Phishing Email Response Template
Here are some of the images for Phishing Email Response Template that we found in our website database.

Complete Guide to Phishing: Techniques Mitigations Valimail

What is a Phishing Attack and How to Prevent It? SSL Dragon

Phishing Attack: Definition Types and Prevention
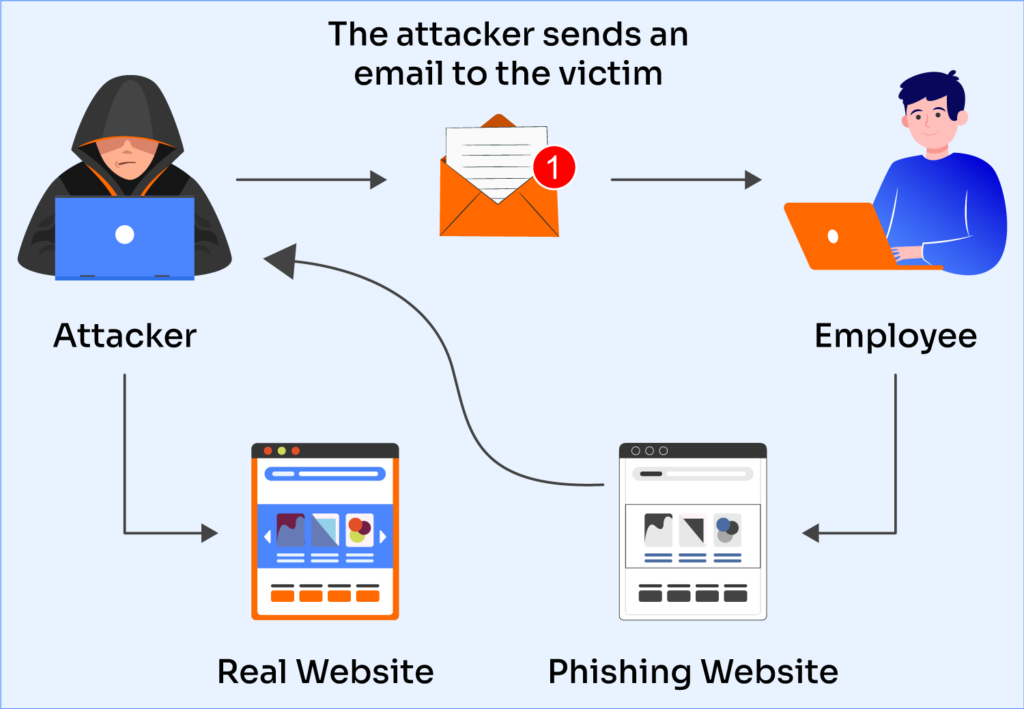
Phishing Prevention Best Practices: How to Detect Avoid Valimail

