It Security Risk Assessment Template
Here are some of the images for It Security Risk Assessment Template that we found in our website database.
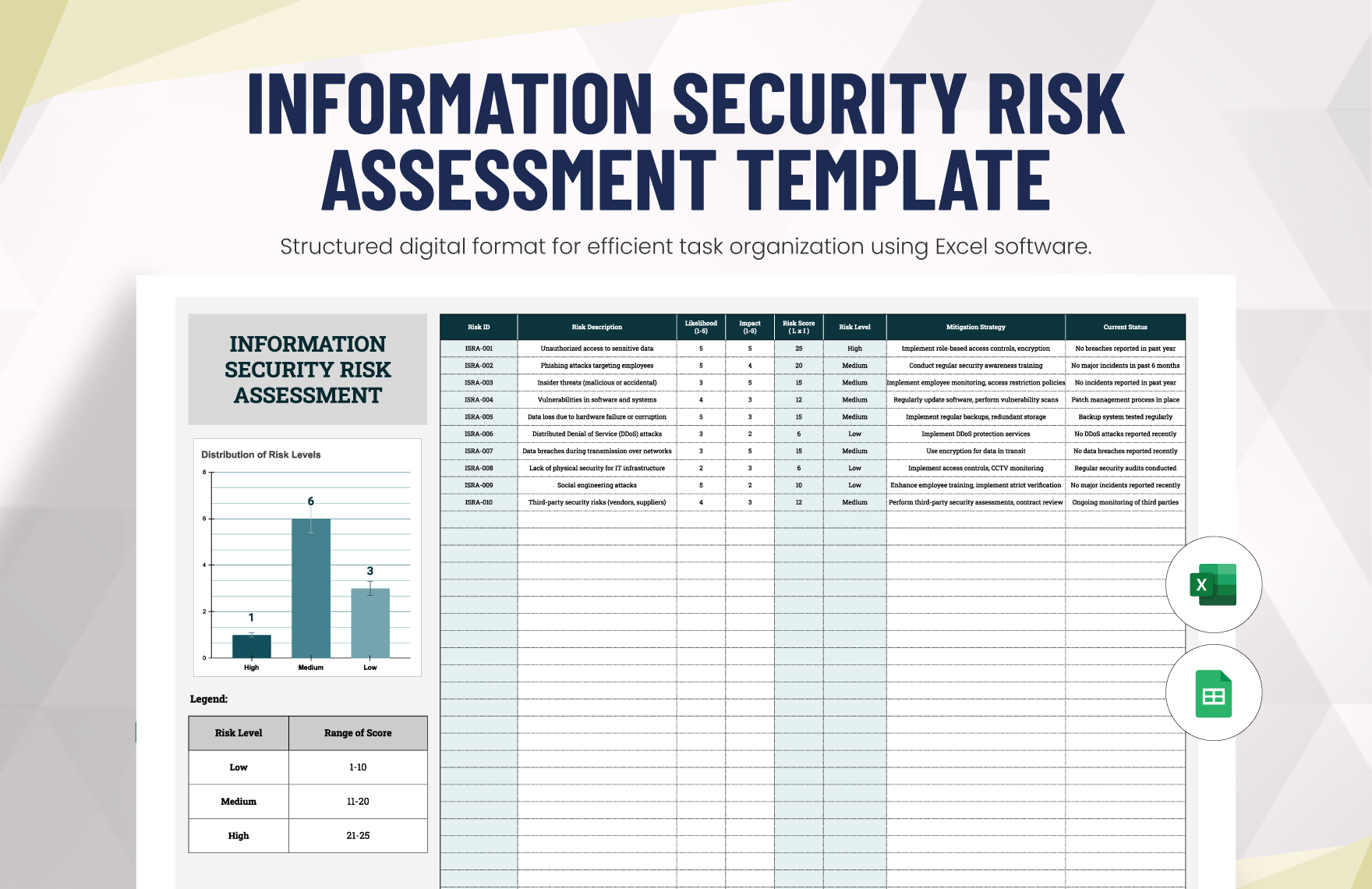
Information Security Risk Assessment Template Template net
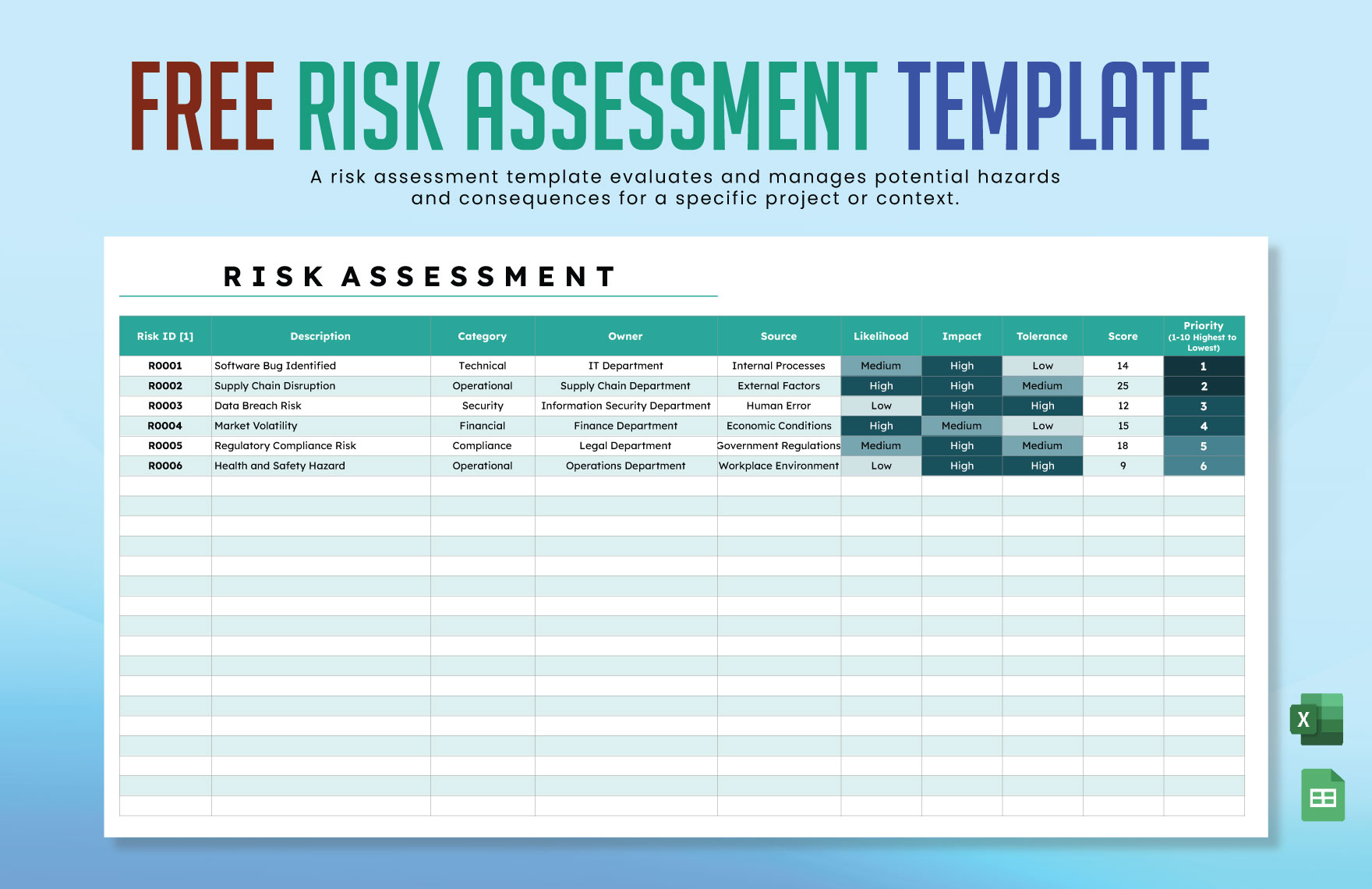
Information Security Risk Assessment Template Template net

