Vulnerability Management Certifications
Here are some of the images for Vulnerability Management Certifications that we found in our website database.

Vulnerability Management Managing IT Limited
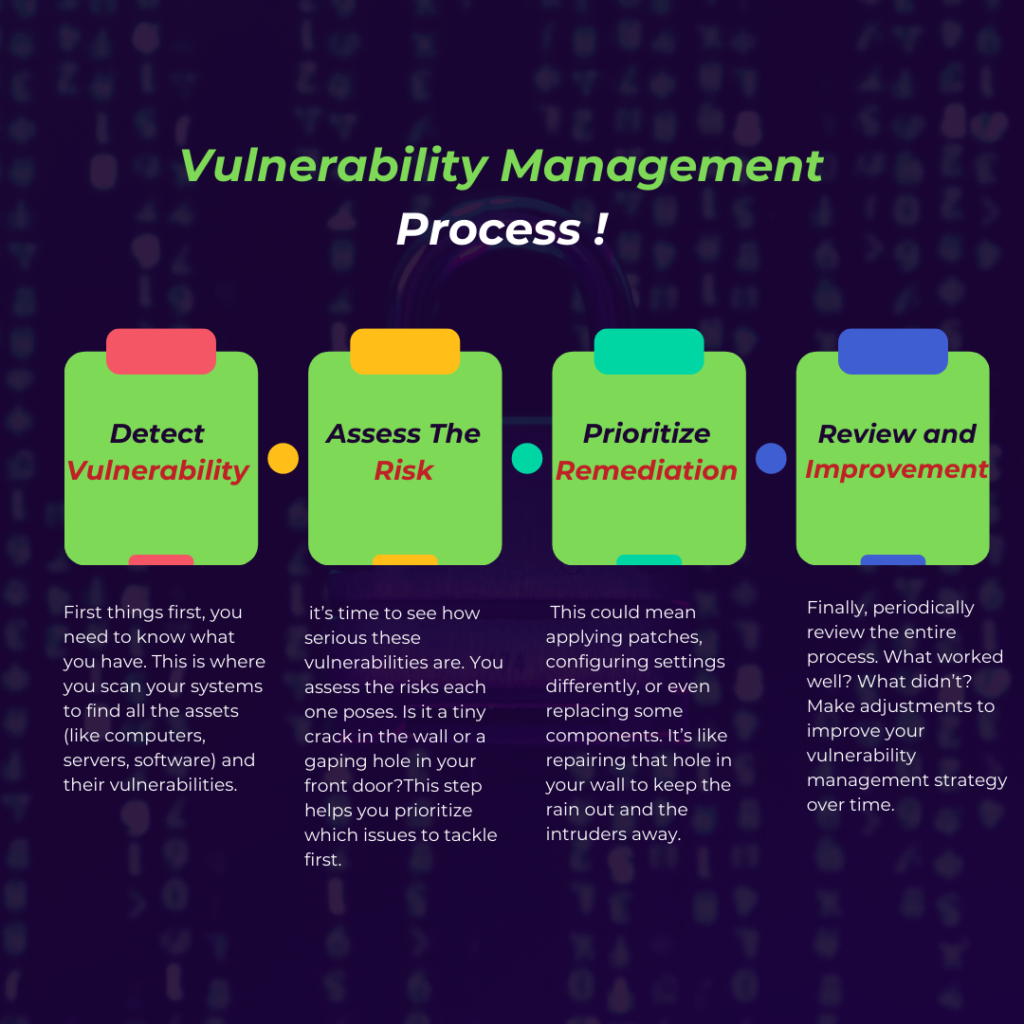
Master of Vulnerability Management

