Threat Hunting Certification
Here are some of the images for Threat Hunting Certification that we found in our website database.

Select the Factors You Should Consider to Understand the Threat in Your

Ten Cybersecurity Threats stock illustration Illustration of worms

What are the common types of cyber security attacks

Cybersecurity Threat Landscape in 2024: What You Need to Know

Cyber security threat detection and mitigation using IT discovery Virima

Combating seven common threat techniques in 2018 IT Security Guru
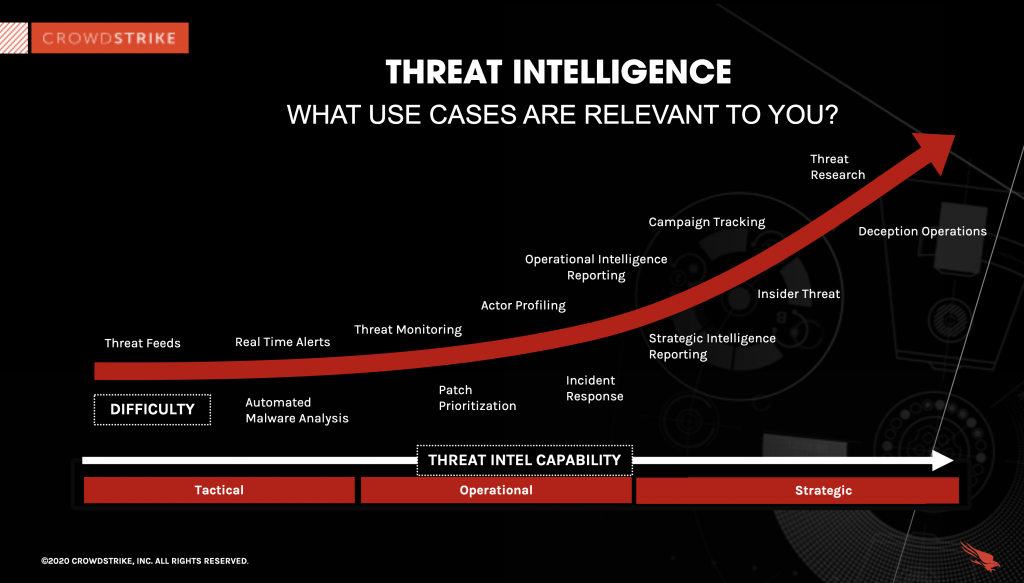
What is Cyber Threat Intelligence? Beginner #39 s Guide