Cybersecurity Risk Assessment Template in Word PDF Google Docs

IT Network Security Risk Assessment Template in Word PDF Google Docs

Free Cybersecurity Risk Assessment Template to Edit Online
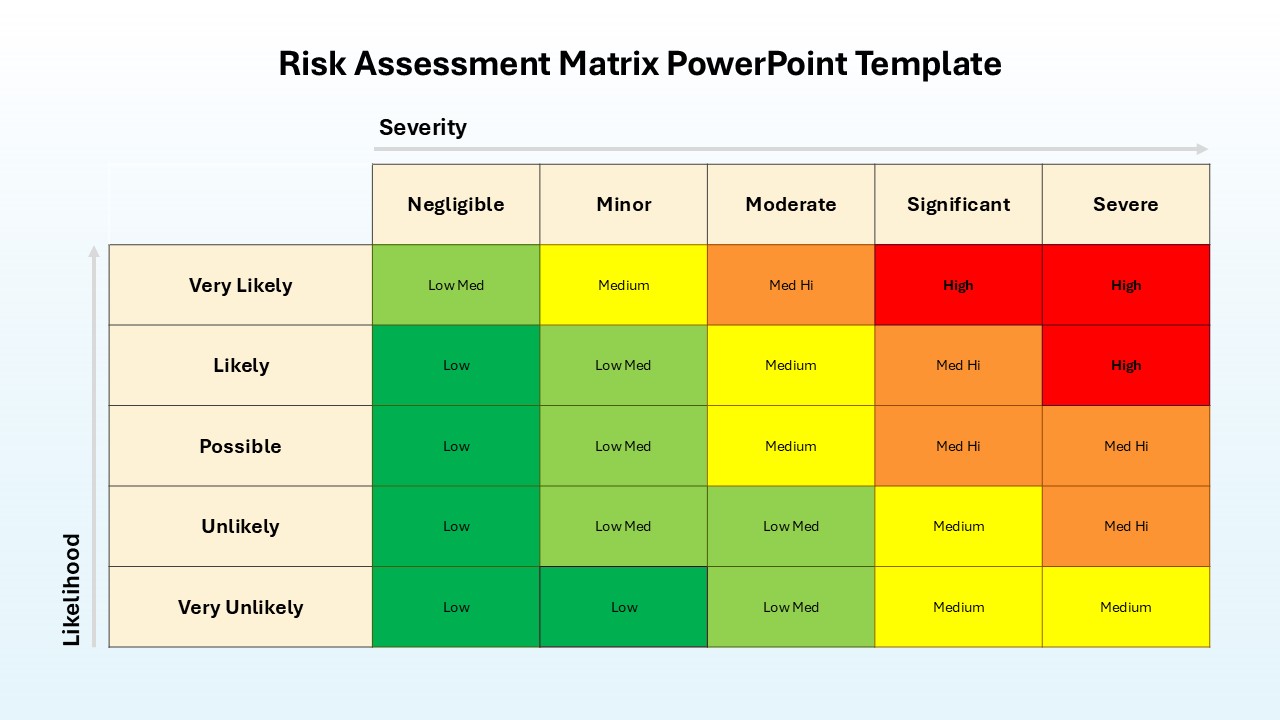
Security Risk Assessment PowerPoint and Google Slides Template SlideKit
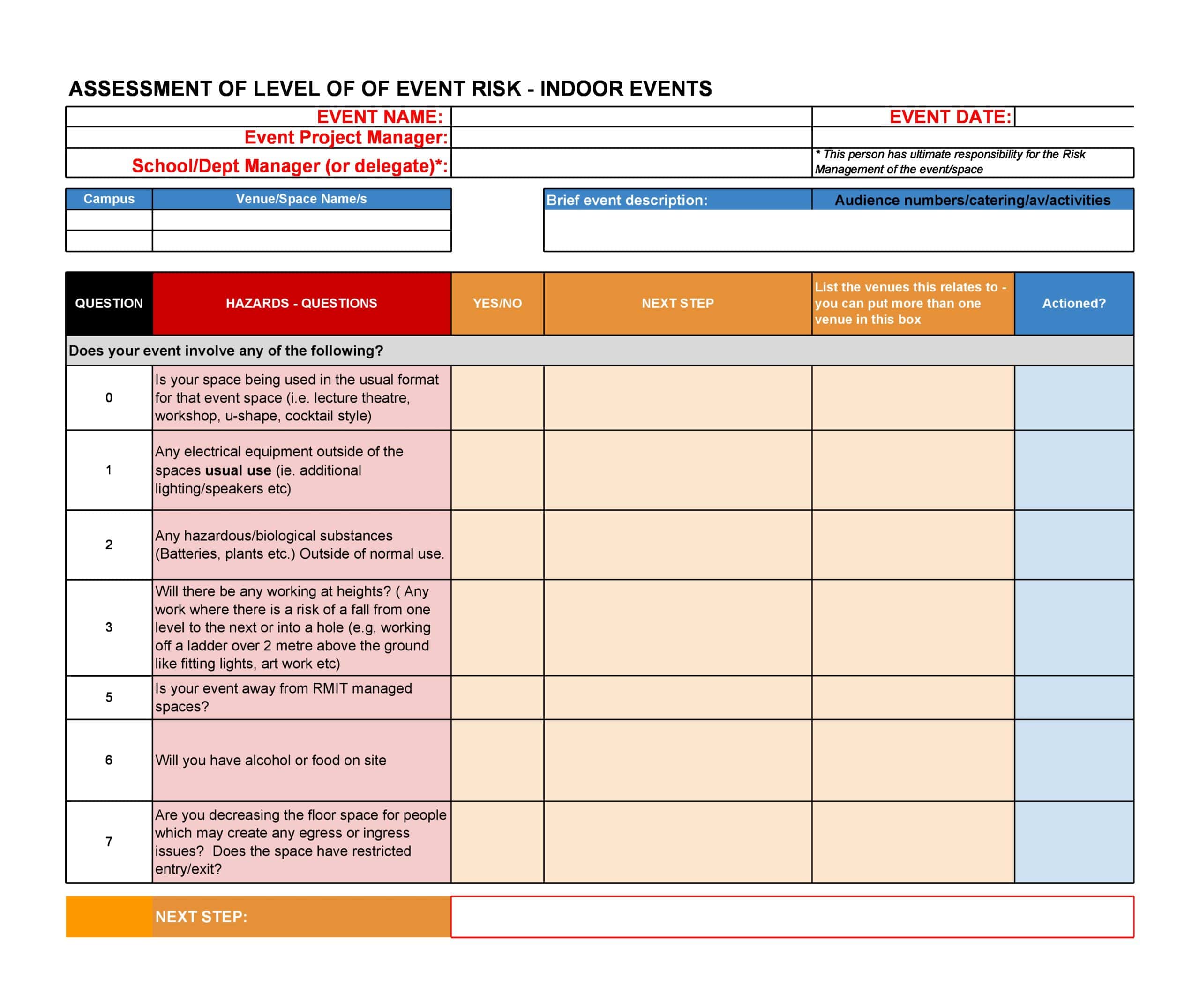
30 Useful Risk Assessment Templates ( Matrix ) TemplateArchive
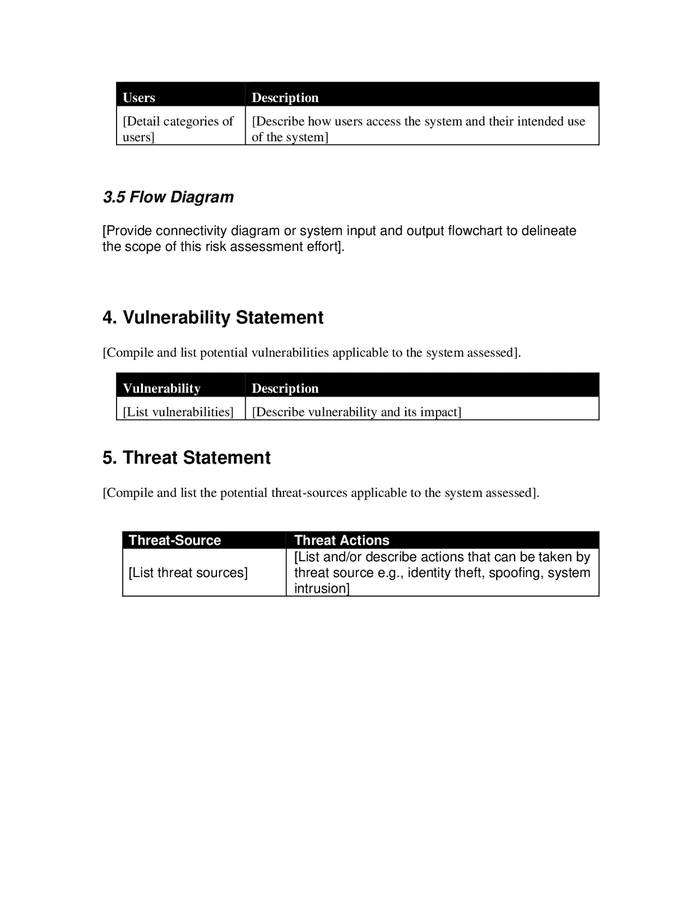
Security risk assessment template in Word and Pdf formats page 4 of 5

