Ssl Certificate Signed Using Weak Hashing Algorithm
Here are some of the images for Ssl Certificate Signed Using Weak Hashing Algorithm that we found in our website database.
SSL Certificate Signed Using Weak Hashing Algorithm turingsecure

SSL Certificate Signed Using Weak Hashing Algorithm Vulnerability

SSL Certificate Signed Using Weak Hashing Algorithm in windows server

Solved: 9800 L F WLC SSL Certificate Signed Using Weak Hashing

PCI fail: SSL Certificate Signed Using Weak Hashing Algorithm (Known CA)
HP iLo 4 Weak Hashing Algorithm Patch megaw co za
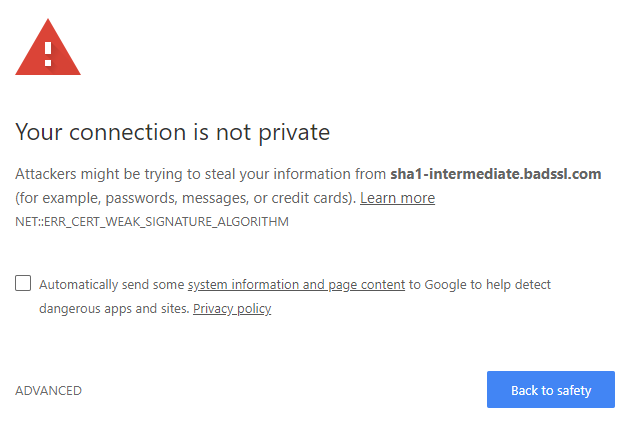
How To Fix NET:: ERR CERT WEAK SIGNATURE ALGORITHM
Weak Hashing Algorithm Archive Der Windows Papst IT Blog Walter
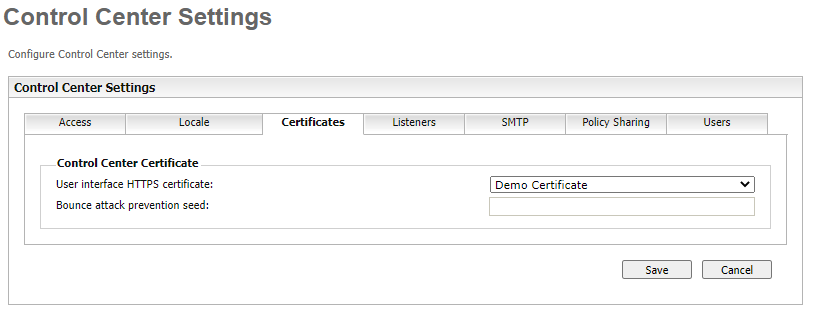
has been added to administration certificates the control center web
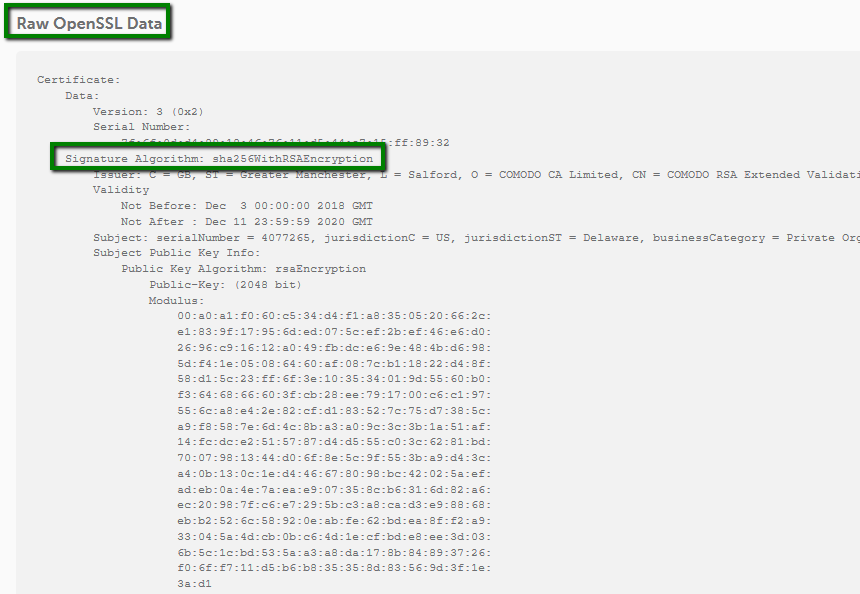
How do I check my hashing algorithm? SSL Certificates Namecheap com

