Vulnerability Management Certifications
Here are some of the images for Vulnerability Management Certifications that we found in our website database.

What Are The Benefits Of Using Vulnerability Management Software Enmaru Indonesia

Vulnerability Management Certifications prntbl concejomunicipaldechinu gov co

Vulnerability Management Services Cloud21

Patch Management vs Vulnerability Management

Vulnerability Management by Wentz Wu CISSP/ISSMP/ISSAP/ISSEP CCSP CSSLP CISM PMP CBAPWentz Wu

Top 10 vulnerability assessment and management best practices Sysdig

Vulnerability Management: Lifecycle Tools and Best Practices
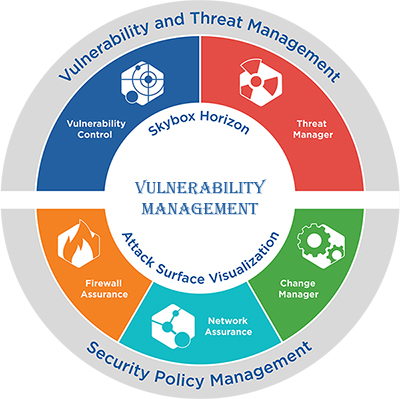
Vulnerability Management Intelipath Group

Vulnerability Management Lifecycle Blue Team Resources

Unified Vulnerability Management (UVM) Services Microland

Top 10 Vulnerability Management Tools Spiceworks

Vulnerability Management System: The Definitive Guide (2022) Cyvatar

How To Build An Effective Vulnerability Management Program

Vulnerability Management: Processes and tools
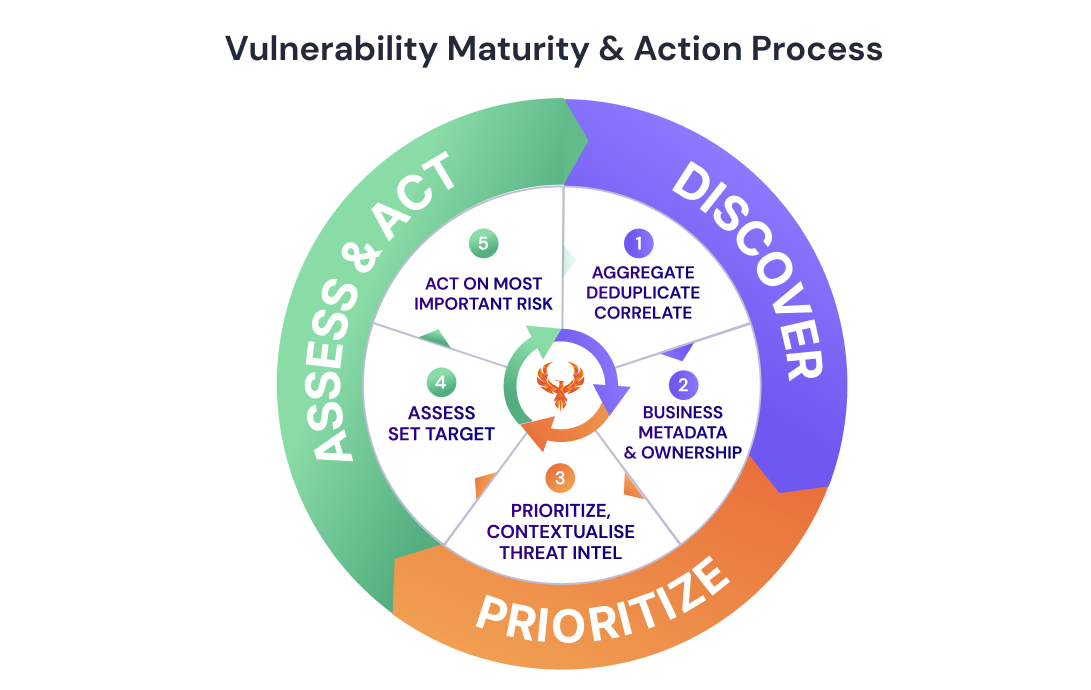
Vulnerability Managment Framework Application Security Code to Cloud

What Is Vulnerability Management? Get the Answers You Need
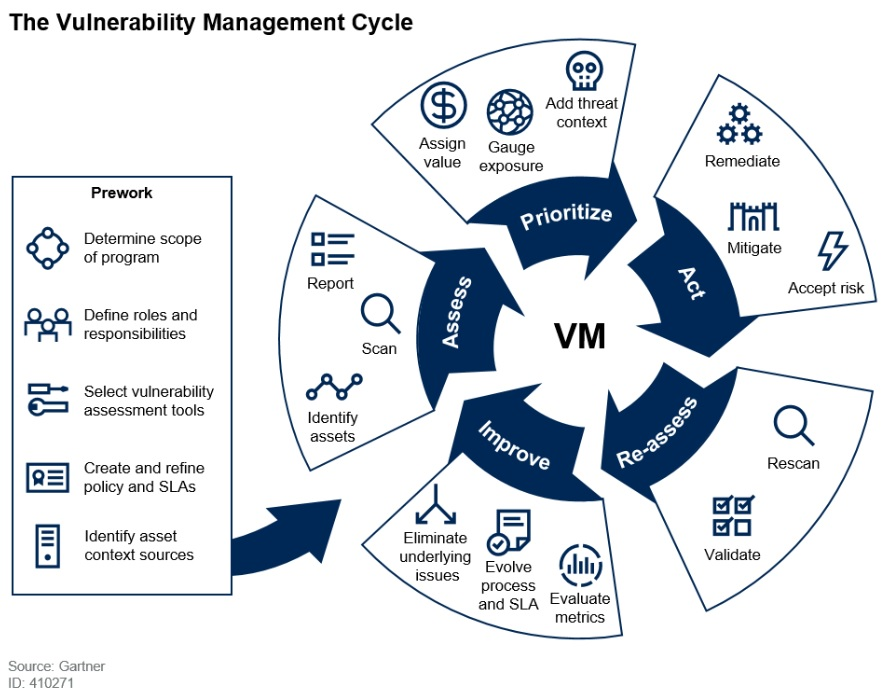
The Art of Proactive Vulnerability Remediation Netrust
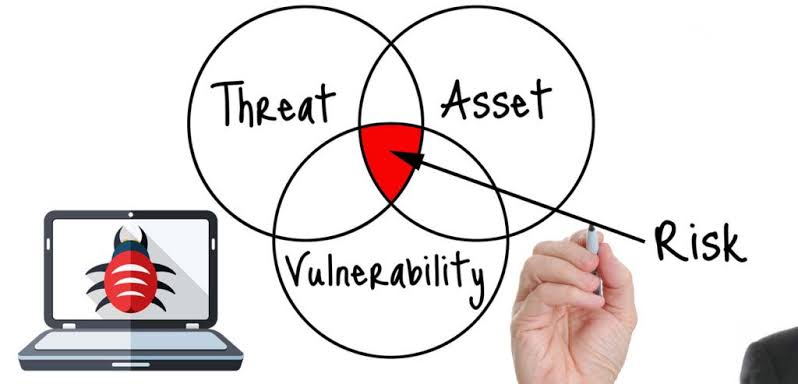
How is Vulnerability Management Different from Vulnerability Assessment? Kratikal Blogs

