Malware Analysis Certification
Here are some of the images for Malware Analysis Certification that we found in our website database.

Malware Analysis Course Training Certification 202400 Updated

Malware Analysis Training Certification in Delhi India 2025

Malware Analysis Tools 25 Best Malware Analysis Tools and Techniques
Malware Analysis 4 Vital Stages of Malware Analysis You Should Know

Best Malware Analysis Courses Malware Analyst Certification Training
PPT Malware Analysis Course Training Certification PowerPoint

PPT Malware Analysis Course Training Certification PowerPoint
PPT Malware Analysis Course Training Certification PowerPoint

💡 Malware Analysis Course and Certification 1) Ultimate Malware

PPT Malware Analysis Course Training Certification in delhi

PPT Malware Analysis Course Training Certification in delhi

PPT Malware Analysis Course PowerPoint Presentation free download

Learn Best Malware Analysis Course with Certification in Delhi NCR pdf

Practical Malware Analysis Triage Expert Training

CosmicDuke Malware Analysis CYFIRMA

MARE Malware Analysis and Reverse Engineering Certification Course

GIAC Reverse Engineering Malware GREM

Malware Analysis Course and Certification: 1 Ultimate Malware Analysis

Learn Best Malware Analysis Course with Certification in Delhi NCR pdf

I m happy to share that I ve obtained a new certification: Malware

🌟Achieving Malware Analysis Fundamentals Certification

Mastering Malware Analysis: A Journey through SANS FOR610 and GREM

Mastering Malware Analysis: A Journey through SANS FOR610 and GREM

Mastering Malware Analysis: A Journey through SANS FOR610 and GREM

Mastering Malware Analysis: A Journey through SANS FOR610 and GREM

Mastering Malware Analysis: A Journey through SANS FOR610 and GREM

Malware Analysis Certificate (2 of 4) ISC2 Security Administration
STRRAT: Malware Analysis of a JAR archive ANY RUN #39 s Cybersecurity Blog

