Vulnerability And Patch Management Policy Template
Here are some of the images for Vulnerability And Patch Management Policy Template that we found in our website database.

Patch Management Policy Template advansappz

Vulnerability and Patch Management Policy Omyalabs

Patch Management Policy IT Procedure Template
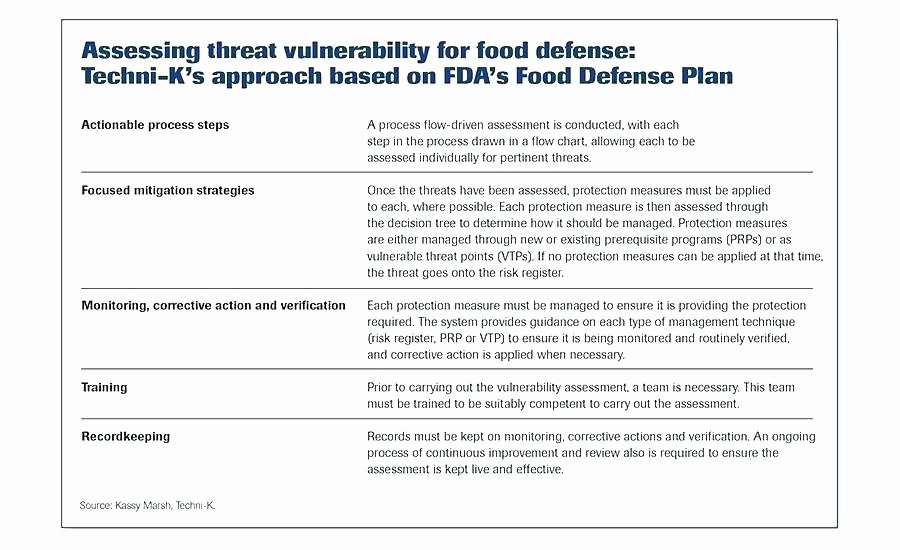
Vulnerability And Patch Management Policy Template

Sample Cip010 R3 Vulnerability Assessment And Patch Management
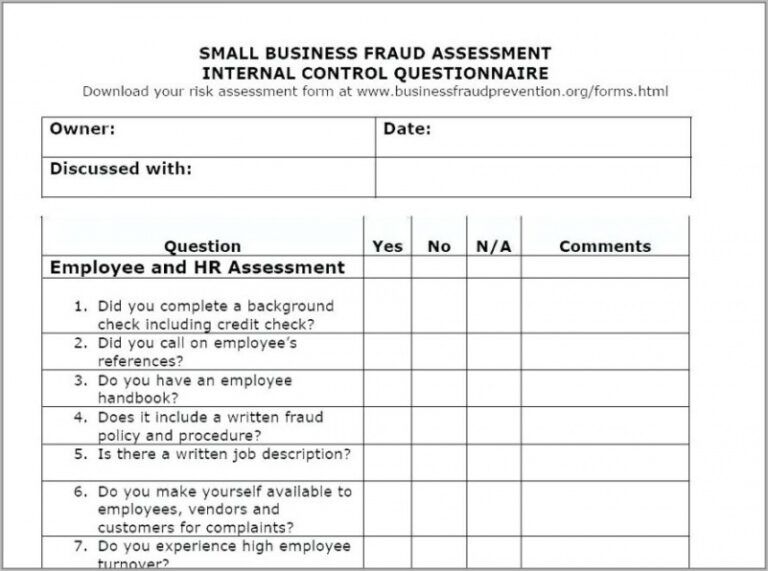
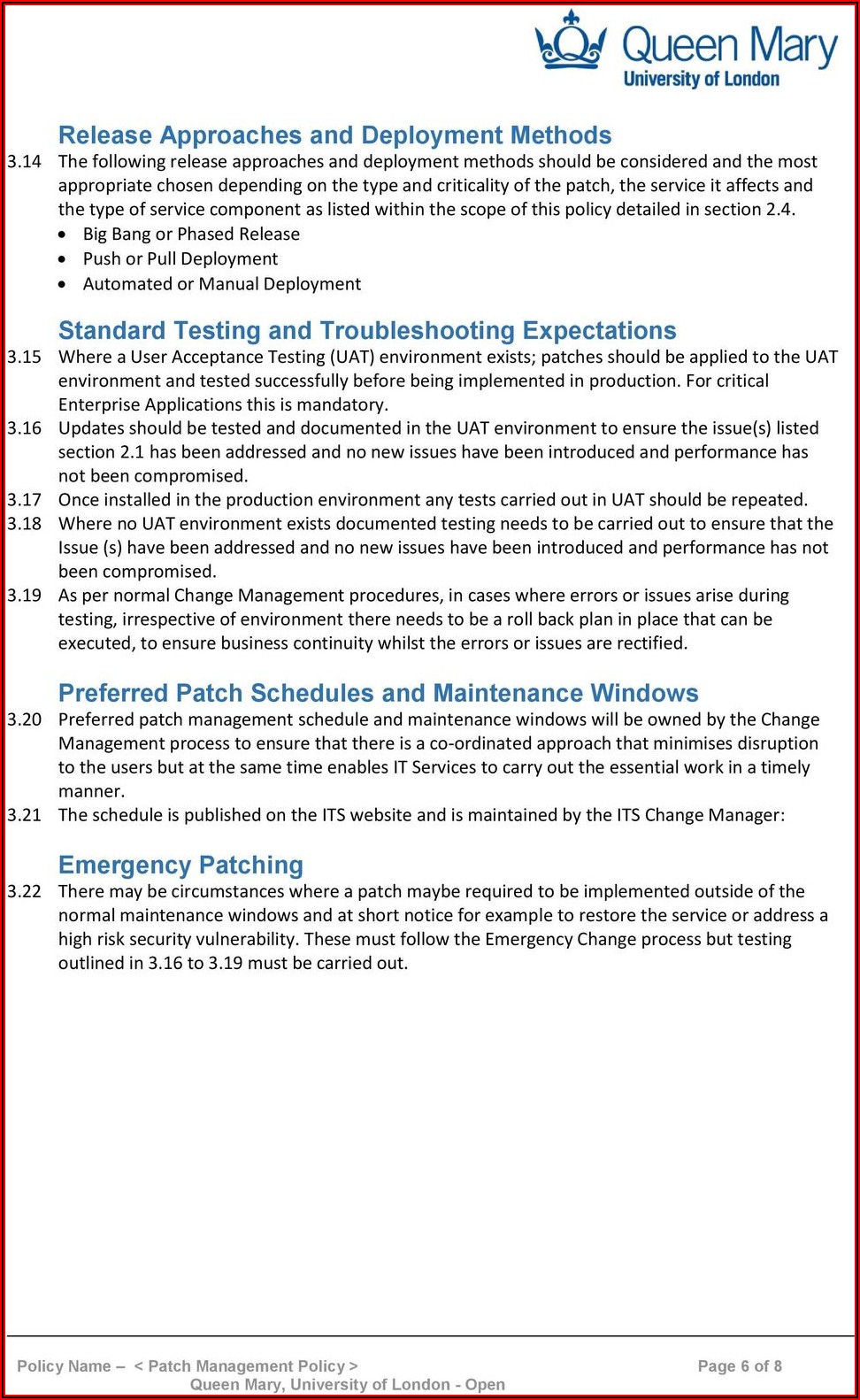
Vulnerability And Patch Management Policy Template

