Vulnerability Management Policy Template Nist
Here are some of the images for Vulnerability Management Policy Template Nist that we found in our website database.
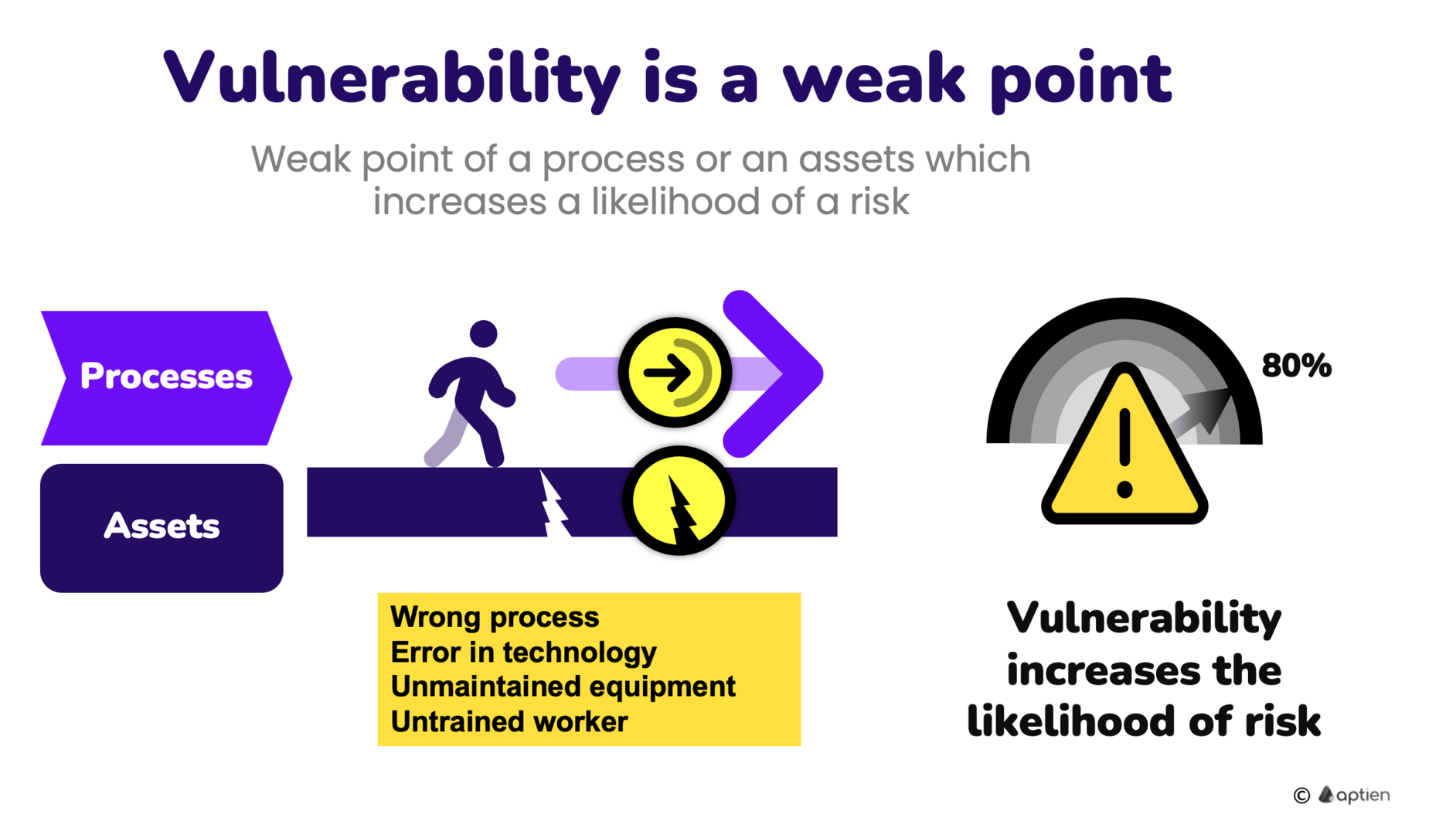