Vulnerability Management Certifications prntbl
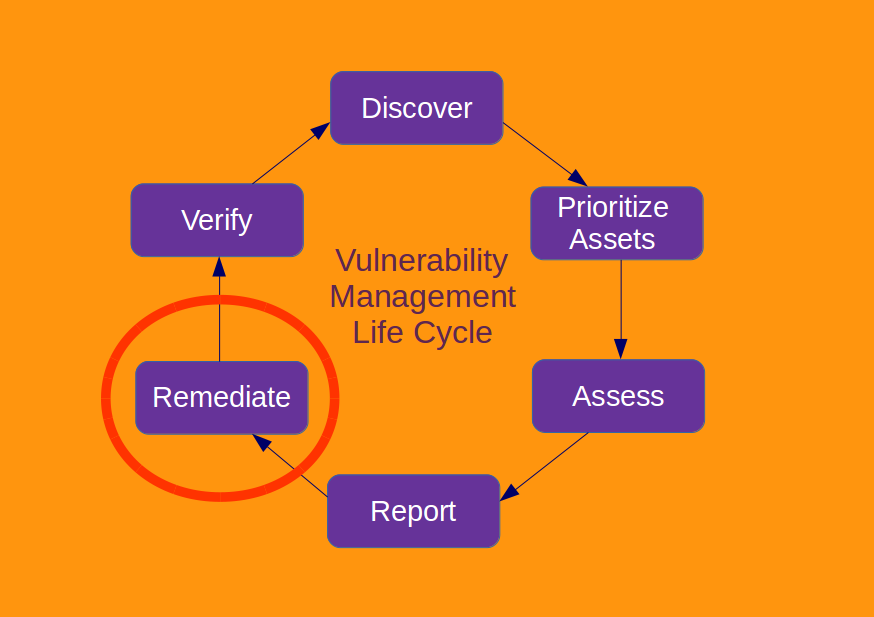
Vulnerability Management Certifications prntbl

Vulnerability Management Certifications prntbl
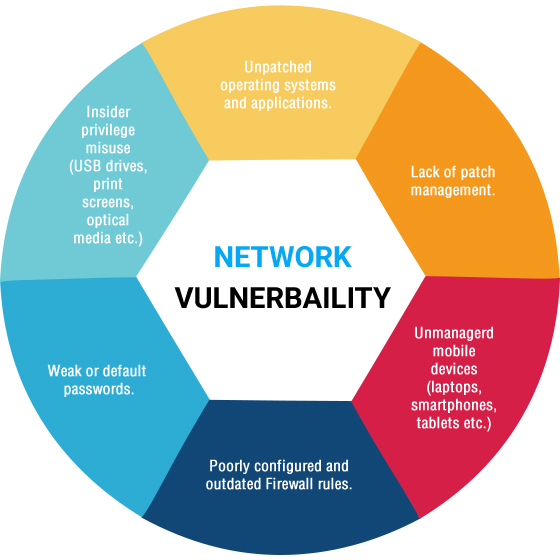
Vulnerability Management Certifications prntbl