Tactical Intelligence vs Strategic Intelligence Explained

SWOT Analysis Threat Examples and Definition
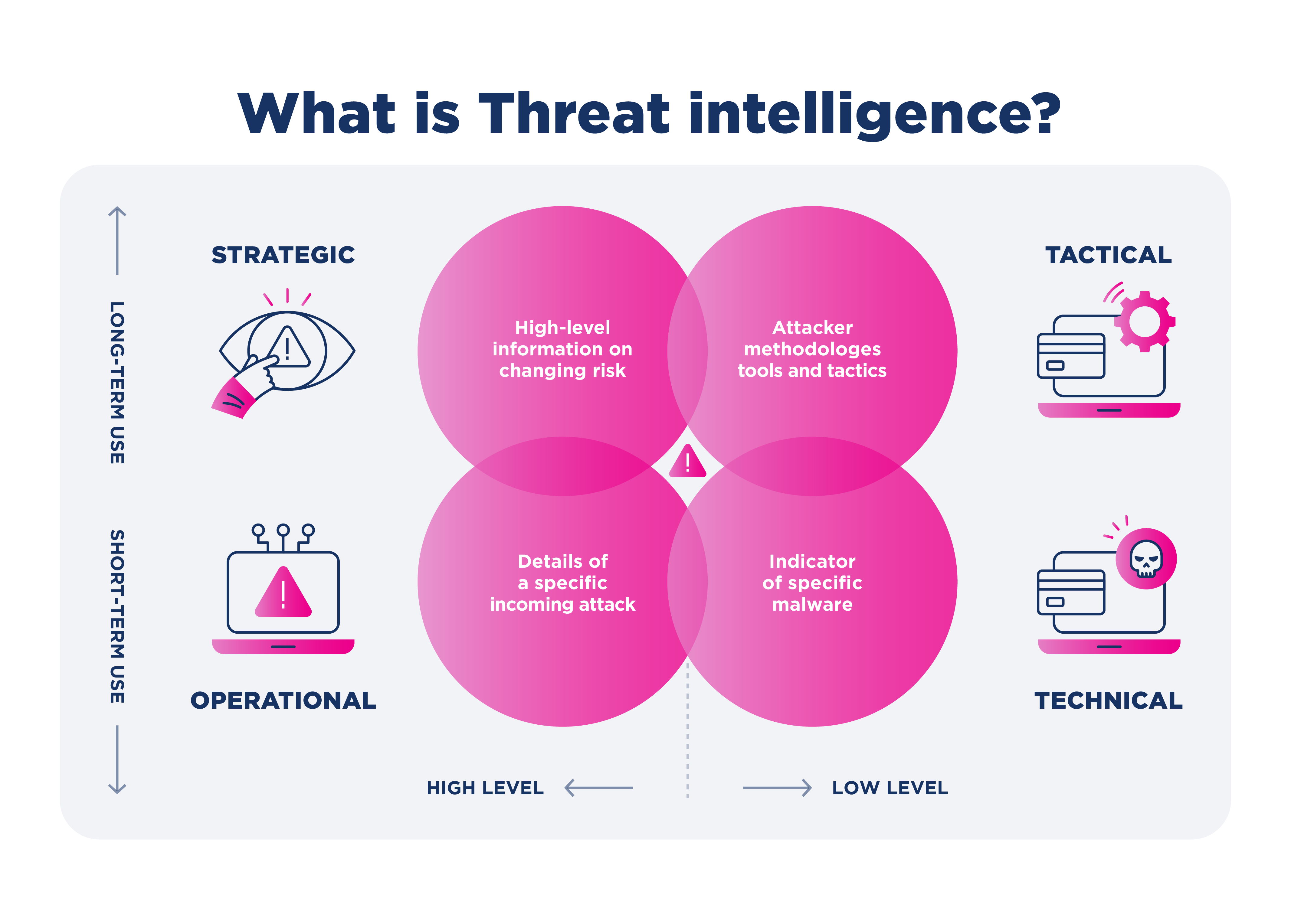
6 Steps to Building a Cyber Threat Intelligence Framework

Network Security Malicious Threats and Common Computer Definitions
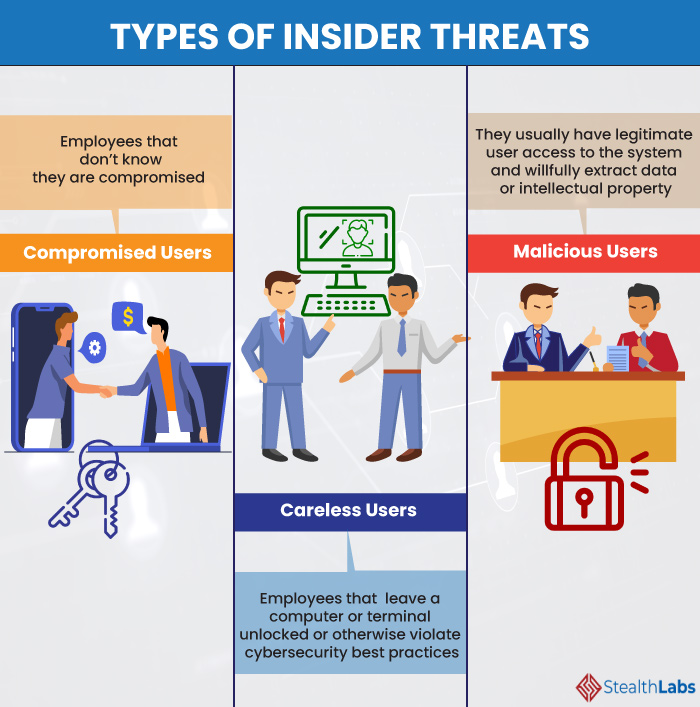
Threats