How To Perform A Vulnerability Assessment: A Step by Step Guide

Vulnerability Management: Processes and tools

Cisco Certifications Cyber Threat Prioritize Real Time Vulnerability Networking Management
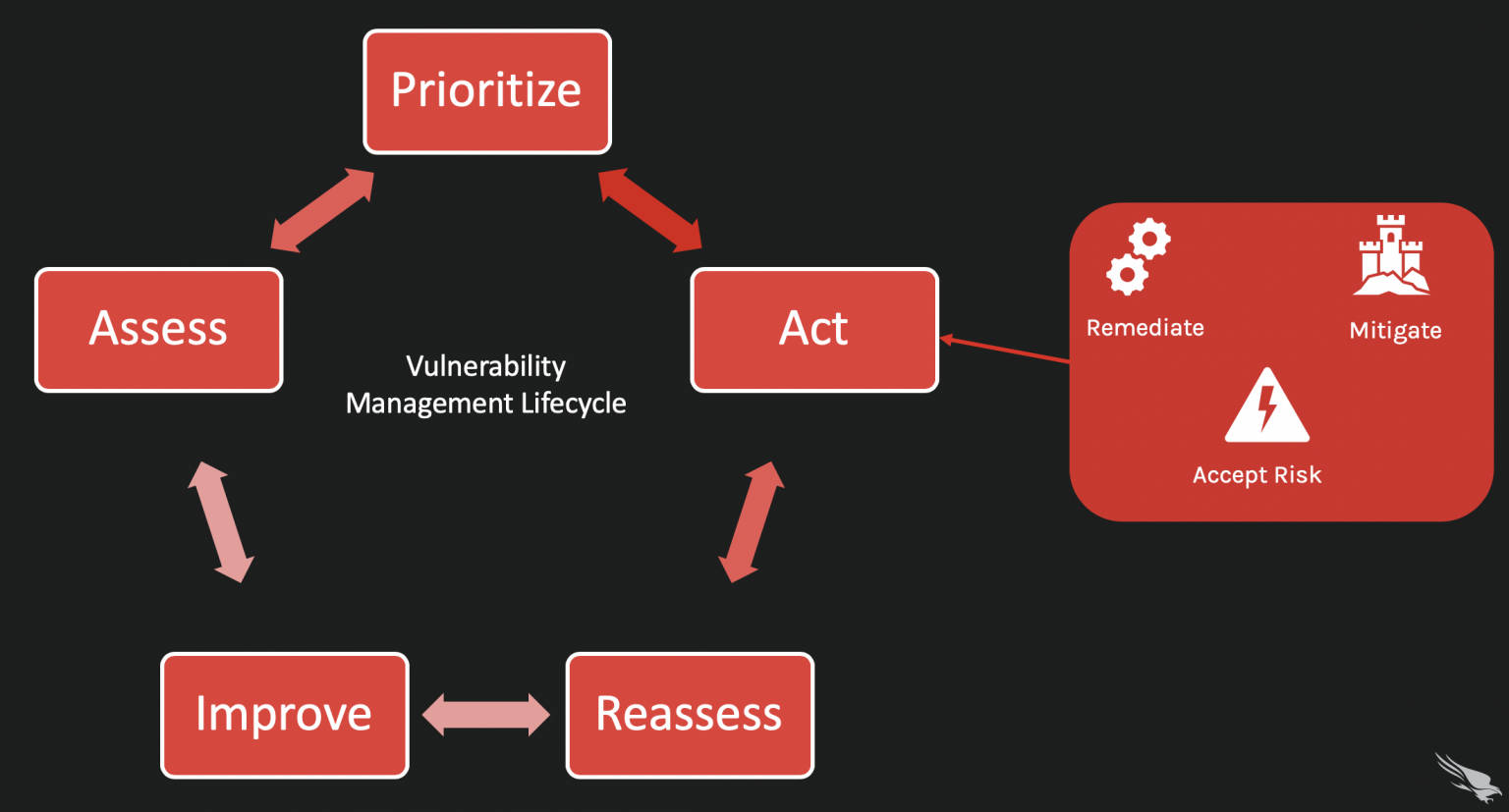
The Vulnerability Management Lifecycle (5 Steps) CrowdStrike