Vulnerability Management Policy Template Nist

Vulnerability Management Policy Template
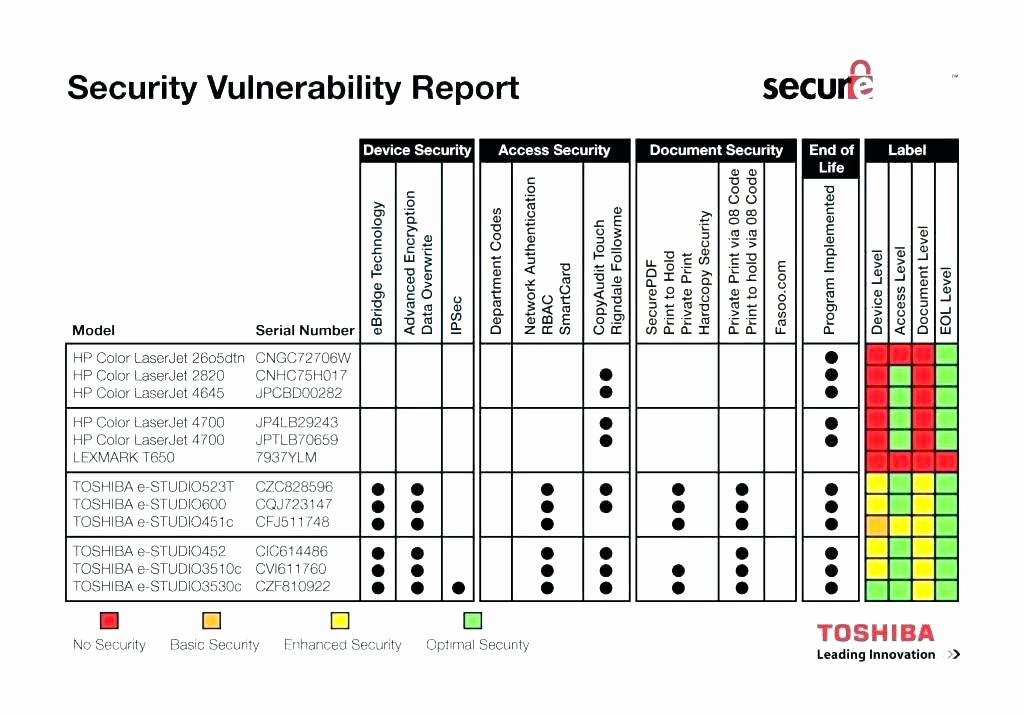
Patch And Vulnerability Management Plan Template
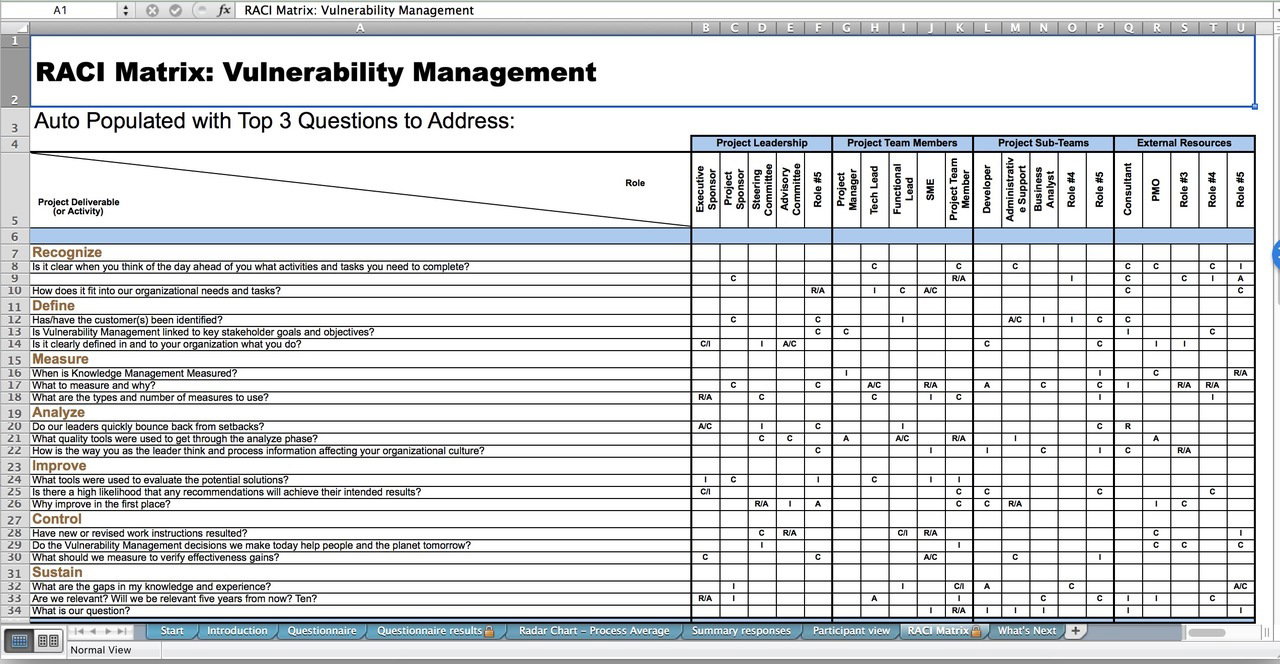
Patch And Vulnerability Management Plan Template