Phishing Attack Prevention: How to Identify Avoid Phishing Scams

Understanding and Avoiding Online Phishing: A Comprehensive Guide

Phishing: qué es y cómo evitarlo ¡Identifica una de las técnicas

Common Indicators of Phishing Attacks Technology Solutions

How to Handle Phishing Attacks Be Structured Technology Group

What Is Phishing In Cyber Security And How To Prevent it? It Support

20 types of phishing attacks phishing examples Norton
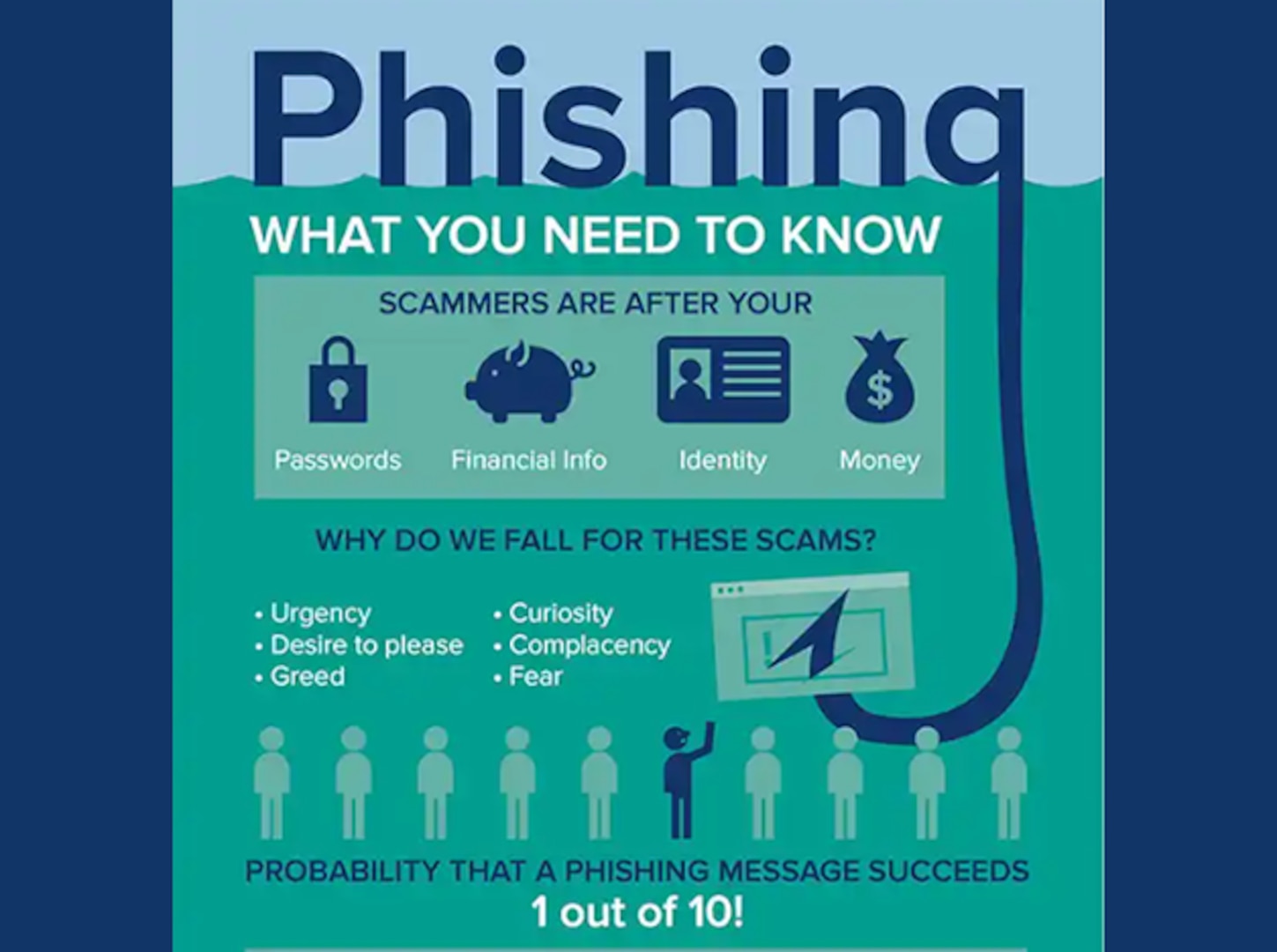
Cybersecurity Awareness Month: Recognizing reporting phishing gt Joint
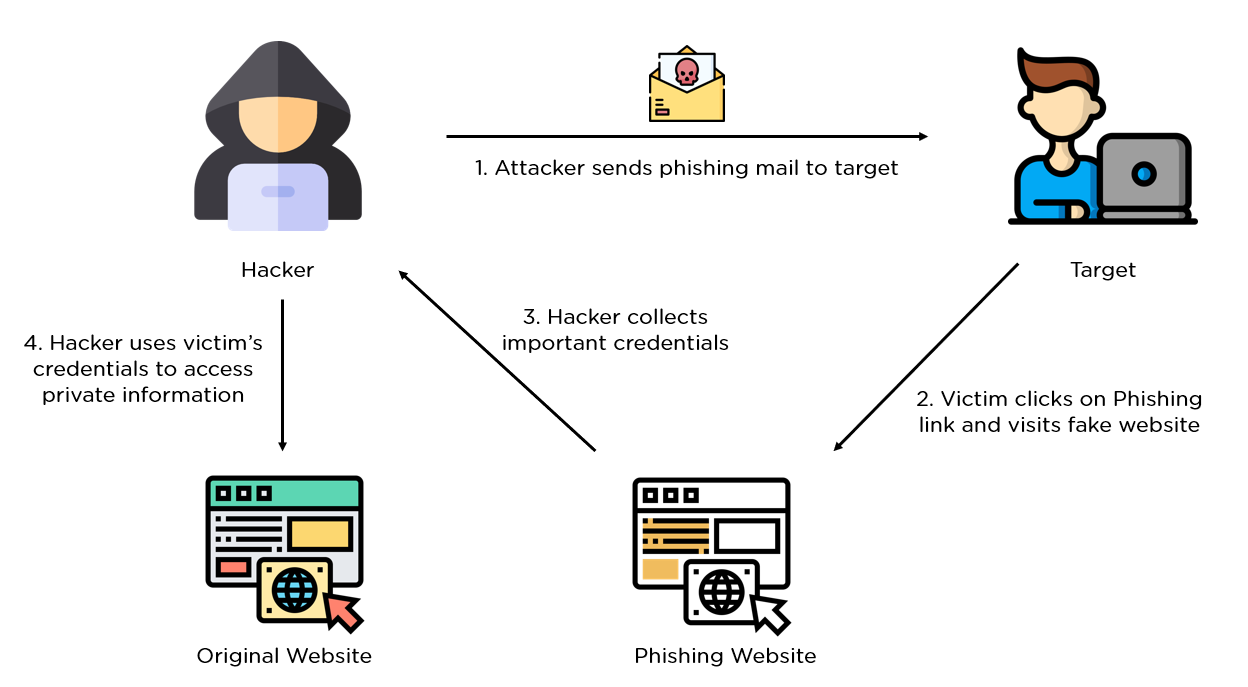
Novel interpretable and robust web based AI platform for phishing email

