Least Privilege Policy Template
Here are some of the images for Least Privilege Policy Template that we found in our website database.

Definition And Examples Least Define Least Algebra

Least vs Lowest English Grammar TED IELTS

Less or Least What s the Difference?

quot Less quot vs quot Least quot in the English Grammar LanGeek

PPT Comparative and Superlative Adjectives PowerPoint Presentation

Most and Least Number Worksheets for KS1/KS2 Maths Teachwire

Last But Not Least: Definition Important Rules with Useful Examples

Мало меньше самый маленький по английски Сравнительные прилагательные
Definition And Examples Least Define Least Algebra

自学英语 如何区分late、last、latest、least? 知乎

Opposite Of Least Antonyms of Least Meaning and Example Sentences

least(最も小さい)の意味と使い方 あふろさんブログ
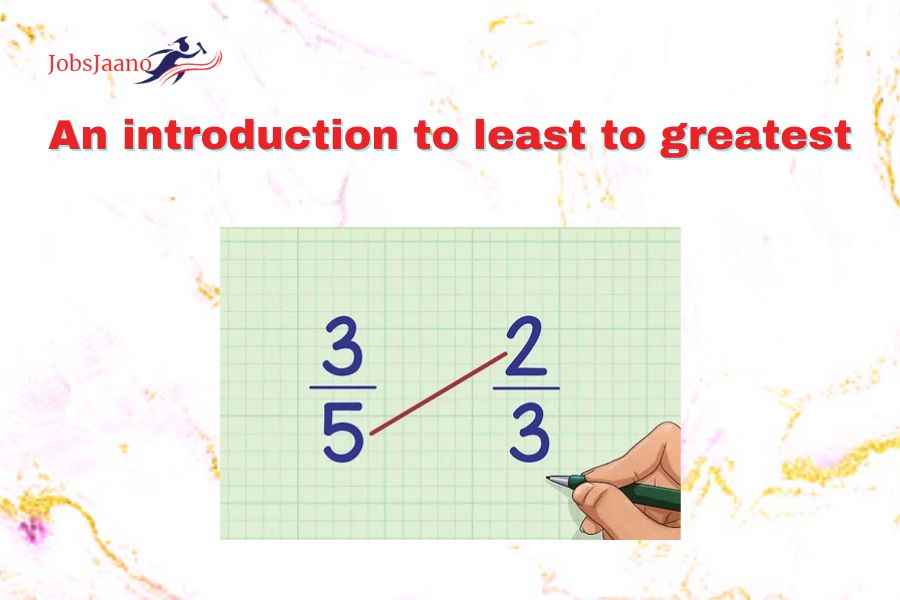
Least Common Denominator
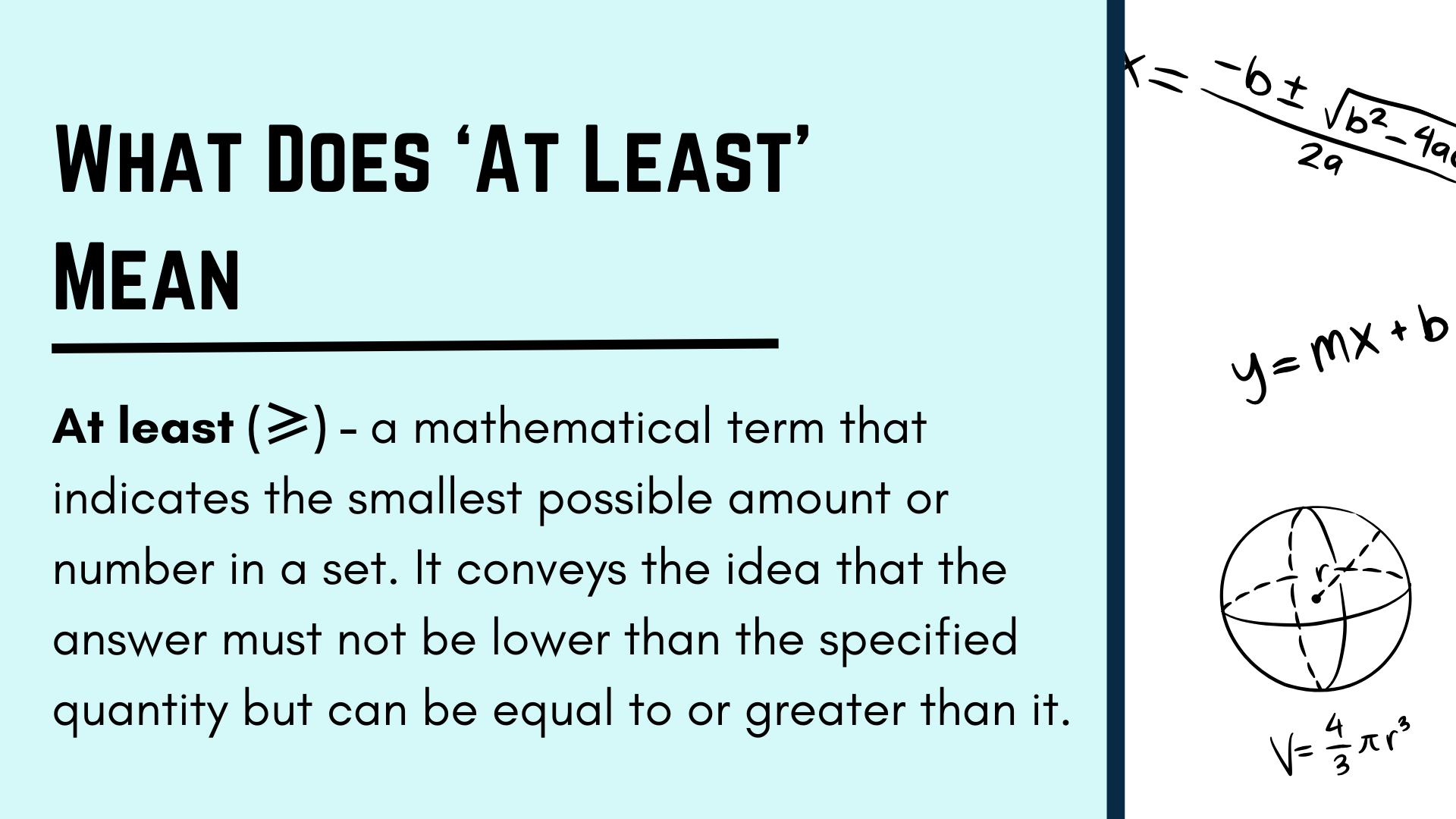
Discover the Secrets of quot At Least quot in Math: Master Mathematical