Free Patch Management Policy Template ( Examples)

Vulnerability Management Template

Patch Management Plan Template

Patch Management Policy Template

Vulnerability Management Policy Template for CIS Control 7

Patch Management Policy Template

Patch Management Policy Template (Free) eSecurity Planet

Vulnerability Management Process Template

Nist Patch Management Policy Template
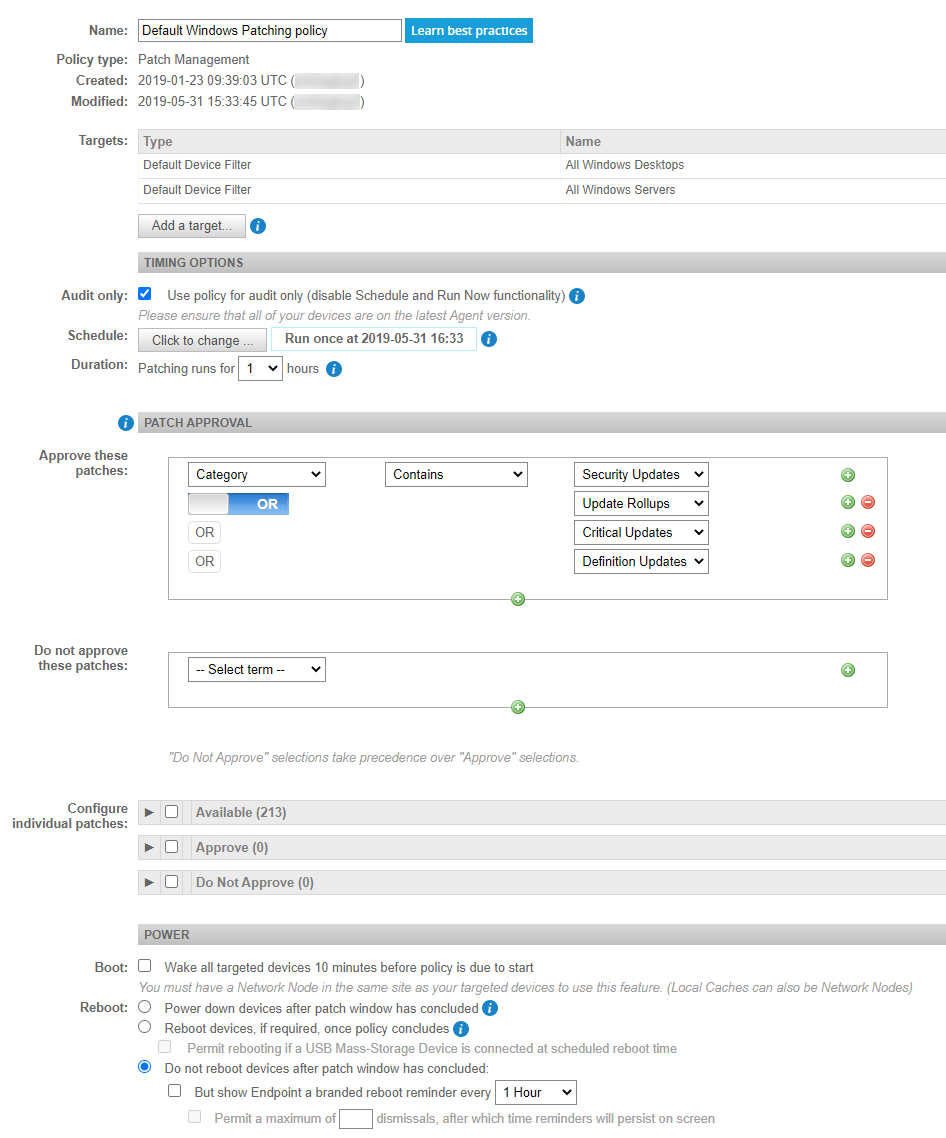
Patch Management Policy Template Nist
Patch Management Policy Template Nist