Vulnerability Management: Keystone of Cybersecurity Infrastructure

Top 5 Best Vulnerability Management Software for 2022 The Cybersecurity Times
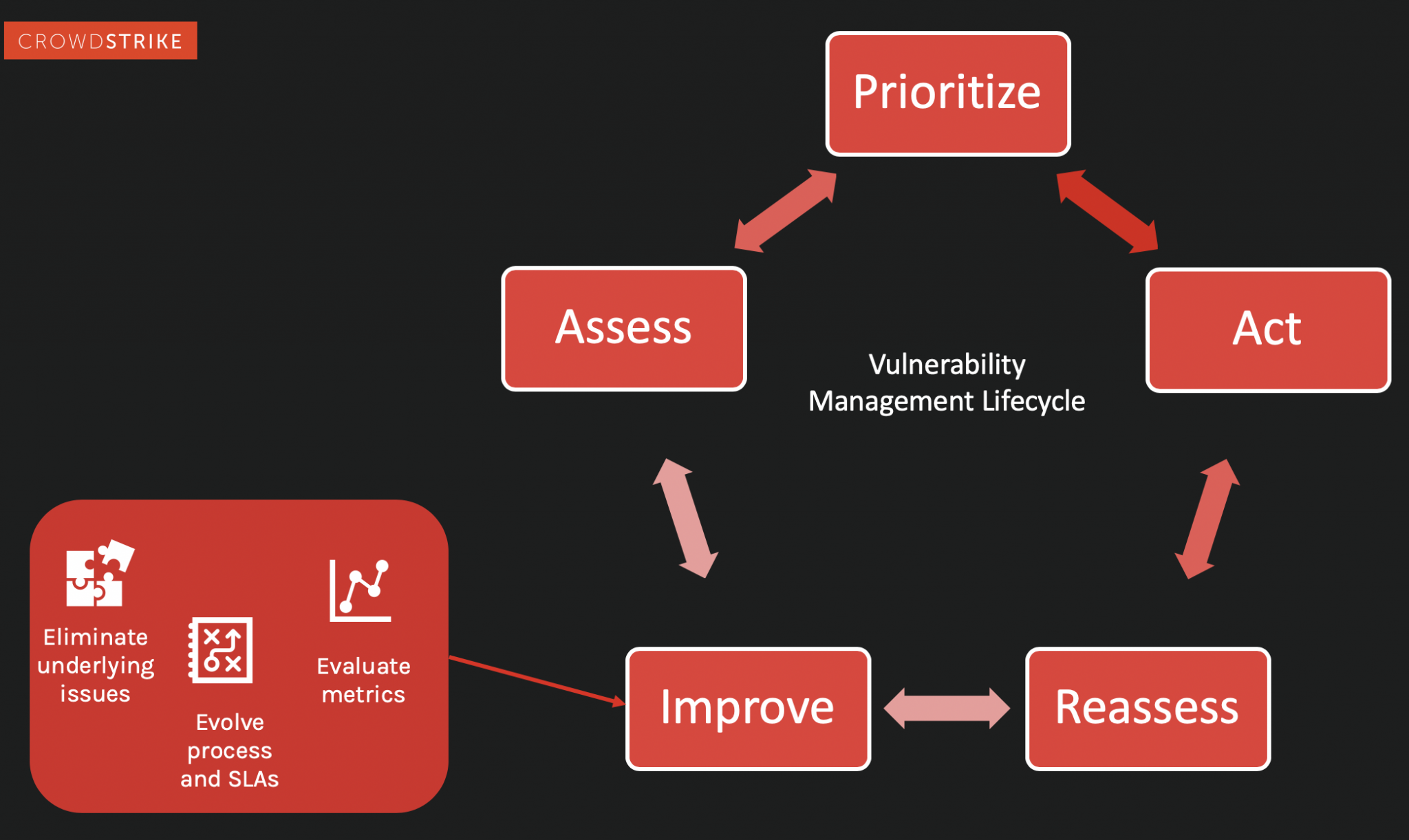
The Vulnerability Management Lifecycle (5 Steps) CrowdStrike
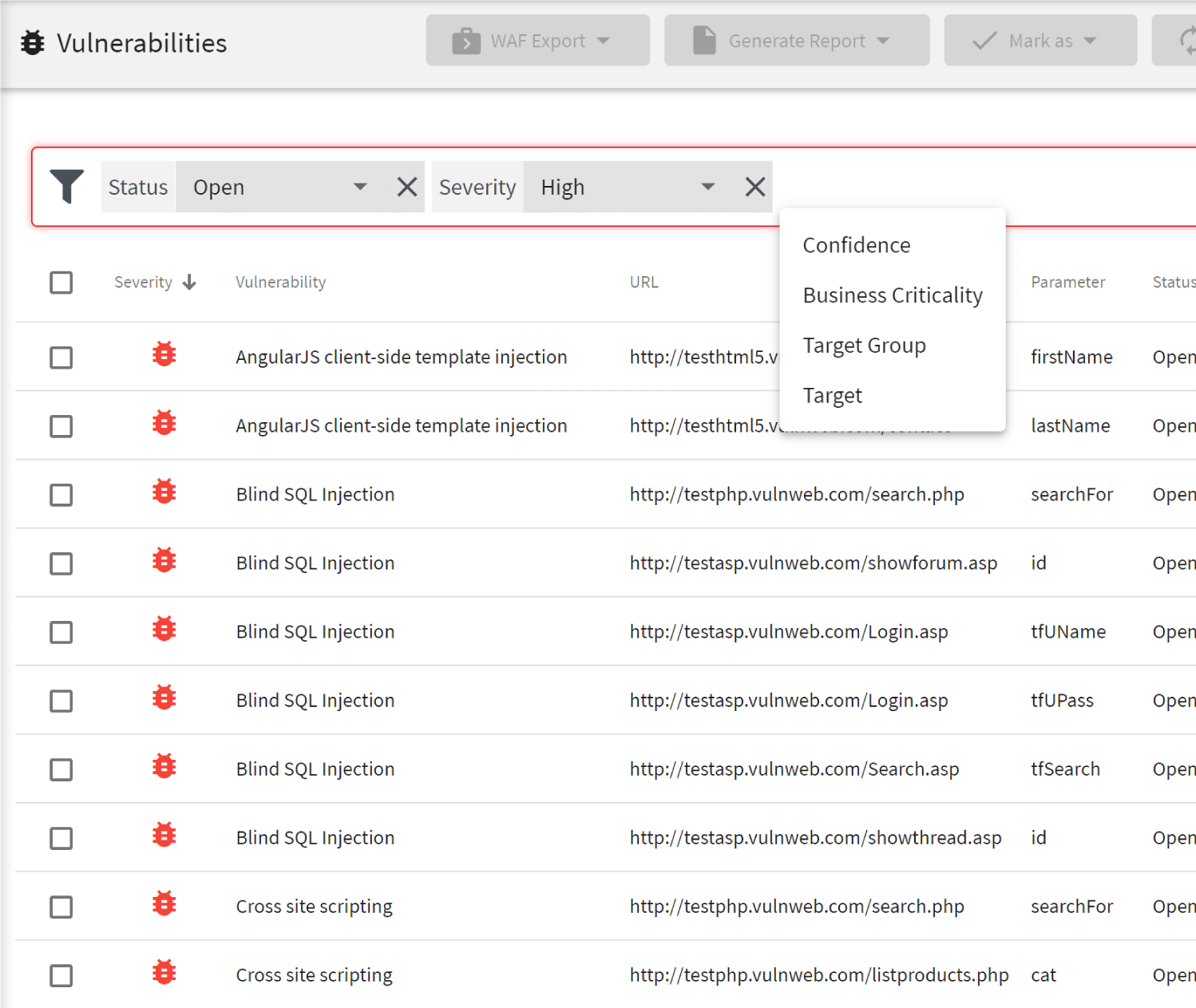
Vulnerability Management Software Acunetix ob欧宝体育在线登录备用
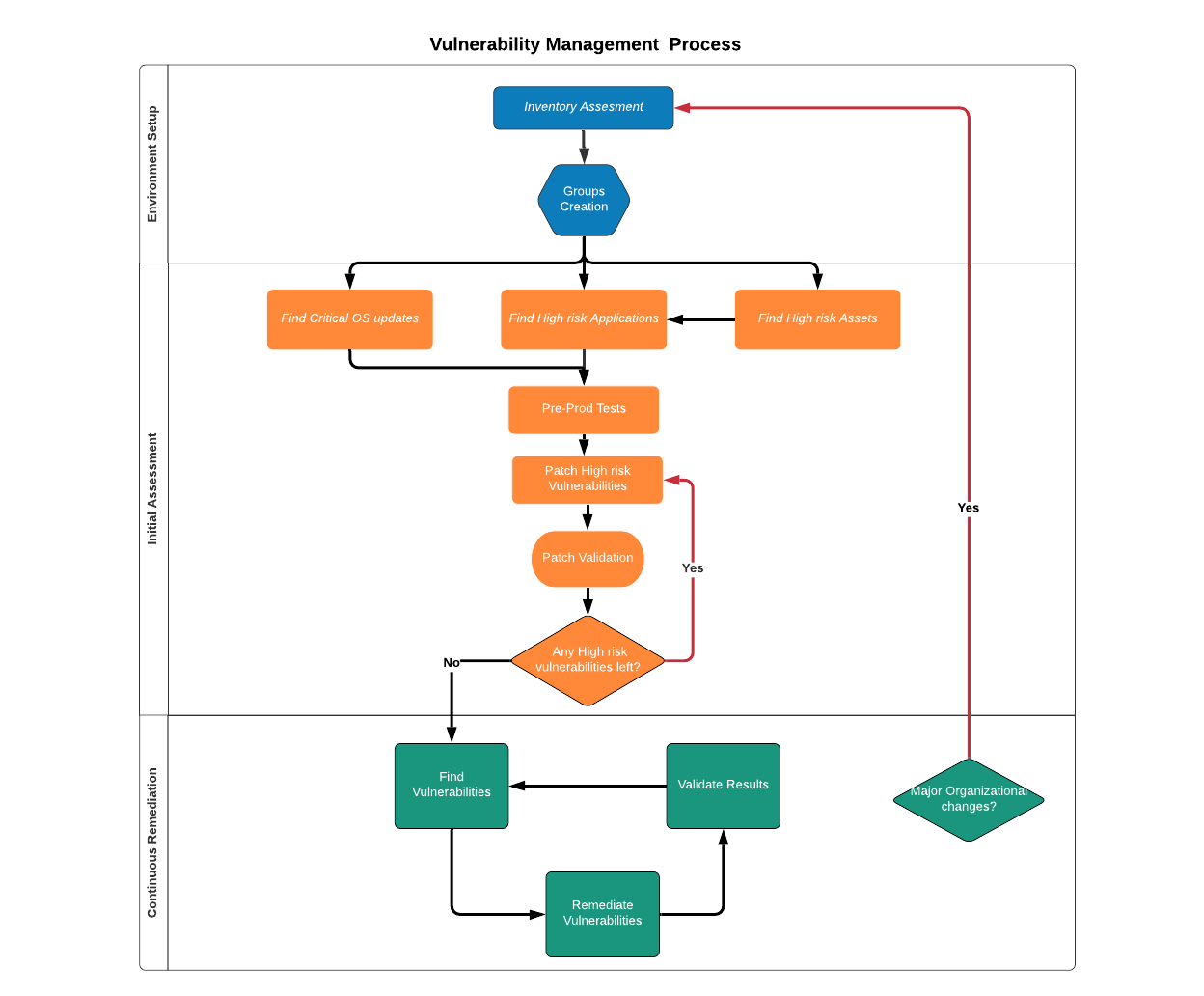
Vulnerability Management Best Practices Vicarius

Introducing a risk based approach to threat and vulnerability management Microsoft Community Hub

