Security Deposit Return Template
Here are some of the images for Security Deposit Return Template that we found in our website database.

Free security guard Stock Photos Pictures FreeImages

Benefits of Using Wireless Security Systems Minnesota Majority

3840x240 Resolution Cybersecurity Core 3840x240 Resolution Wallpaper
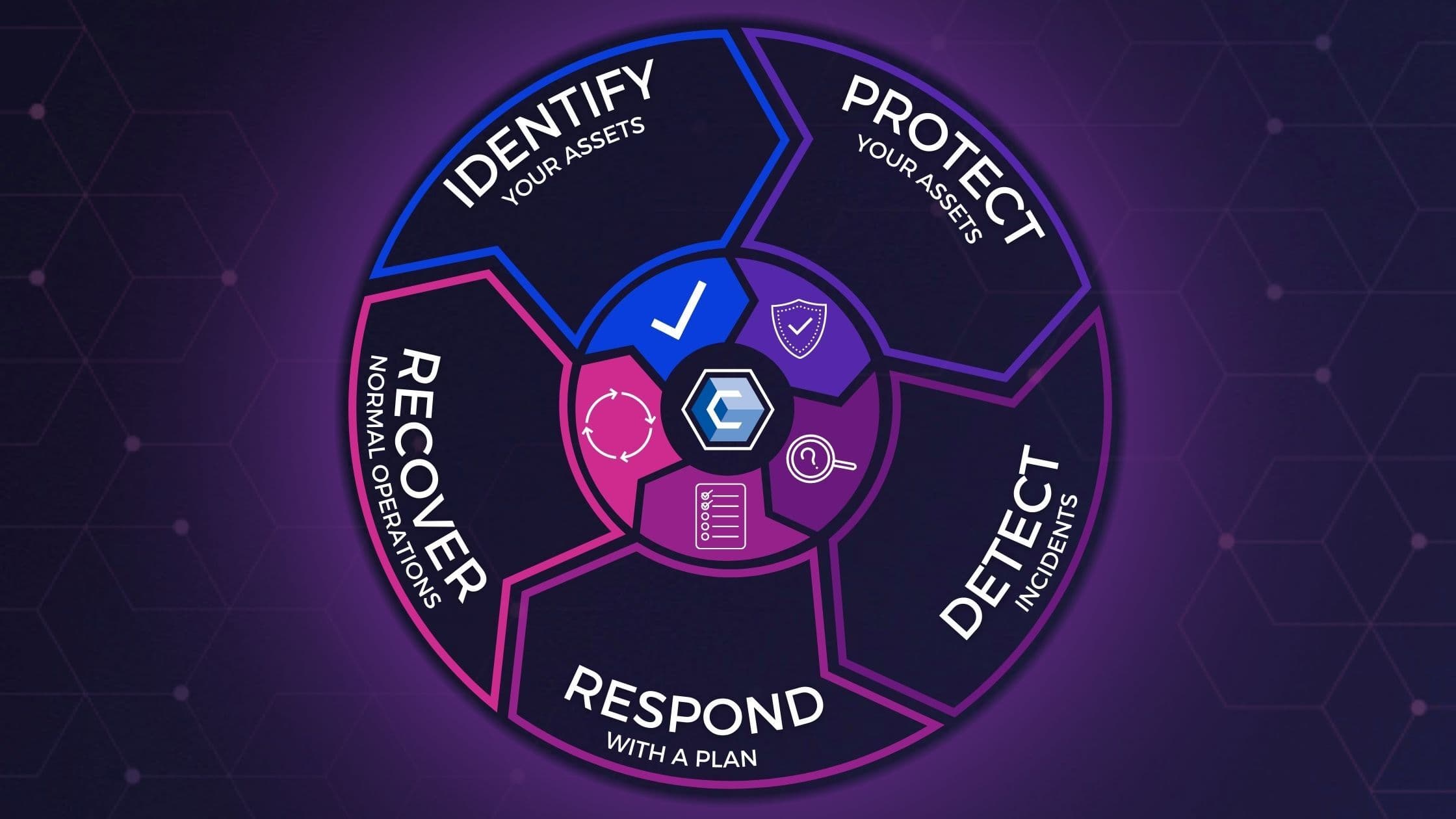
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES
Explorando os Benefícios das Câmeras de IA para Inteligência de Vídeo