Sample Patch Management Policy Template Doc Template pdfFiller

ISO 27001 Patch Management Policy Template

ISO 27001 Patch Management Policy Template

ISO 27001 Patch Management Policy Template

The Ultimate ISO 27001 Patch Management Policy Template
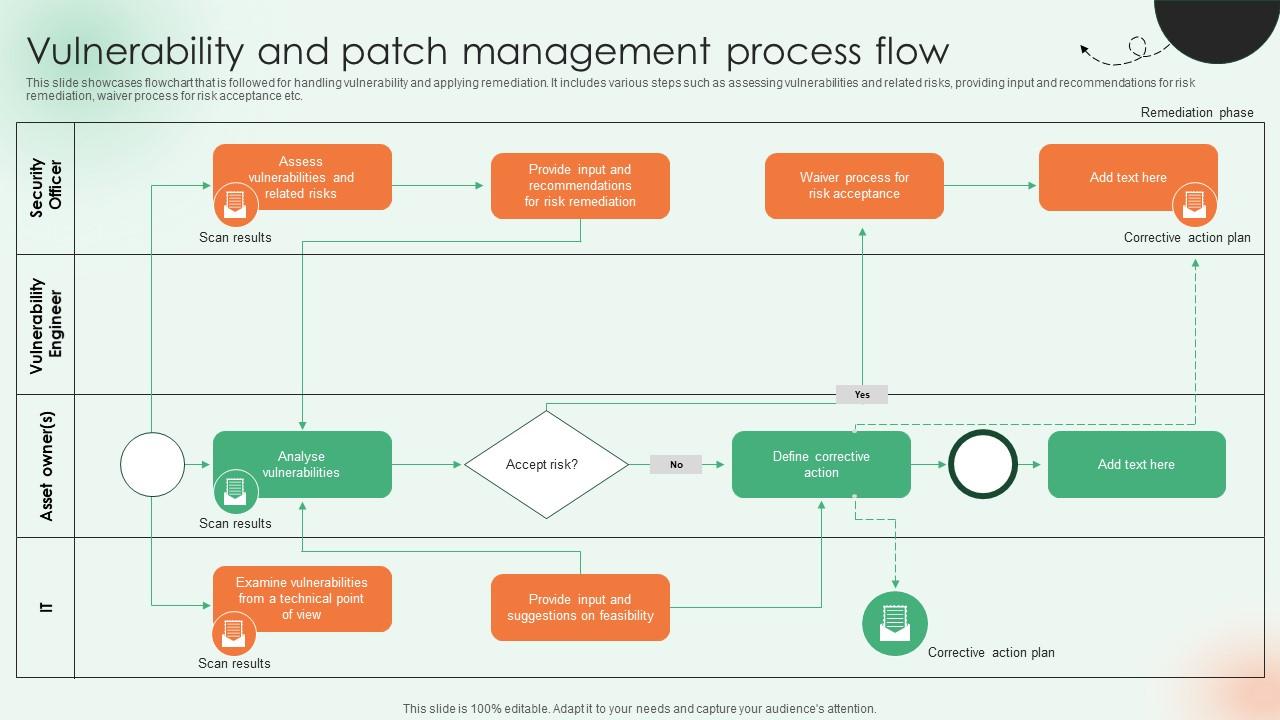
Vulnerability And Patch Management Process Flow PPT Slide

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA
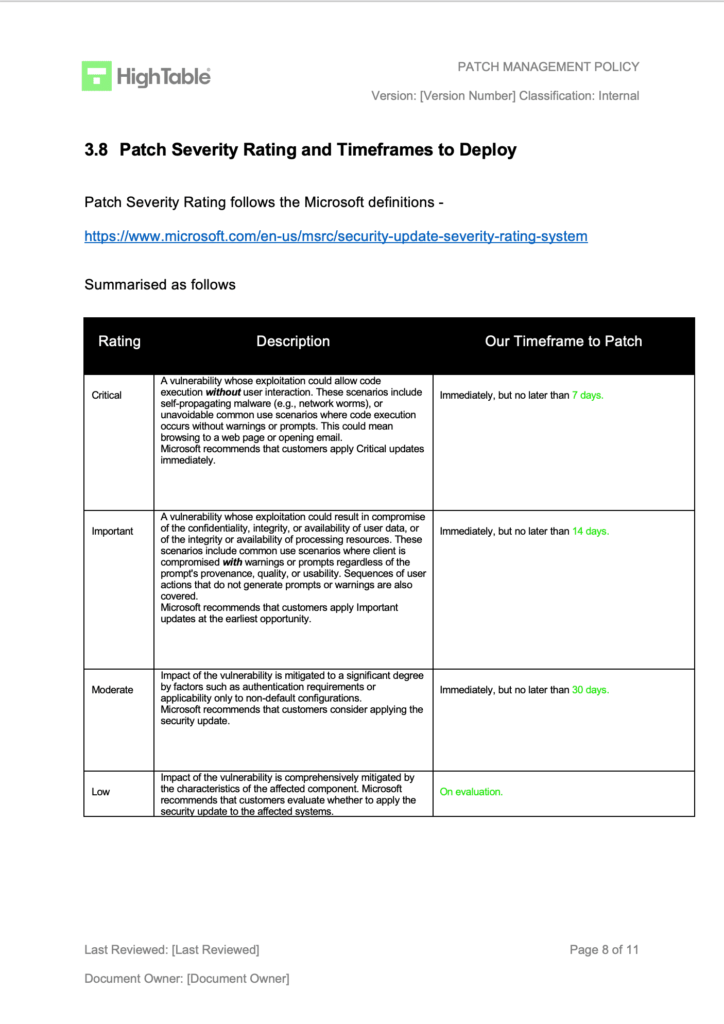
Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA

Patch Management Policy Template: ISO27001:2022/ NIS2 / DORA
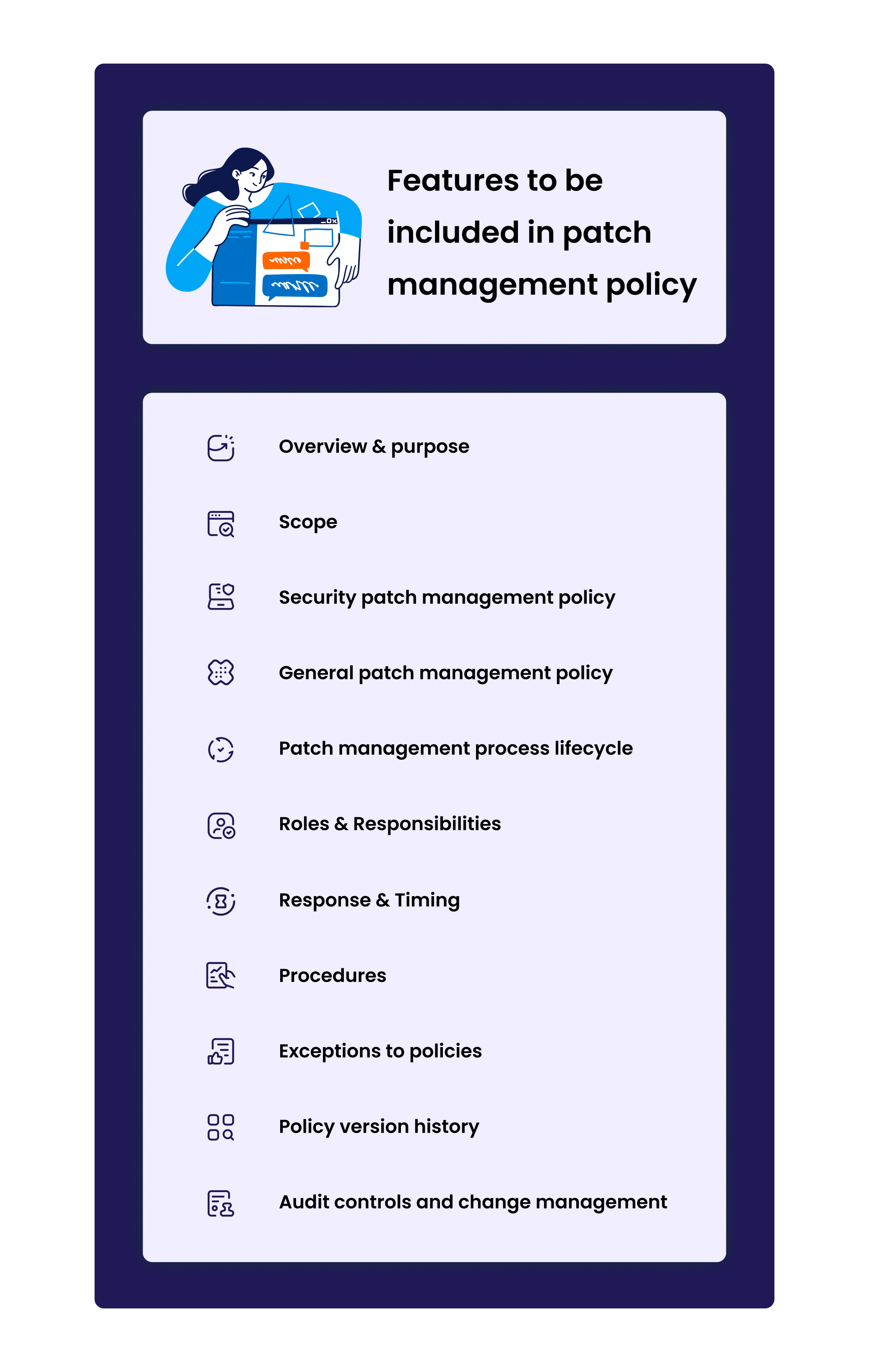
The what where and how of a patch management policy SuperOps ai

ISO 27001:2022 Patch Management Policy Template Word

ISO 27001:2022 Patch Management Policy Template Word

ISO 27001:2022 Patch Management Policy Template Word

Free Vulnerability Management Policy Template ( Examples)
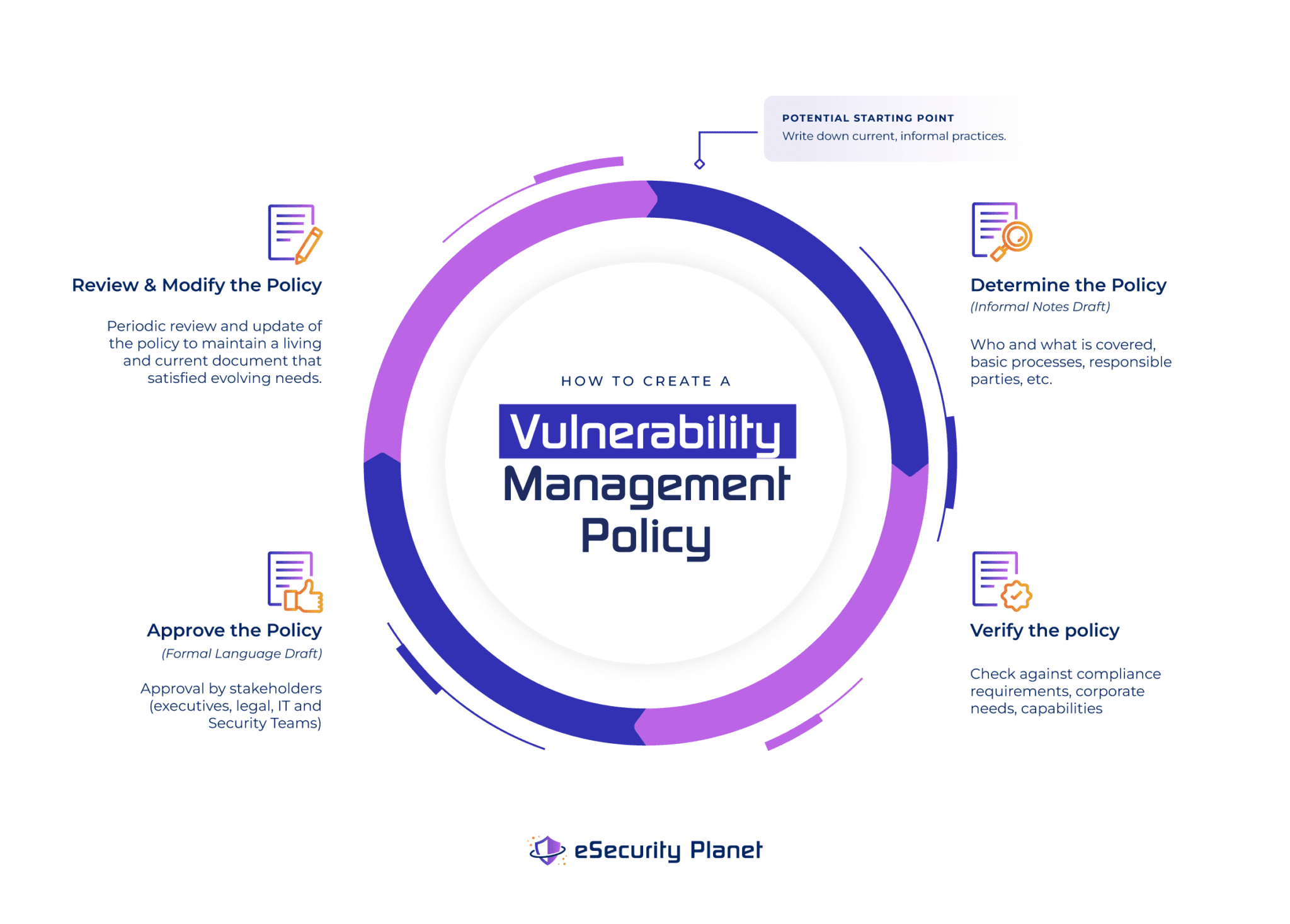
Free Vulnerability Management Policy Template ( Examples)