Vulnerability Management Certifications prntbl
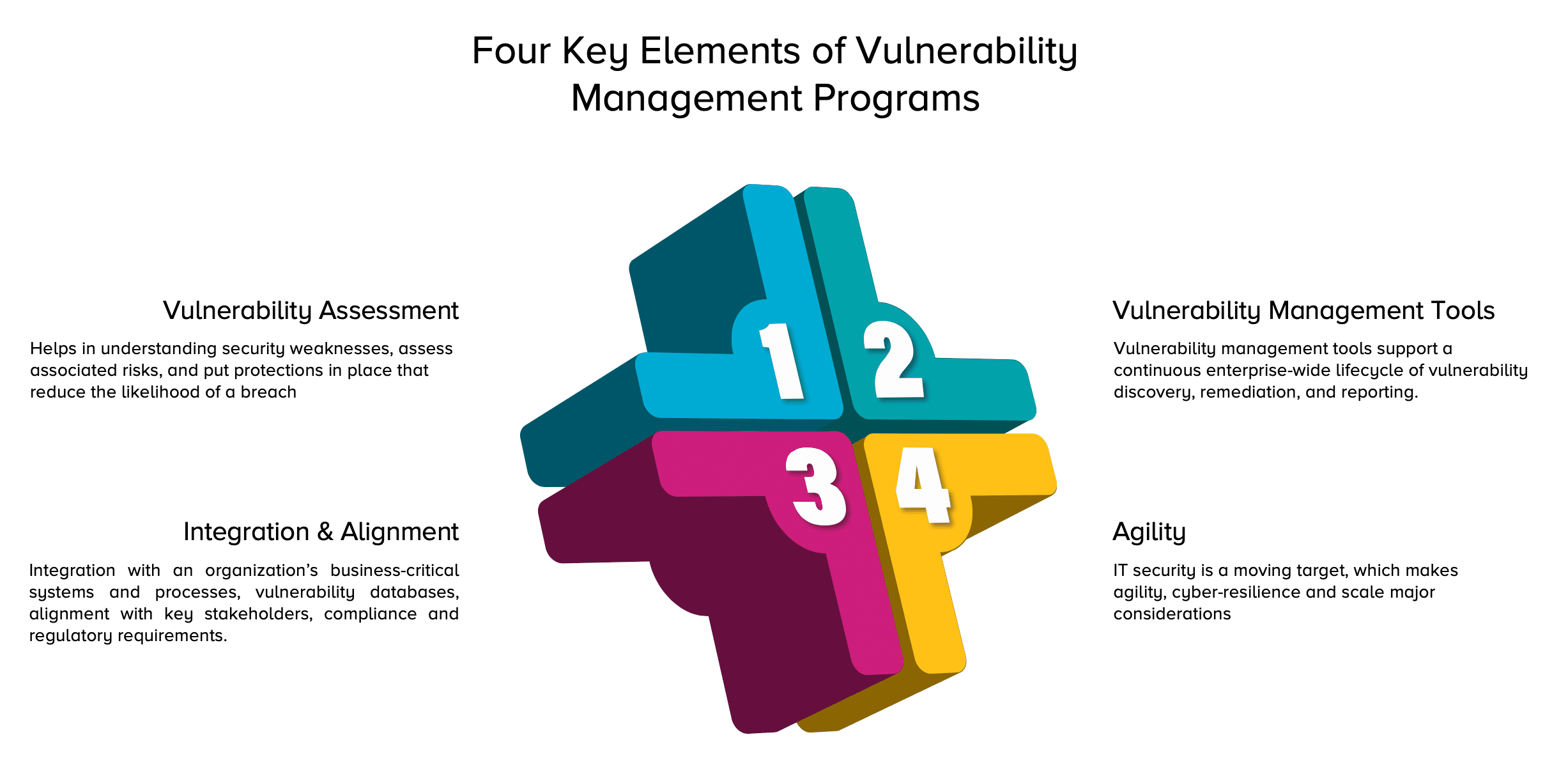
Vulnerability Management Certifications prntbl

Vulnerability Management Certifications prntbl
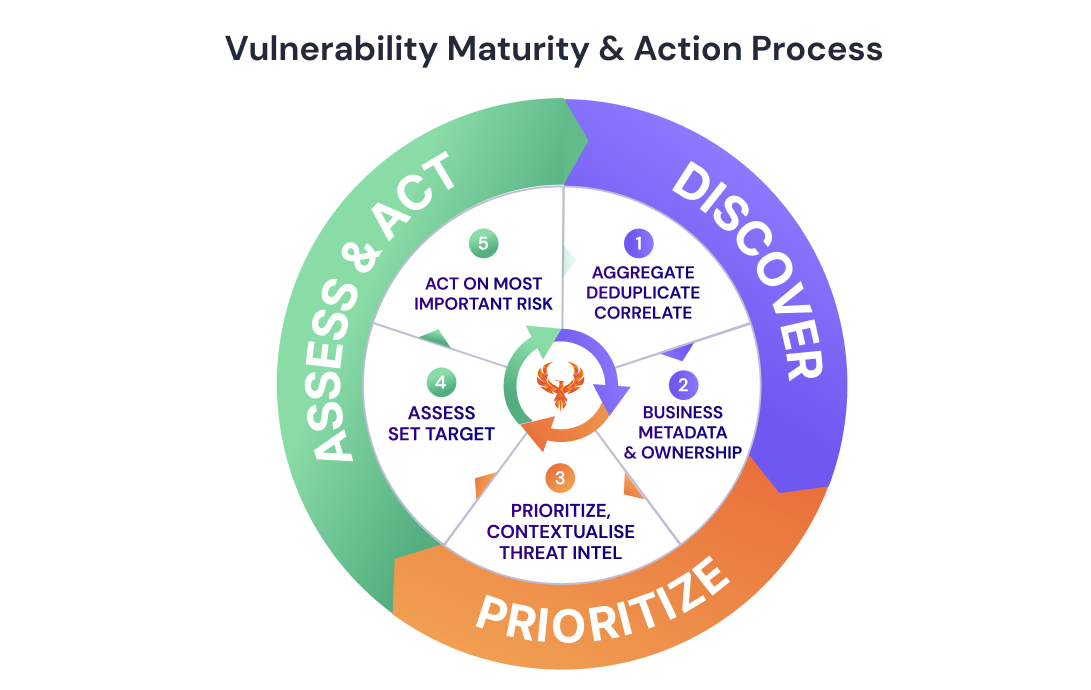
Vulnerability Management Certifications prntbl