Cyber Security Risk Assessment PowerPoint Template PPT Slides
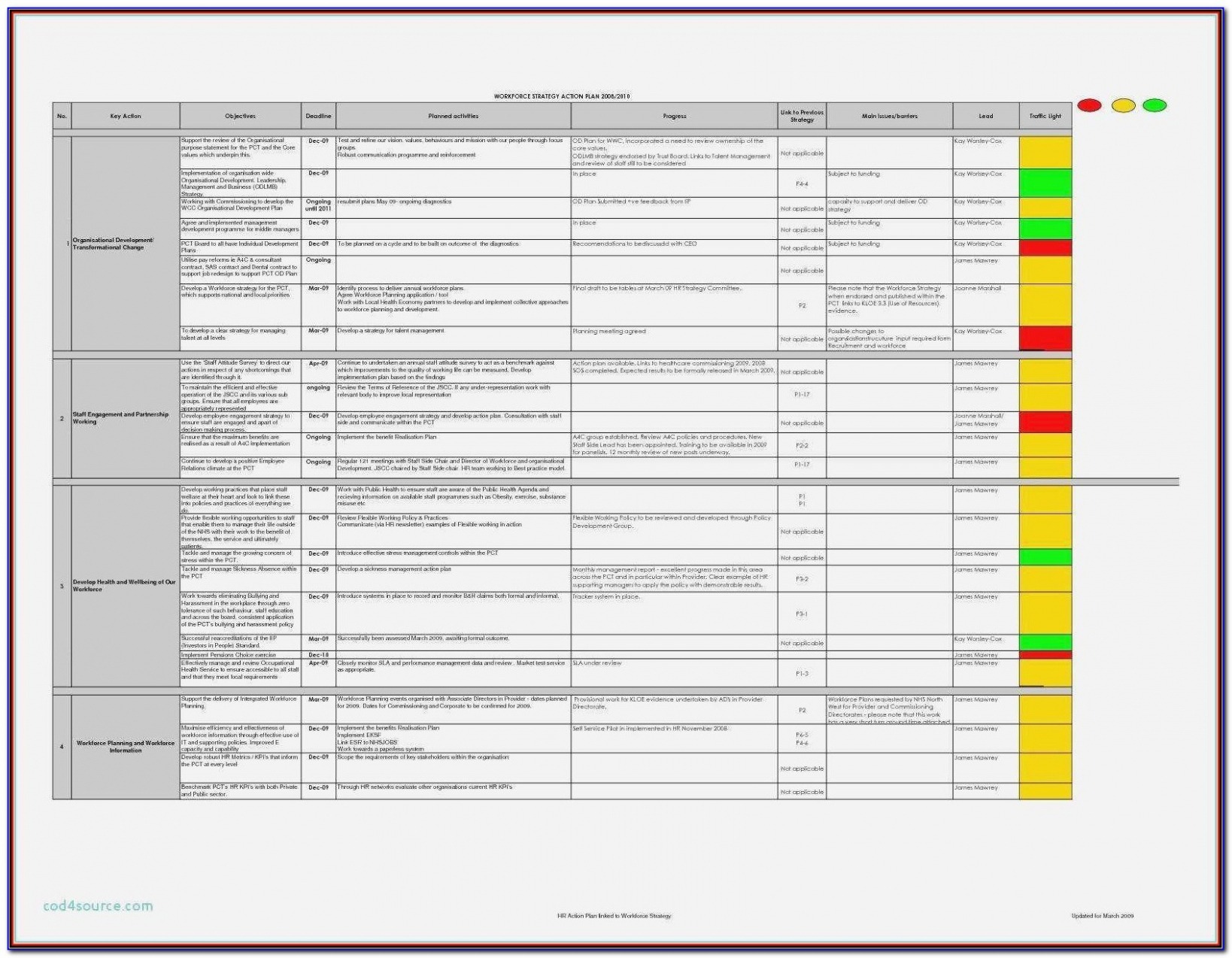
Best Cyber Security Risk Assessment Report Template XLS Tacitproject
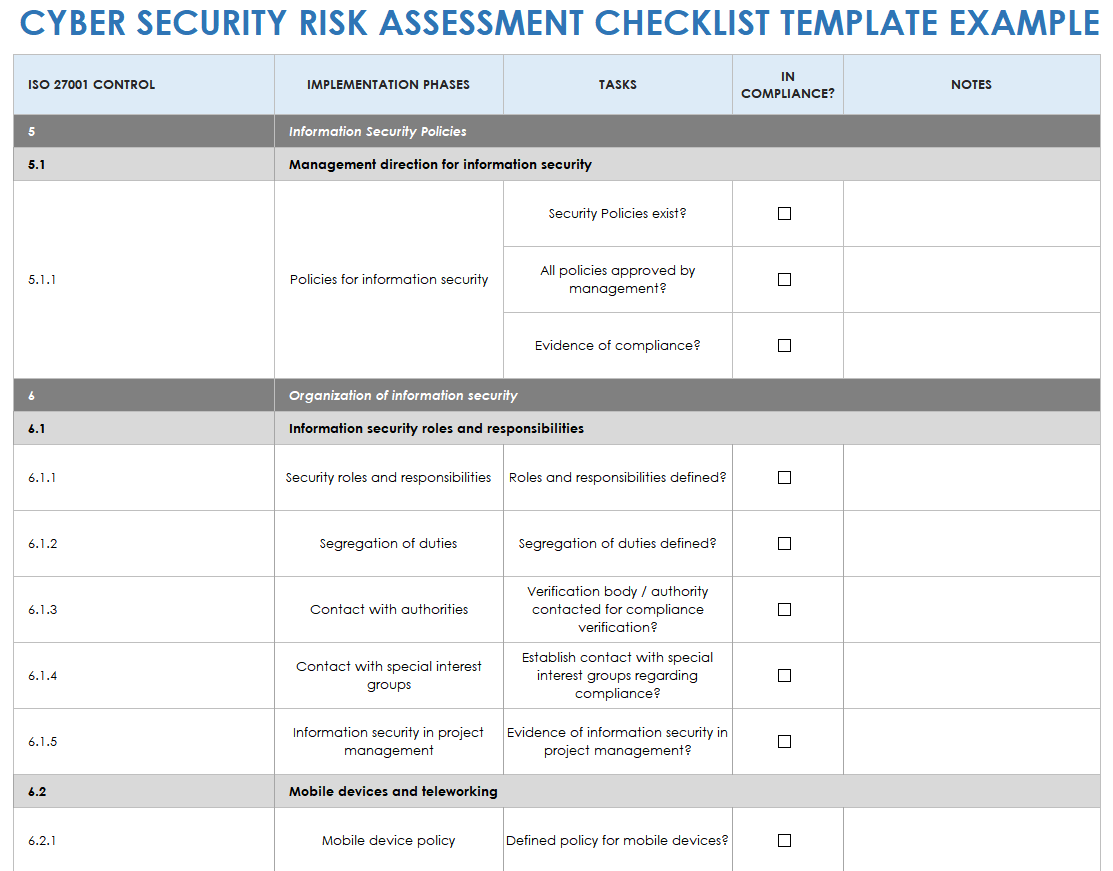
Security Risk Assessment Template Bioterrorism Security Risk

