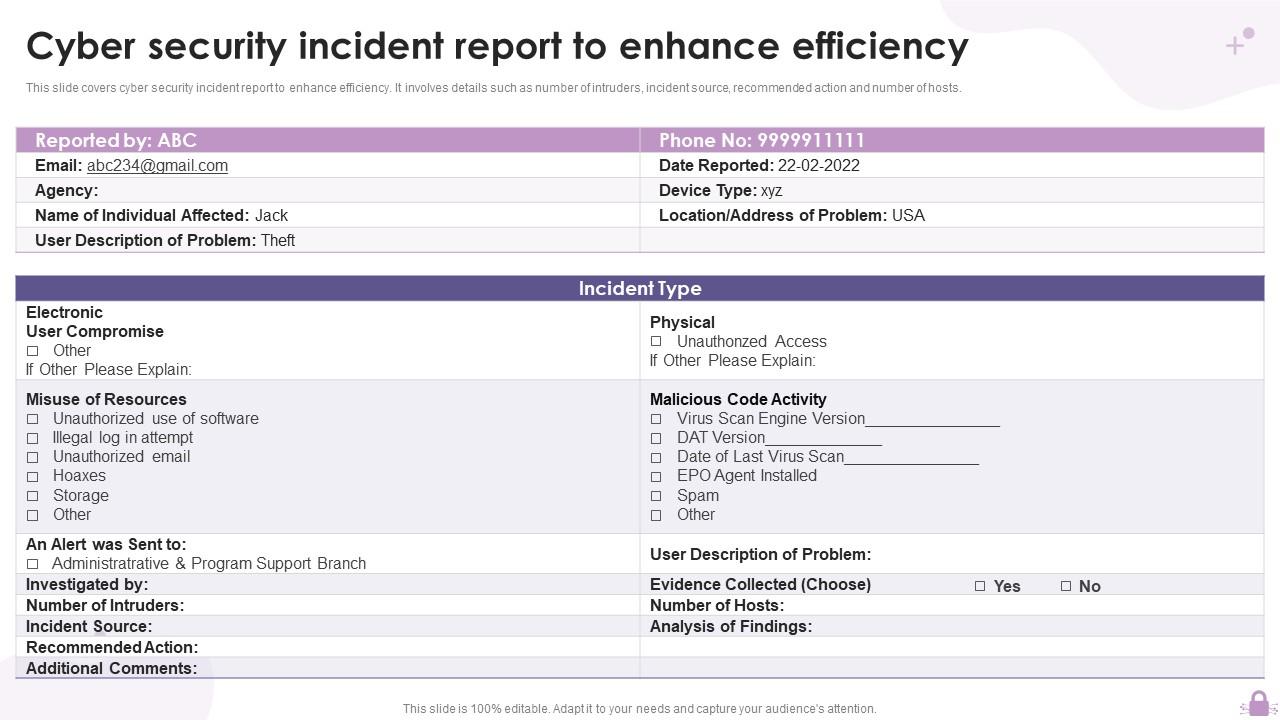
Cybersecurity Incident Response Report Template prntbl

Cyber Incident Response Plan Template Venngage

30 Policy Memo Examples to Download
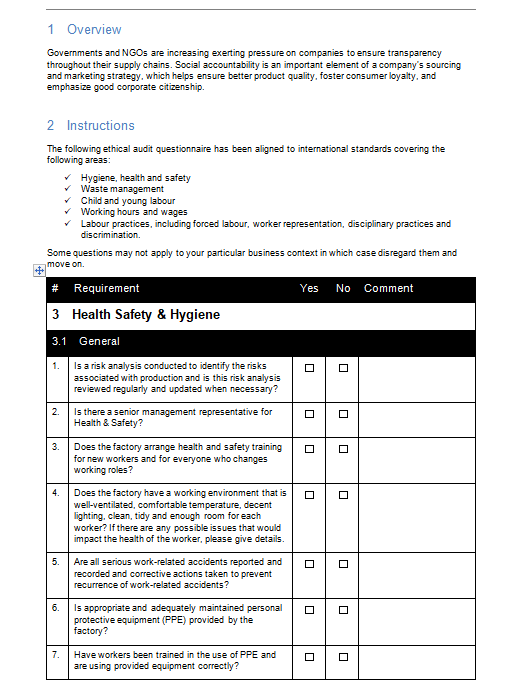
Questionnaire for Ethical Audit GRCReady
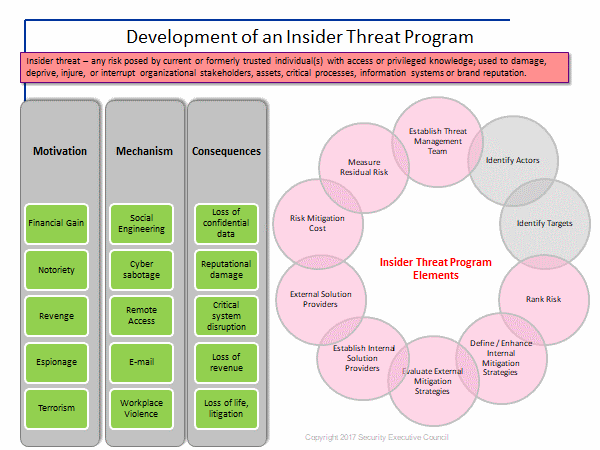
Development of an Insider Threat Program
Inside company PowerPoint templates Slides and Graphics