Vulnerability Management System (VMS) on LinkedIn: #penetrationtesting

Quality Management Certifications Kinetic India

Vulnerability Management: Critical Strategy for IT Security
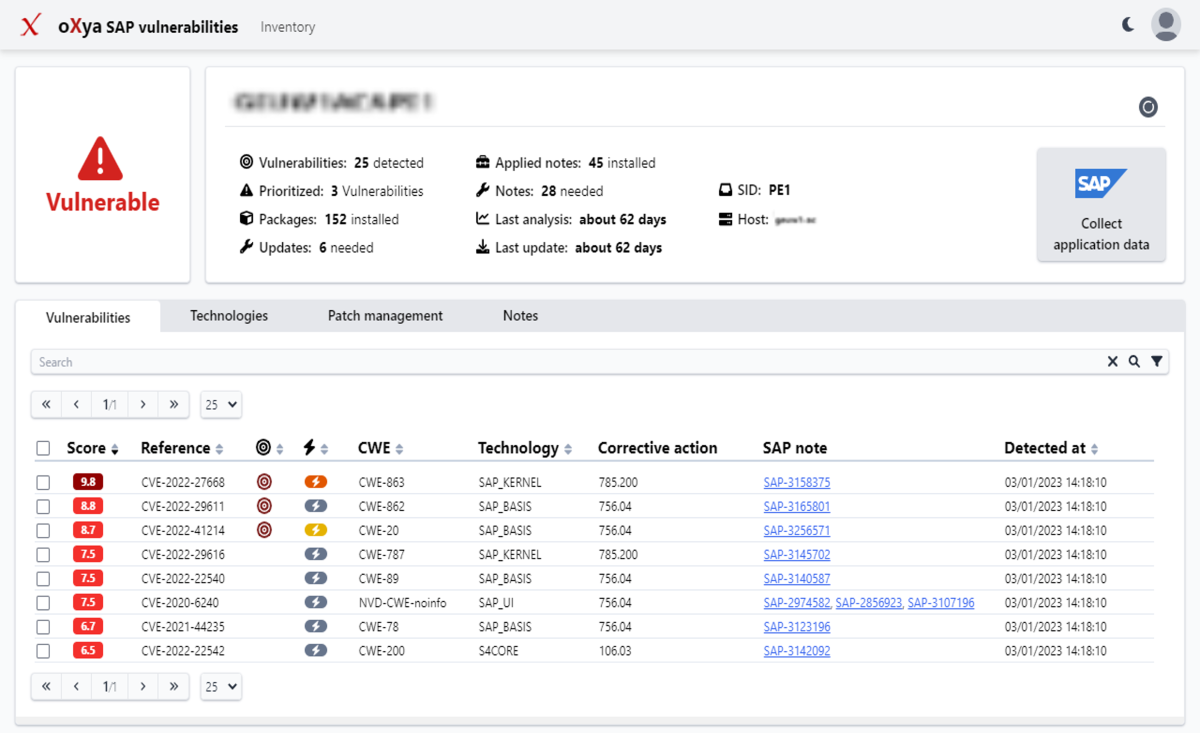
Vulnerability Management by oXya oXya