Security Risk Assessment Template New Sample Risk Assessment Report
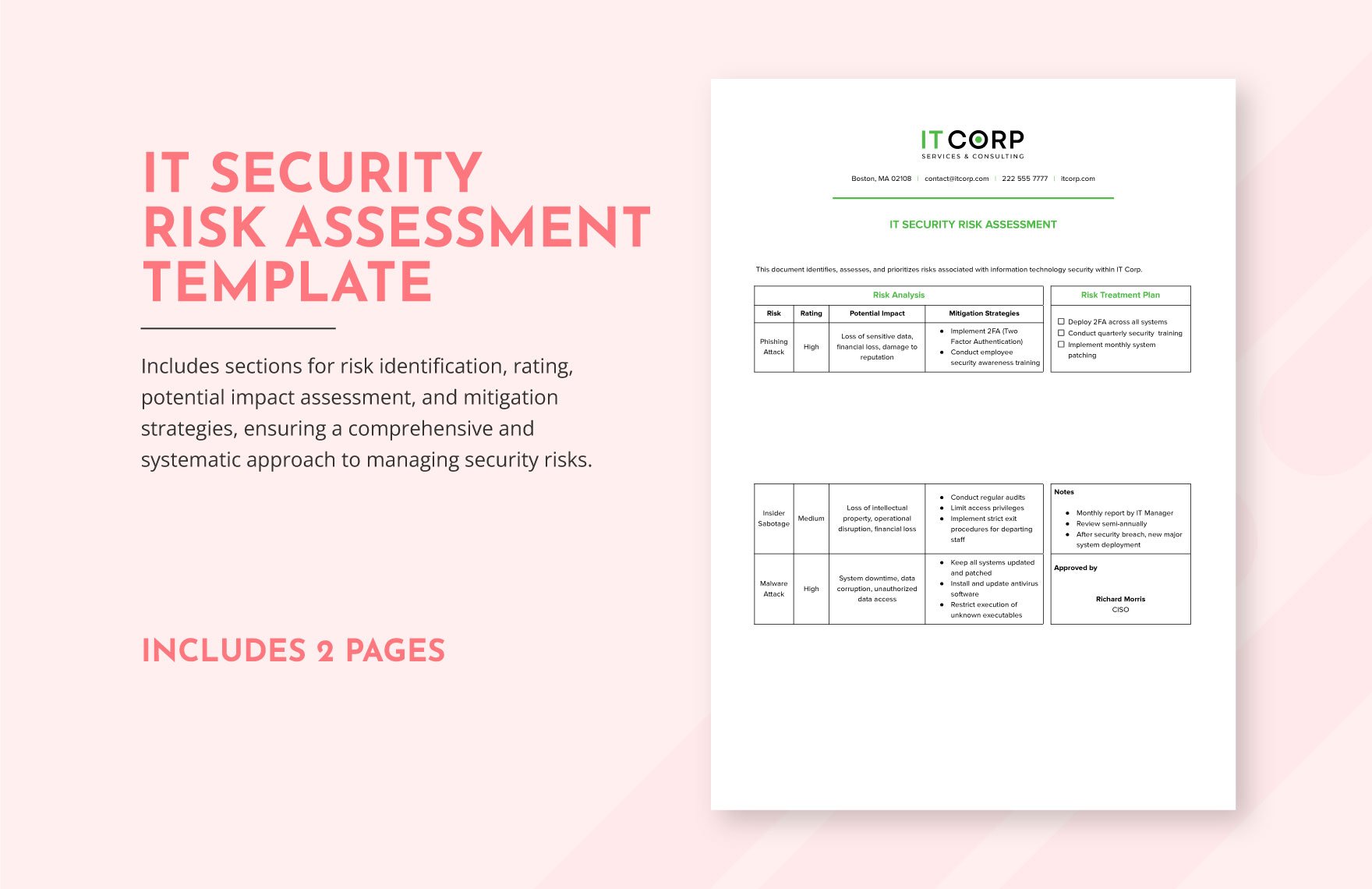
IT Business Continuity Risk Assessment Template Download in Word
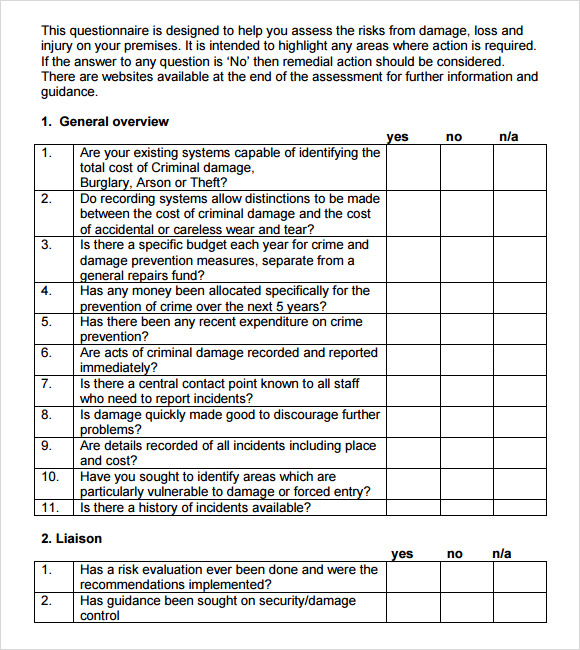
FREE 12 Sample Security Risk Assessment Templates in PDF MS Word Excel
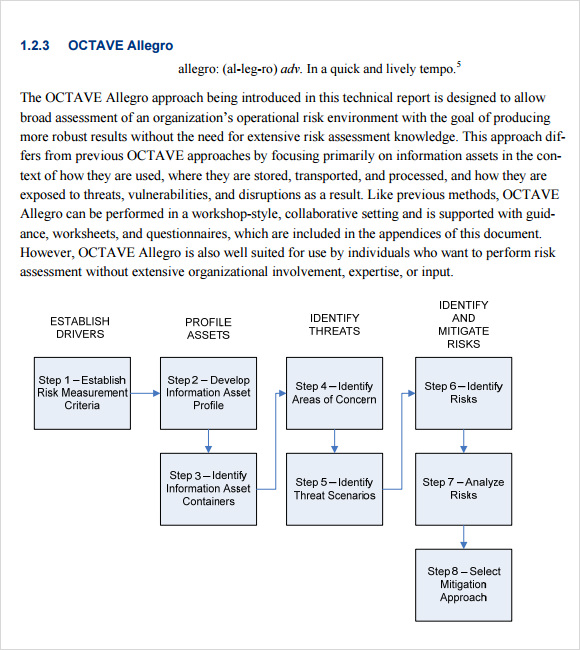
FREE 12 Sample Security Risk Assessment Templates in PDF MS Word Excel
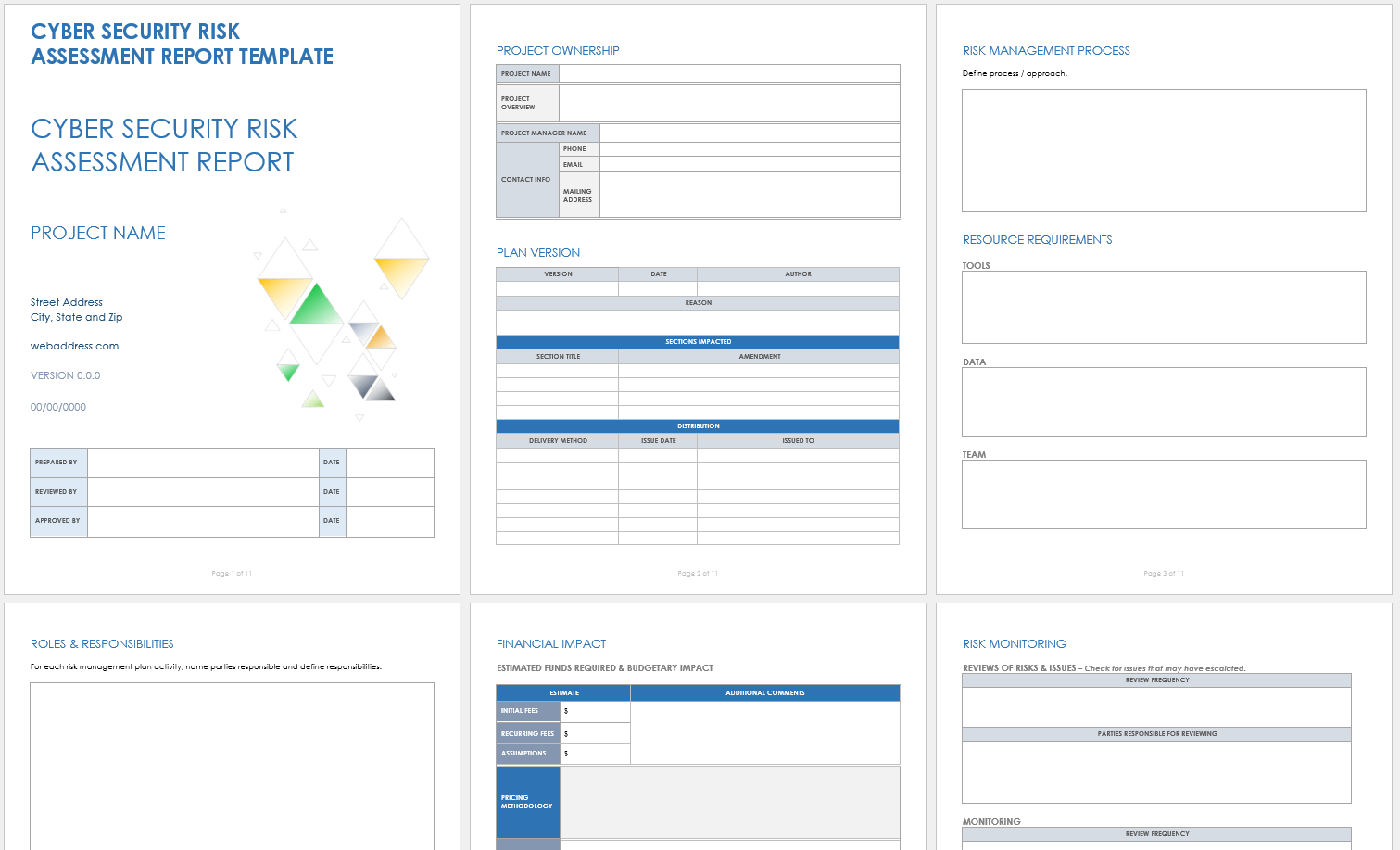
Security Risk Assessment Template New 9 Sample Risk Assessment Report

