Select The Eap Protocol That Uses Digital Certificates For Authentication
Here are some of the images for Select The Eap Protocol That Uses Digital Certificates For Authentication that we found in our website database.

Select Button Png

Sql Select Examples

Select Stamp Set Select Square Grunge Sign Stock Vector Illustration
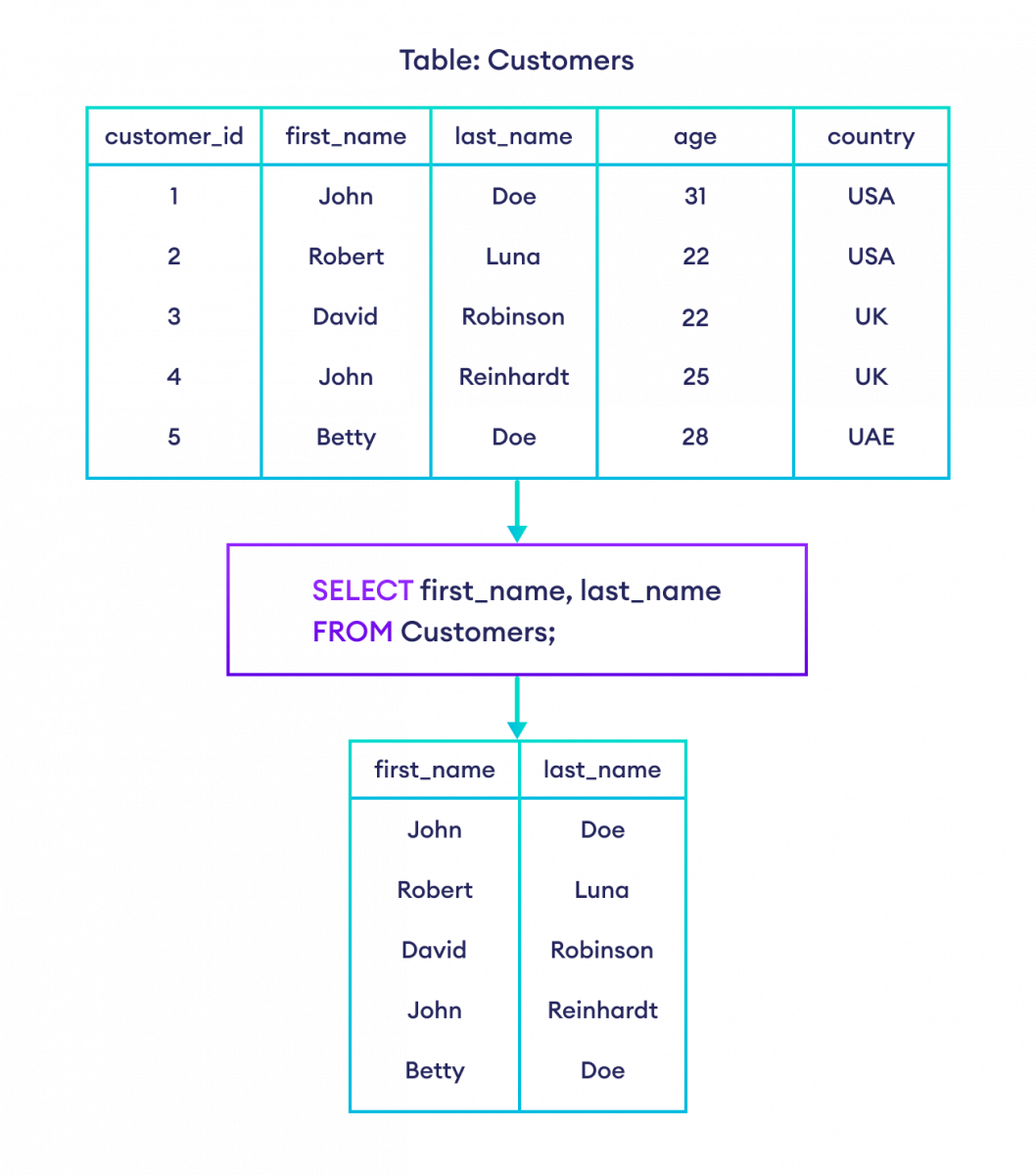
SQL SELECT and SELECT WHERE (With Examples)