20 types of phishing attacks phishing examples Norton
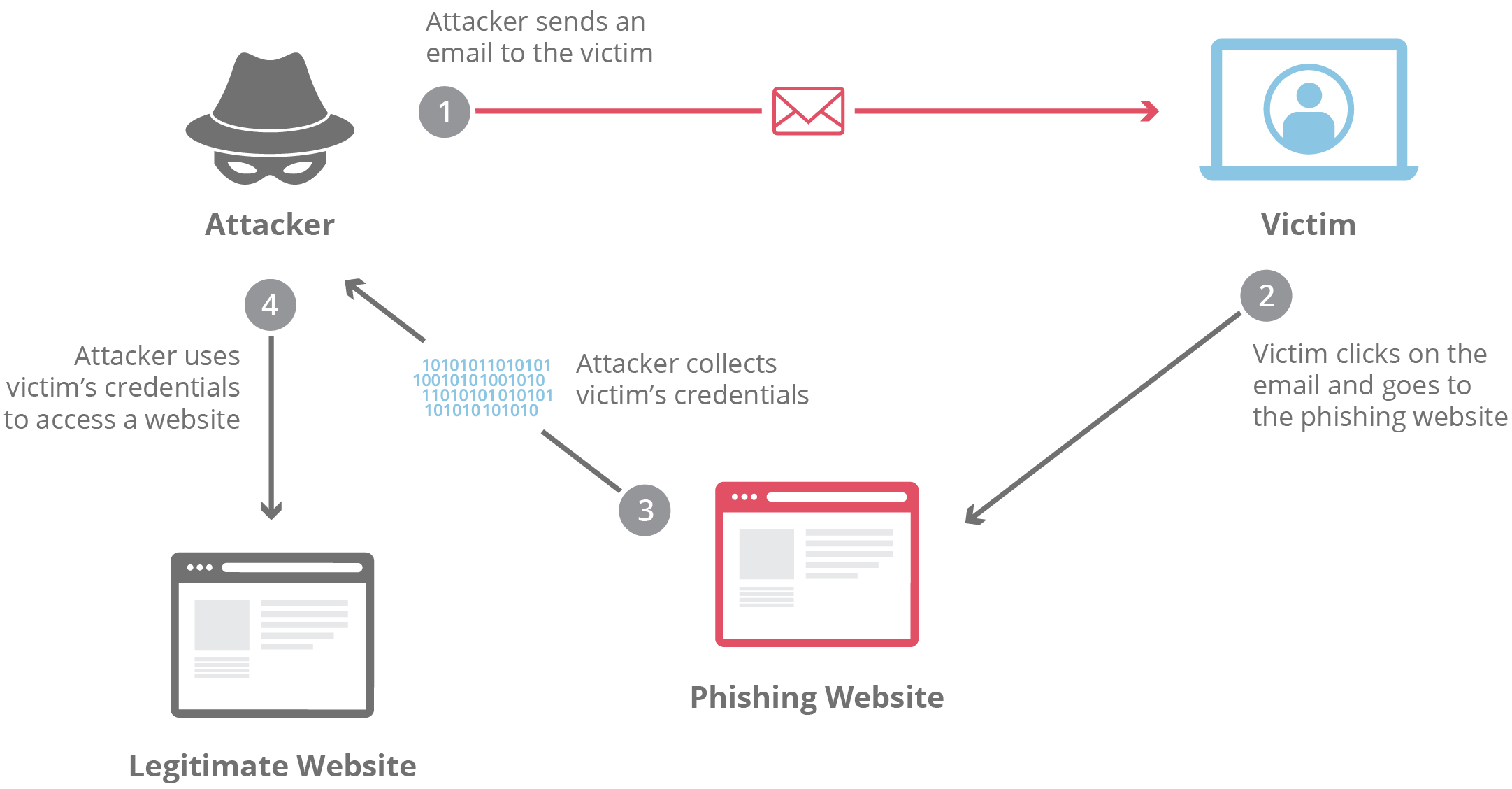
What is phishing? Phishing attack prevention Cloudflare