Vulnerability Management Services 12 Points
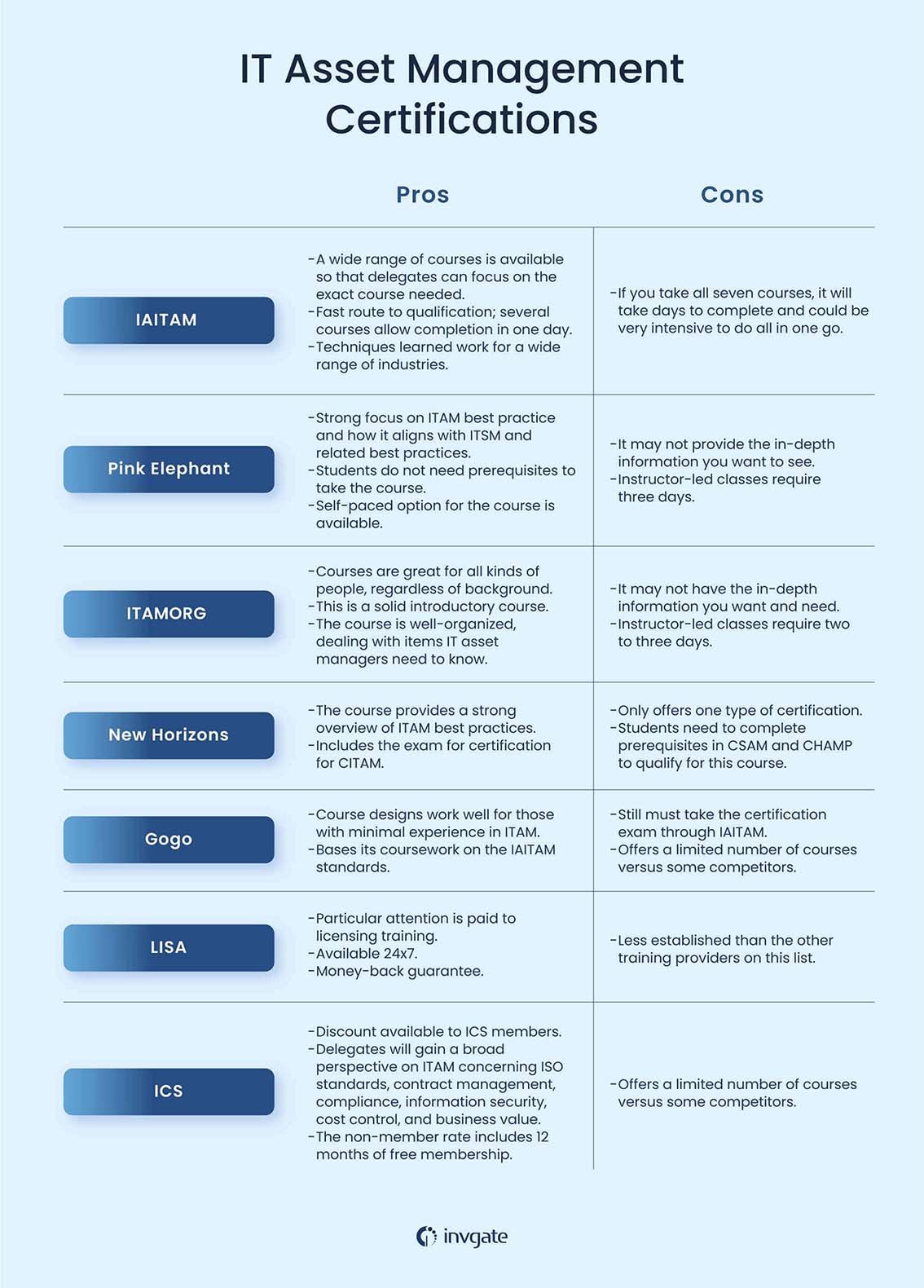
IT Asset Management Certifications: The 7 Best ITAM Training Courses