How to use SQL Select? Explanation with example
select concept line icon Simple element illustration select concept

SQL SELECT Statement How to Select Data from a Database
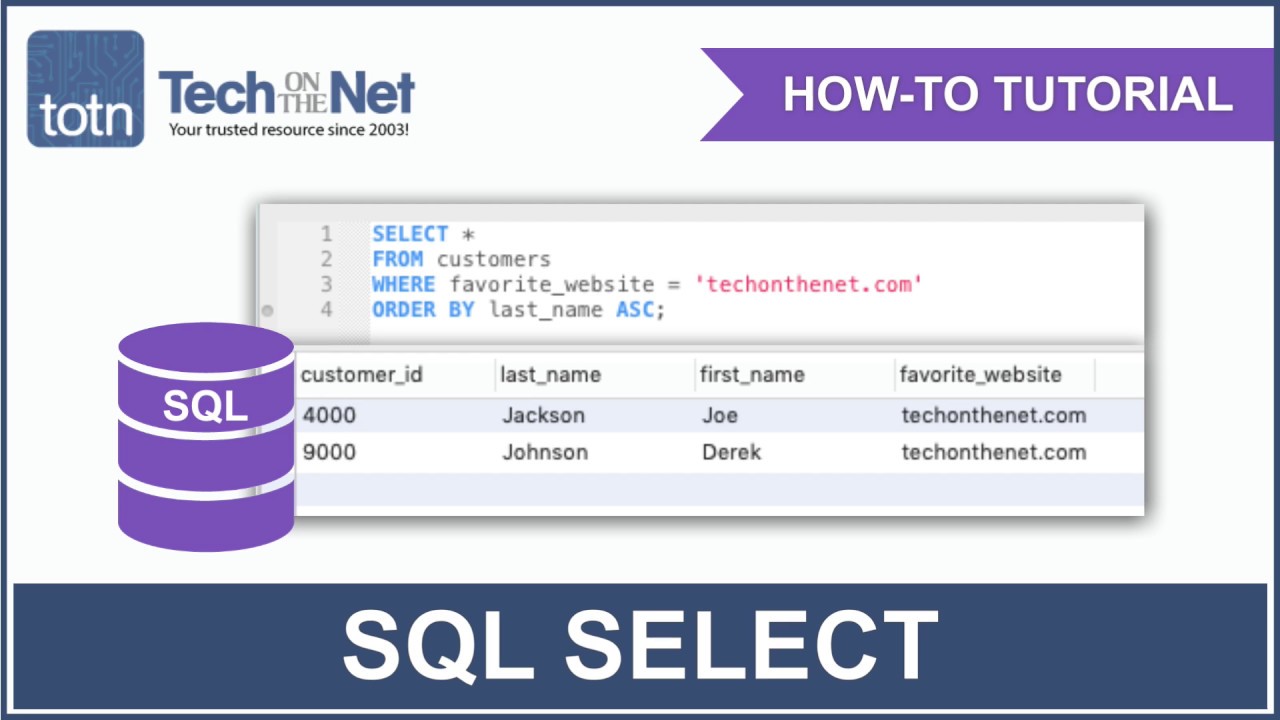
How to use the SQL SELECT Statement YouTube

Learn SQL: SELECT statement

Select stamp select label round grunge sign Vector Image
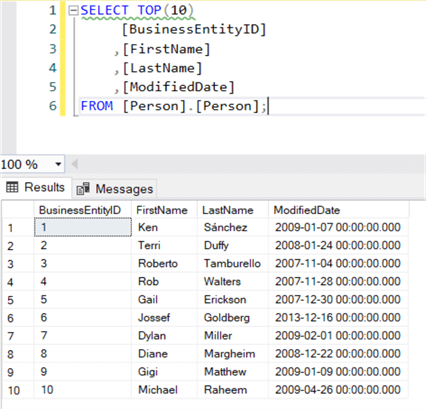
SQL Server SELECT Examples