quot Most quot vs quot Least quot in the English Grammar LanGeek

What is Least Count? Definition Calculation Error Examples
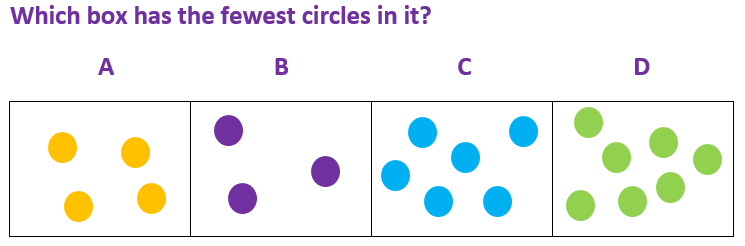
KS1 Number Quantities Most Fewest and Least

Discover the Secrets of quot At Least quot in Math: Master Mathematical
:max_bytes(150000):strip_icc()/LeastSquaresMethod-4eec23c588ce45ec9a771f1ce3abaf7f.jpg)
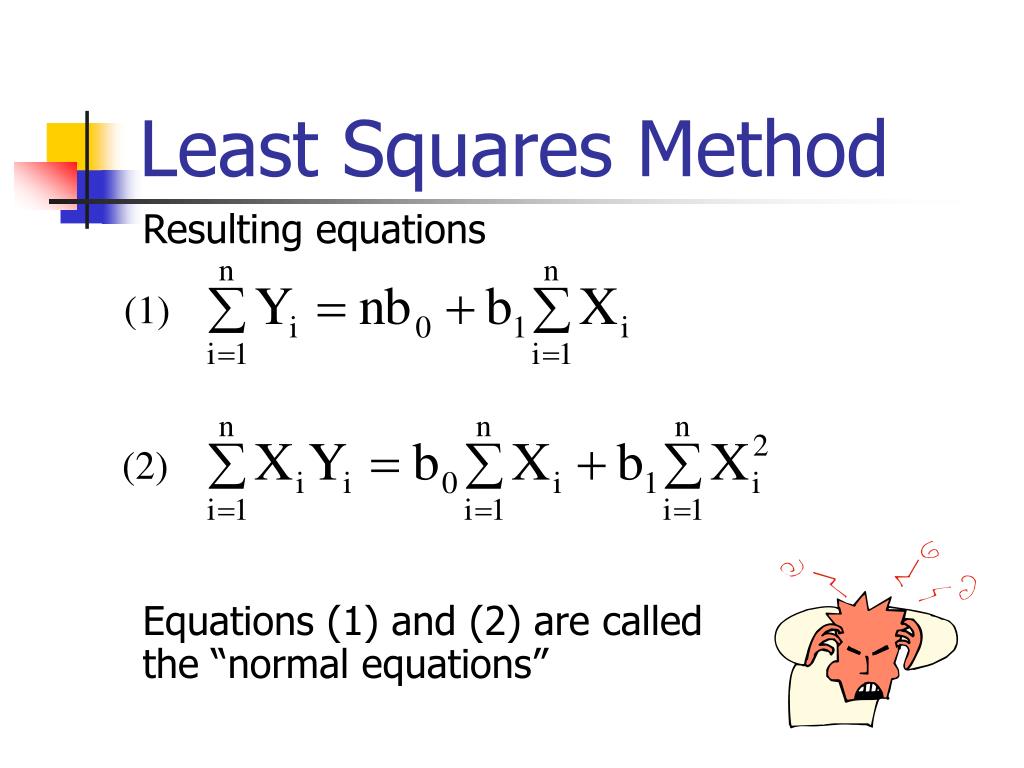
Least Squares Method: What It Means and How to Use It With Examples

you might also be interested in these resources aim high inspire
Least Common Denominator Example