How to Have an Effective Vulnerability Management Program
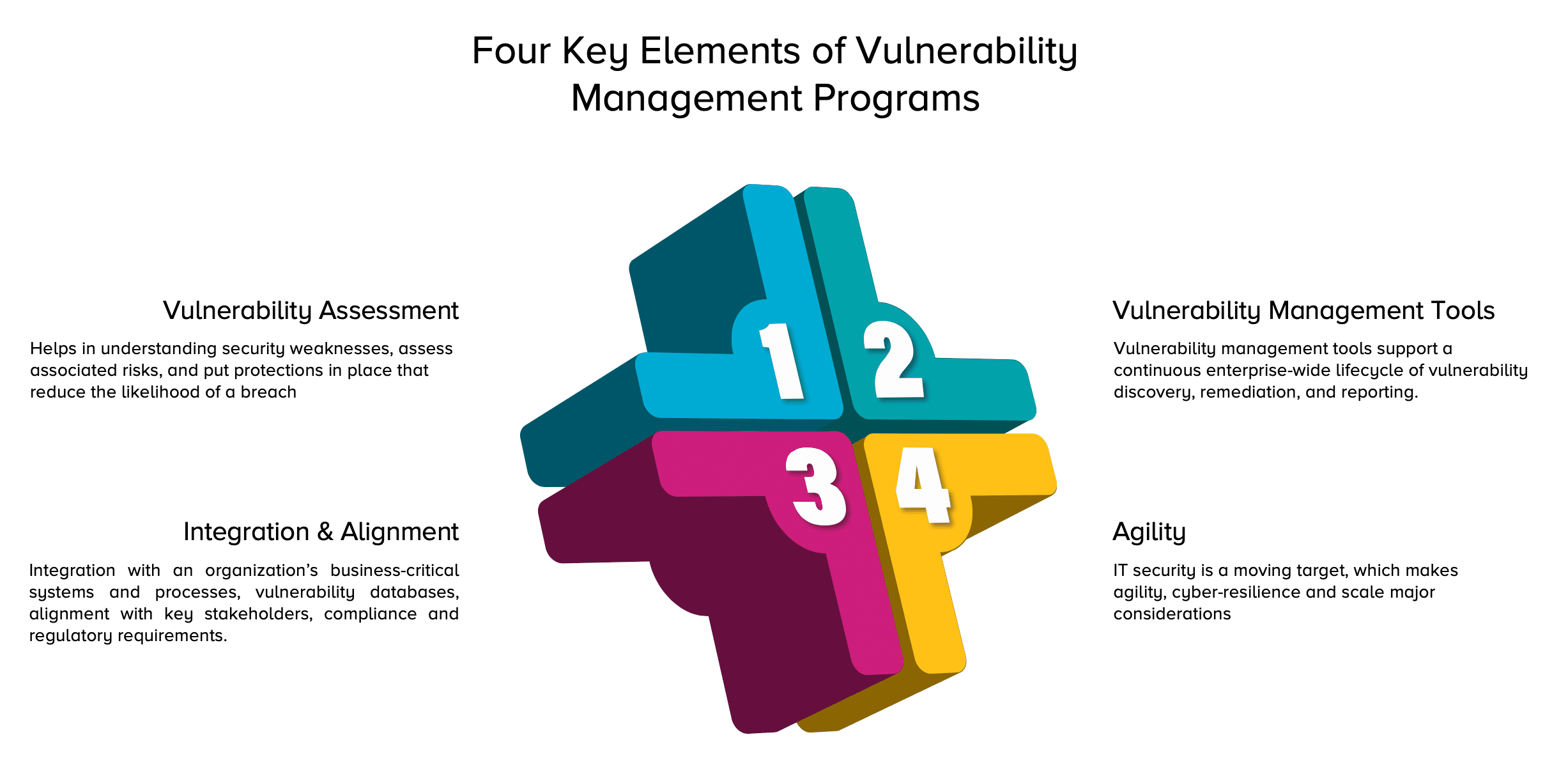
Vulnerability Management Certifications prntbl concejomunicipaldechinu gov co
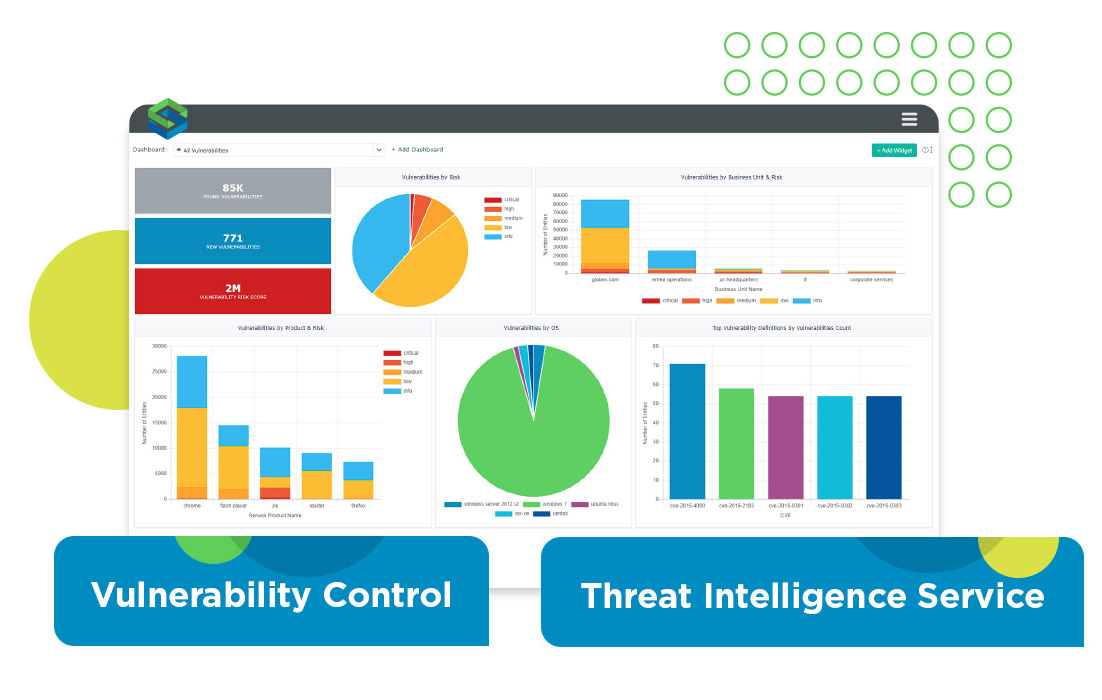
Prevent breaches with proactive vulnerability management
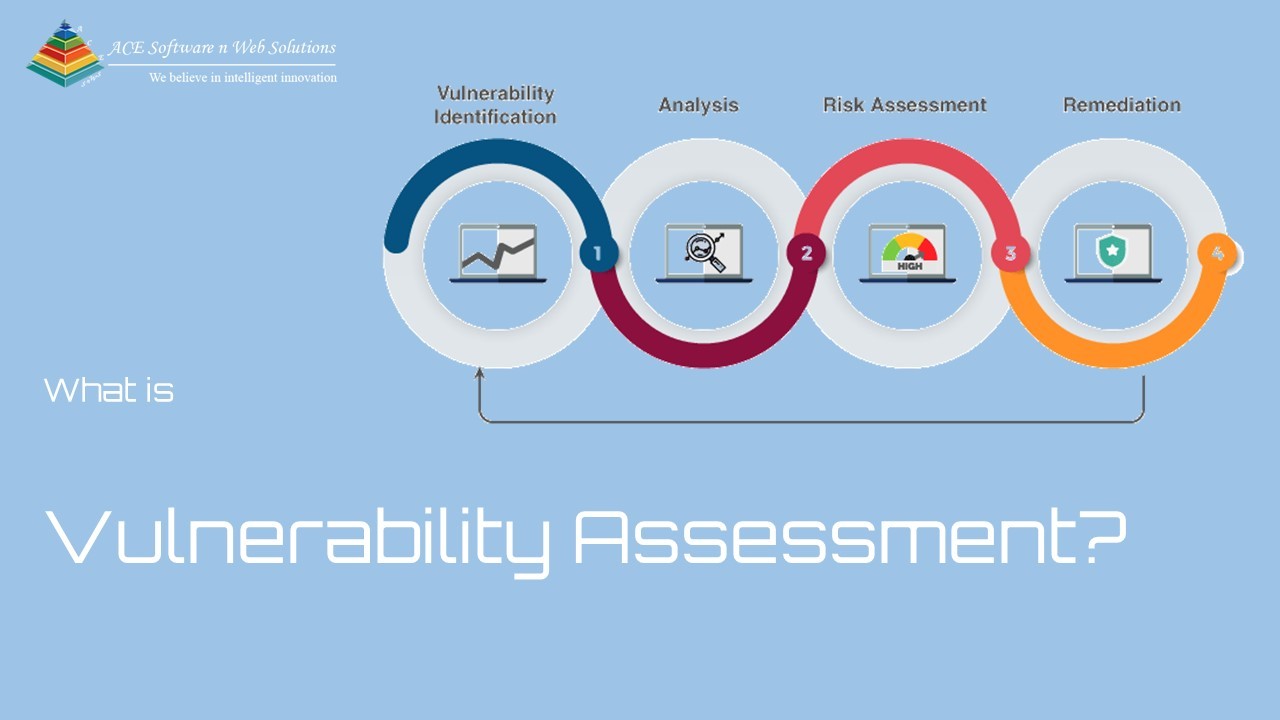
What is Vulnerability Assessment?