SQL SELECT Statement SQL SELECT Query with Example
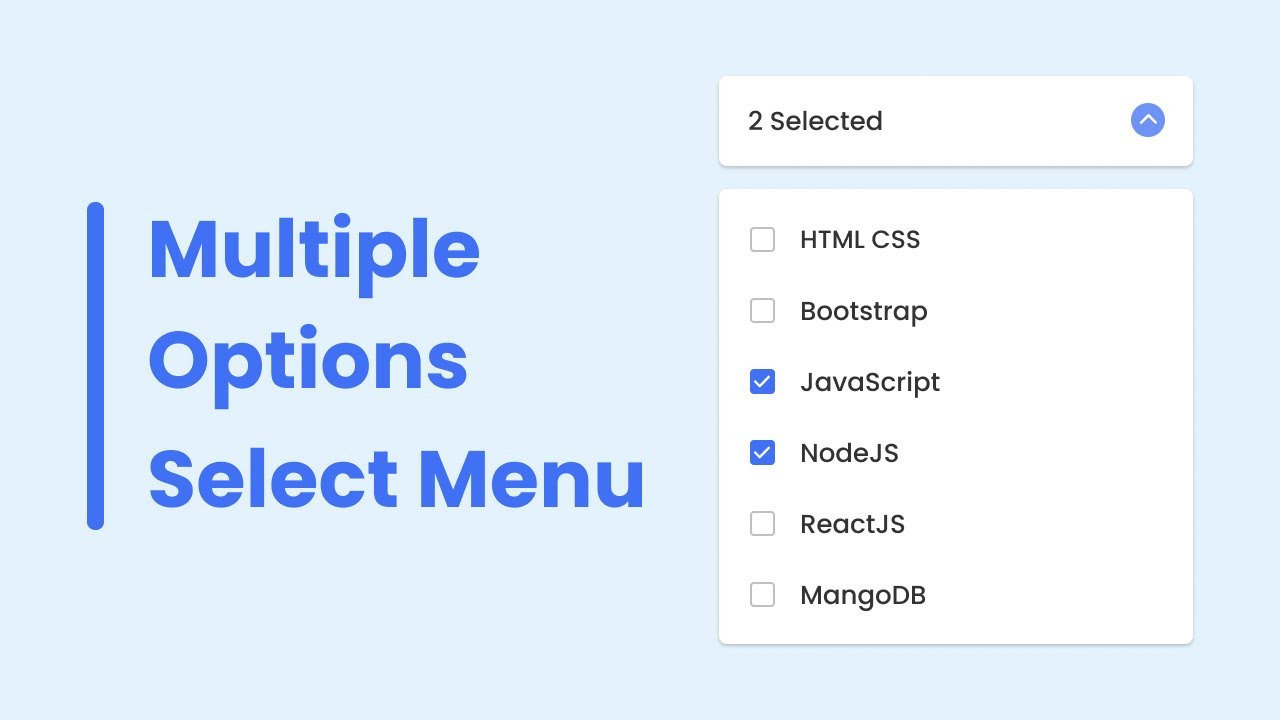
Multiple Options Select Menu in HTML CSS JavaScript YouTube