Phishing Email Examples How to Spot a Scam Intersys Blog

The Major Types of Phishing Attacks How to Identify Them: The

How To Identify And Handle Phishing Emails: A Complete Guide EIRE Systems
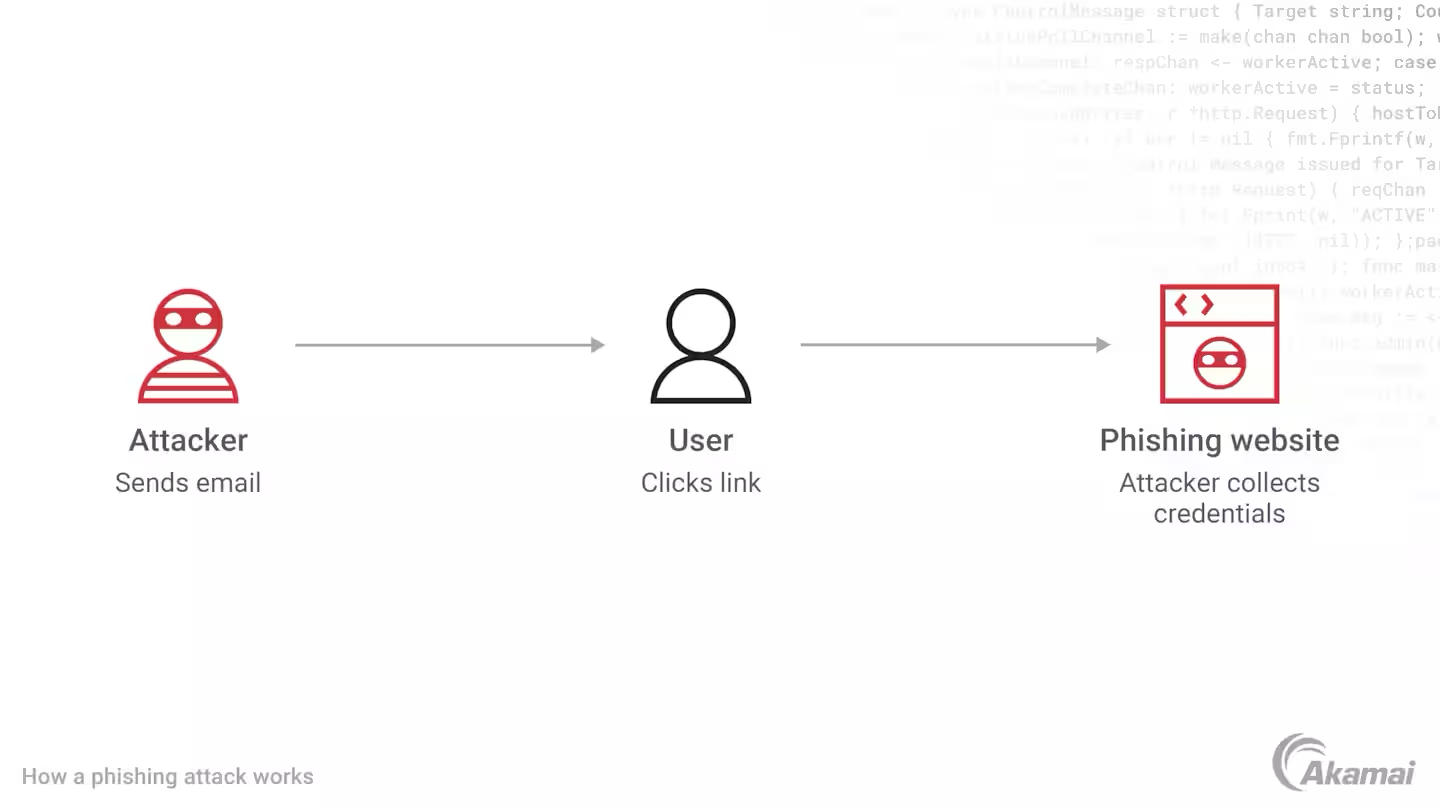