Complete Course and Certification Review of Zero2Automated The

Complete Course and Certification Review of Zero2Automated The

Complete Course and Certification Review of Zero2Automated The

toolkit: The essential toolkit for reversing malware analysis and

I m happy to share that I ve obtained a new certification: Malware

In Depth Malware Dissection: Insights from Chapter 9 Lab of Practical

Emsisoft Anti Malware receives VB100 certification in latest round of
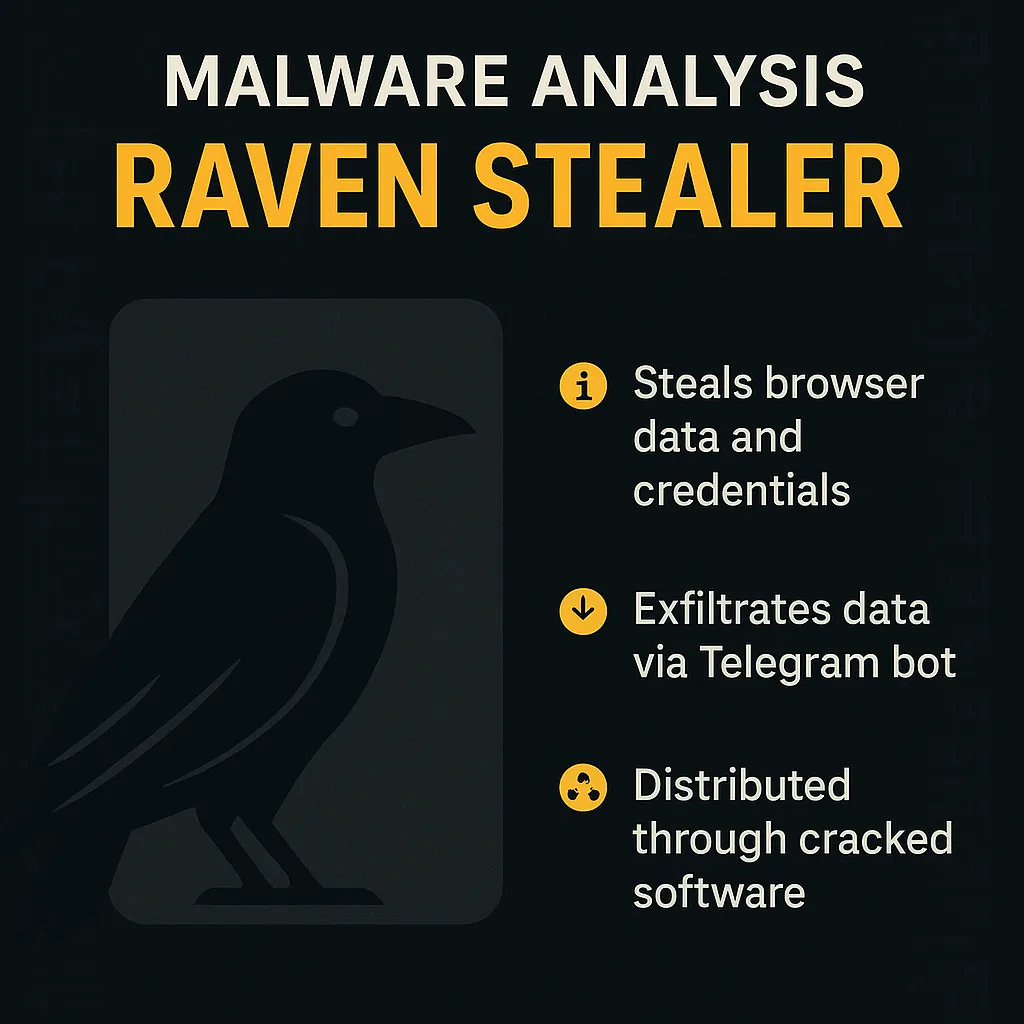
Lets Defend: Malware Analysis Fundamentals by Sakshee Bapat Medium
Lets Defend: Malware Analysis Fundamentals by Sakshee Bapat Medium

Lets Defend: Malware Analysis Fundamentals by Sakshee Bapat Medium
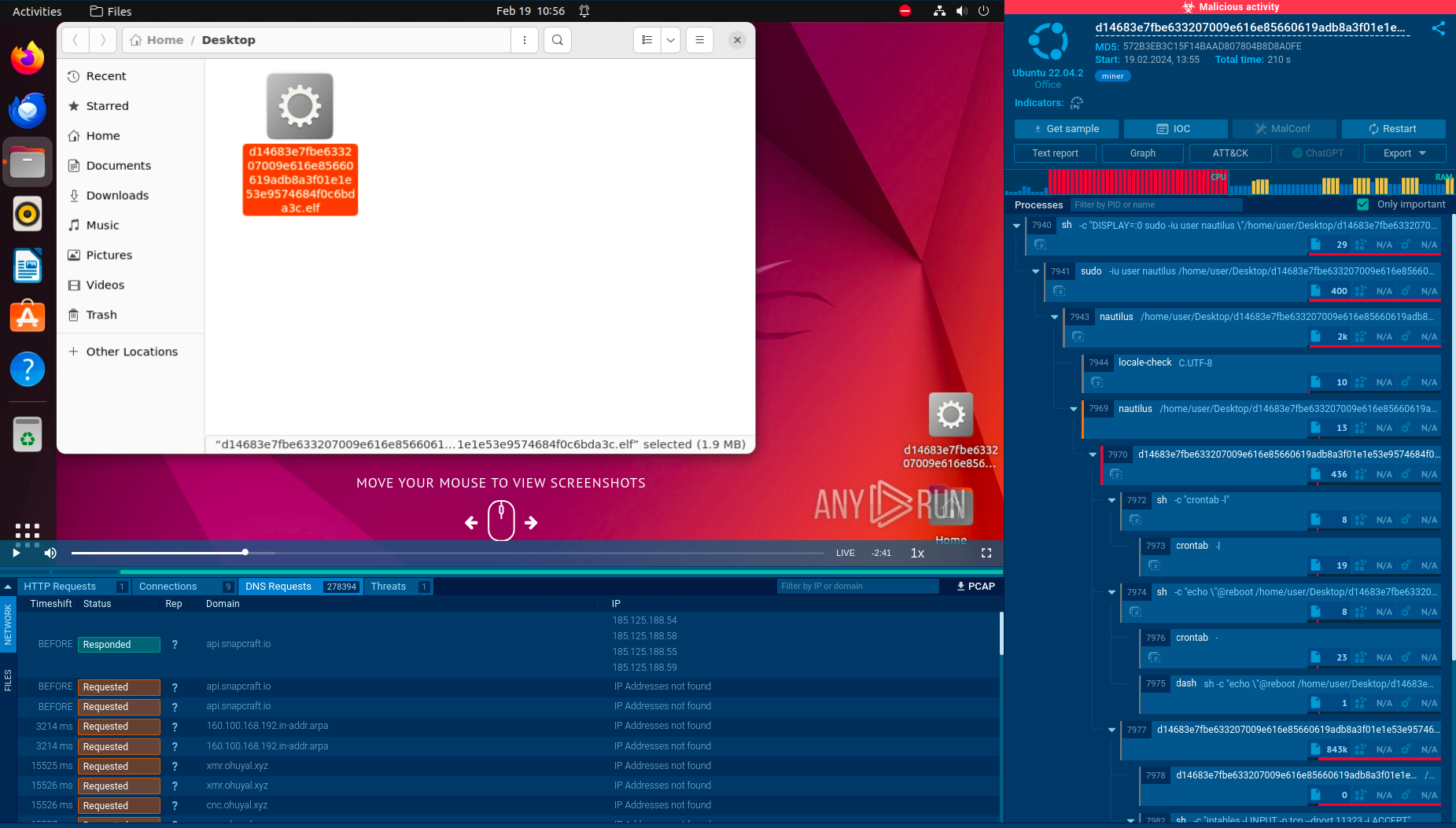
Stealc Malware Analysis Overview by ANY RUN