SQL SELECT statement

Our selection Stock Photos Royalty Free Our selection Images

Hand Find Select Person In Line Of People Stock Illustration Image

Speech Select blue cloud frame and wire frame bifurcation arrow left

SQL Select Statement: Tutorial Simply Coding

Select Restaurant LinkedIn

Select

SQL Select Statement and Query Examples
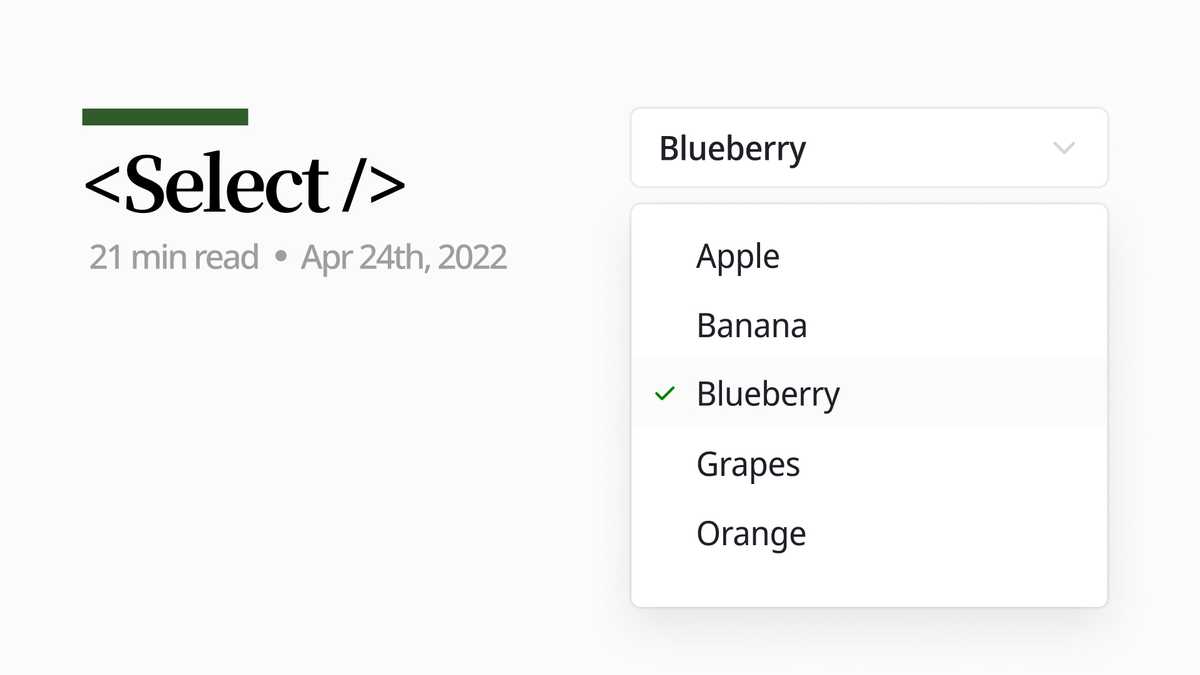
Select 컴포넌트 SOSOLOG
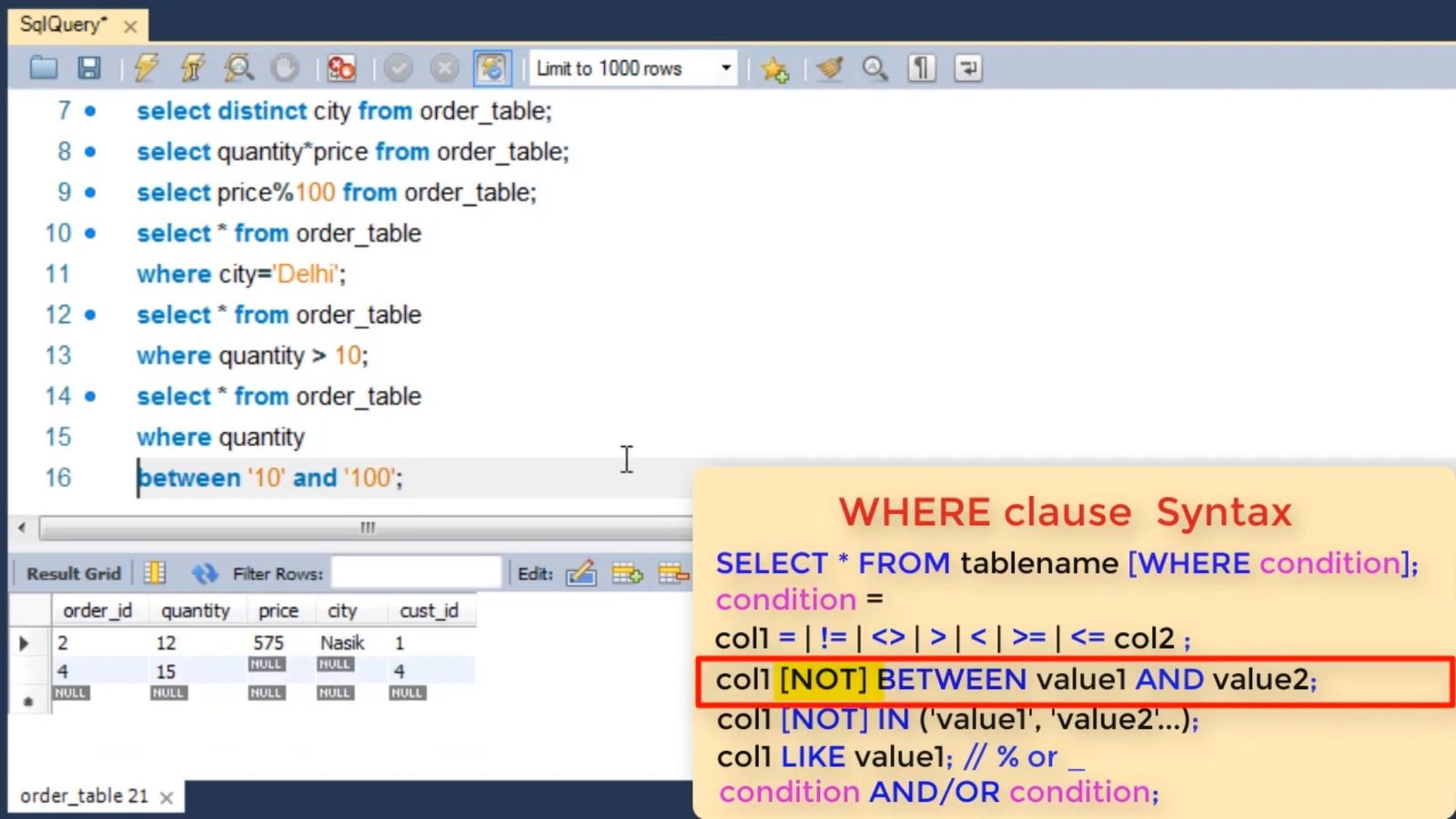
SQL Select Statement: Tutorial Simply Coding