Vulnerability Management Download Scientific Diagram

MVRE Certified Vulnerability Researcher and Exploitation Specialist Security Researcher Training

Introducing a risk based approach to threat and vulnerability management Microsoft Community Hub

The complete guide to vulnerability assessment Theme Vision
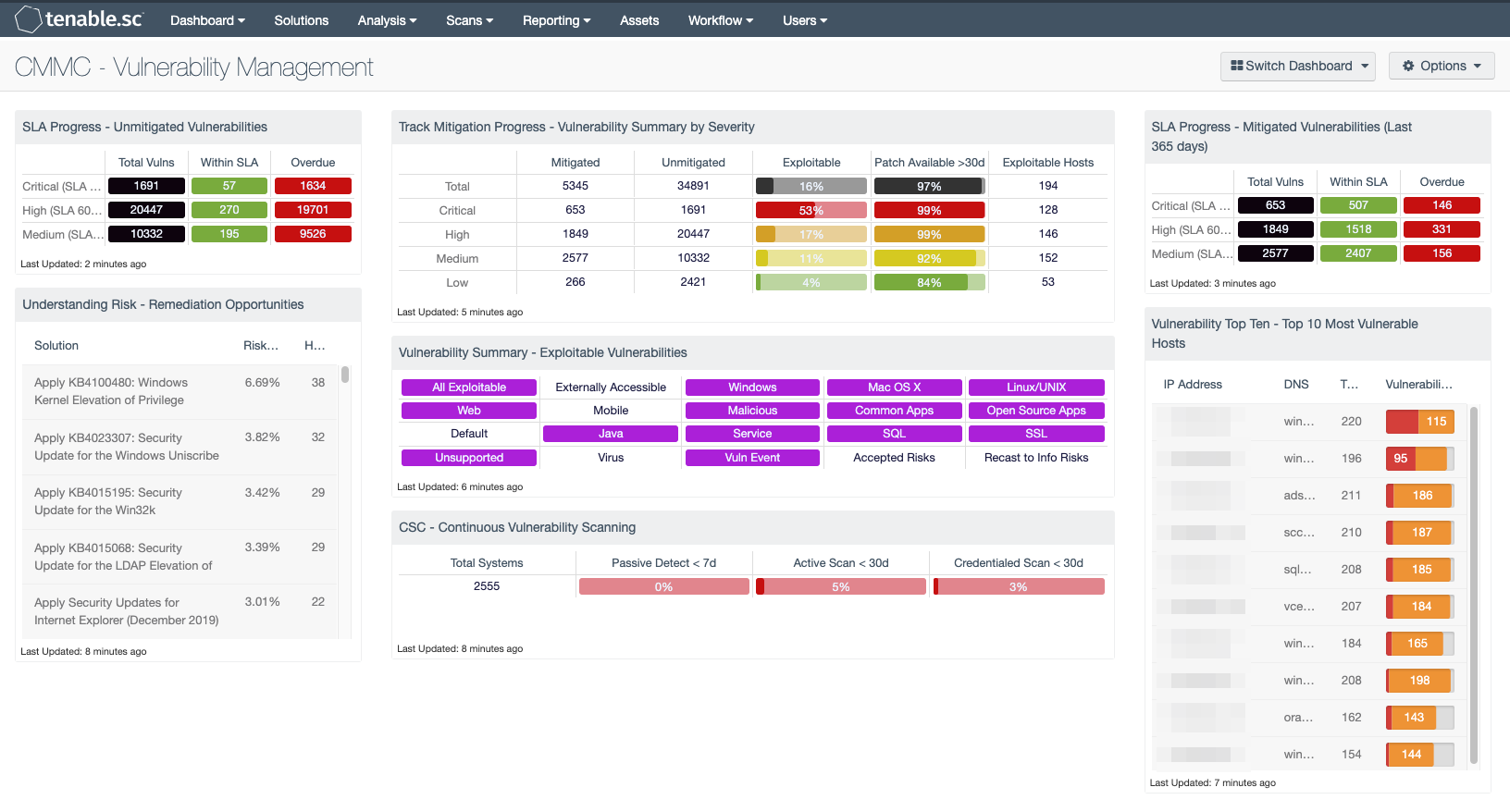
CMMC Vulnerability Management SC Dashboard Tenable®
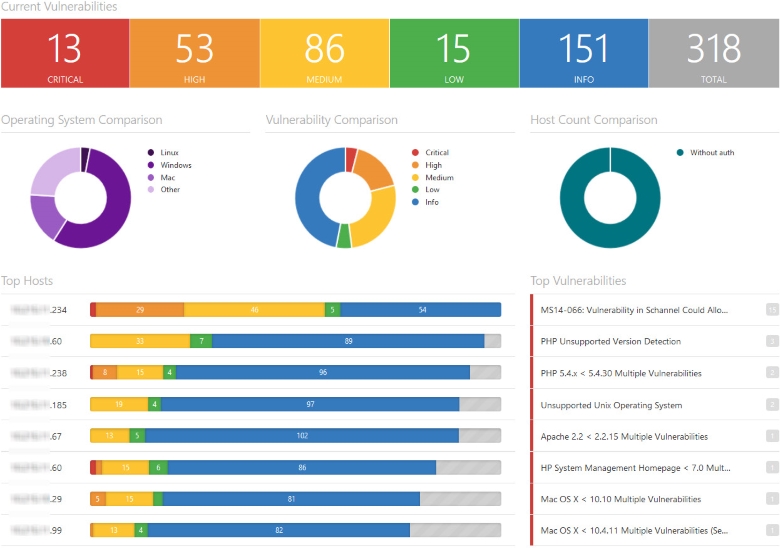
Network / PCI ASV Vulnerability Scanning E Com Security Solutions
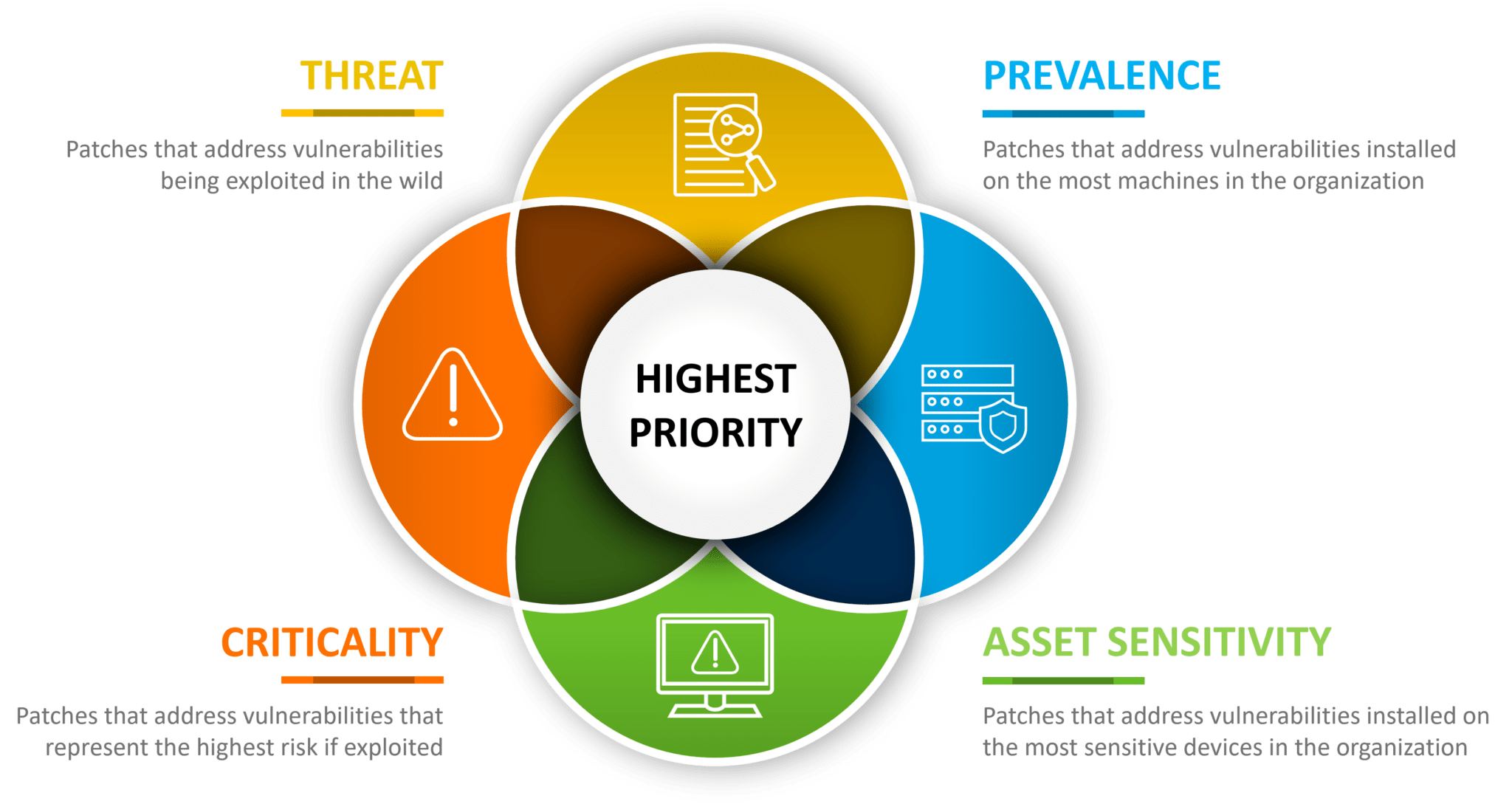
Software Vulnerability Prioritization
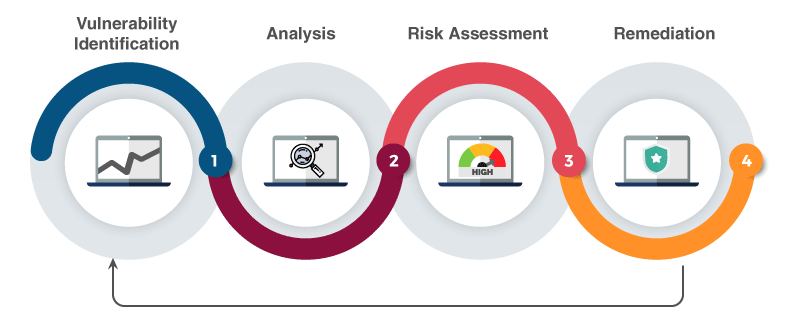
Vulnerability Assessments: A Quick Guide