Understanding A Phishing Attack Phishing Attack Alert: How Scammers
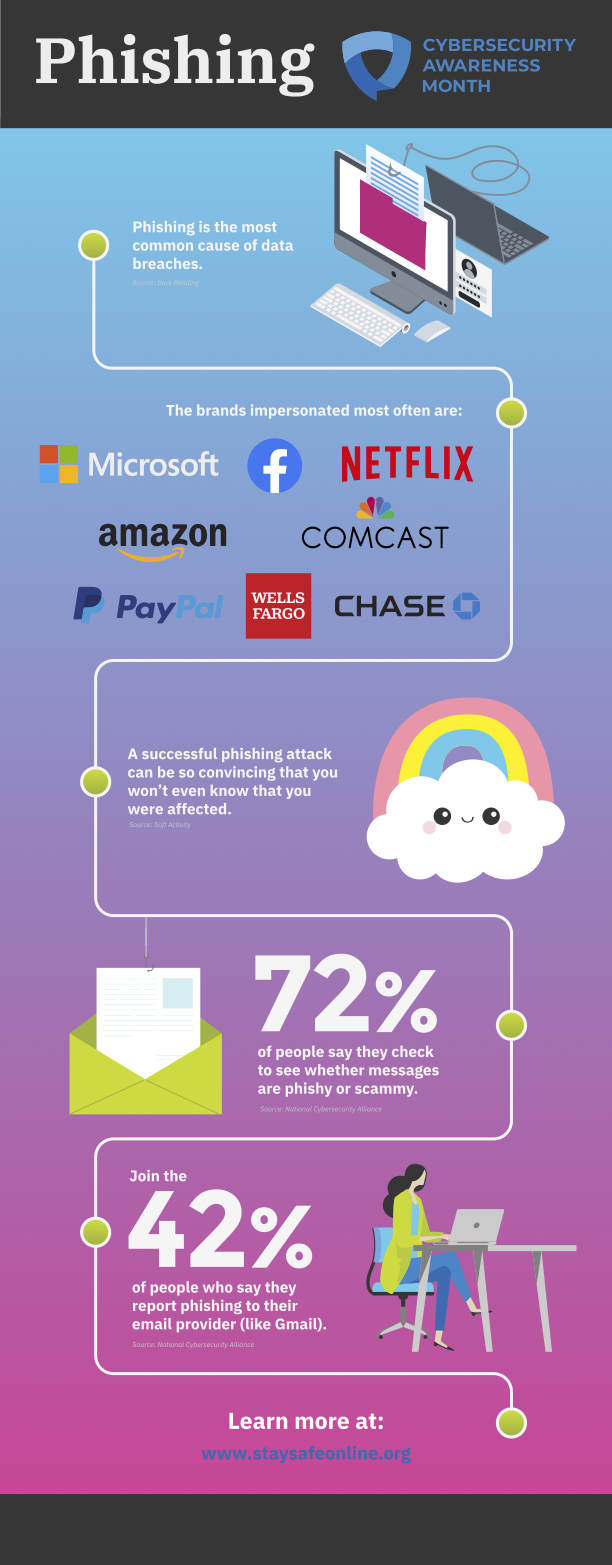
How to recognize avoid and report phishing Information Security
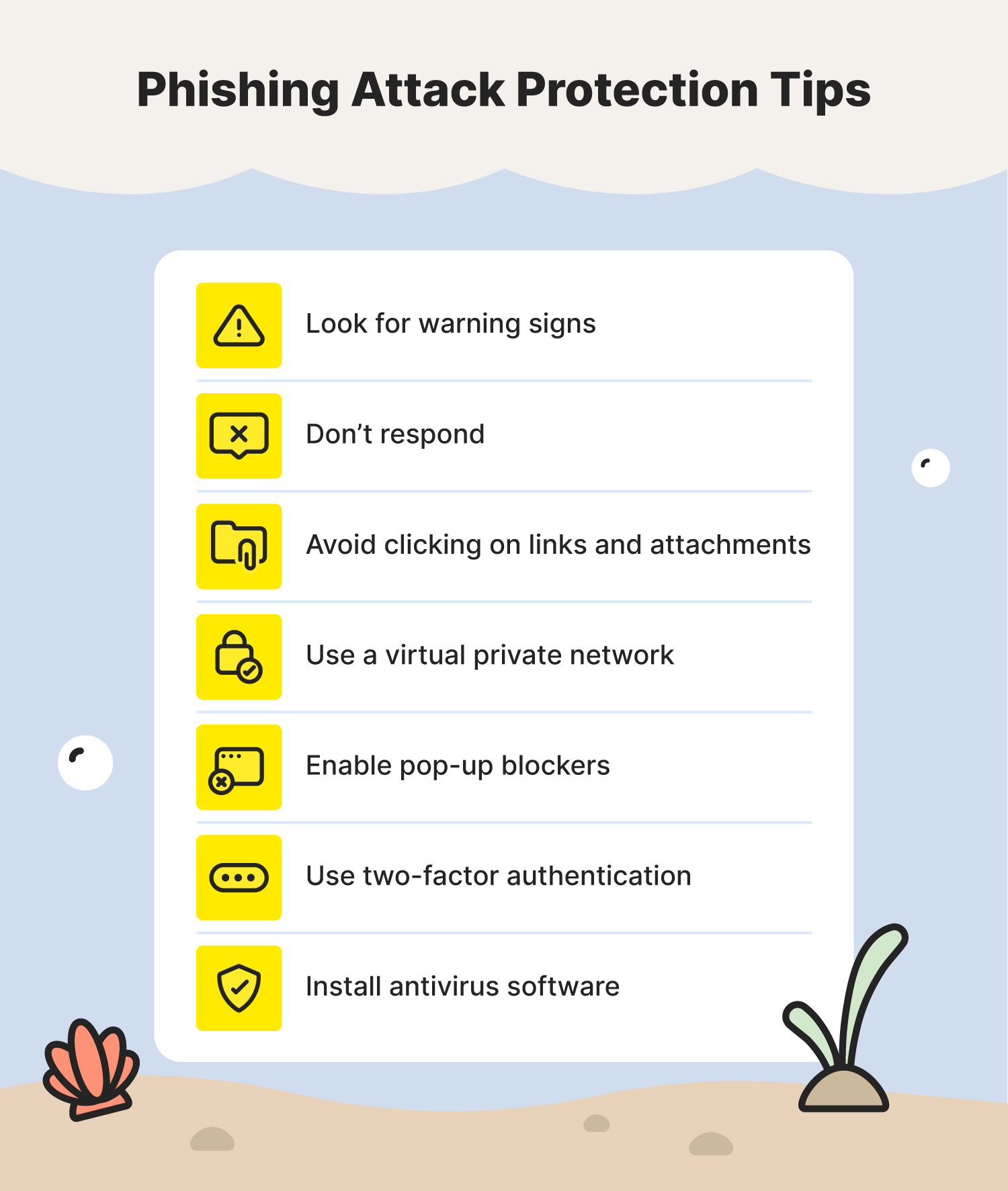
20 types of phishing attacks phishing examples Norton