Patch Management Schedule Template
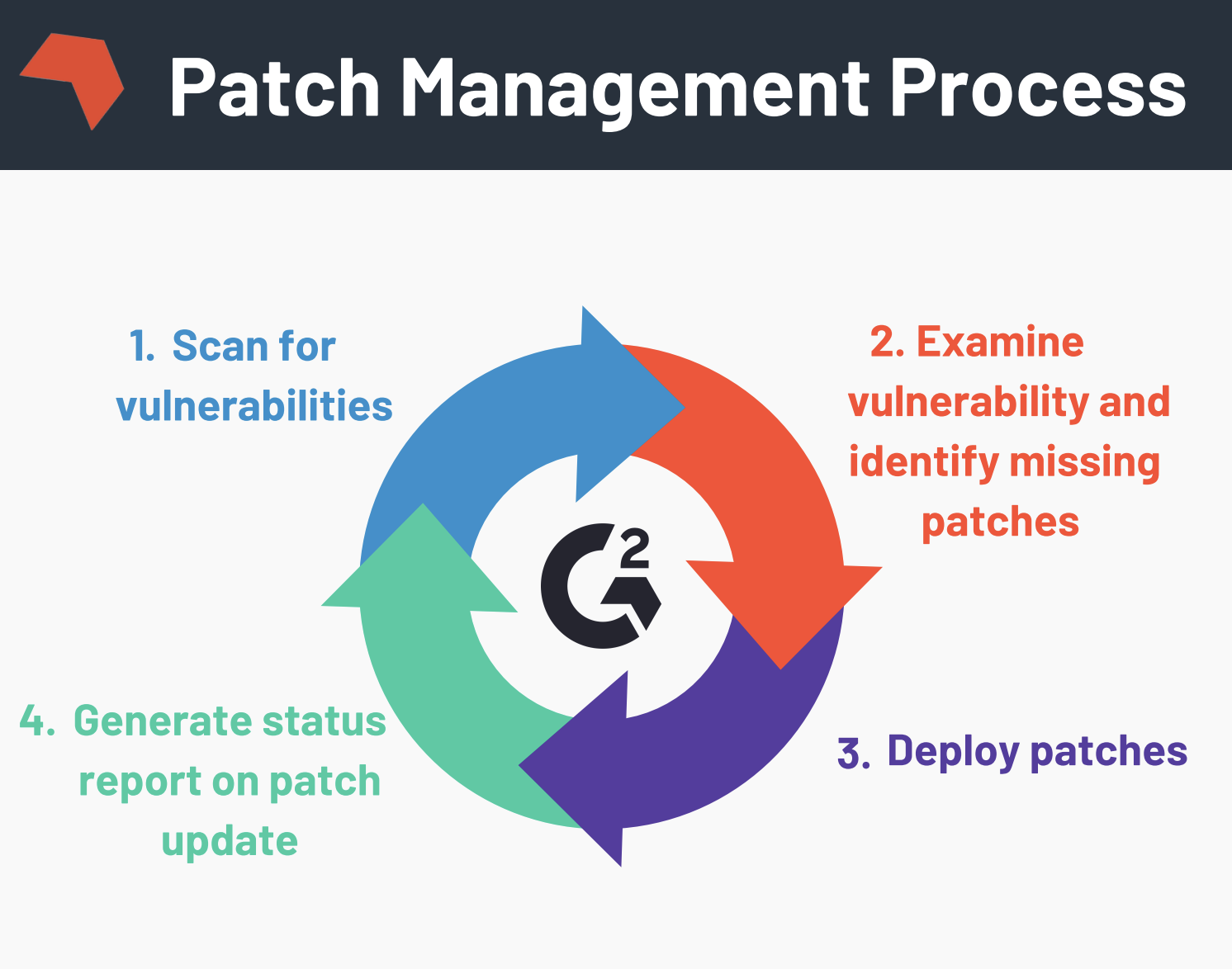
Patch Management Process Template

Patch Management Template Free Downloadable 2026

Vulnerability Remediation Plan Template Printable Word Searches
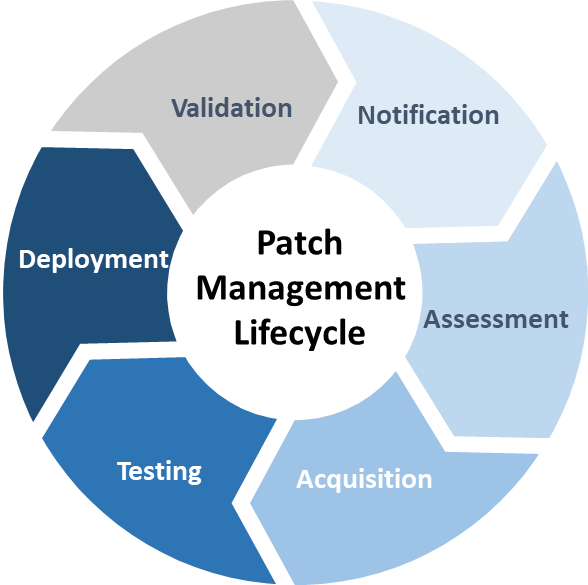
Patch Management Plan Template prntbl concejomunicipaldechinu gov co

