Security Camera Policy Template
Here are some of the images for Security Camera Policy Template that we found in our website database.

超过 3100000 张关于 网络安全 和 网络安全 的免费图片 Pixabay

What Is Cybersecurity? Forage

aimssoft com

ISO/IEC 27032:2023 Cybersecurity Guidelines ANSI Blog

Perusahaan Penyedia Jasa Security Profesional Hubungi Bilss

Ontario Security Group Your Trusted Security Partner

Download Woman Security Surveillance Royalty Free Stock Illustration

8 000 Free Security Firewall Firewall Images Pixabay

Software Security: Definisi Tipe Dan Kegunaannya Coding Studio

7 Best Practices of Data Security for Businesses in Tech Corporate

CloudBric: The Future of Cloud Computing and Cyber Security by Carl

Security Guard Provision (573)578 9930 Security Services Code 3

Duties and demand of Security guard services in Los Angeles CITIGUARD

Zero Trust as a Cybersecurity Measure FSR Inc AV Connectivity
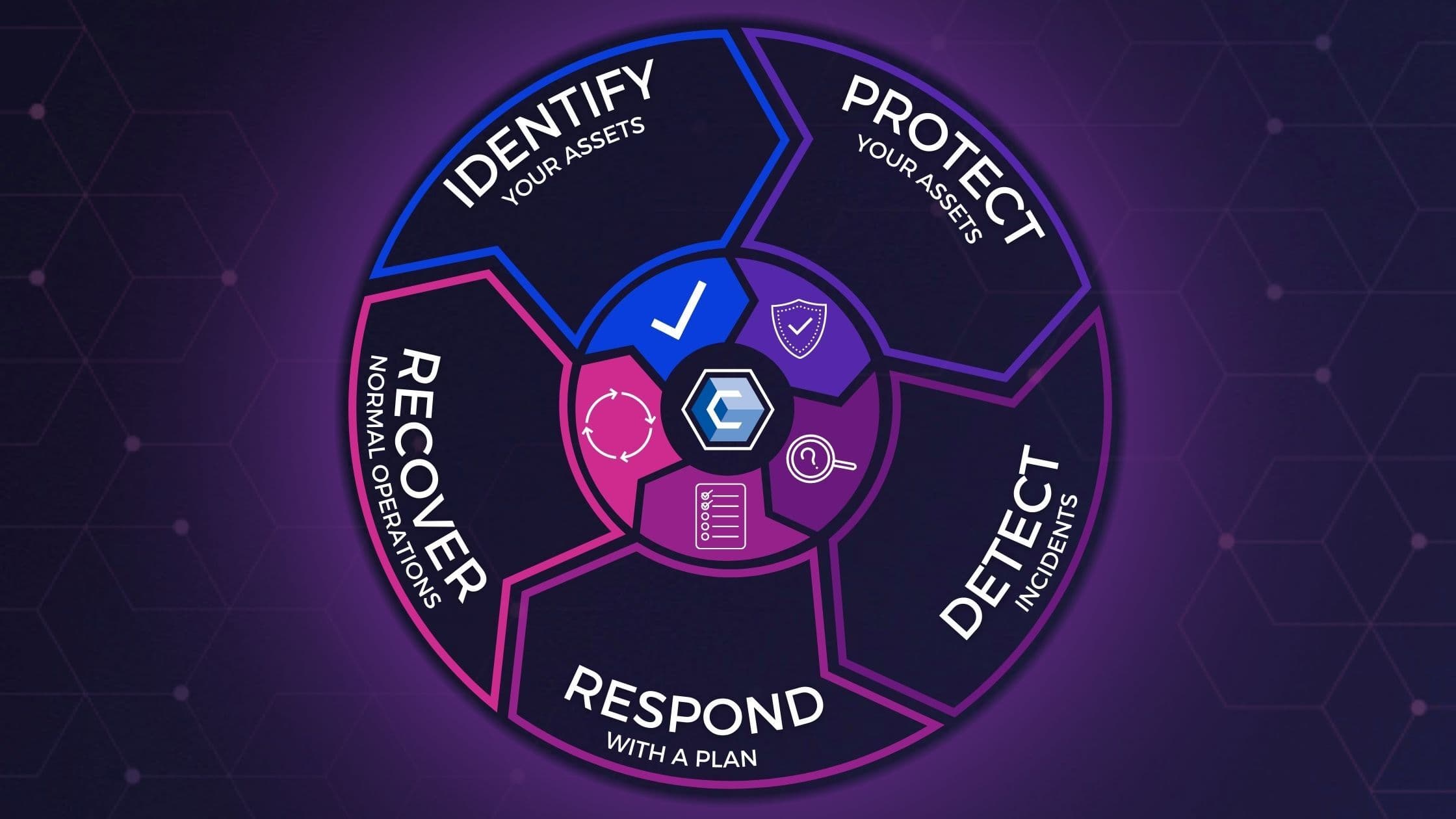
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