HOWTO: Disable weak protocols cipher suites and hashing algorithms on
What Is Hashing In Cryptography? Crypto Legacy
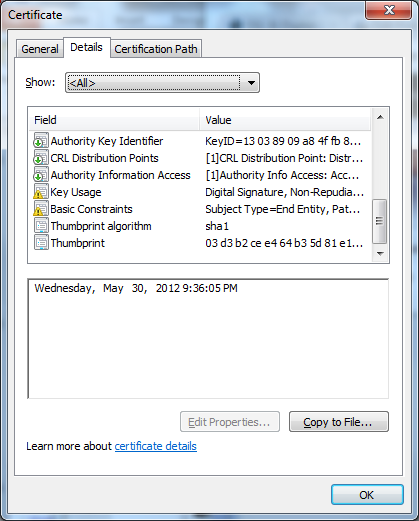
Microsoft Windows Update SSL certificate gets failing grade Ars Technica
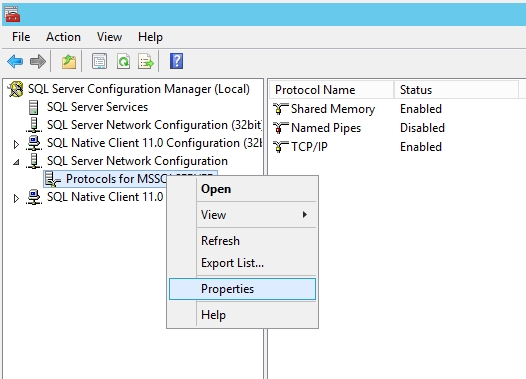
How Secure Are Your Client Connections? WickTech Blog
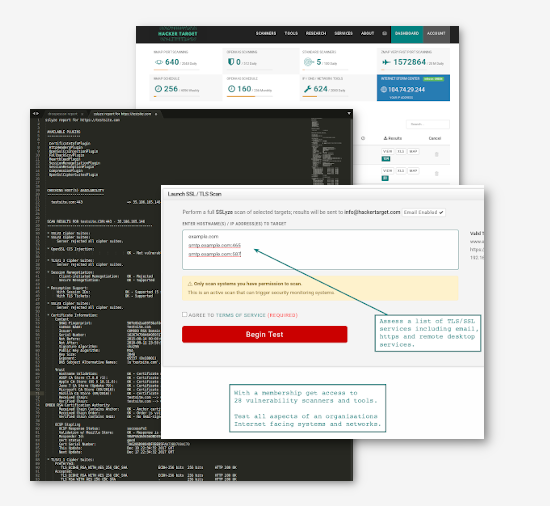
Online SSL Scan with SSLyze HackerTarget com
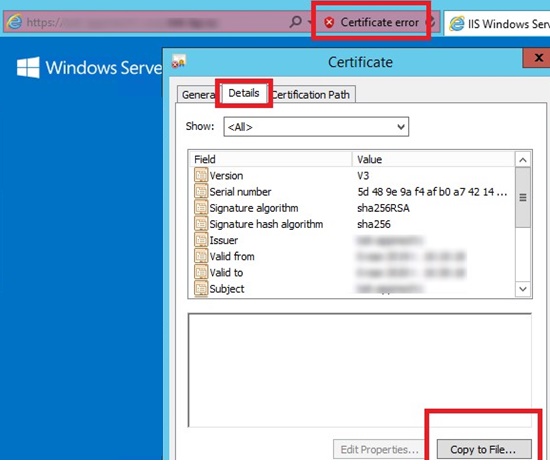
How to Deploy SSL Certificate on a Computers Using GPO? Windows OS Hub
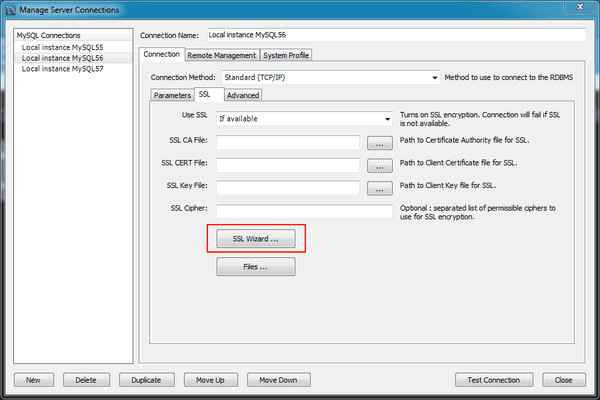
MySQL :: MySQL Workbench Manual :: 5 3 5 SSL Wizard (Certificates)
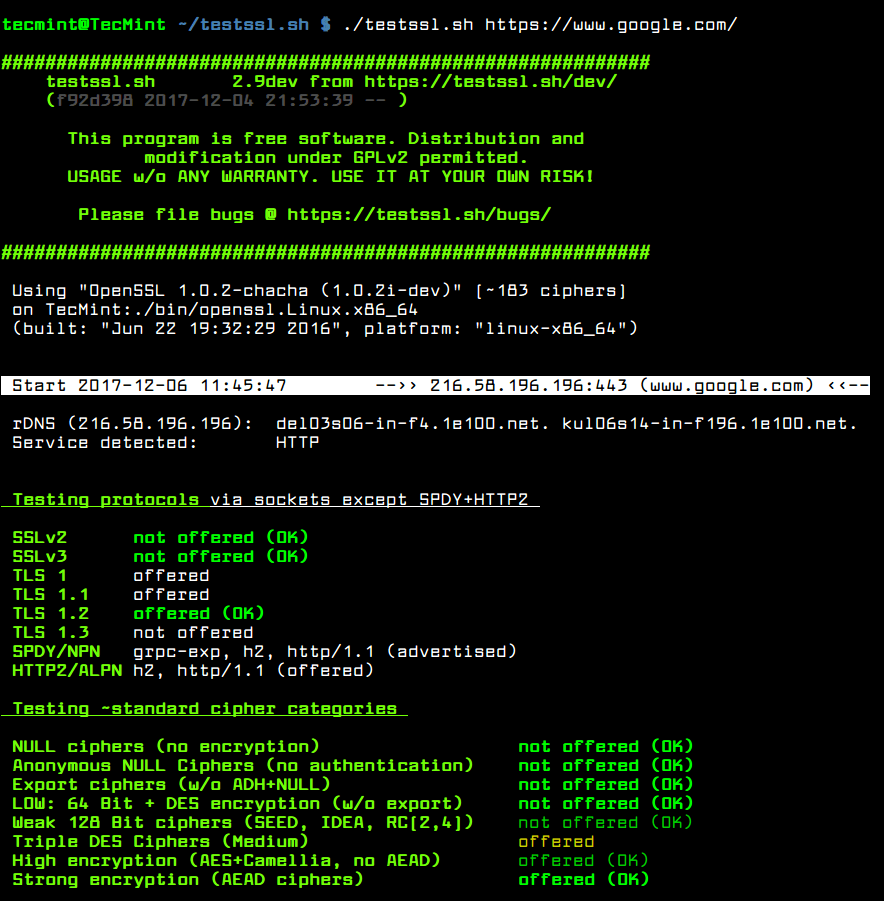
Testssl sh Testing TLS/SSL Encryption Anywhere on Any Port
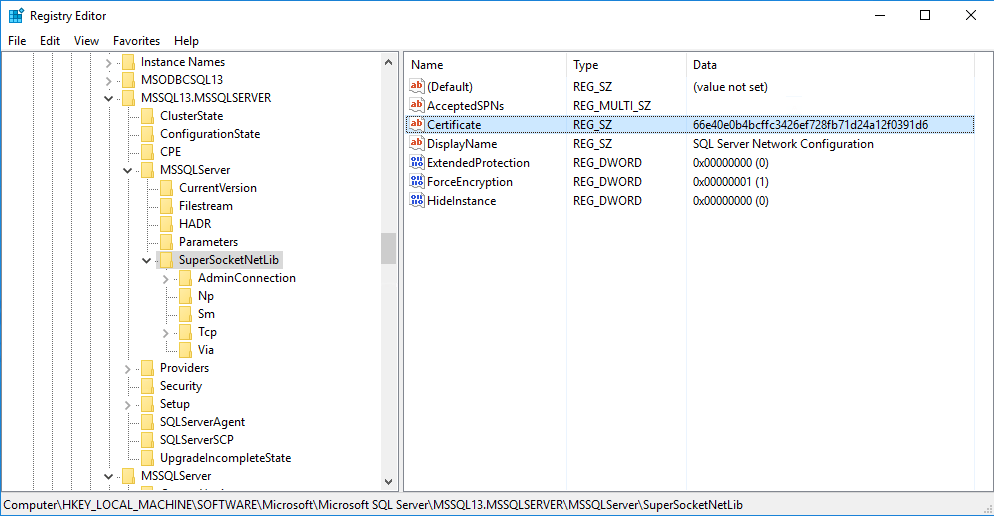
SSL Self Signed Fallback SQL Server Der Windows Papst IT Blog Walter
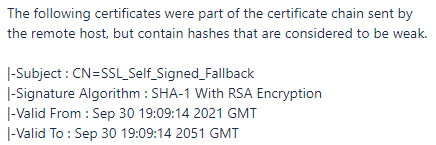
SSL Self Signed Fallback SQL Server Der Windows Papst IT Blog Walter
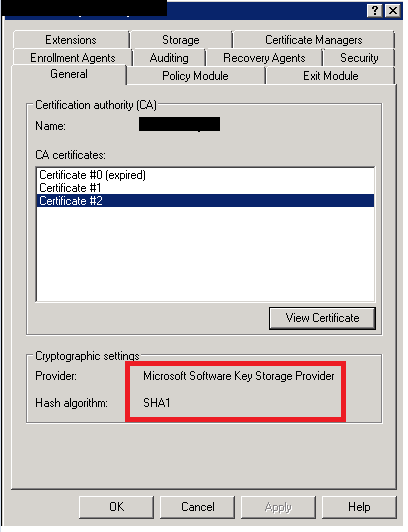
Gotham Technology Group