Network security concept Cyber protection Anti virus software

Helping to shape the RMIT Centre for Cyber Security Research and

ISO/IEC 27032:2023 Cybersecurity Guidelines ANSI Blog

Cyber Security Vector Art Icons and Graphics for Free Download

Home Security System Define at Gustavo Martinez blog

超过 30000 张关于 网络安全风险评估 和 网络安全 的免费图片 Pixabay

Companies Worry In Cybersecurity To Rise In 2024 CIO Africa

What Is Cybersecurity? Forage

Cybersecurity Plan: 3 Keys for CISOs Trend Micro (US)

Cyber Security Concept Data Protection And Secured Internet Access

Gartner #39 s 8 Cybersecurity Predictions for 2023 2025 Krontech
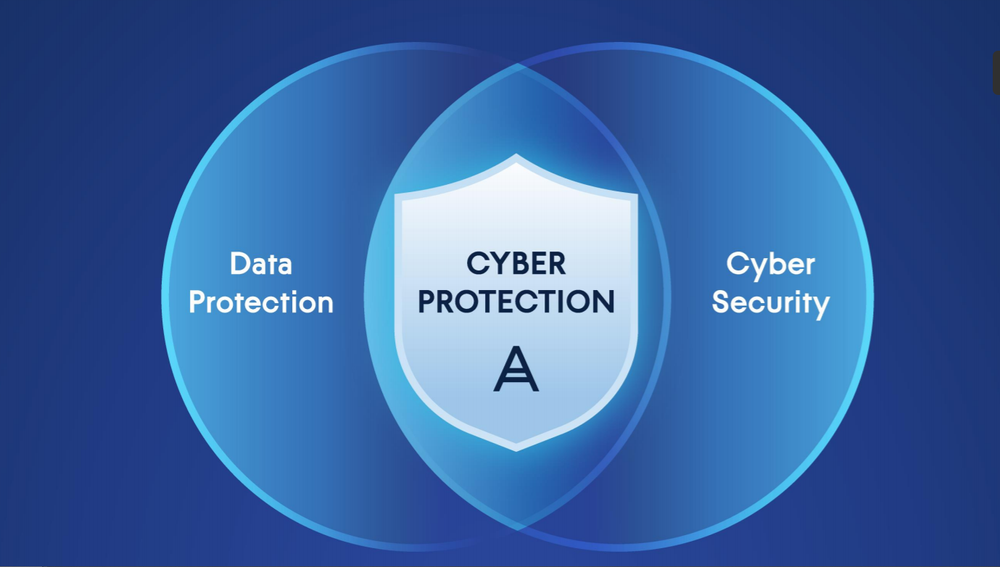
What is cyber protection? Definition Importance Types Cost Acronis