Top Critical Infrastructure Cyber Threats Critical Infrastructure Cyber

Nationstate Threat Actors Often Discover Vulnerabilities And Hold On
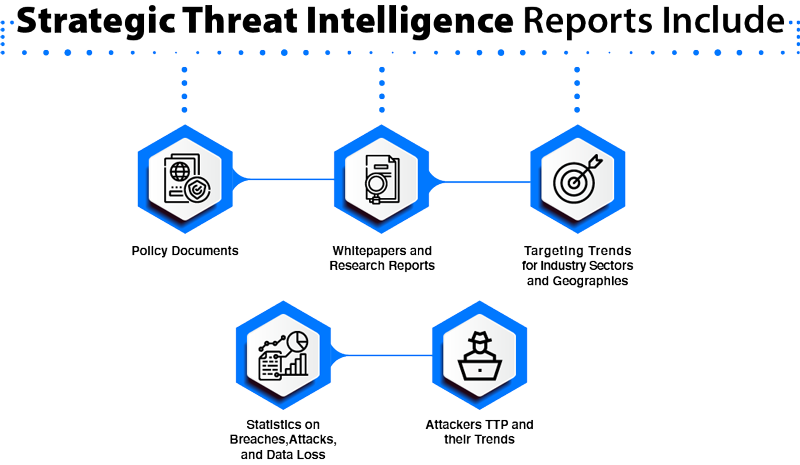
What is Cyber Threat Intelligence Cyber Threat Intelligence Analyst

What Are Cyber Threats And How Can You Stay Protected? The
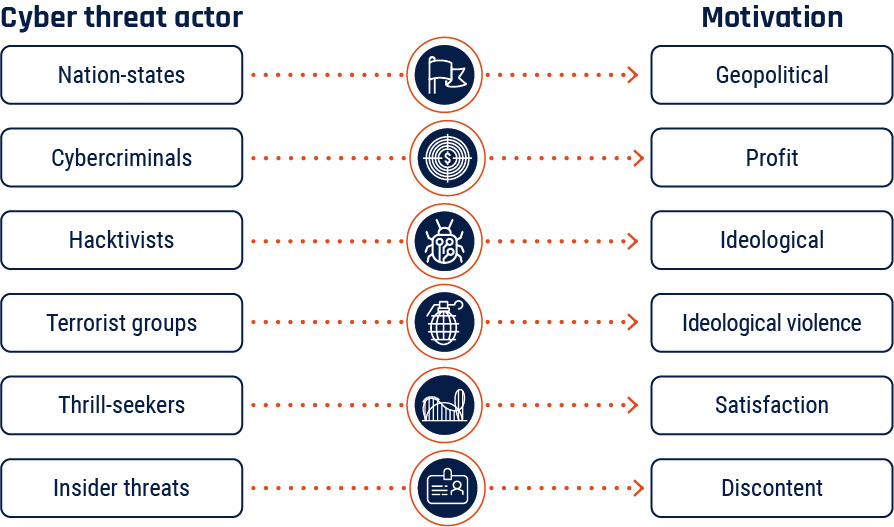
Cyber Threats