Lets Defend: Malware Analysis Fundamentals by Sakshee Bapat Medium

Top Malware Analyst Certification Programs for Aspiring Cybersecurity

Top Malware Analyst Certification Programs for Aspiring Cybersecurity

Top Malware Analyst Certification Programs for Aspiring Cybersecurity
Exploring Malware Types: From Viruses to RATs 29 Tools for Faster

OALABS: Malware analysis Reverse Engineering Course Expert Training
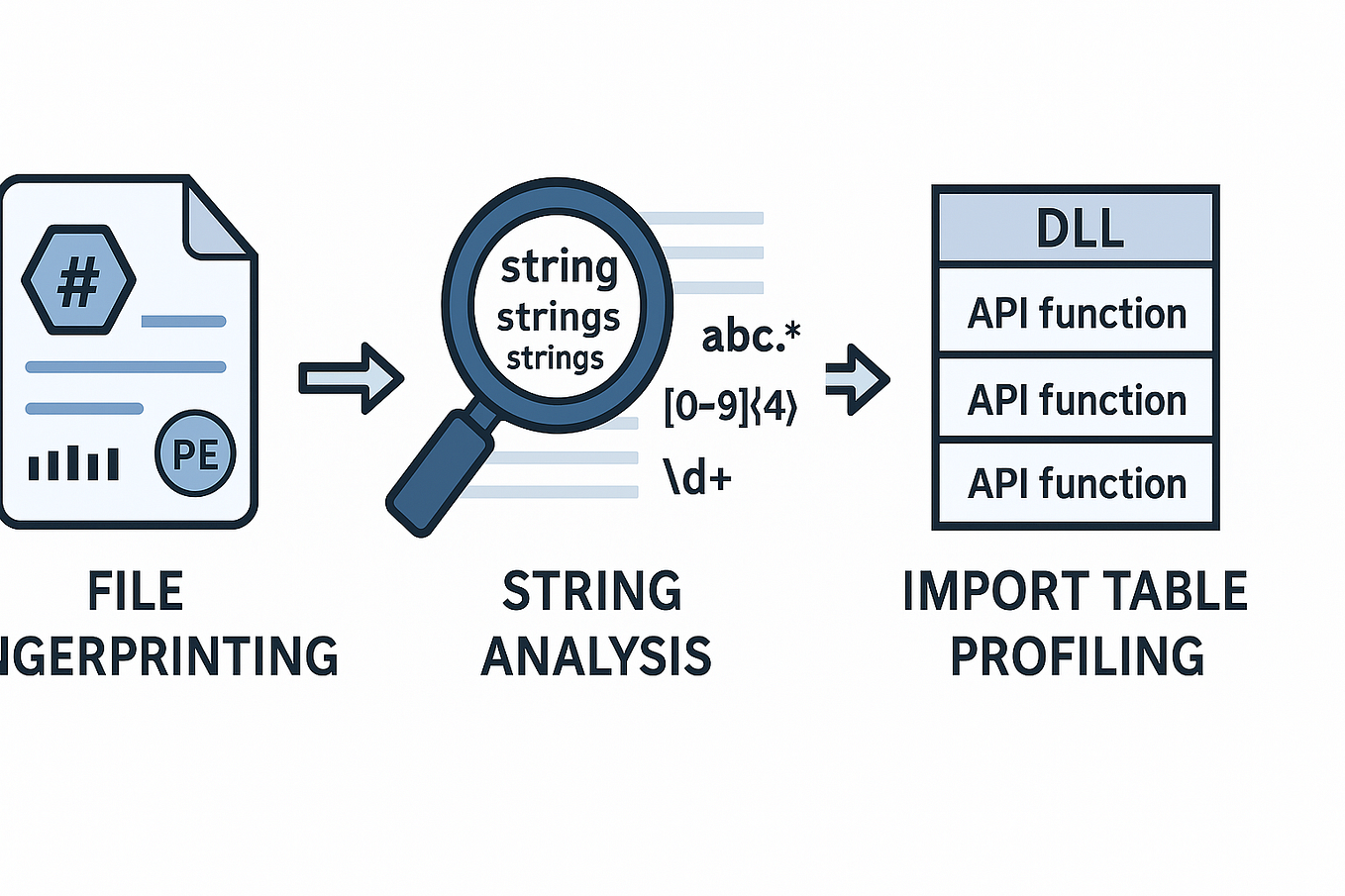
Building a Malware Analysis Lab with VMware Workstation: A Step by Step
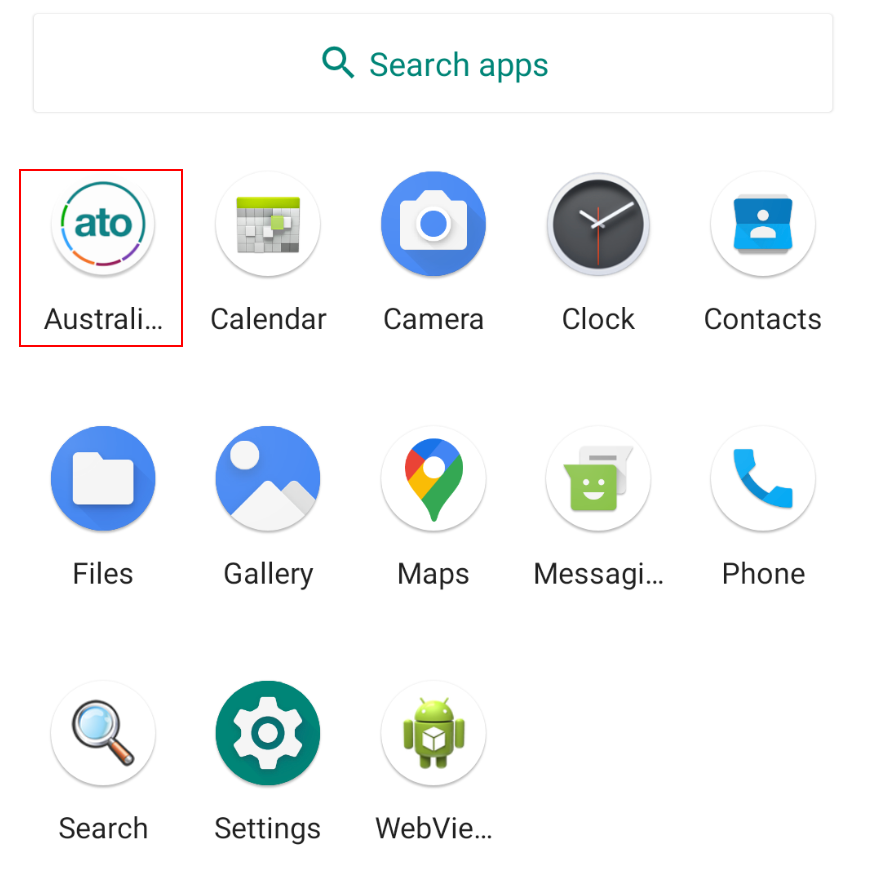
Android Malware Analysis Series ATO apk Part 3 1 · n0ps
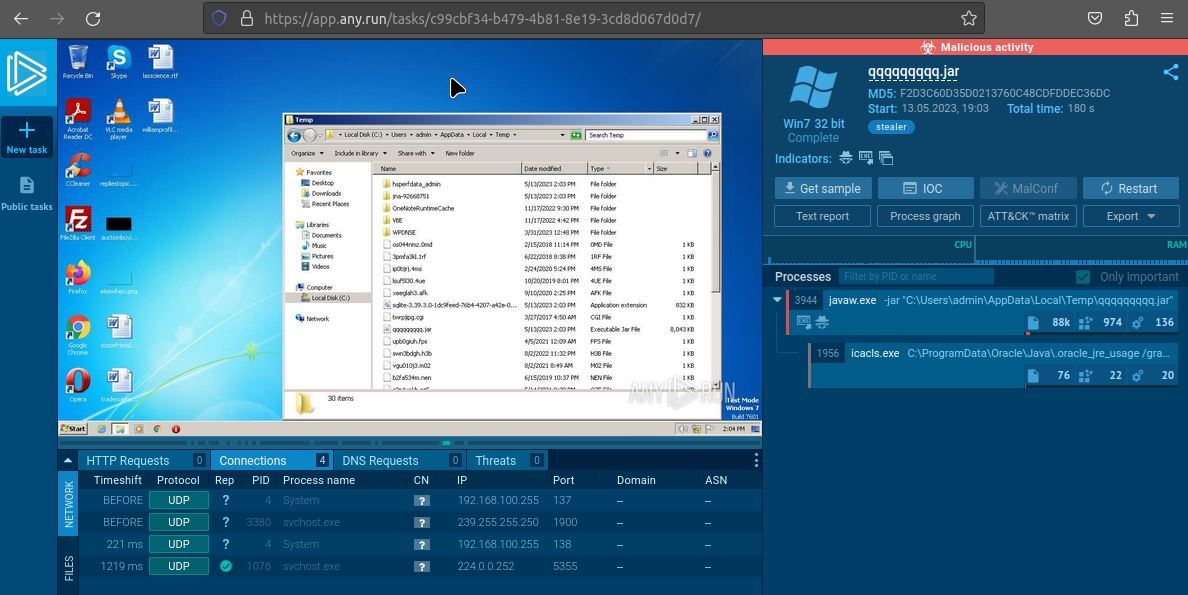
5 Free Online Sandboxing Tools to Test Applications and Files for Malware

Intro to Malware Analysis What to do when you run into a by

Practical Junior Malware Researcher (PJMR) Certification Review

دوره Malware Analysis Fundamentals آکادمی راوین

Earned a new certification: Malware Analysis and Assembly Shefali

Unpacking a UPX Malware Demystifying UPX: Unpacking the Secrets by

Unpacking a UPX Malware Demystifying UPX: Unpacking the Secrets by

#opswat #ofsa #malware #fileuploads #certification #analysis #cdr #

Complete OSWE Certification Guide (2025 Edition)

Received My ISC2 Certified in Cybersecurity Course Completion

Practical JuniorTester TCM Security

Practical Malware Research Professional (PMRP) Certification TCM Security

Practical Malware Research Professional (PMRP) Certification TCM Security