KS1 Number Quantities Most Fewest and Least
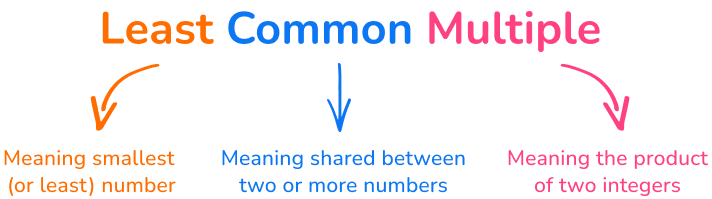
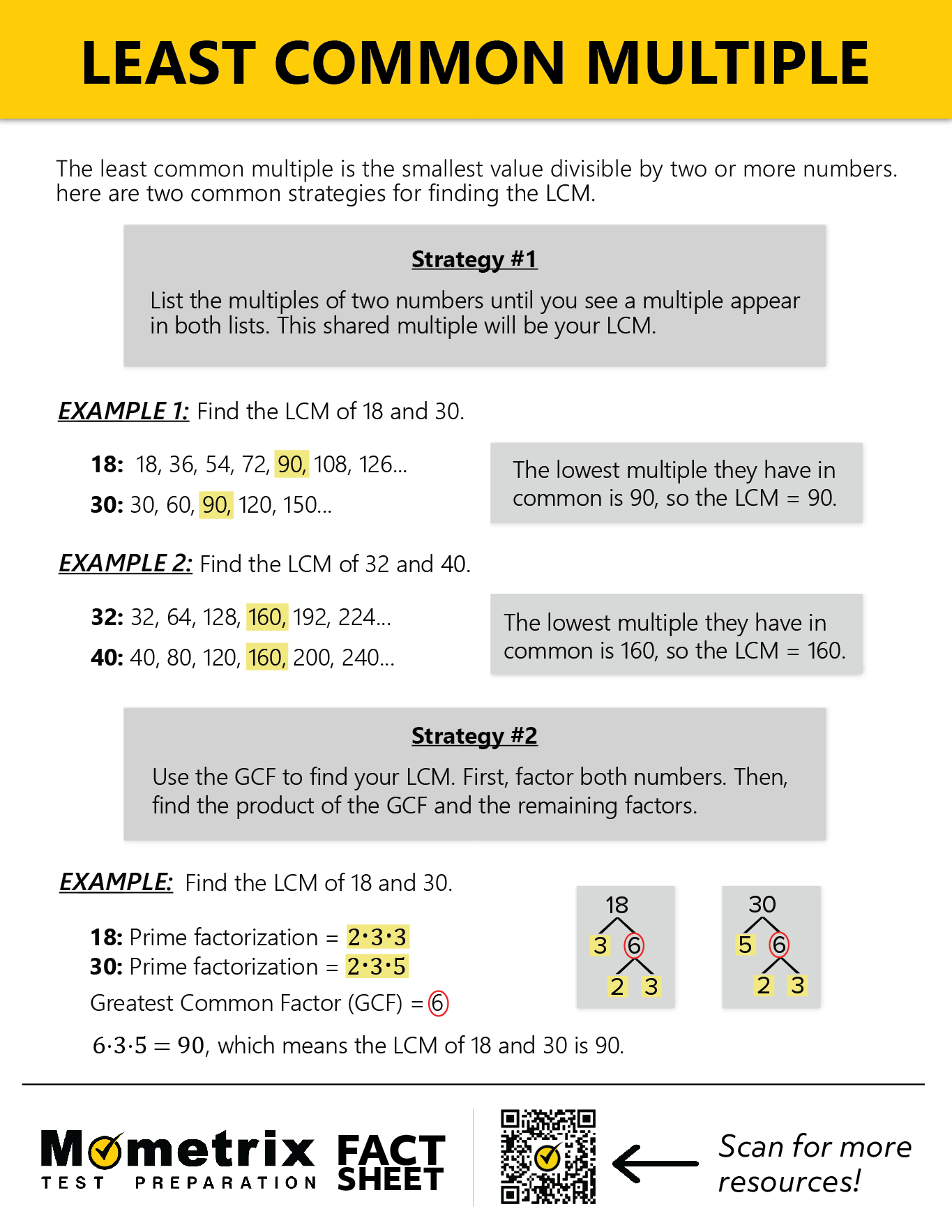
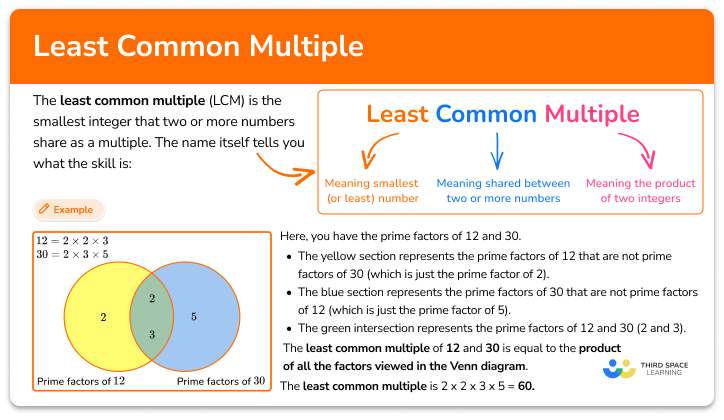
Least Common Multiple Definition