Security risk assessment template in Word and Pdf formats page 4 of 5

Application Security Risk Assessment Template Printable Word Searches

Security risk assessment template excel
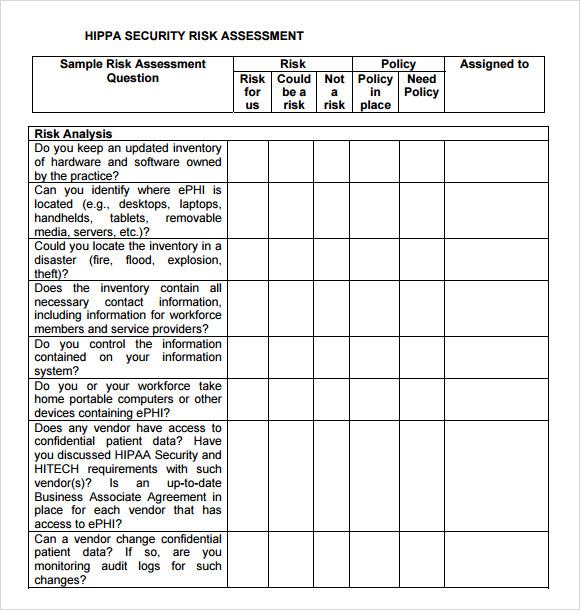
Security Risk Assessment 8 Free Download for PDF Word Excel
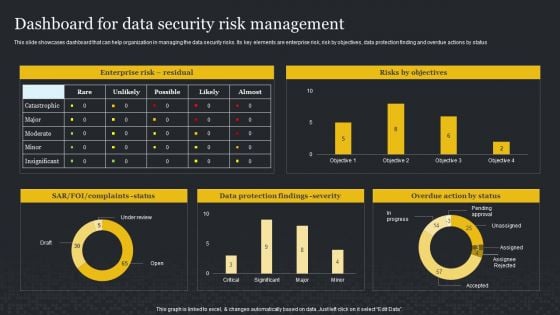
Dashboard For Data Security Risk Management Cybersecurity Risk
SSBA Security Risk Assessment and Risk Management Plan template

Free Security Assessment Template and Examples

Free Security Assessment Template and Examples
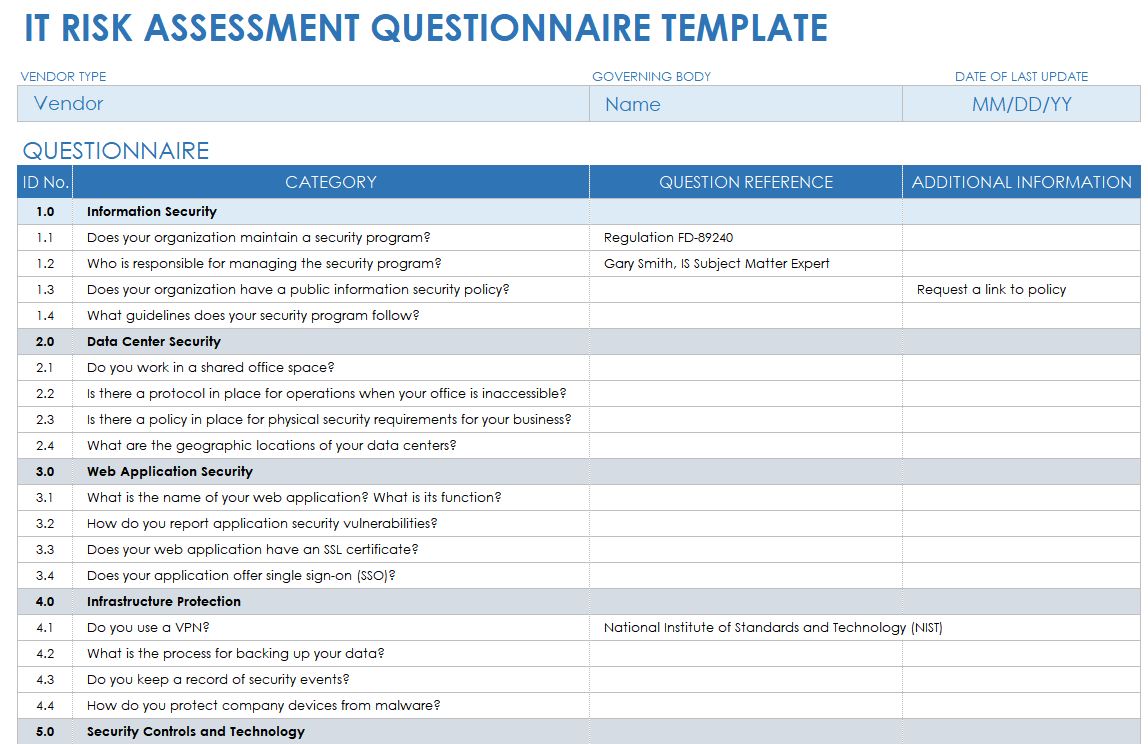
Information Security Risk Assessment Policy Template prntbl
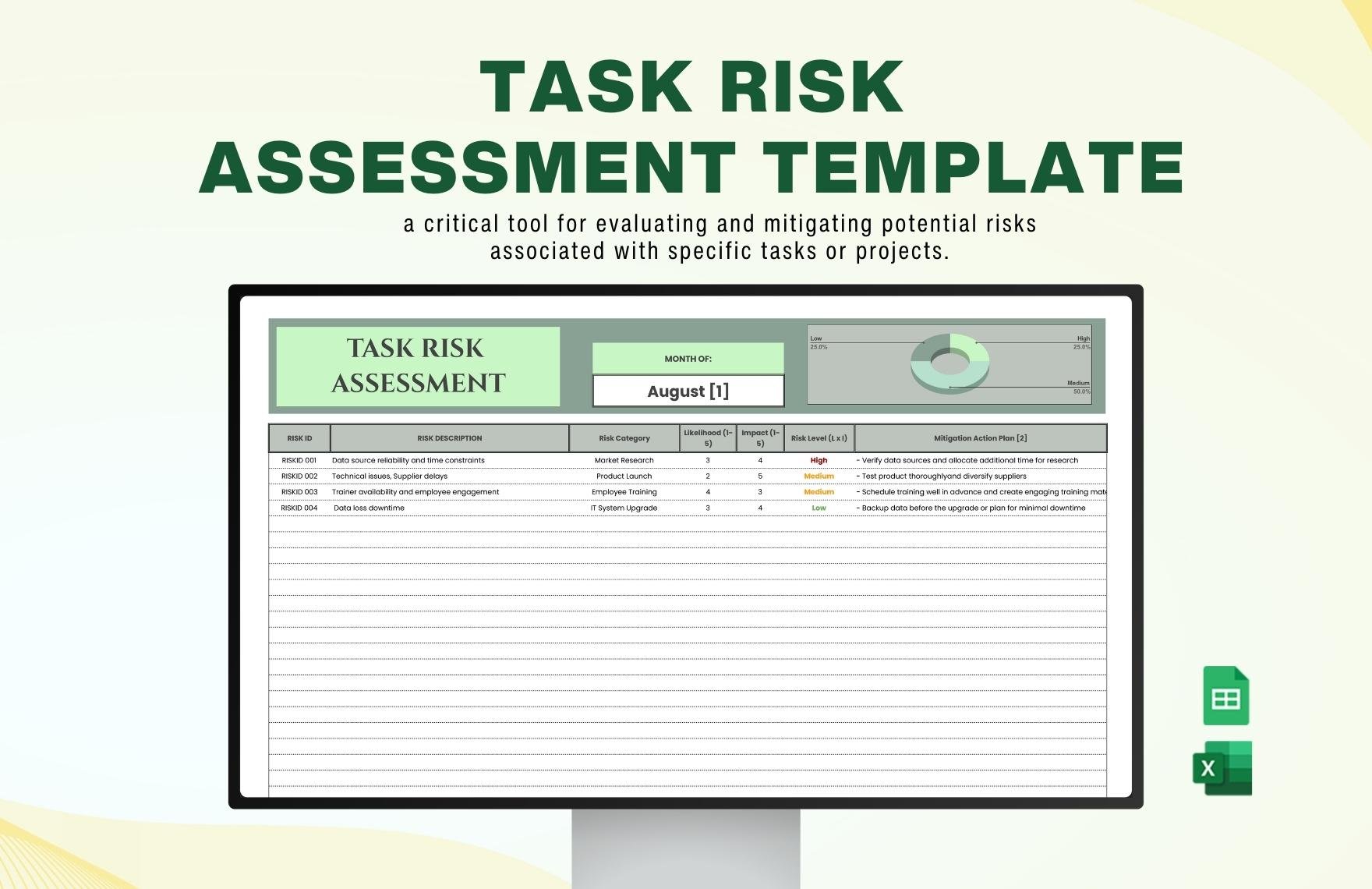
Data Quality Assessment Template in Excel Google Sheets Download

