Security Desk Request Crossword Clue
Here are some of the images for Security Desk Request Crossword Clue that we found in our website database.

400 Free Surveillance Security Images Pixabay

700 Gambar Introduction To Cybersecurity Cybersecurity Gratis Pixabay

Download Ai Generated Cybersecurity Firewall Royalty Free Stock

What Are the Pros and Cons of Cyber Security? Technology Solutions

The Future of Global Private Security Night Eyes Protective Services Inc

What Is Cybersecurity? Forage
Qué es OSINT: cómo descubrir información sin hackear

Digital Definition Cyber Security at Matthew Tindal blog

Cyber Security Technology And Online Data Protection In An Innov
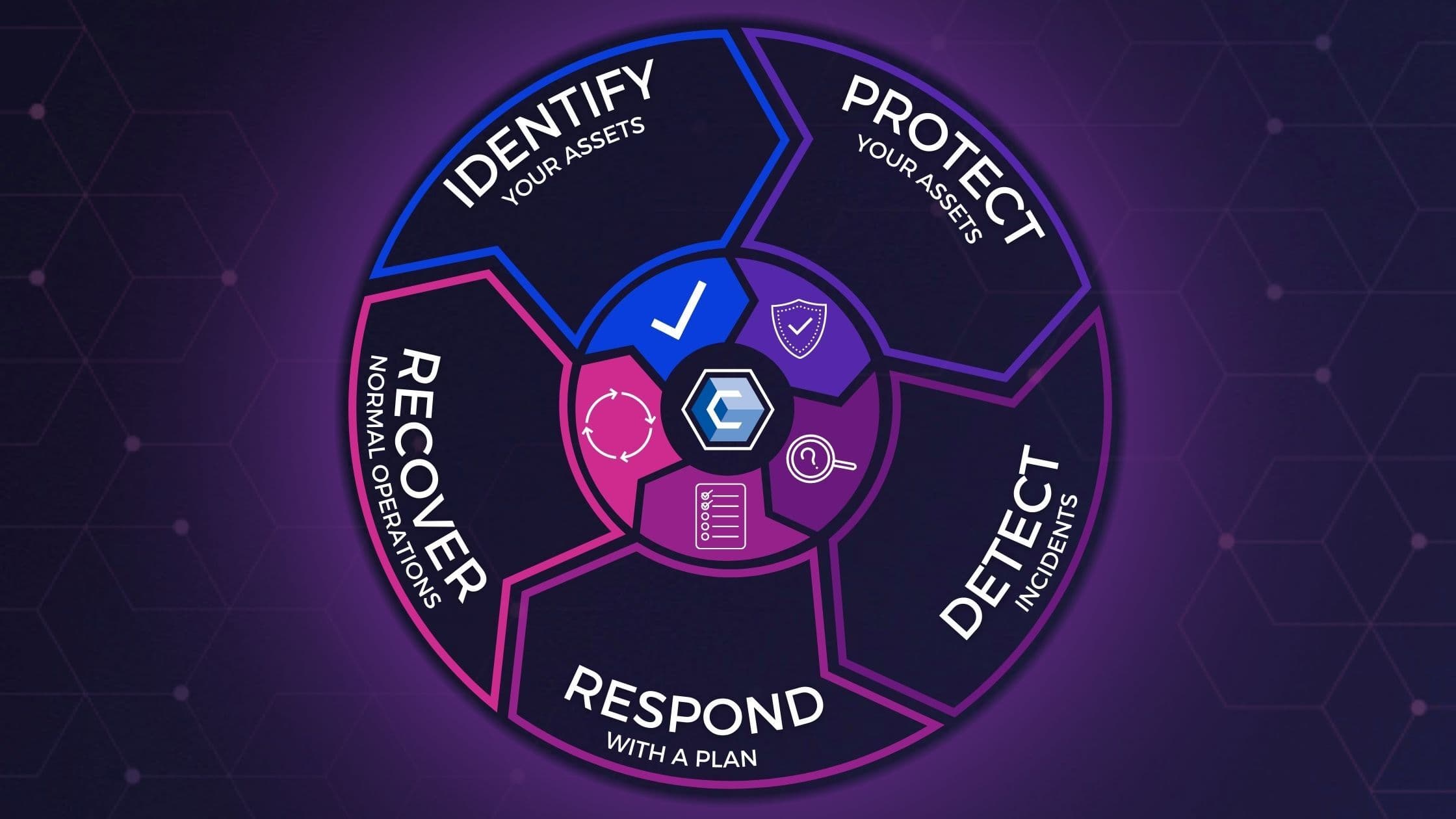
Reviewing the 5 Stages of the Cybersecurity Lifecycle EXAMPLES

Mobile Patrols Marvasti Security

How is Edge Security Helping Secure Devices that Use Edge AI? Xailient

300 000 Free Cyber Security Wallpaper Cyber Security Images Pixabay

Need Of Secure Protocols

Understanding the 3 Phases of Cybersecurity Architecture Ardoq

Cyber Security Introduction Part 1 Dev Community Bank2home com

Why Should Cybersecurity Be Taught In Schools?