Phishing platform Lucid behind wave of iOS Android SMS attacks

Phishing Email Examples and Their Impact EasyDMARC

How to Protect Your Business From a Phishing Attack

Phishing Techniques Cybiant Knowledge Centre Cybiant
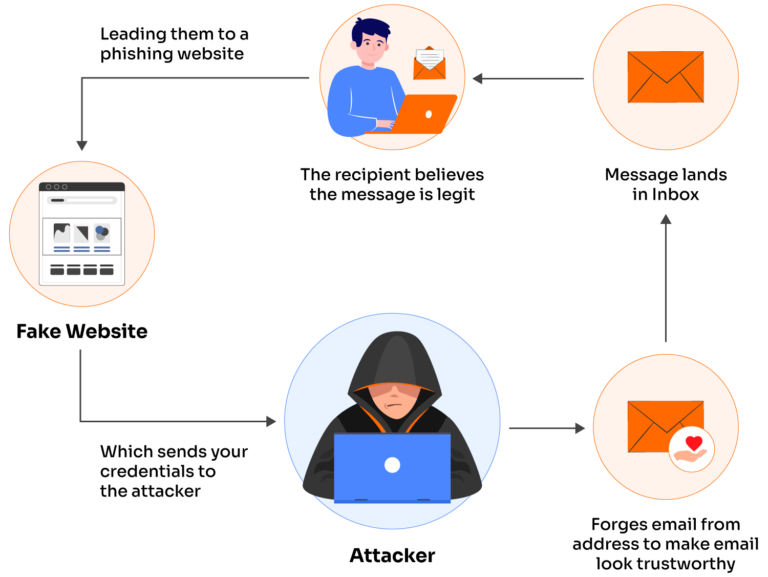
Understanding A Phishing Attack Phishing Attack Alert: How Scammers

Phishing Attacks: How to Identify Avoid and Safeguard Against This

5 Ways to Detect Phishing Email

What is Spear Phishing? Meaning Attacks and Examples

Phishing Awareness Program and CyberSecurty Services

Phishing Tips tricks and strategies to protect your business and

Targeting Phishing Attacks: Security Best Practices to Protect Your

Phishing Messages Elizabethtown College ITS Blog

15 Types of Phishing and How To Protect Your Business Graphus

Phishing Season