Select Deals Tips and Product Reviews Select NBC News

Select Quality Life Services

SQL SELECT Statement: An Introduction Master Data Skills AI

Select for Communications Information Technology LinkedIn

Select meaning of Select YouTube

Pure JavaScript HTML Multiple Select Tag YouTube

Select Wholesale Application Select Cards

Select Select Technology Group
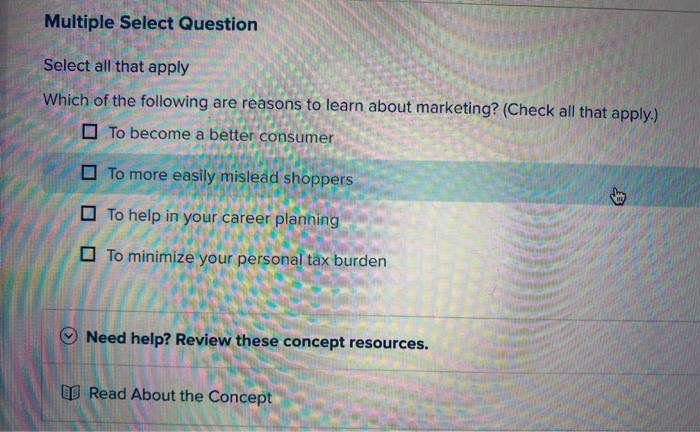
Solved Multiple Select Question Select all that apply Which Chegg com

Select Rebranding on Behance

SELECT

Select Author Christie Matheson Random House Children #39 s Books