Migrating AD certificate services to SHA 2: Considerations and

ssl Chromium Browsers TLS1 2 Fails with ADCS issued certificate on

Certificate Services Migrate from SHA1 to SHA2 (SHA256) Appunti dalla

Certificate Services Migrate from SHA1 to SHA2 (SHA256) Appunti dalla

SSL Certificate Signed Using Weak Hashing Algorithm Tenable®
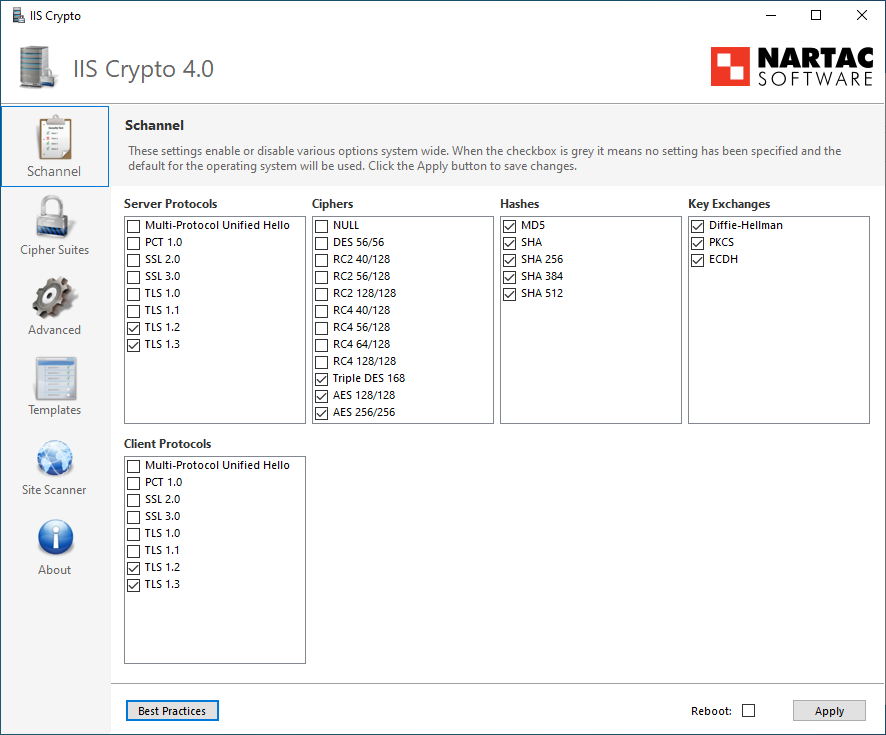
Nartac Software IIS Crypto
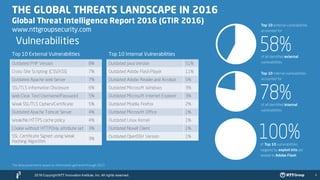
Global Cyber Threat Intelligence PDF Information and Network
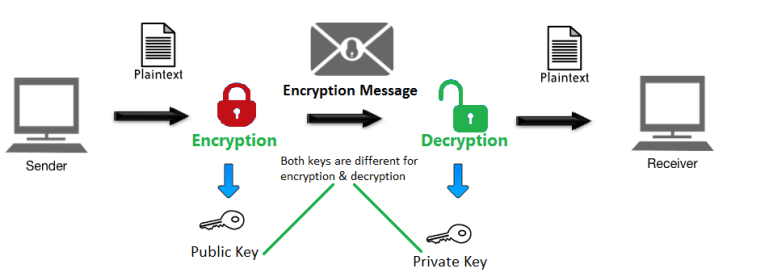
What is Public and Private Key in Cryptography? An Introduction
.jpeg)
Protecting Against Weak Cryptographic Algorithms Microsoft Learn
.jpeg)
Protecting Against Weak Cryptographic Algorithms Microsoft Learn

Microsoft discontinues MD5 crypto for digital certificates to improve

Sr2T Converts Scanning Reports To A Tabular Format
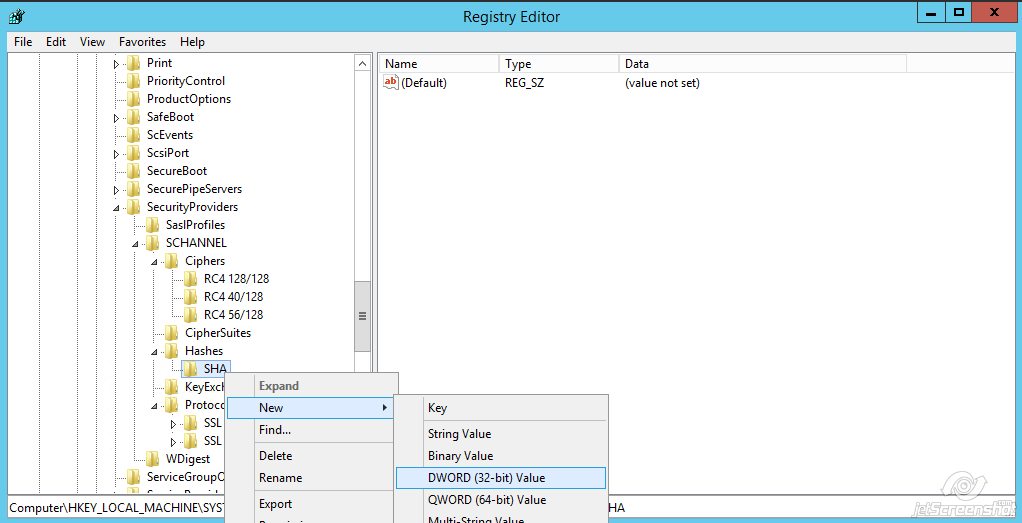
Disabling SHA 1 SSL Certificates Namecheap com