Ics Risk Assessment Template prntbl concejomunicipaldechinu gov co
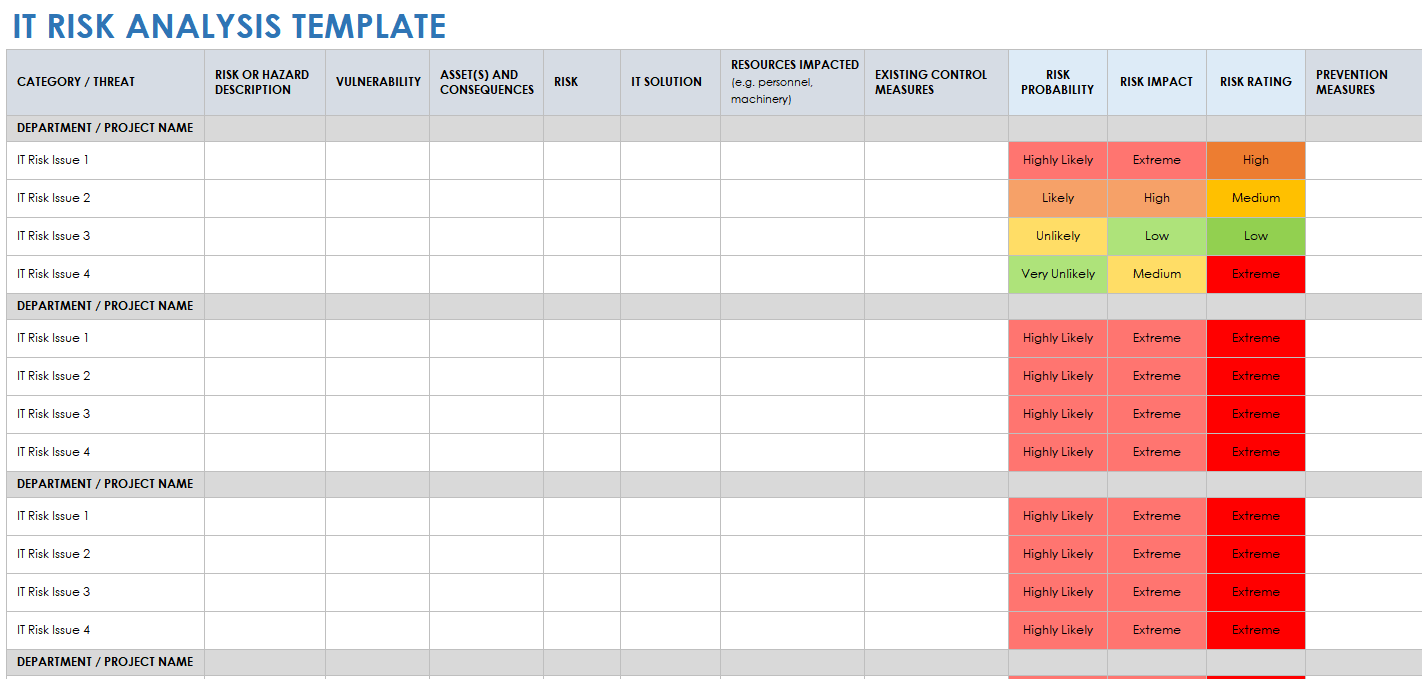
Bank Risk Assessment Template prntbl concejomunicipaldechinu gov co
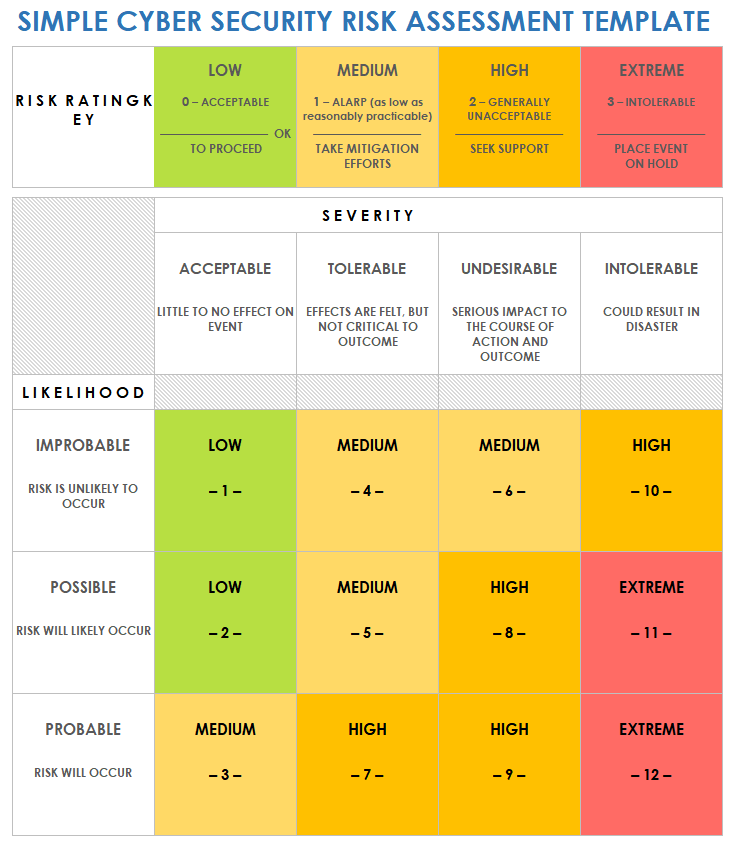
Security Assessment Report Template prntbl concejomunicipaldechinu gov co
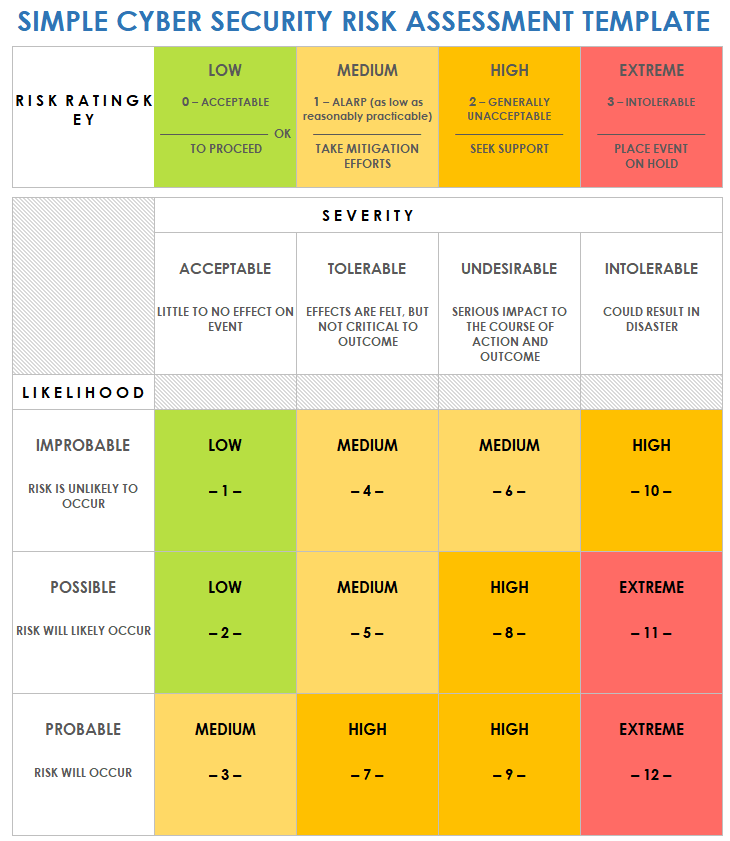
Security Assessment Report Template prntbl concejomunicipaldechinu gov co