Patch Management Plan Template prntbl concejomunicipaldechinu gov co

How to Create a Patch Management Policy Content Pack

Patch Management Policy and Procedure Liaison International
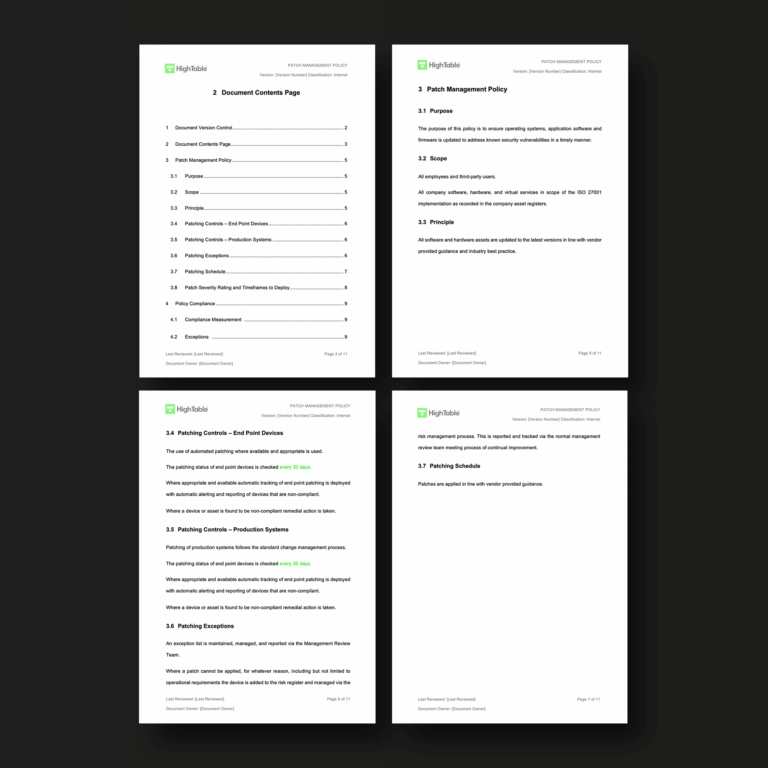
ISO 27001 Patch Management Policy Beginner s Guide Template
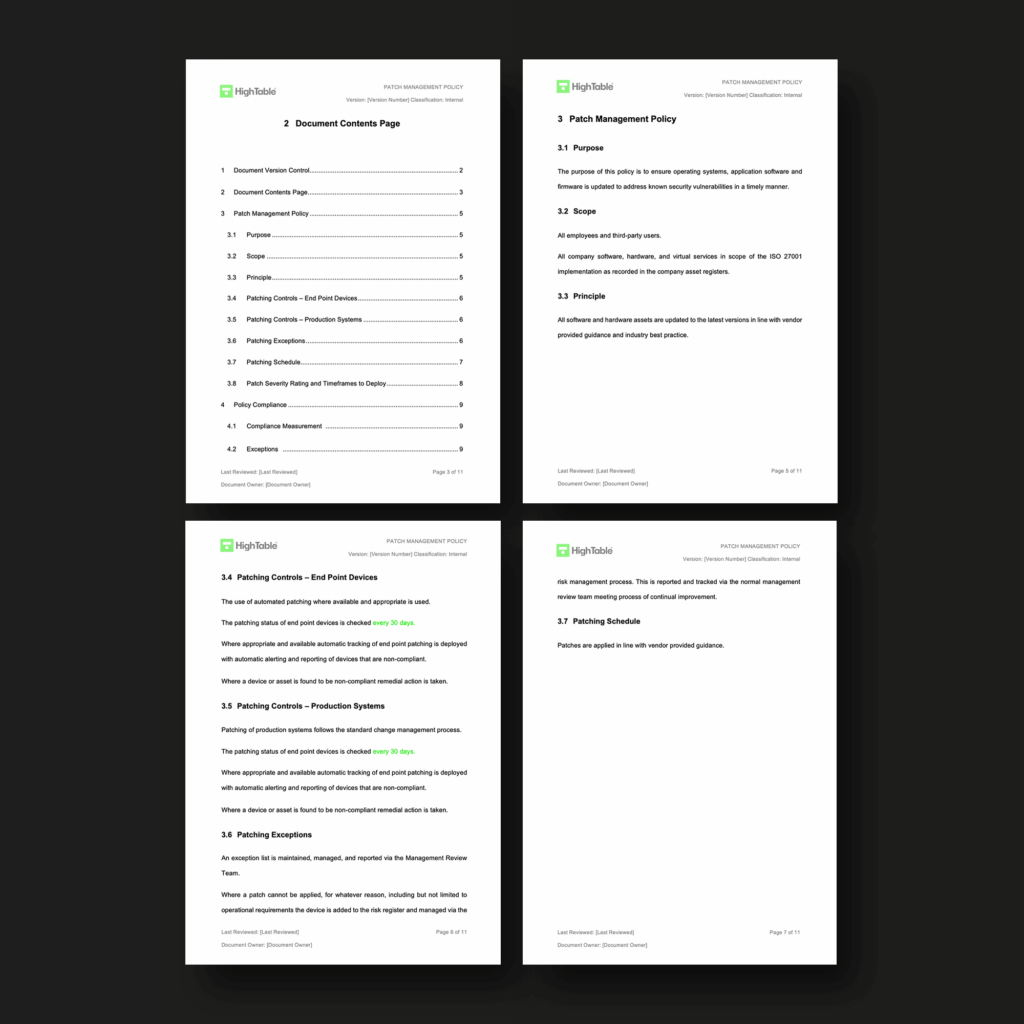
ISO 27001 Patch Management Policy Beginner s Guide Template