Product showcase: ManageEngine Vulnerability Manager Plus Help Net Security

https://itcertinfographic blogspot com/2020/02/an overview on comptia cybersecurity

Vulnerability Management Protects Your Organization Riset
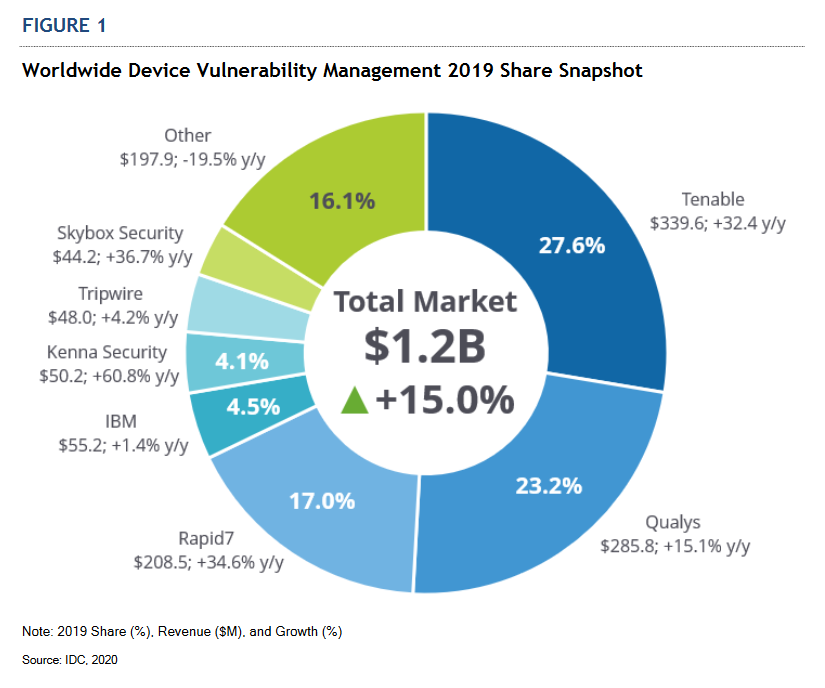
Tenable is #1 in vulnerability management market share
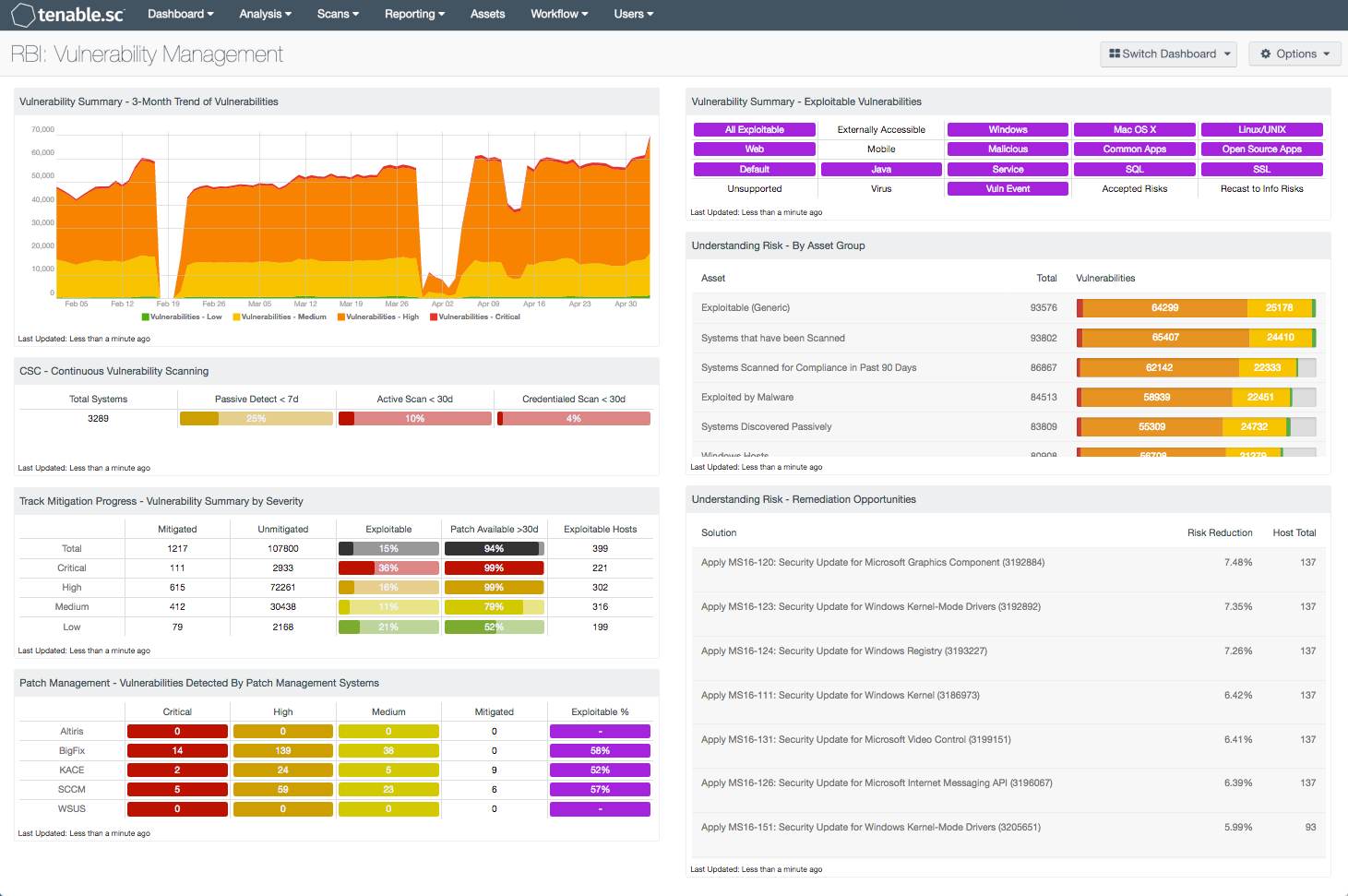
RBI: Vulnerability Management SC Dashboard Tenable®