Pin on templates
Framer Templates Free prntbl concejomunicipaldechinu gov co

Framer Templates Free prntbl concejomunicipaldechinu gov co

Top 6 Cybersecurity Risk Assessment Templates and Tips
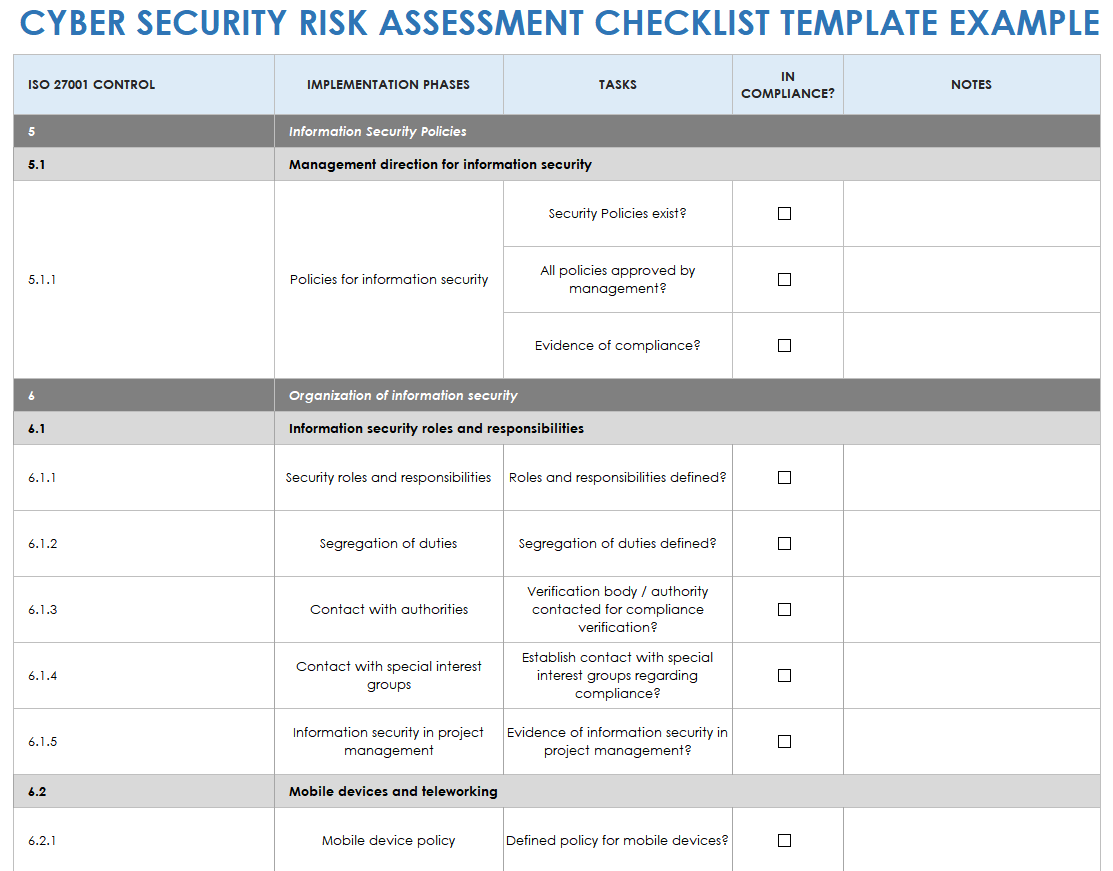
Free Cybersecurity Risk Assessment Templates Smartsheet

Related Links

Presidential Memo on Insider Threats Why Now?

UNCLAS Feature NITTF fw

NITTF Minimum Standards by Category

2017 Insider Threat Guide