What is Vulnerability Risk and Continuity Management Glossary Aptien

Vulnerability Assessment Lanworks

Vulnerability Introducing A New Vulnerability Class: False File
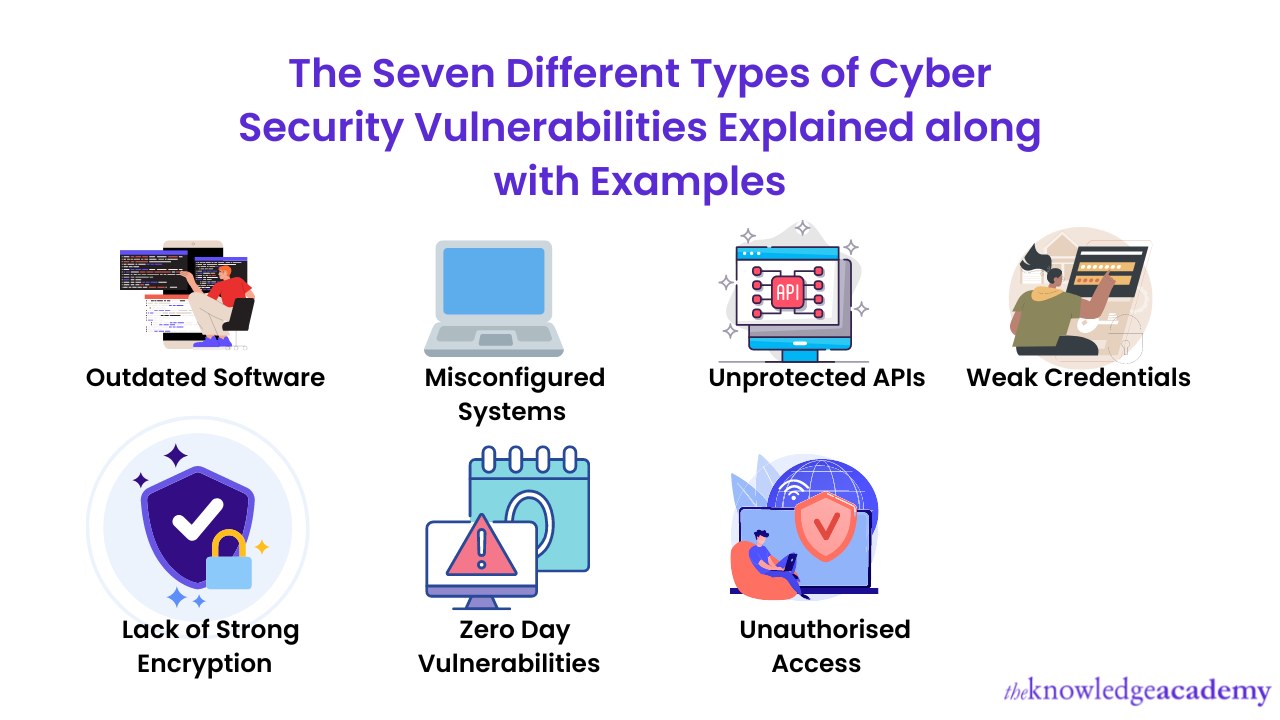
Vs Code Security Vulnerabilities at Daniel Shears blog
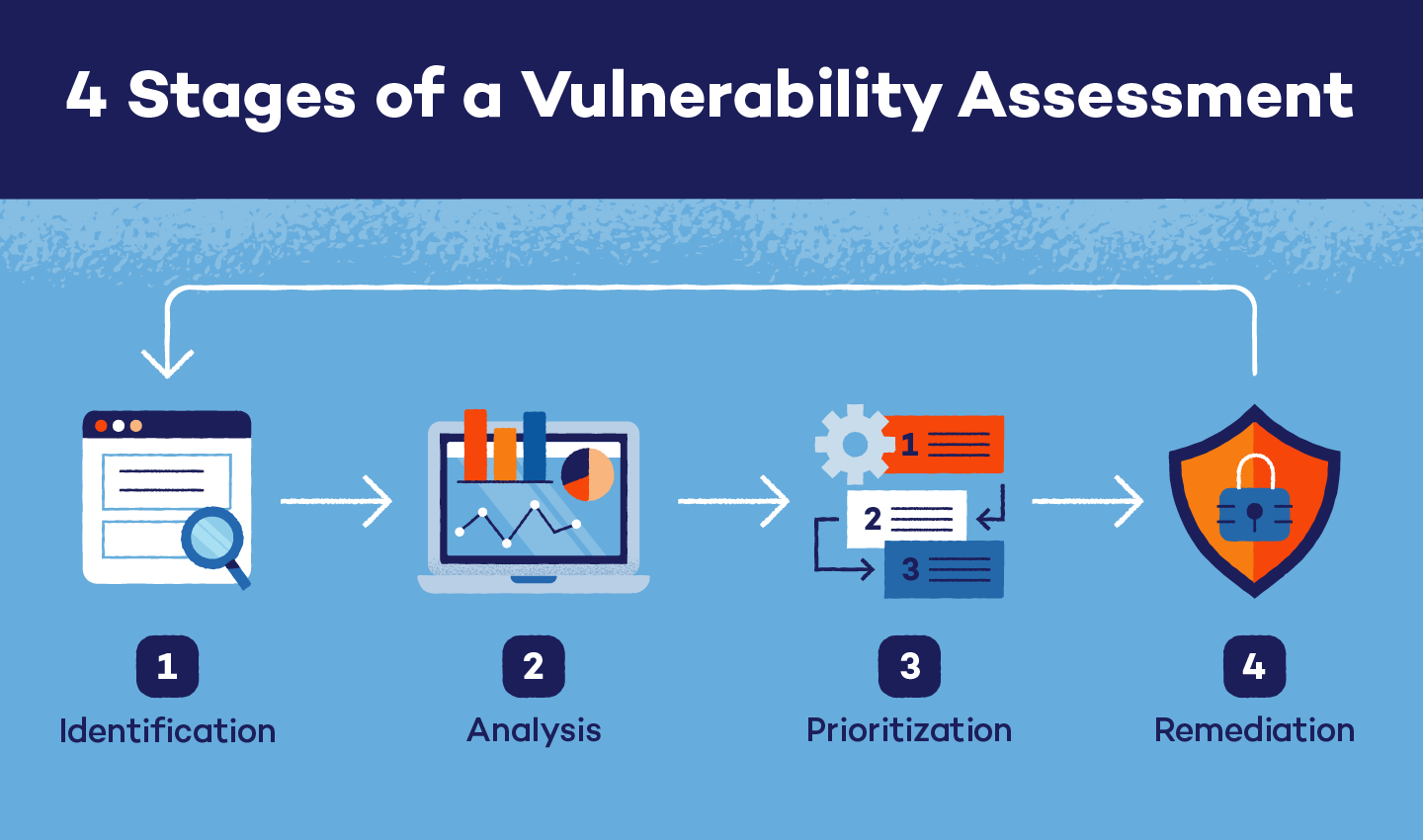
What is a Vulnerability Assessment? Panda Security
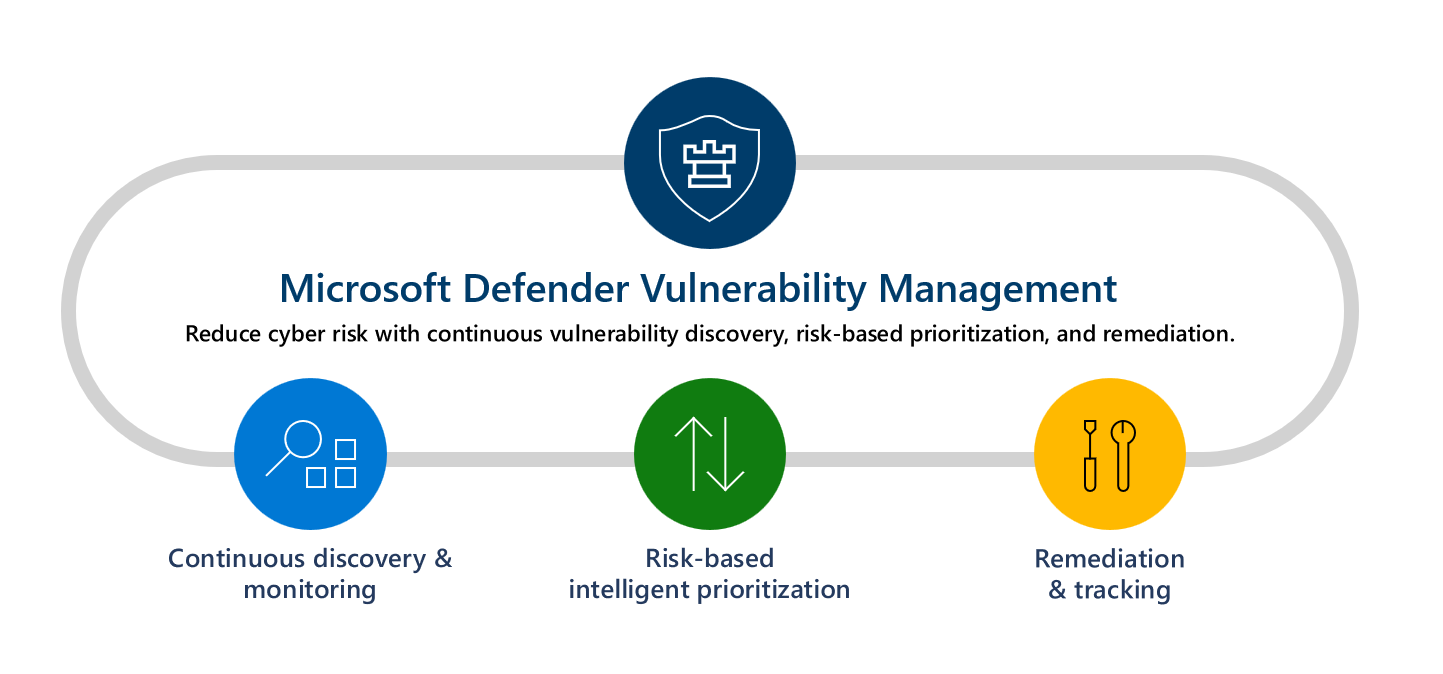