Cyber Security Threat Assessment: How to Manage Risk WBM Technologies

Cyber Attack Prevention Plan Elevated Tech Network Security
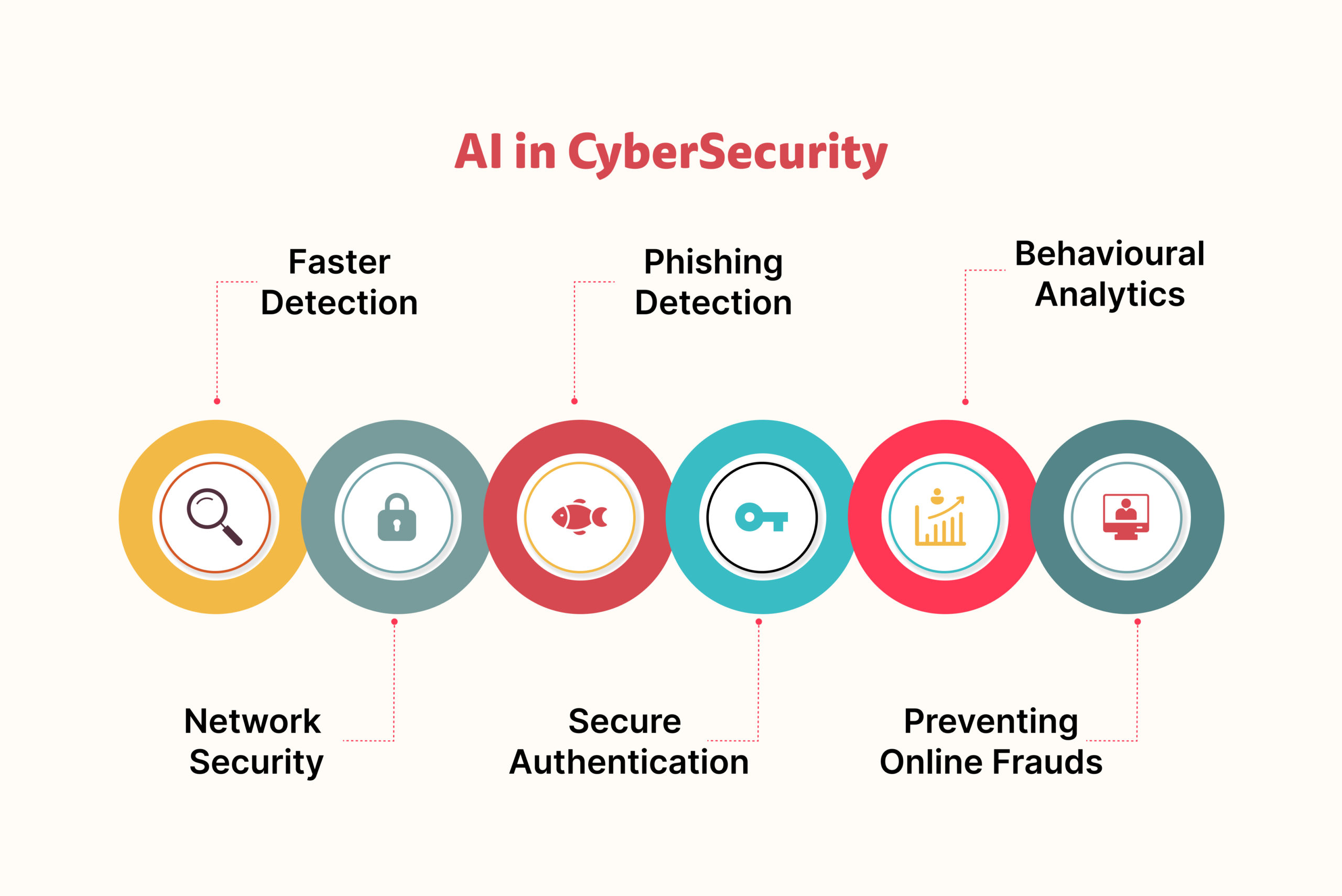
How AI in Cybersecurity Reimagines Cyberthreat

Understanding the 3 Phases of Cybersecurity Architecture Ardoq

Cybersecurity Tunya Systems Limited

Cyber Security Synpase

Security Risks With Ai

Karriere in der Security Branche: Jobs für mehr Sicherheit careeasy

How to Ensure Network Security? Logsign

BroadBand Nation: Cybersecurity Career Pathway (INFOGRAPHIC)