La Facultad de Facultad de Matemáticas UADY

Nartac
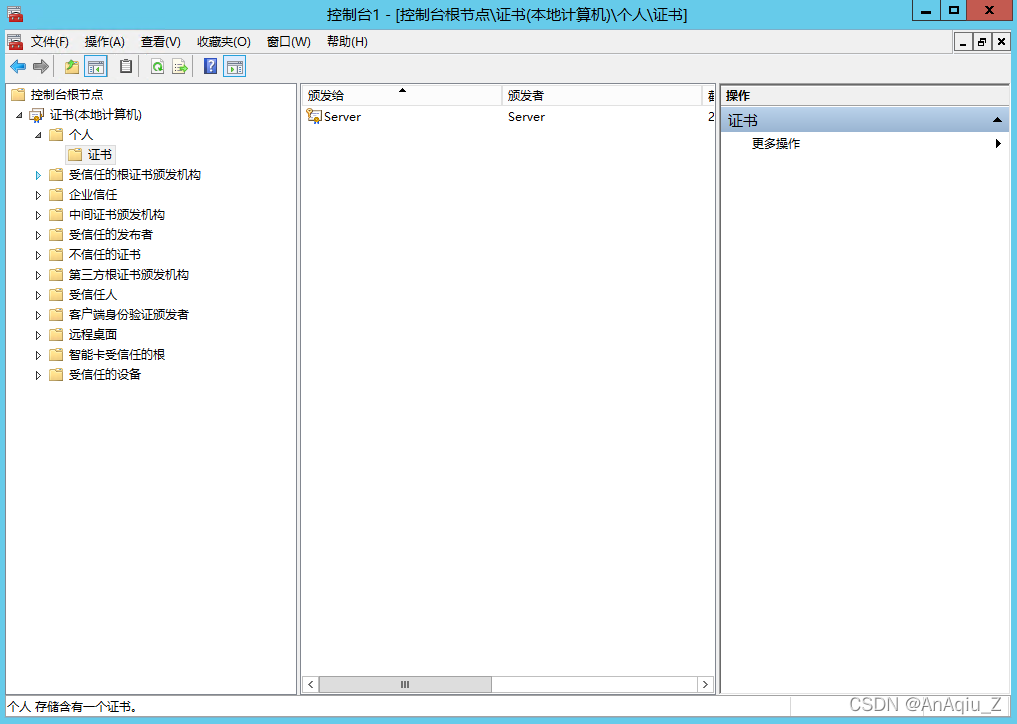
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) 源码巴士

SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) 源码巴士
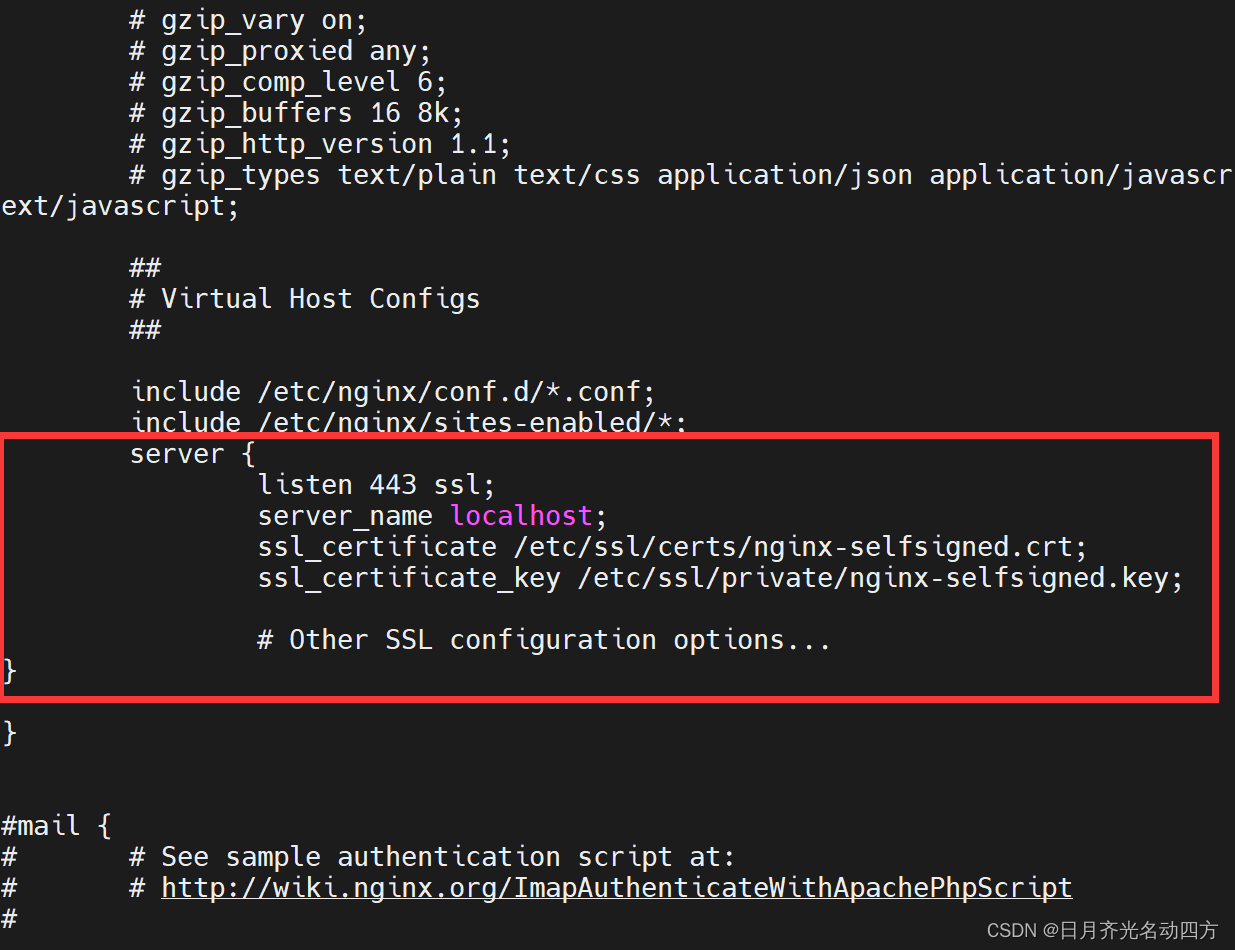
【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak
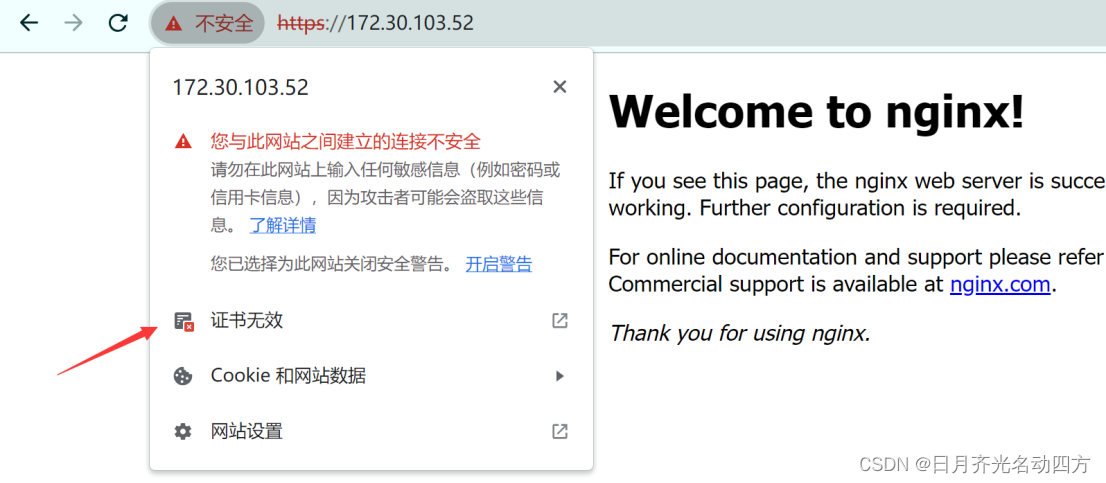
【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak
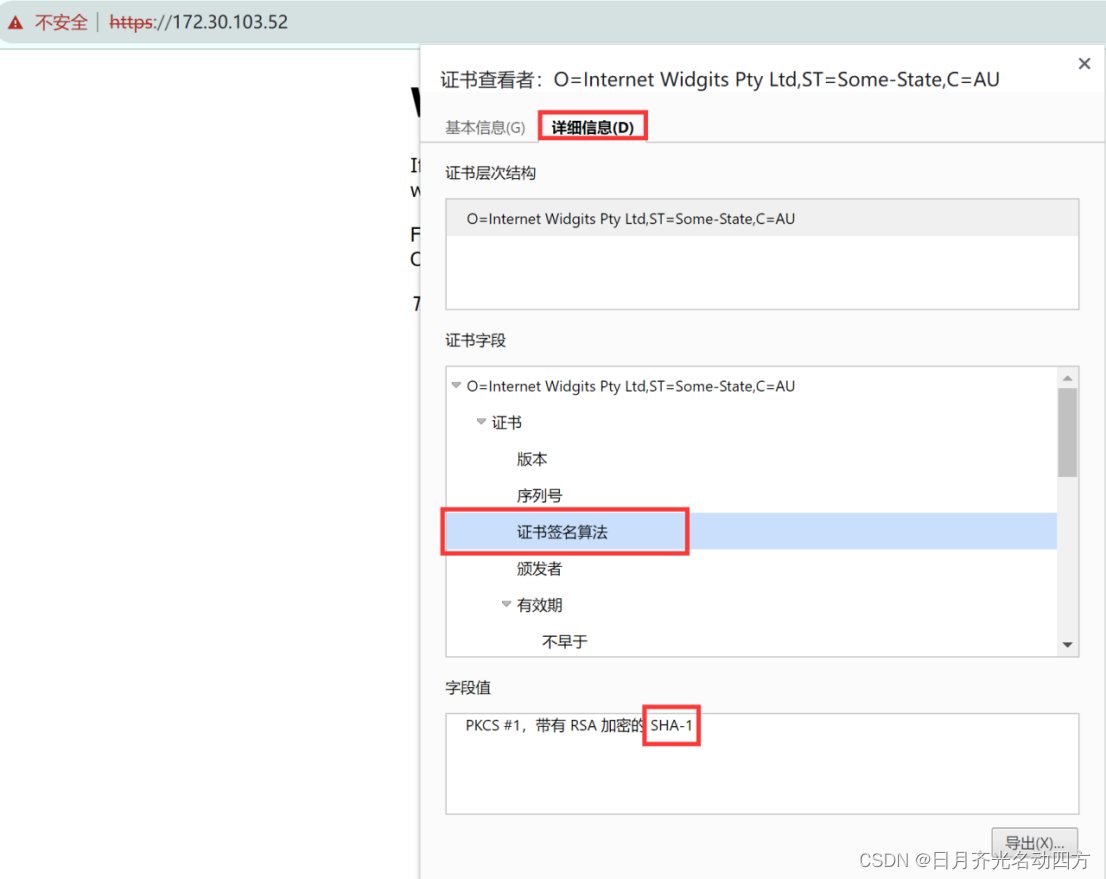
【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak
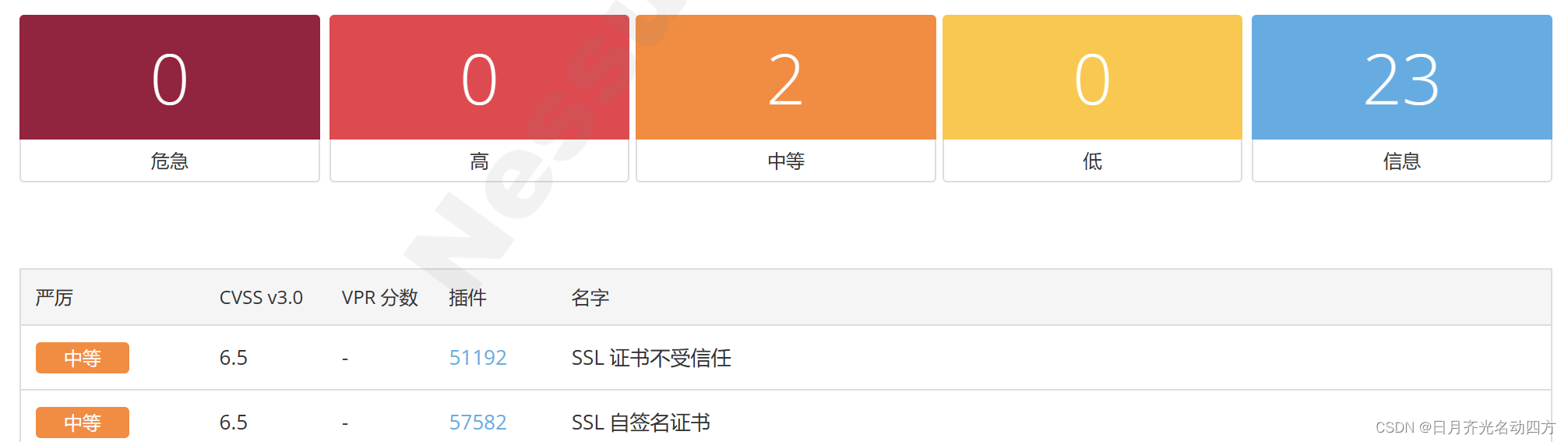
【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak
【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak
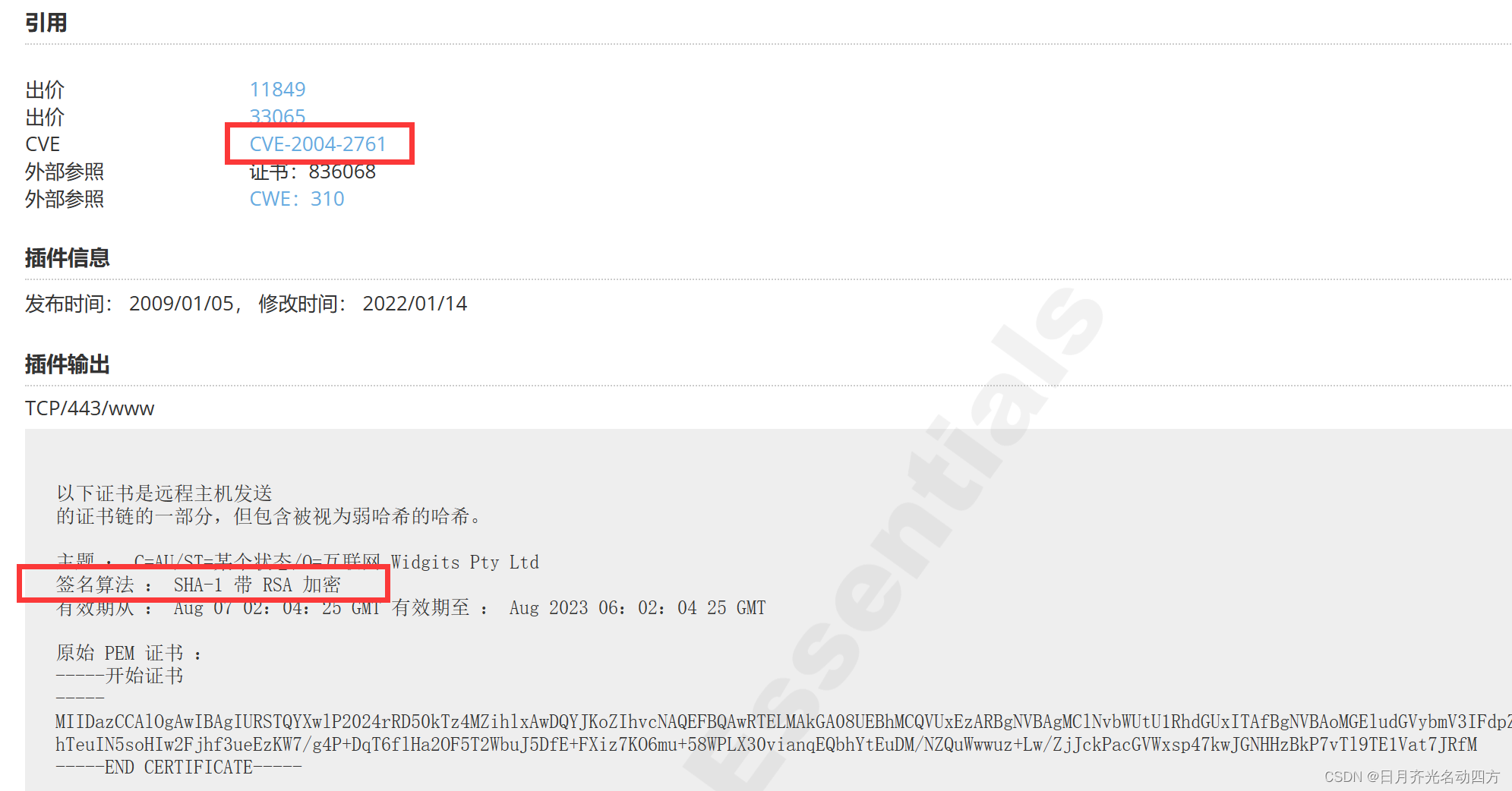
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
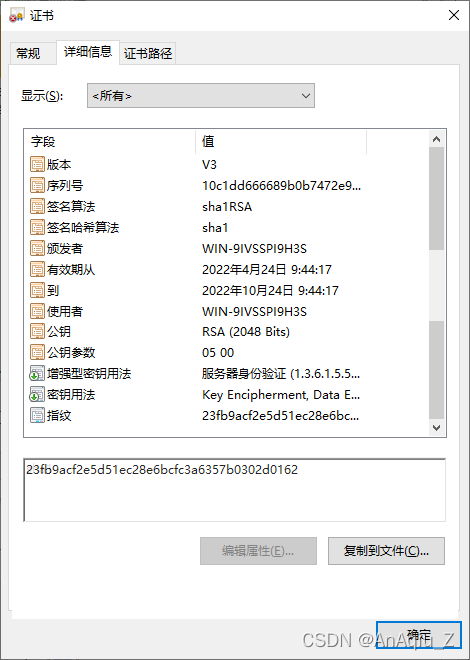