Protecting California: A Comprehensive Guide To Security Guard Services
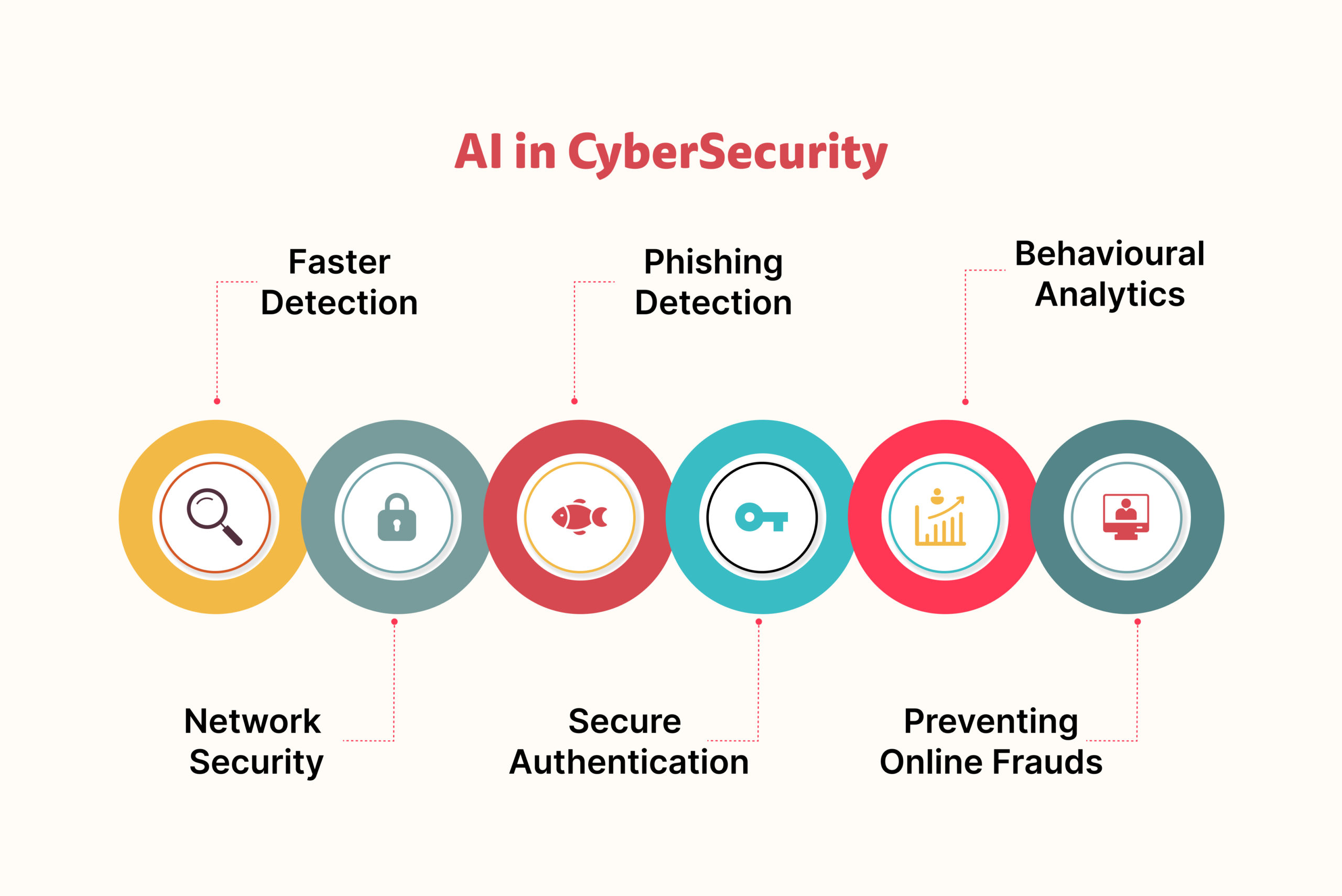
How AI in Cybersecurity Reimagines Cyberthreat

Importance of Cybersecurity in Business

10 000 Free Security Guard Security Images Pixabay

What is GLBA Compliance? Key Requirements and Concepts BD Emerson

Security Guard Provision (573)578 9930 Security Services Code 3

Bolstering cybersecurity readiness in the cloud Information Age

Physical Security Services Armed and Unarmed RiP Group

Security Companies Johannesburg Complete List 2023

How to Evaluate Your Business #39 s Cybersecurity Posture: Key Steps for a

4500x5500 Resolution Cybersecurity Core 4500x5500 Resolution Wallpaper

What Is Cloud Migration Security? Implementation Checklist

CCTV Installation: Day Versus Night Security

Drones Security Sales Integration

Cyber security in software development: 12 outsourcing tips

What is a DMG File? Understanding Mac Disk Images

CSA Asset Security

Simple Ways Hackers Steal Your Information and How to Identify Them