How To Secure Your Cryptocurrency Assets: Best Practices And Tools

Lock Cyber security Padlock With Keyhole icon made with binary code

Bolstering cybersecurity readiness in the cloud Information Age

Securing The Future: The Most Critical Cybersecurity Trends Of 2023

Simple Ways Hackers Steal Your Information and How to Identify Them

Importance of Cybersecurity in Business

Building a Robust Cybersecurity Awareness Program to Empower Your Workforce

Event Security Melbourne Security for Parties Events

Cybersecurity Fortification in Edge Computing Innovate

Emerging Technologies in Cybersecurity

Cyber security in software development: 12 outsourcing tips

Responsabilidades da Empresa em Caso de Incidente de Segurança

Cyber Security Company LinkedIn

Security Companies Johannesburg Complete List 2022

How To Hire A Security Guard Security On Demand Zuluhood

Physical Security Management: finding the optimal balance between

CyberSecurity: The goals are simple: safety and security Complete Chain
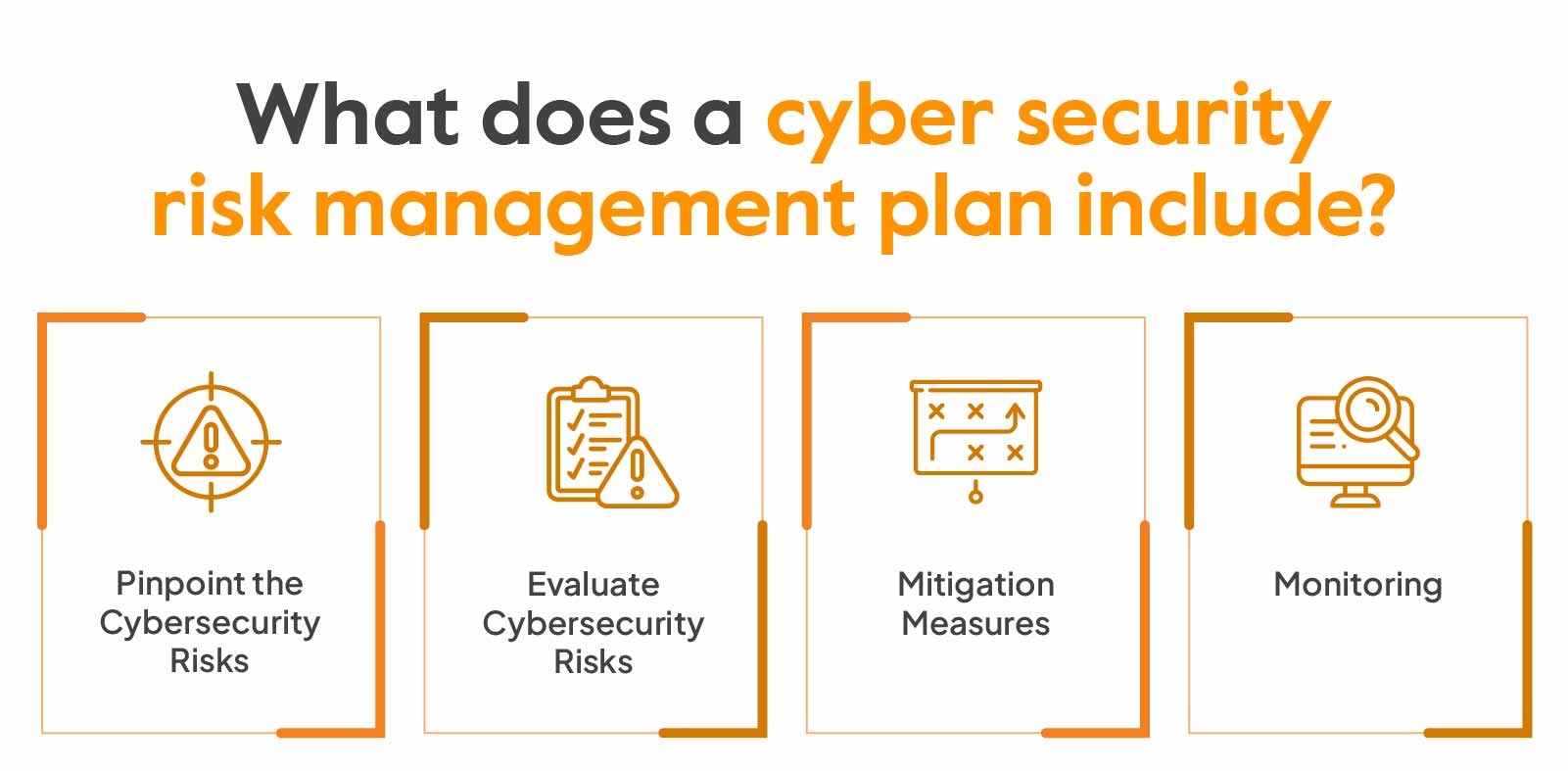
What is Cybersecurity Risk Management? Implementation Guide

Apartment Building Security First Security Protection Services

Considerations for security officer training in healthcare facilities

Cyber Security Introduction Part 1 Dev Community Bank2home com

Cyber Security Stock Photos Images and Backgrounds for Free Download

Can Security Guards Use Force? Intercept Security Services

20 Cybersecurity Skills to Boost (or Jumpstart) Your Career

Health Safety Security and Environment (HSSE) Advario

quot Navigating the Digital Realm: A Beginner #39 s Guide to Cybersecurity quot

Monitors AG Neovo Global

SOC As A Service Rockwell Automation

Qu #39 est ce que la sécurité réseau

Serviços De Segurança Edmonton Foto gratuita no Pixabay Pixabay

First Use Of Data Flow Diagrams For Cybersecurity Flow Syste
.png)
What are the Different Types of Cyber Security?

The History of Cyber Security: A Detailed Guide Updated