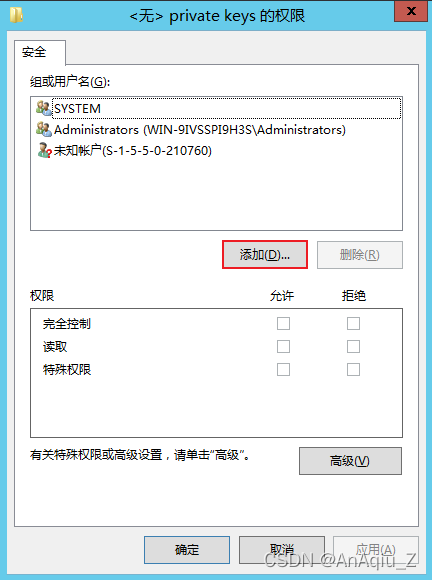
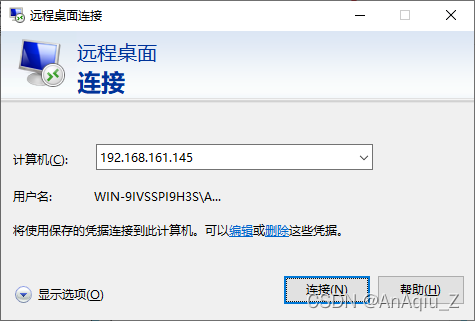
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
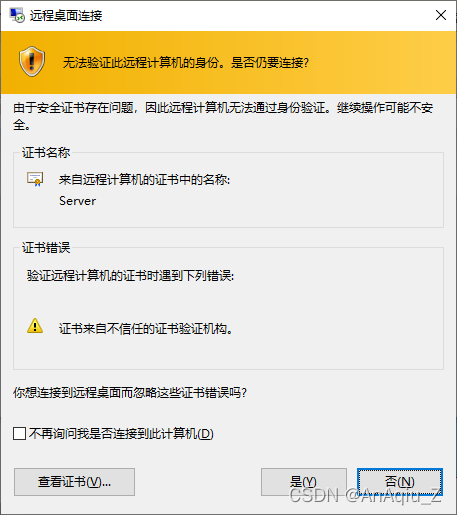
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
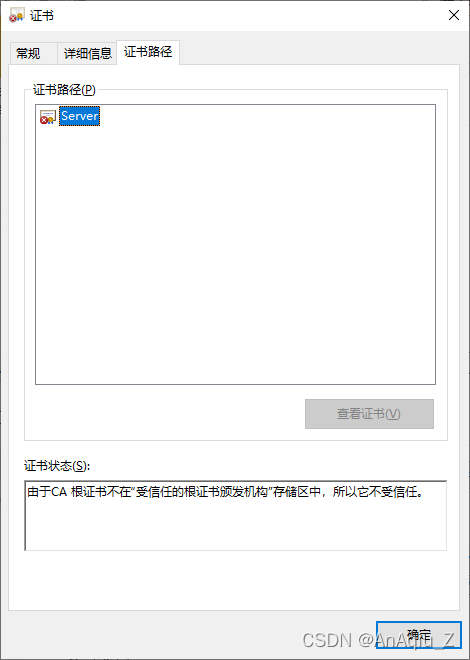
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
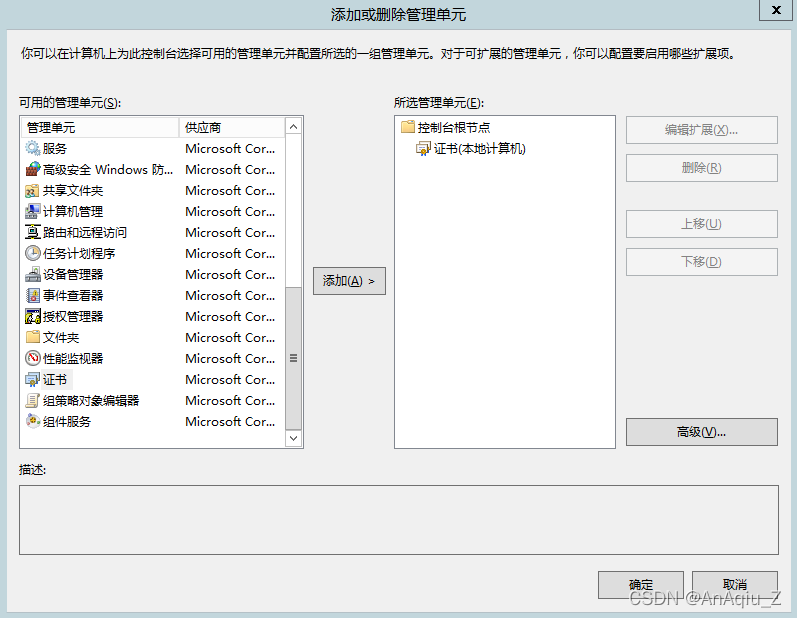
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
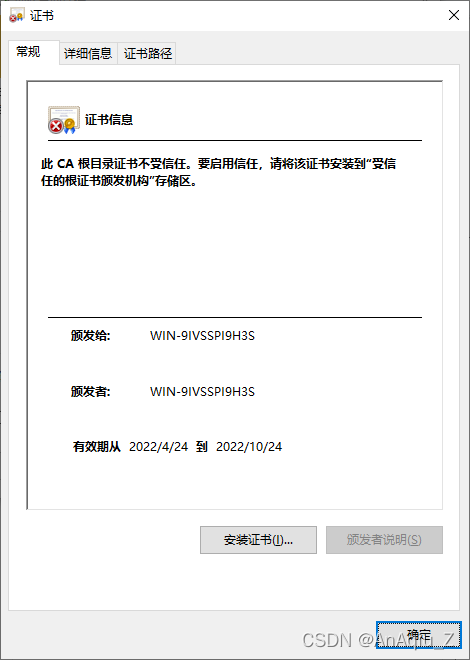
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
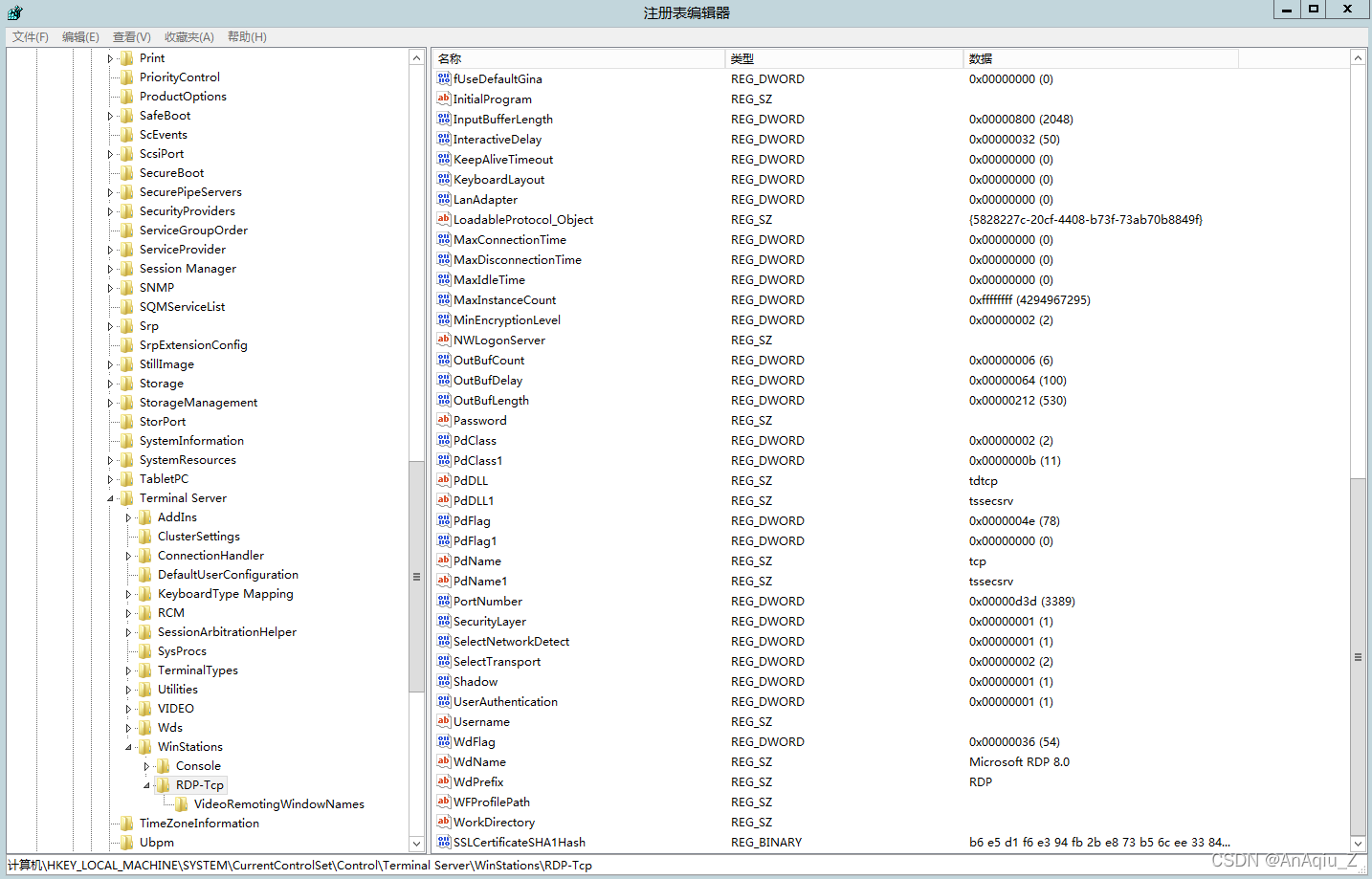
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客