What is vulnerability management? Vulnerability management process ManageEngine

Vulnerability Risk Assessment Gambaran
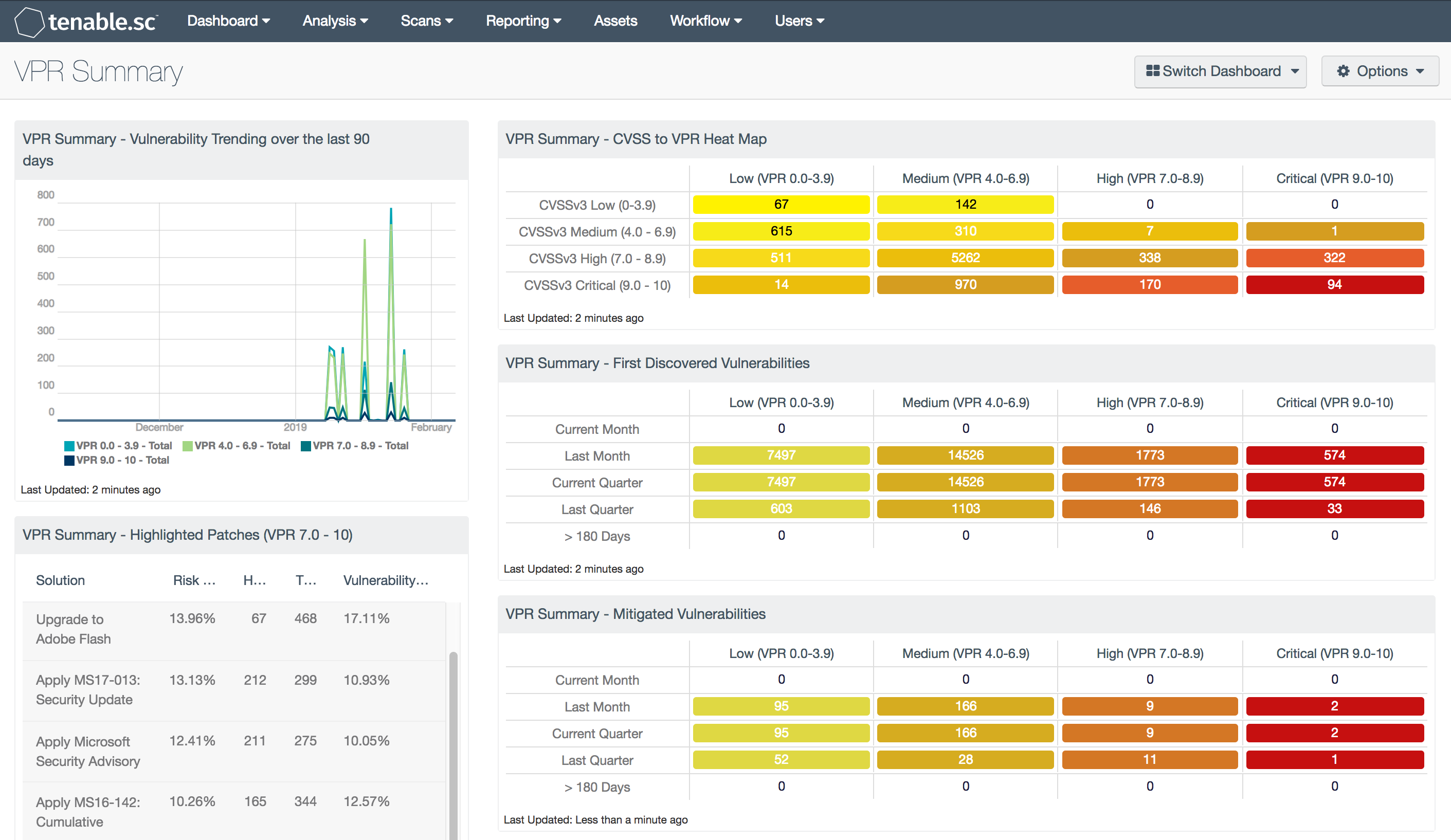
Vulnerability Priority Rating (VPR) Summary SC Dashboard Tenable®
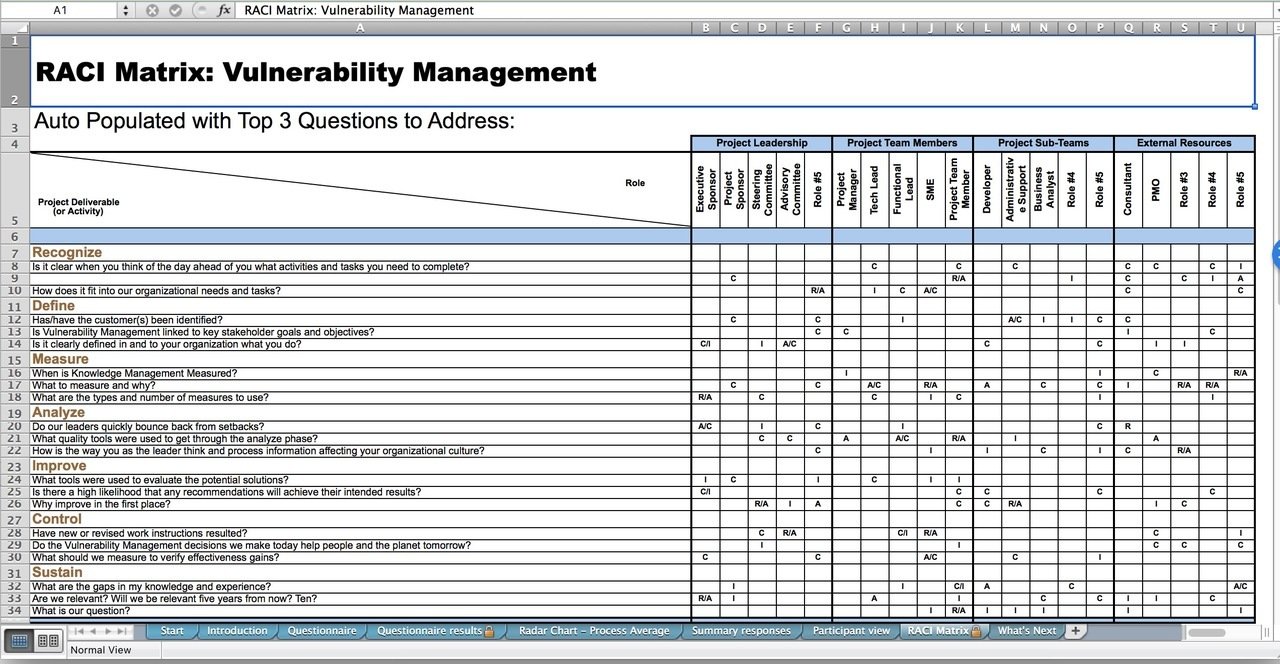
The Art of Service: Vulnerability Management Standard Requirements: From $249 For $99 TODAY

Vulnerability Management Certifications prntbl concejomunicipaldechinu gov co

The role of vulnerability assessment and the corresponding Download Scientific Diagram