Least Meaning YouTube

Less and Least Easy With video and quiz English with a Smile
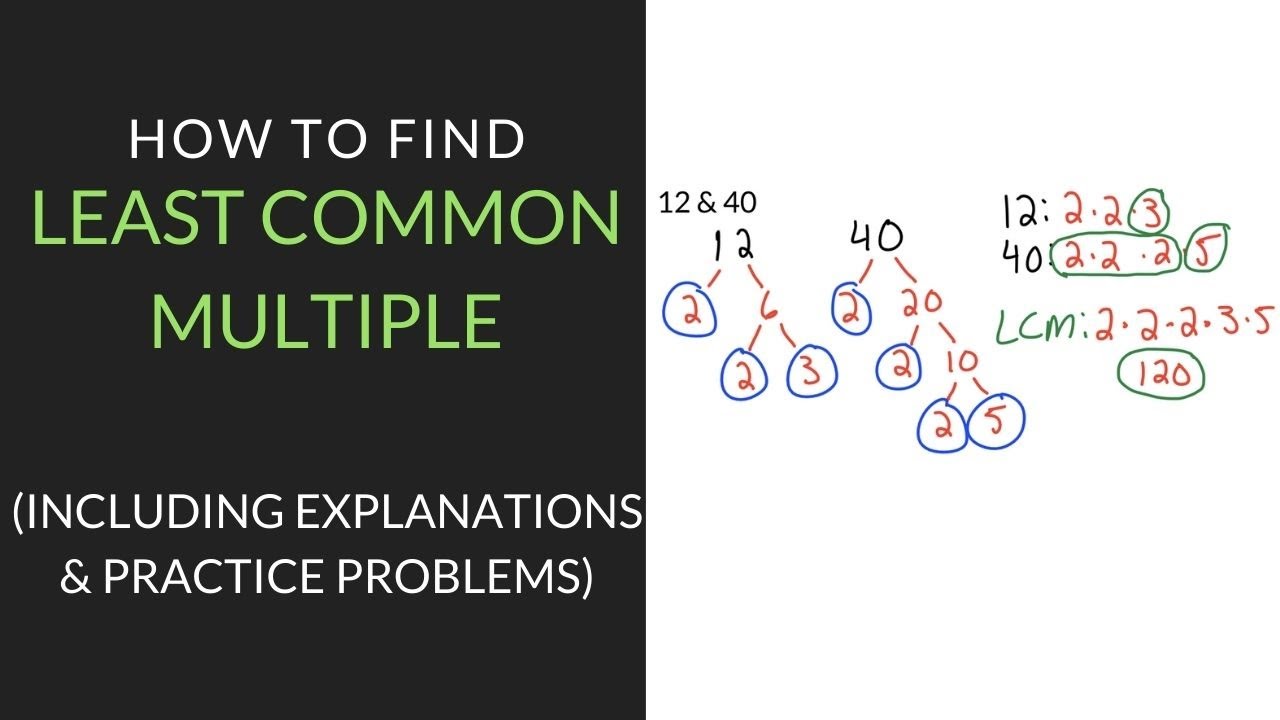
Least Common Multiple Examples

At least là gì? Ý nghĩa và Cách Sử dụng ĐÚNG 2025

Asafetida Sentence Example at George Farrow blog

least word on white keyboard 5984452 Stock Photo at Vecteezy

Most or Least Symbol Businessman Turns Beautiful Wooden Cubes and
PPT Graphical Analysis PowerPoint Presentation free download ID
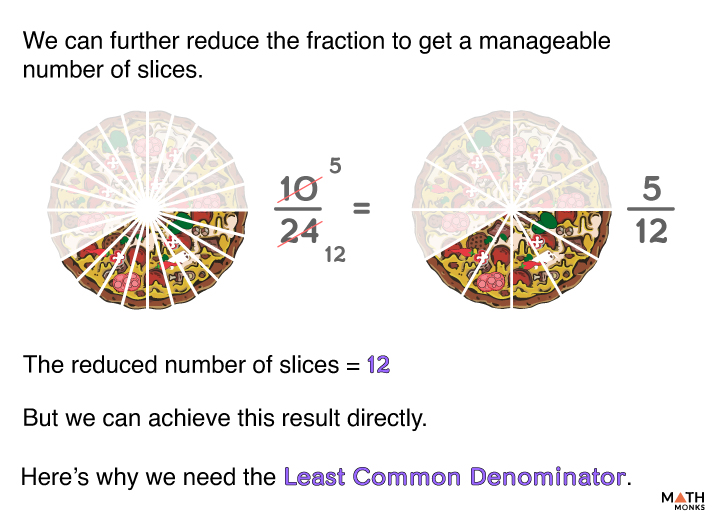
Least Common Denominator