Top Certifications Certificates for Volunteer Management Professionals
Vulnerability Management: The Complete Guide Wiz

2023 State of Vulnerability Management Report

Just completed my certifications in Vulnerability Management Michael

Qualys Vulnerability Management pdf

Expert Vulnerability Assessment andTesting Services SIS

Expert Vulnerability Assessment andTesting Services SIS

Expert Vulnerability Assessment andTesting Services SIS

Anatomy of SAP Vulnerability Management

Top Project Management Certifications for 2025

Expert Vulnerability Assessment andTesting Services SIS
Vulnerability Management Controls for Critical Security Frameworks

Identity Access Management certifications
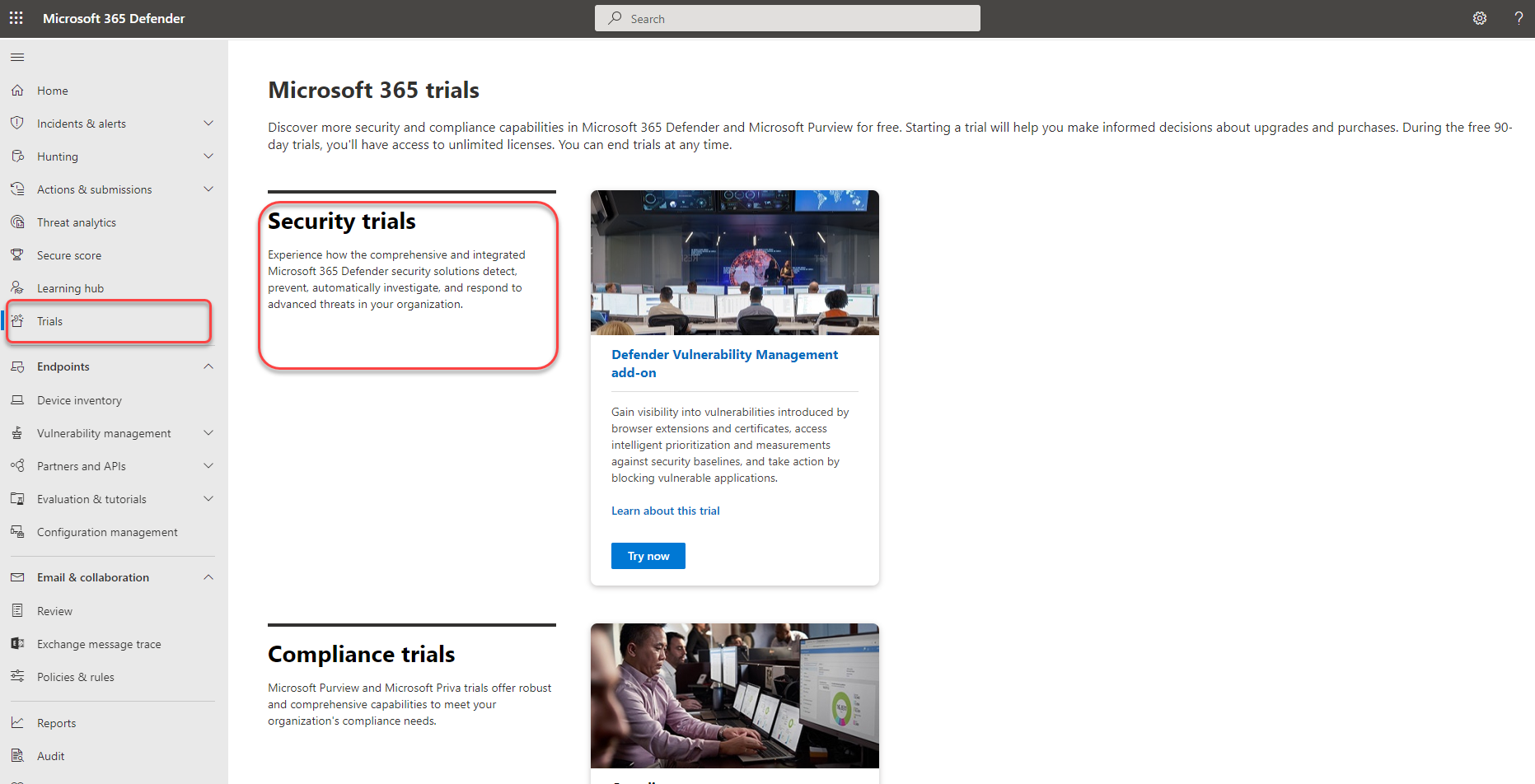
Trial user guide Microsoft Defender Vulnerability Management