【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak
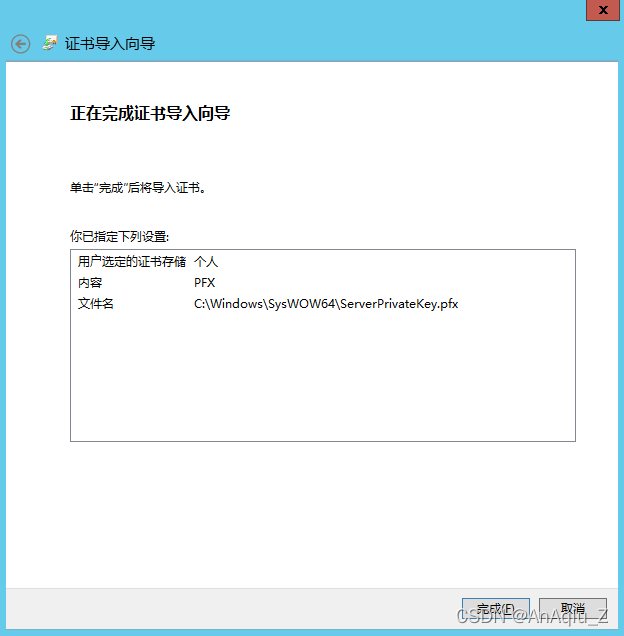
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
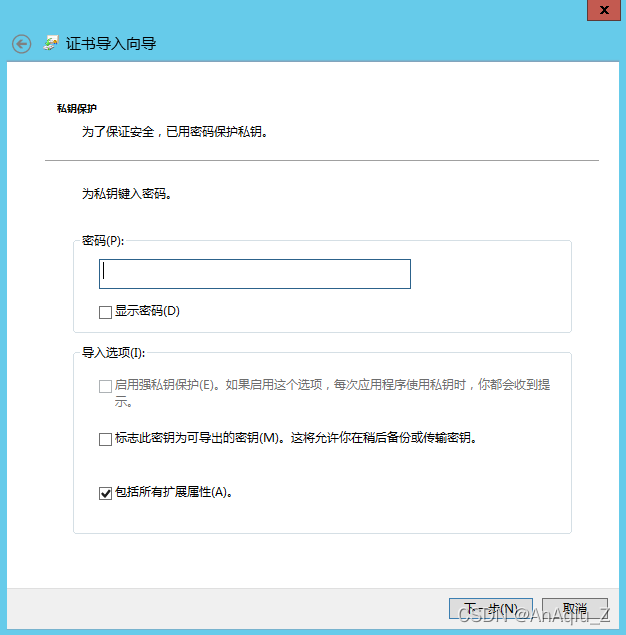
SSL Certificate Signed Using Weak Hashing Algorithm(CVE 2004 2761) CSDN博客
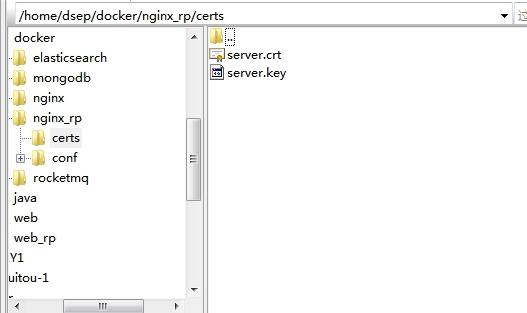
SSL Certificate Signed Using Weak Hashing Algorithm 使用弱哈希算法签名的 SSL 证书的