least 百度百科

What is the meaning of the word LEAST? YouTube
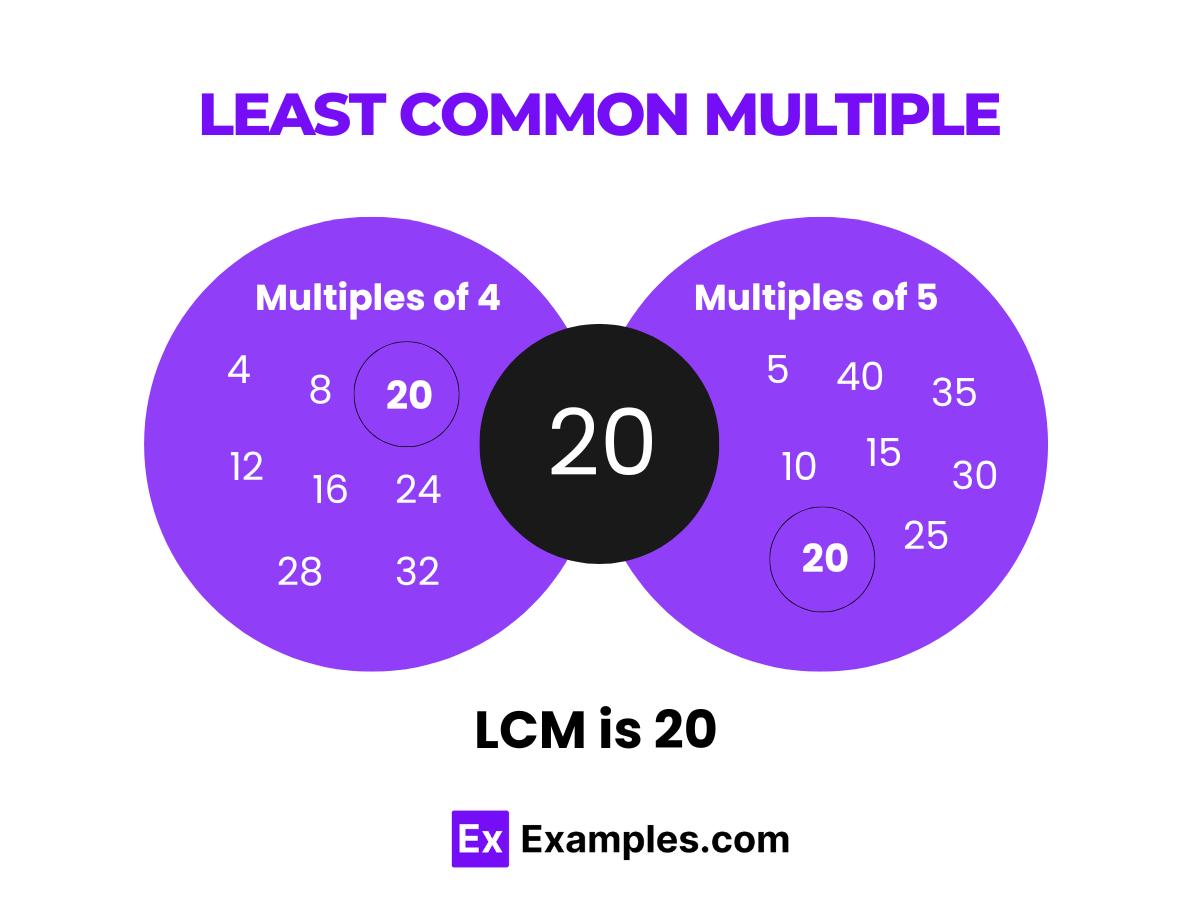
Least Common Multiple Generator