Best Vulnerability Management Tools
Cybersecurity certifications for data protection outline icons

Open Source Enterprise Vulnerability Management Software Tools PPT

Understanding Vulnerability Management

11 Best Talent Management Certifications in 2025 People Managing People

What Certifications Do You Need for Asset Management? Multiply Technology

Vulnerability Worksheets

Top 10 Vulnerability Management Tools for 2025 GCS Network

Wealth Management Certifications Career Growth Flexible Academy of

Vulnerability Management Policy Template (Free) eSecurity Planet

The Most In demand Project Management Certifications in 2024 Yassine

Talent Management Certifications Template Venngage

Vulnerability assessment andtesting PPT

6 Top Vulnerability Management Tools and How They Help Prioritize

Top 5 Best Vulnerability Management Software for 2022 The

15 Best Project Management Certifications to Advance Your Career

Security Blue Team Certifications Freelancer

Study Time for Project Management Certifications

Vulnerability Assessment andTesting EC Council Global

The Importance of Vulnerability Management: Reducing your Cyber Risks

Best SOC Analyst Certifications (2025 s Expert Picks)

5 Incident Response Certifications for 2024
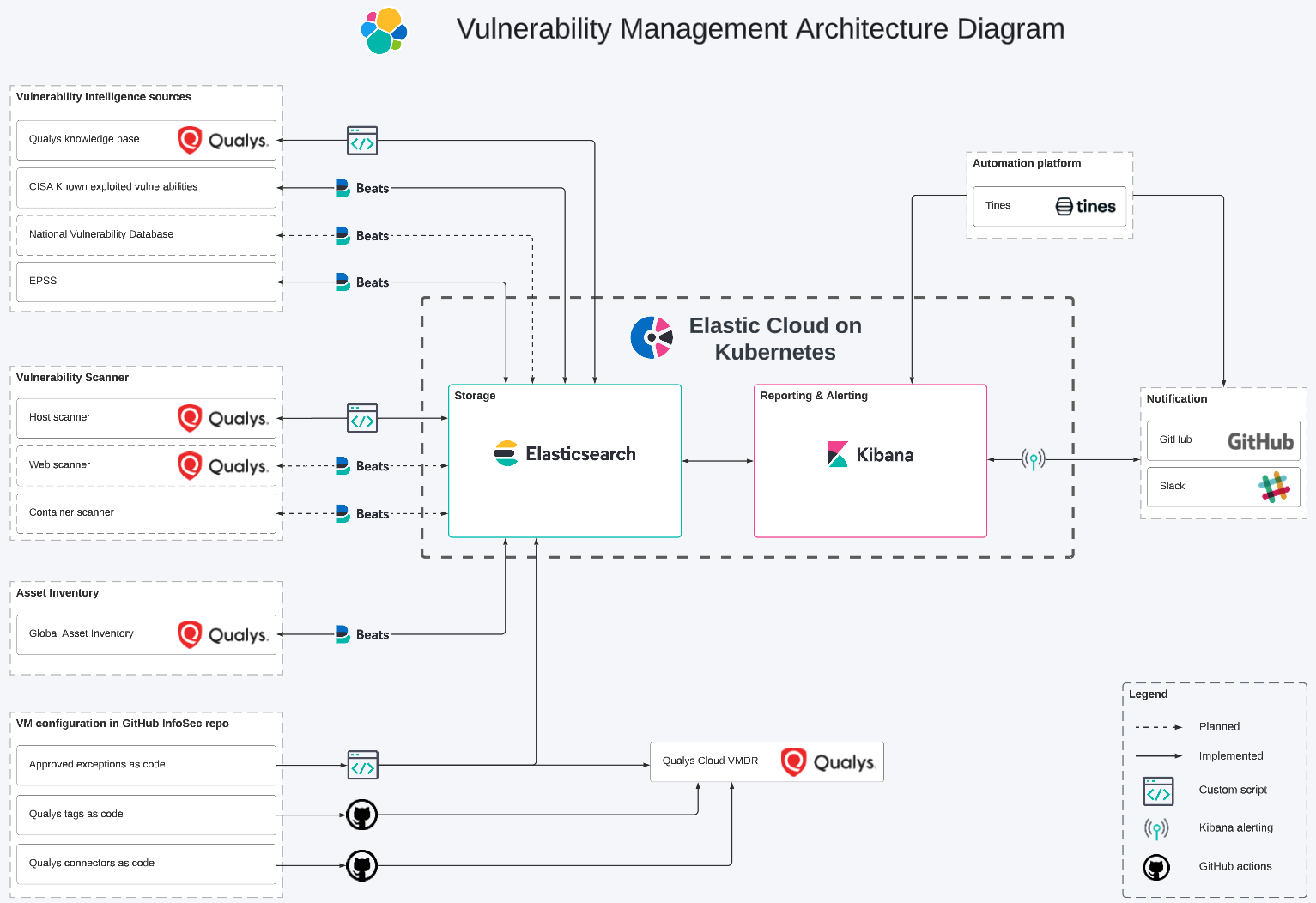
¿Qué es la gestión de vulnerabilidades? Una guía completa de gestión
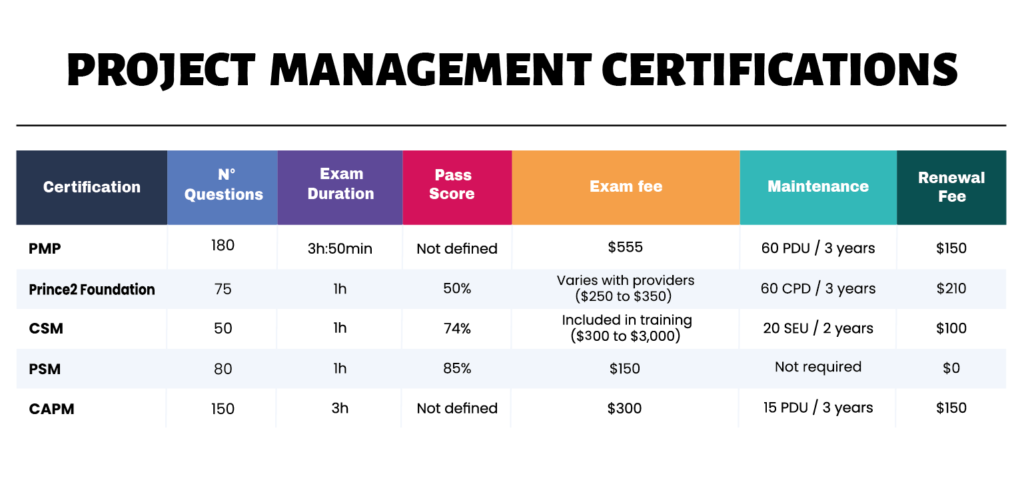
What Is Project Management Project Management Certifi vrogue co

How To Get FREE Qualys Certification Training in 2022 Watch Today

Pinterest

Karl Moses LinkedIn

Archives PMO Advisory

Cisco Networking Academy added Cisco Networking Academy

Yousuf Adil Chartered Accountants Yousuf Adil Chartered Accountants