New Microsoft threat vulnerability management APIs
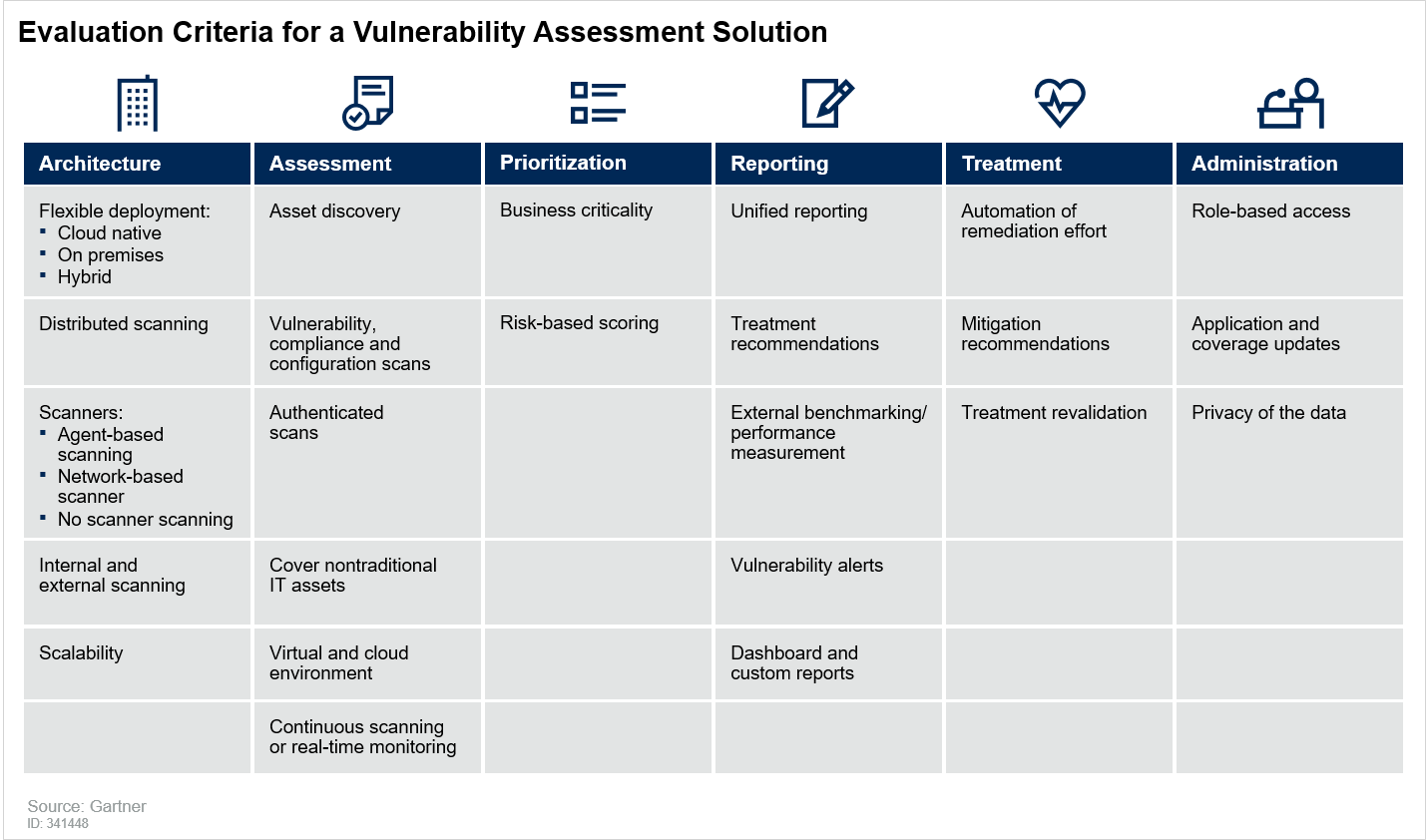
A Guide to Choosing a Vulnerability Assessment Solution by Gartner
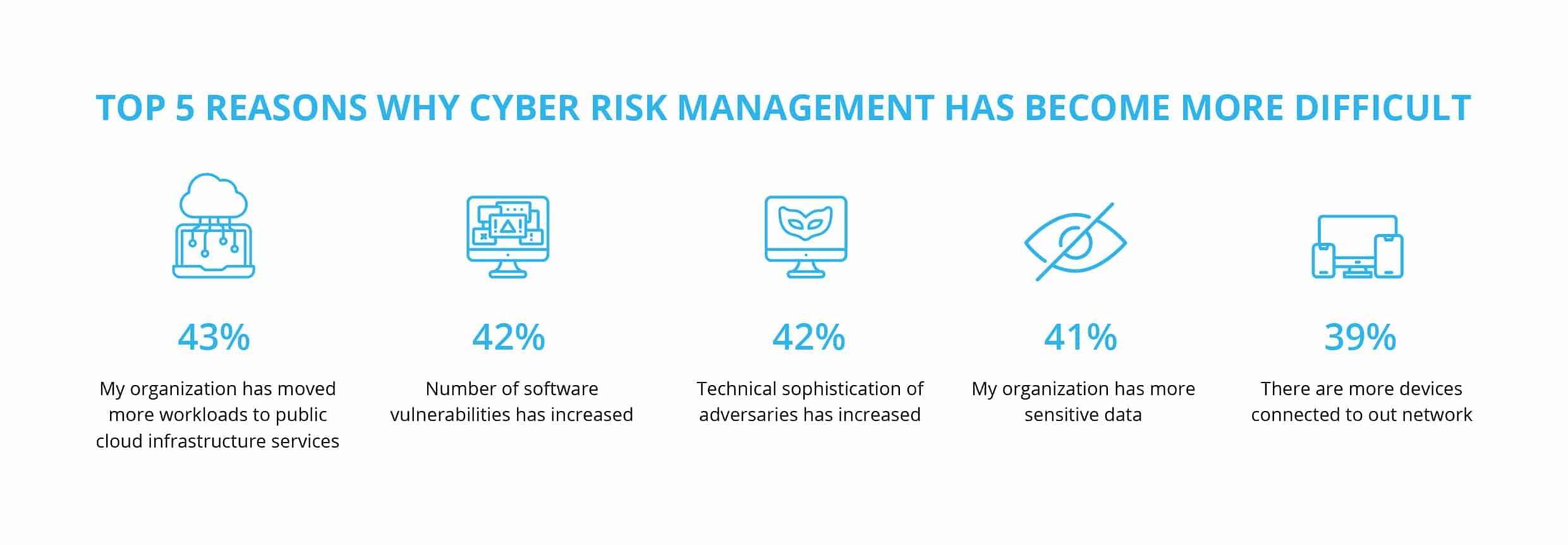
5 step Vulnerability Remediation Process Action1 RMM Blog
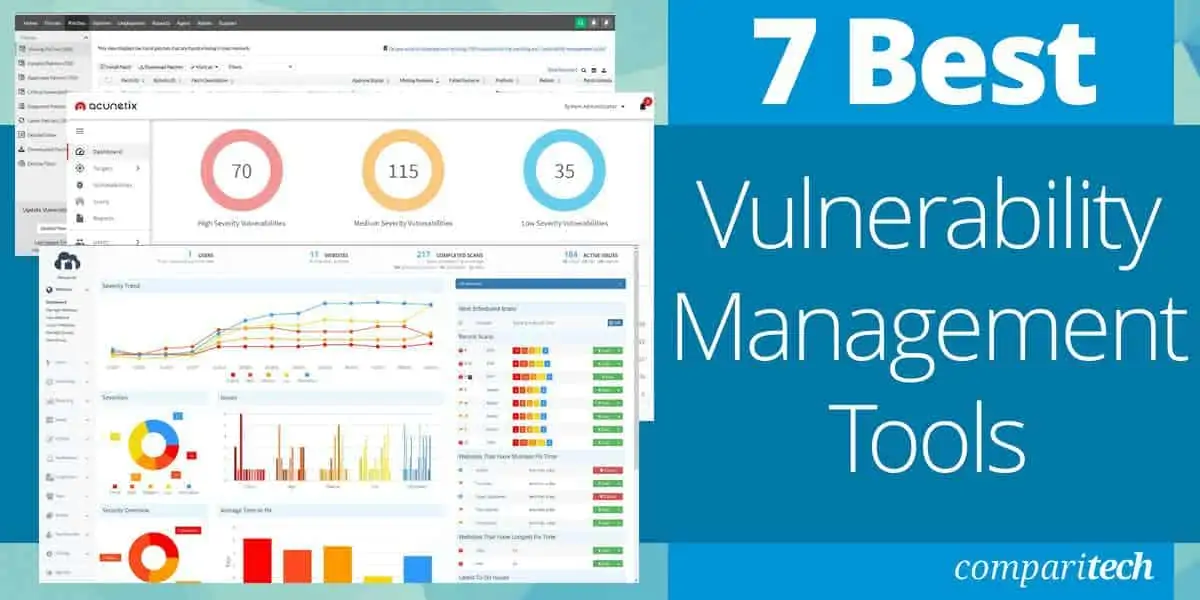
9 Best Vulnerability Management Tools in 2023 (Paid Free)

Threat Assessment Vulnerability Assessment Compliance Assessment
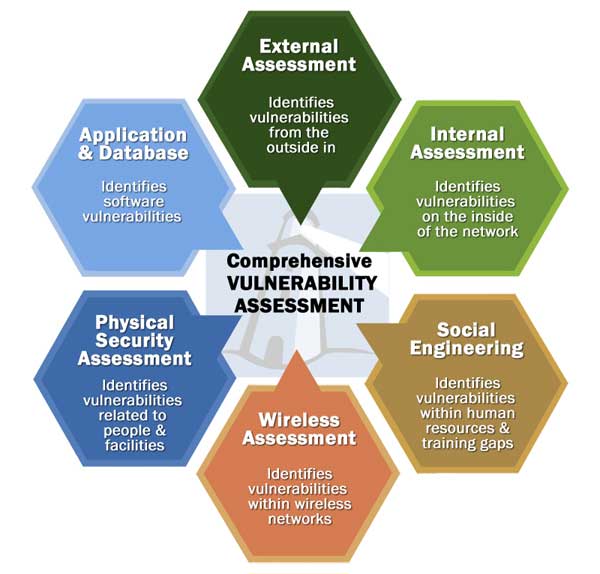
What is Vulnerability Assessment? ~ Network Security Consultant

What is Vulnerability Assessment CyberSecuriosity Professional Cyber Security Services

Vulnerability Assessment Report Template For Your Needs

Network Vulnerability Assessment and Management Guide