Unmasking The Digital Shadows: Cyber Attacks On Iran #39 s Nuclear Ambitions

Solutions Security

10 000 Free Information Security Security Images Pixabay

Security Guard Images

What to Look for in Travel Security and Executive Protection Services

20 000 Free Health Safety Health Images Pixabay

Security Companies Johannesburg Complete List 2023

Bolstering cybersecurity readiness in the cloud Information Age

Cybersecurity Tips for Small Businesses

Security Photos Download The BEST Free Security Stock Photos HD Images

Agent de sécurité filtrage www securitsolutions fr

Greater business security flexibility with alarm system partitions EPS

What is a Secure Processing Center? Food Stamps

Lima Fitur Keamanan dan Privasi Maksimum iPhone TechForID

Cybersecurity Tunya Systems Limited
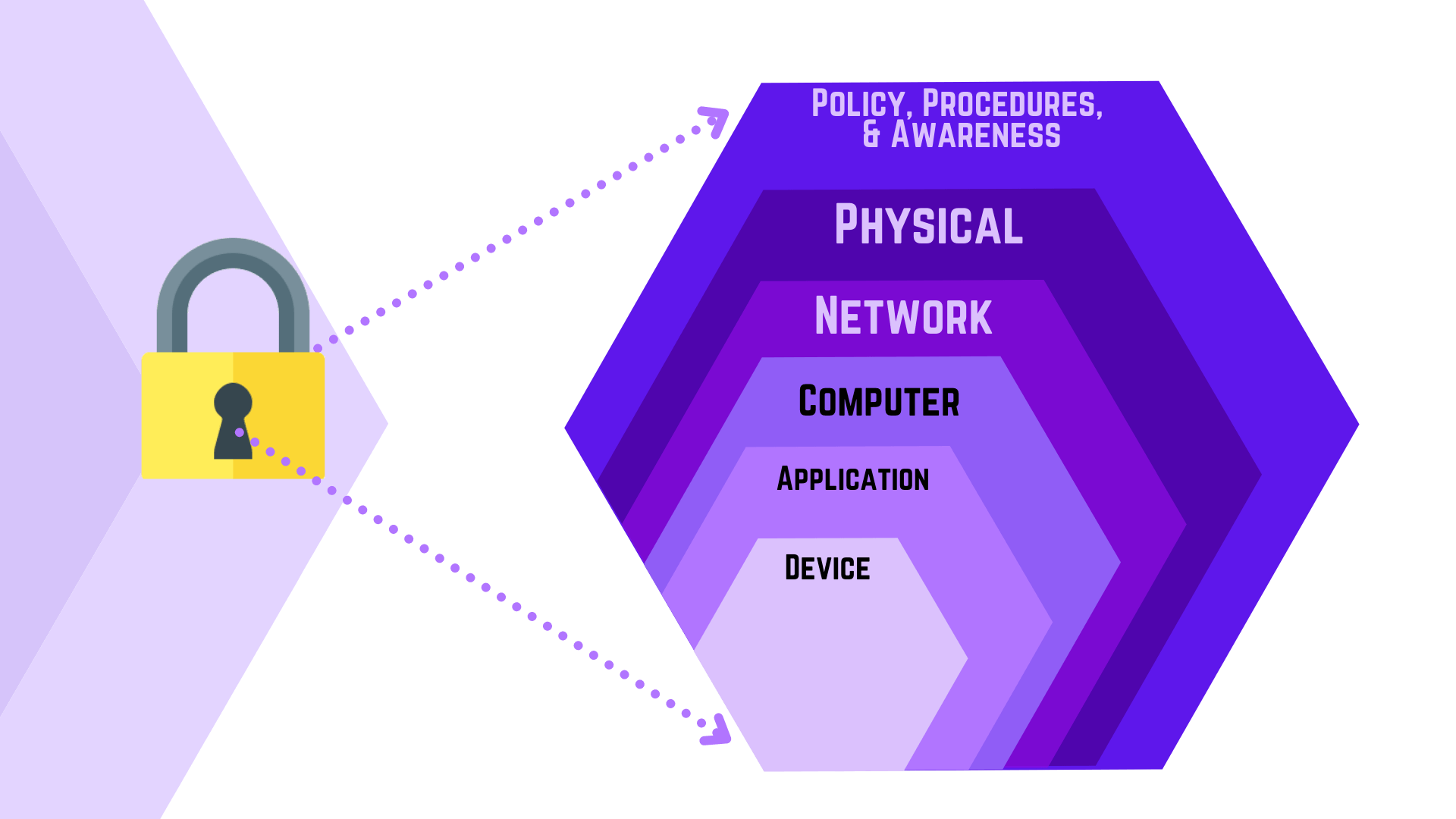
Strategies For Cyber Defense Technology Tronicspro

Cyber security in software development: 12 outsourcing tips

Why You Need To Be Carrying Out A Cyber Security Audit In Your Business

Cyber Security Stock Photos Images and Backgrounds for Free Download

5 Contoh Surat Lamaran Kerja Security/Satpam Lengkap dan Cara