【漏洞复现】CVE 2004 2761:使用弱哈希算法签名的 SSL 证书(SSL Certificate Signed Using Weak

【精选】SSL Certificate Signed Using Weak Hashing Algorithm 使用弱哈希算法签名的 SSL
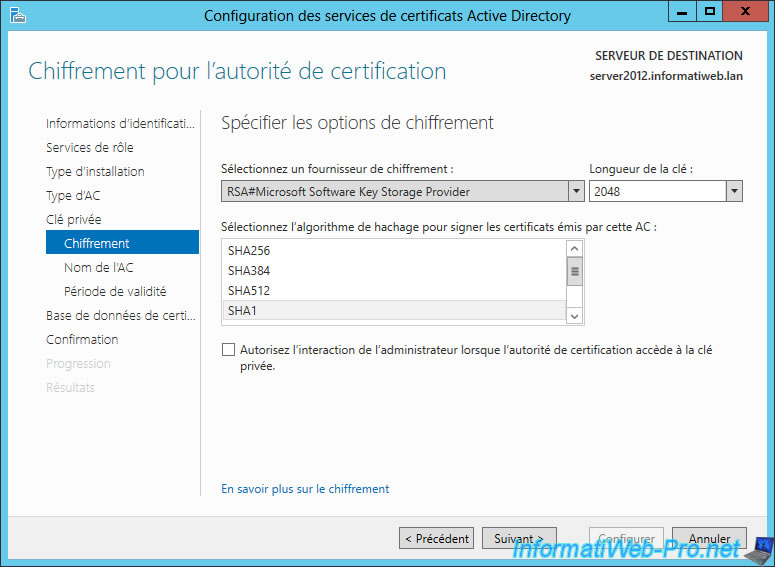
Créer une autorité de certification racine d #39 entreprise (Root CA PKI