ISO 27001 Patch Management Policy Beginner s Guide Template
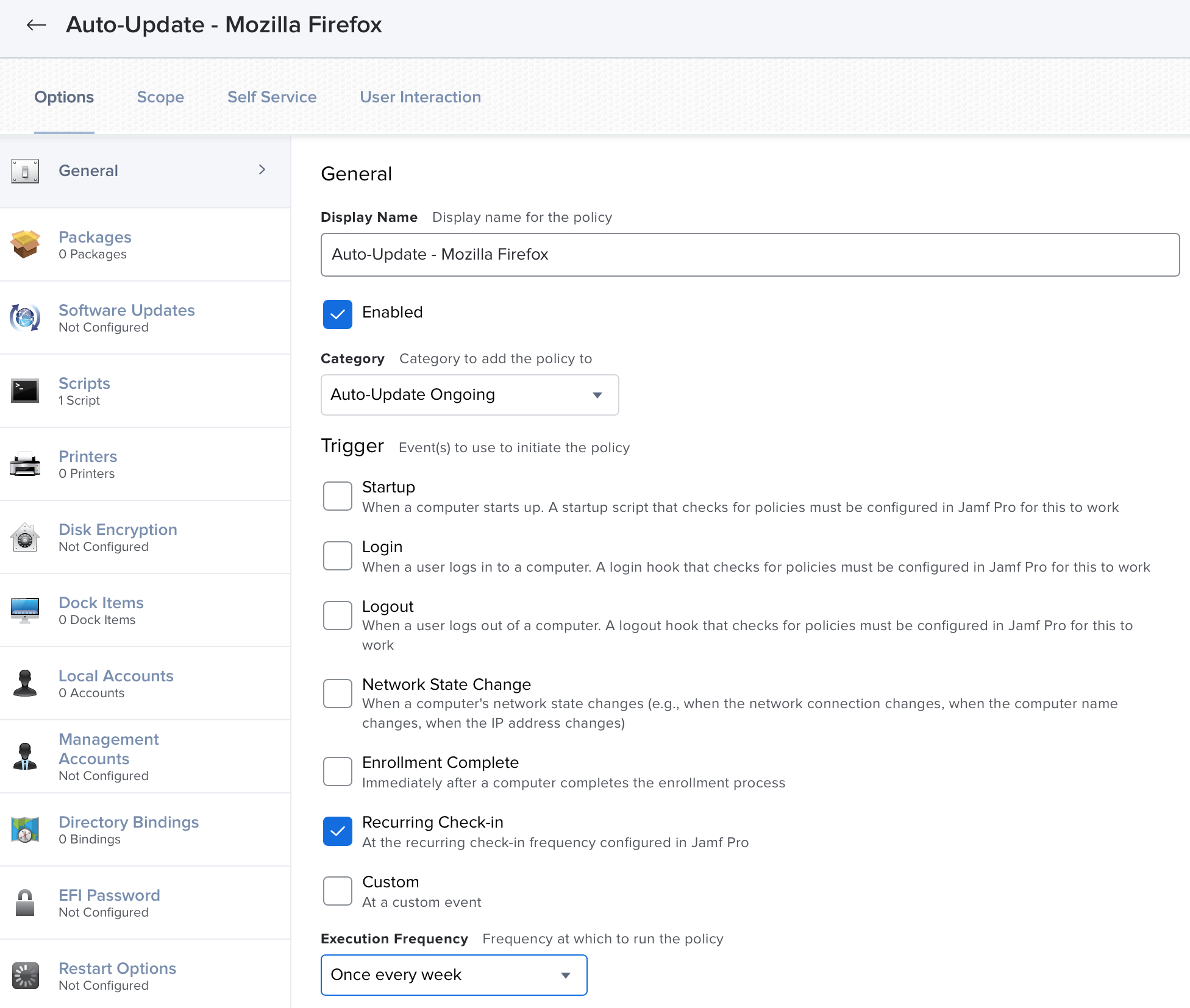
Patching Policy Template

Top 7 Vulnerability Management Process Flow Chart Templates with
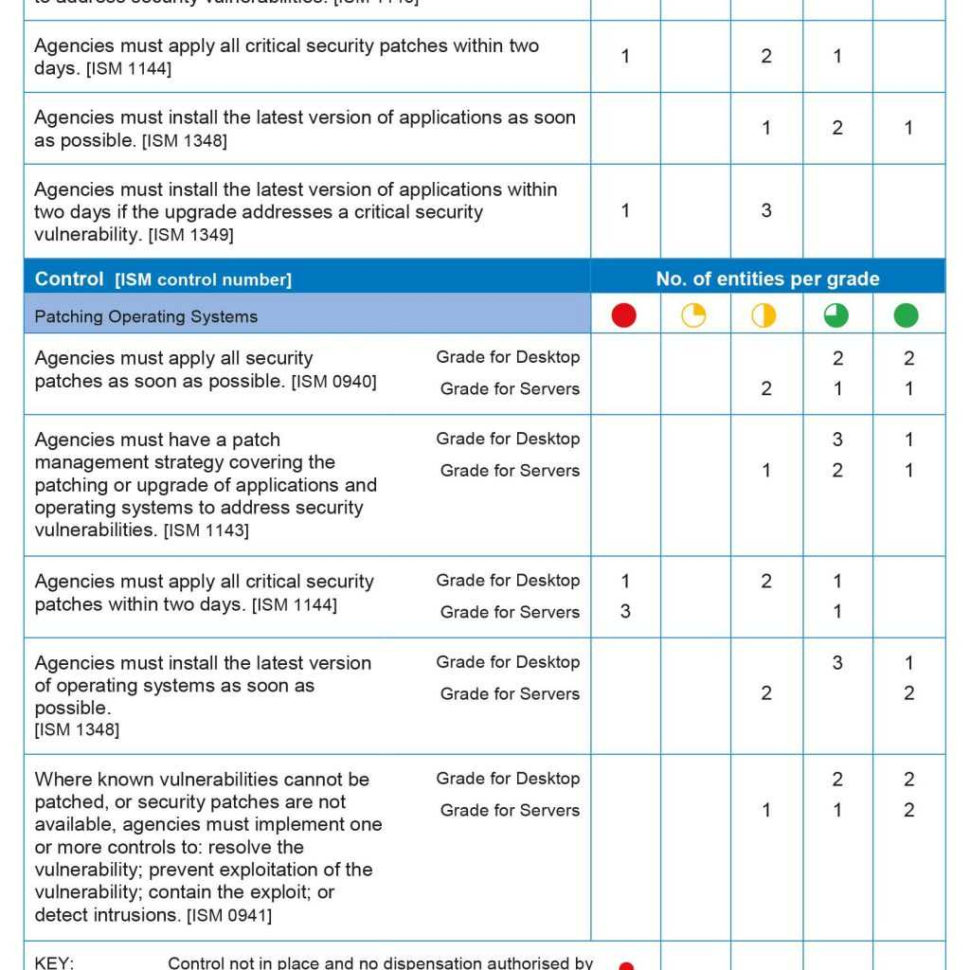
Patching Schedule Template

ISO 27001 Patch Management Policy Template