Microsoft Defender Vulnerability Management Microsoft Learn
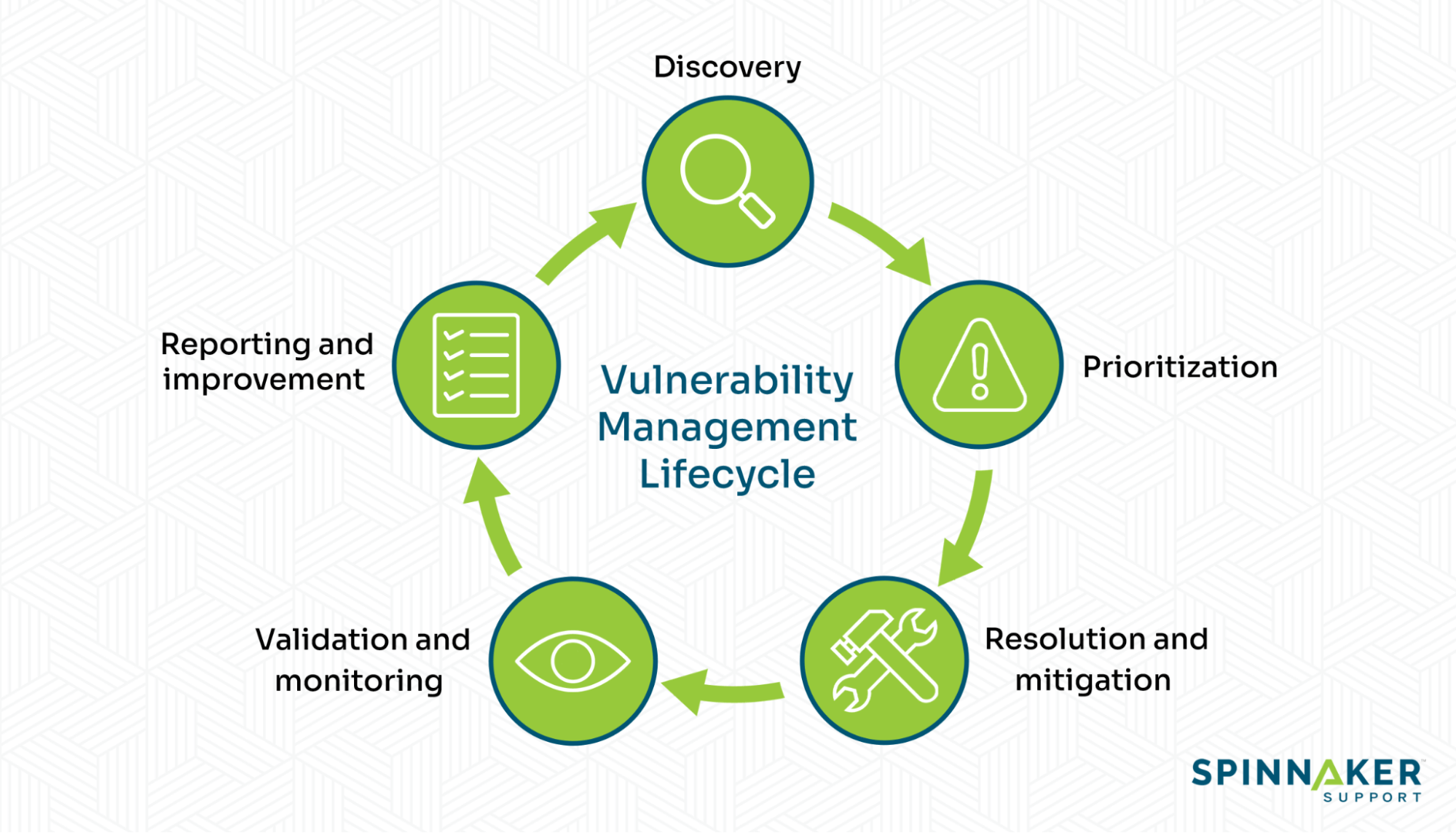
Strengthen Your Company s Cyber Security with Vulnerability Management