Threats

Internal Security Threats Definition at Lachlan Ricardo blog

Terroristic Threats Lawyer in Dallas Gallian Firm
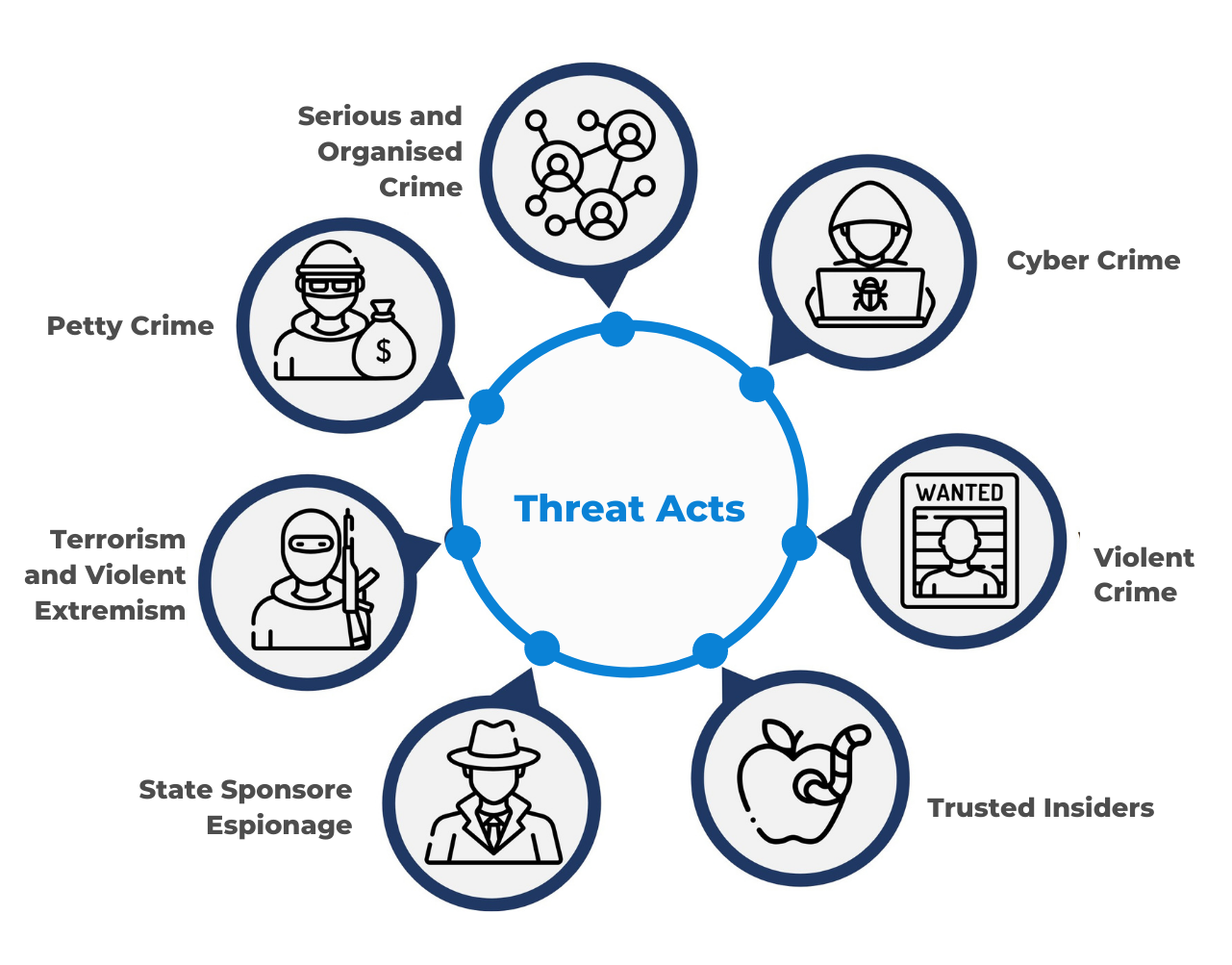
Protective Security Threat Types Core Integrity

Threats

GCSE Computer Science 9 1 OCR J276 Network protocol

How To Identify Cyber Security Threats At An Early Stage

5 Biggest cyber threats businesses are facing this year

Smarter Schools: Leveraging AI for Real Time Threat Detection and Response

12 Techniques to Stop Insider Threats GoGeekz Inc

Premium Vector Threat levels gauge vector illustration

Threat Hunting 101: A Beginner s Guide for Cybersecurity Student by

Understanding The Cyber Threat Landscape IT Security Guru

PPT Facilitated Risk Analysis Process (FRAP) Adapted from Tom Peltier

Insider Threats: Risks Identification and Prevention

Free of Charge Creative Commons threat Image Finger 1

Clipart Panda Free Clipart Images

Threat Threat Image Photo (Free Trial) Bigstock