Threat Assessment Certification
Here are some of the images for Threat Assessment Certification that we found in our website database.
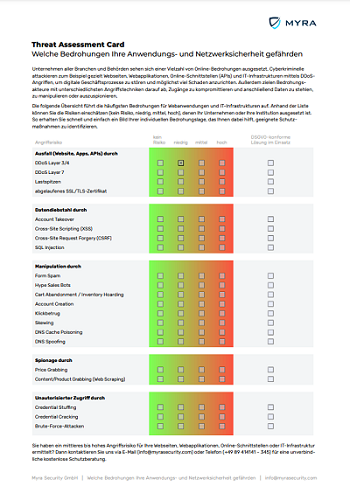
Threat Assessment Card Myra

THREAT ASSESSMENT GROUP Inc Newport Beach CA
Threat Assessment Certification prntbl concejomunicipaldechinu gov co
Threat Assessment Certification prntbl concejomunicipaldechinu gov co
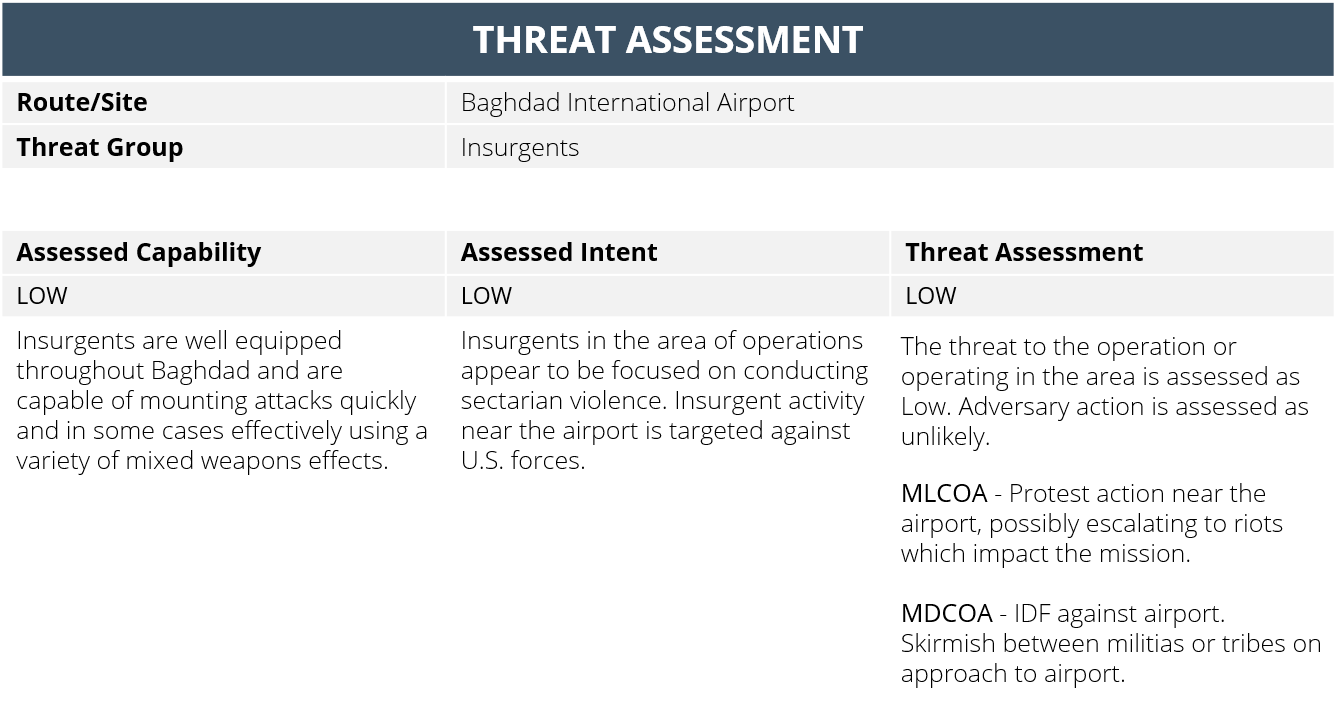
Threat Assessment Certification prntbl concejomunicipaldechinu gov co

Threat Assessment Certification prntbl concejomunicipaldechinu gov co
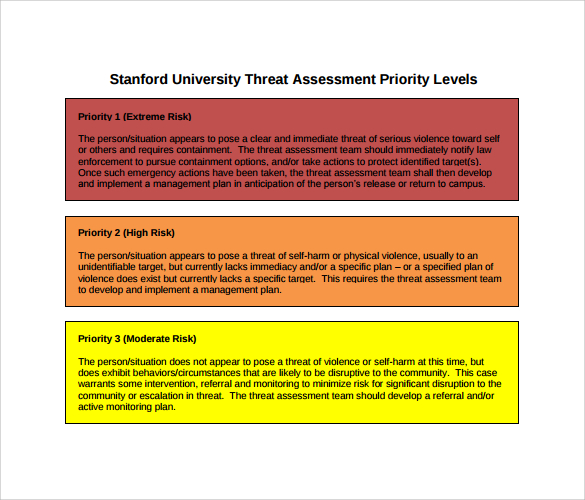
Threat Assessment Certification prntbl concejomunicipaldechinu gov co

Threat Assessment Certification prntbl concejomunicipaldechinu gov co

Threat Assessment Certification prntbl concejomunicipaldechinu gov co
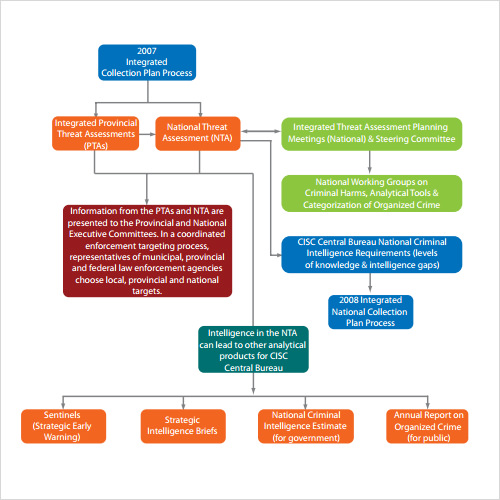
Threat Assessment Certification prntbl concejomunicipaldechinu gov co

Threat Assessment Certification prntbl concejomunicipaldechinu gov co

Threat Assessment Certification prntbl concejomunicipaldechinu gov co

Threat Assessment Certification prntbl concejomunicipaldechinu gov co

Worldwide Threat Assessment CyberTheory

Threat Risk Assessment Threat IQ

Threat Assessment Threat Assessment Plan DisasterRecovery org

Threat Risk Assessment Services ISA Cybersecurity Inc

Threat Intelligence Certification Quest Institute Of Knowledge

Threat Assessment DataNudge

Step One in Your Cybersecurity Journey: Threat Assessment Best

15 Threat Assessment Training Stock Photos Images Photography

Threat Assessment Training Navigate360

Threat Assessment Training Navigate360

Threat Assessment Webinar Recap

Threat Assessment Training: Identify and Defend Against Your Threat

Threat Assessment DataNudge

Myra Threat Assessment Card: Determine attack risk now

Behavioral Threat Assessment Resources Threat Assessment Consultants