Security Risk Analysis Template Free Sample Example Format Template
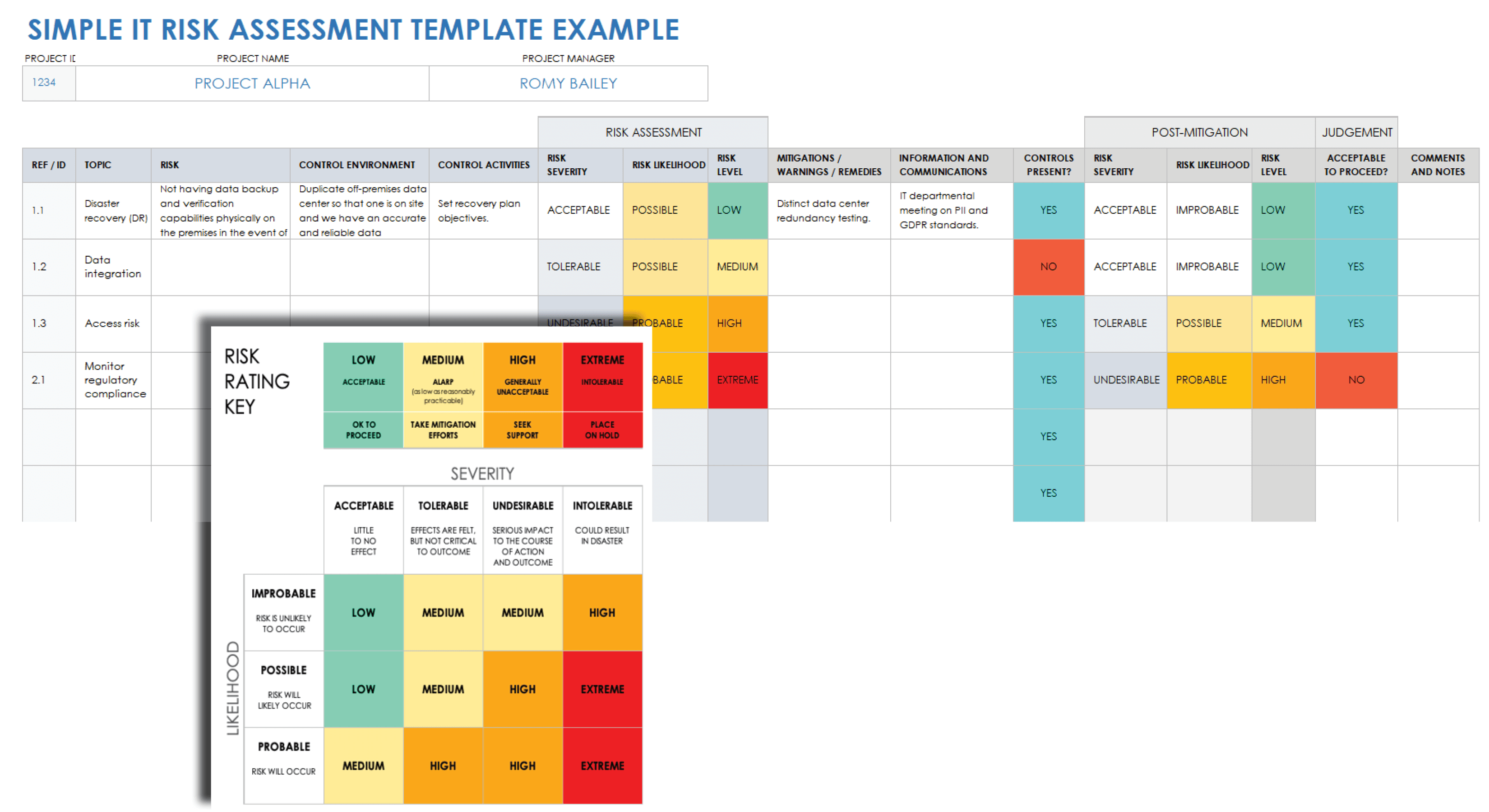
10 Security Risk Assessment Templates Free Samples Security Assessment
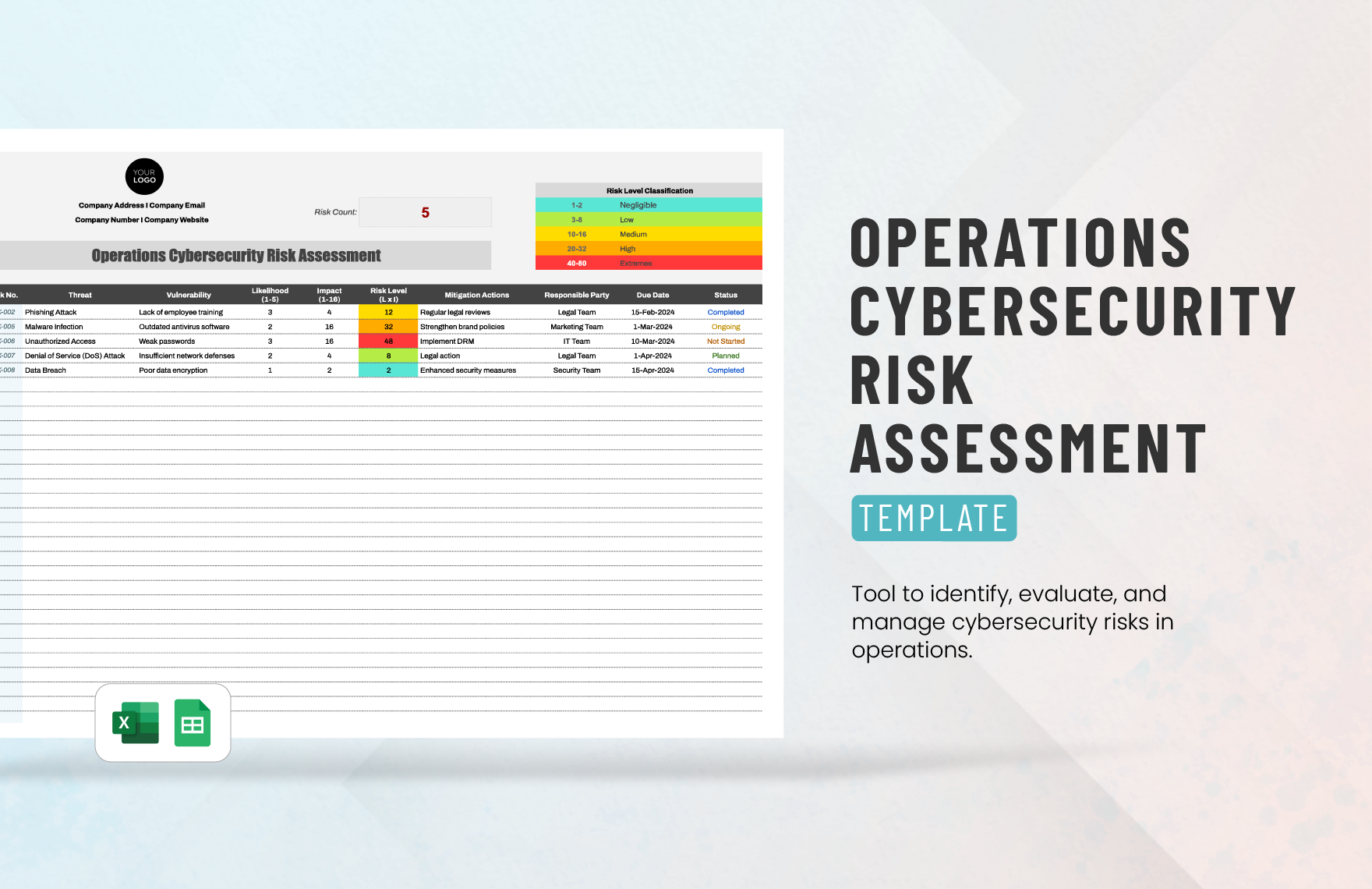
Editable Operation Templates in Excel to Download
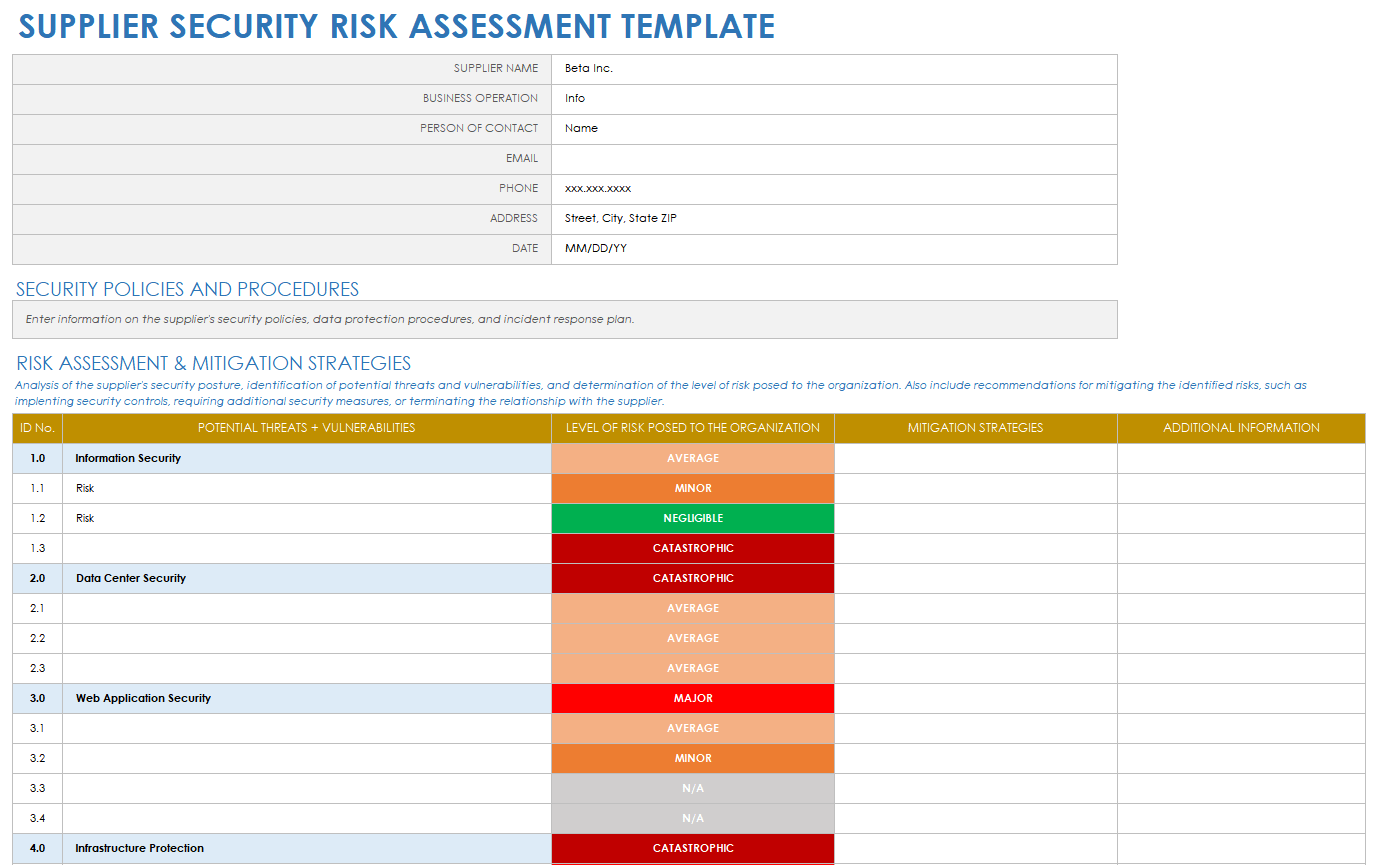
Free Supply Chain Risk Assessment Management Templates Smartsheet
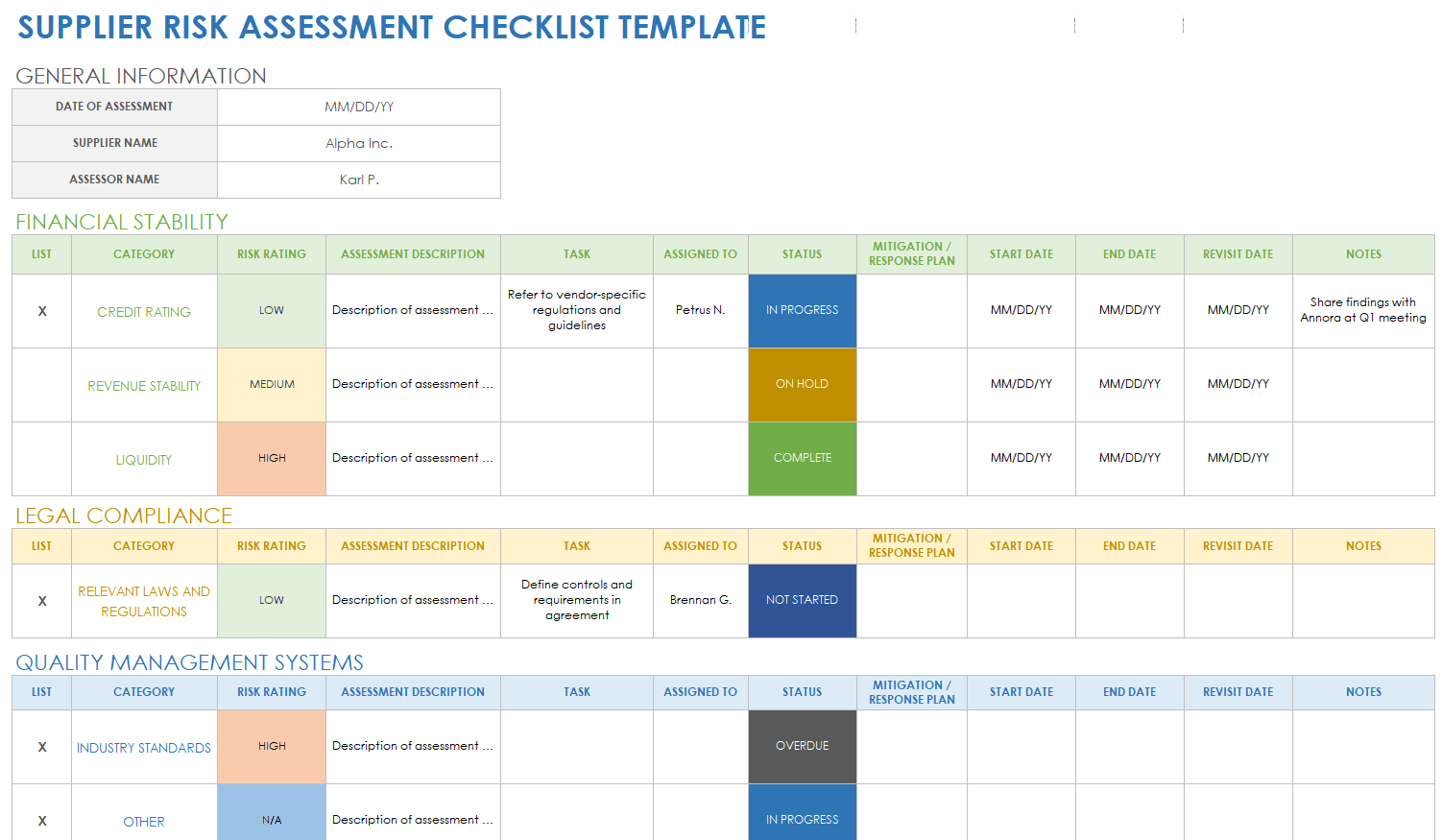
Free Supply Chain Risk Assessment Management Templates Smartsheet

Downloade it risk assessment template excel

Physical Security Risk Assessment Template Business risk Assessment

Security Risk Assessment Template

Security Risk Assessment Template

Security Risk Assessment Template 9 Sample Report Templates