Vulnerability And Threat Management
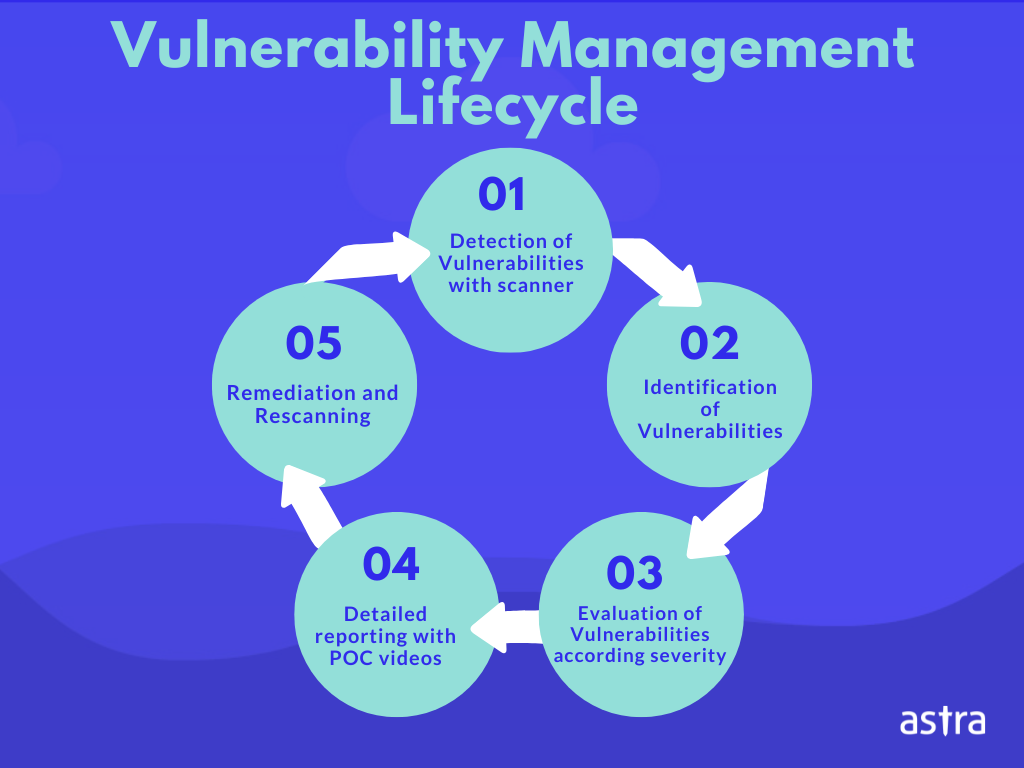
Vulnerability Management

The Importance of Vulnerability Remediation for System Security

Vulnerability Management Lifecycle
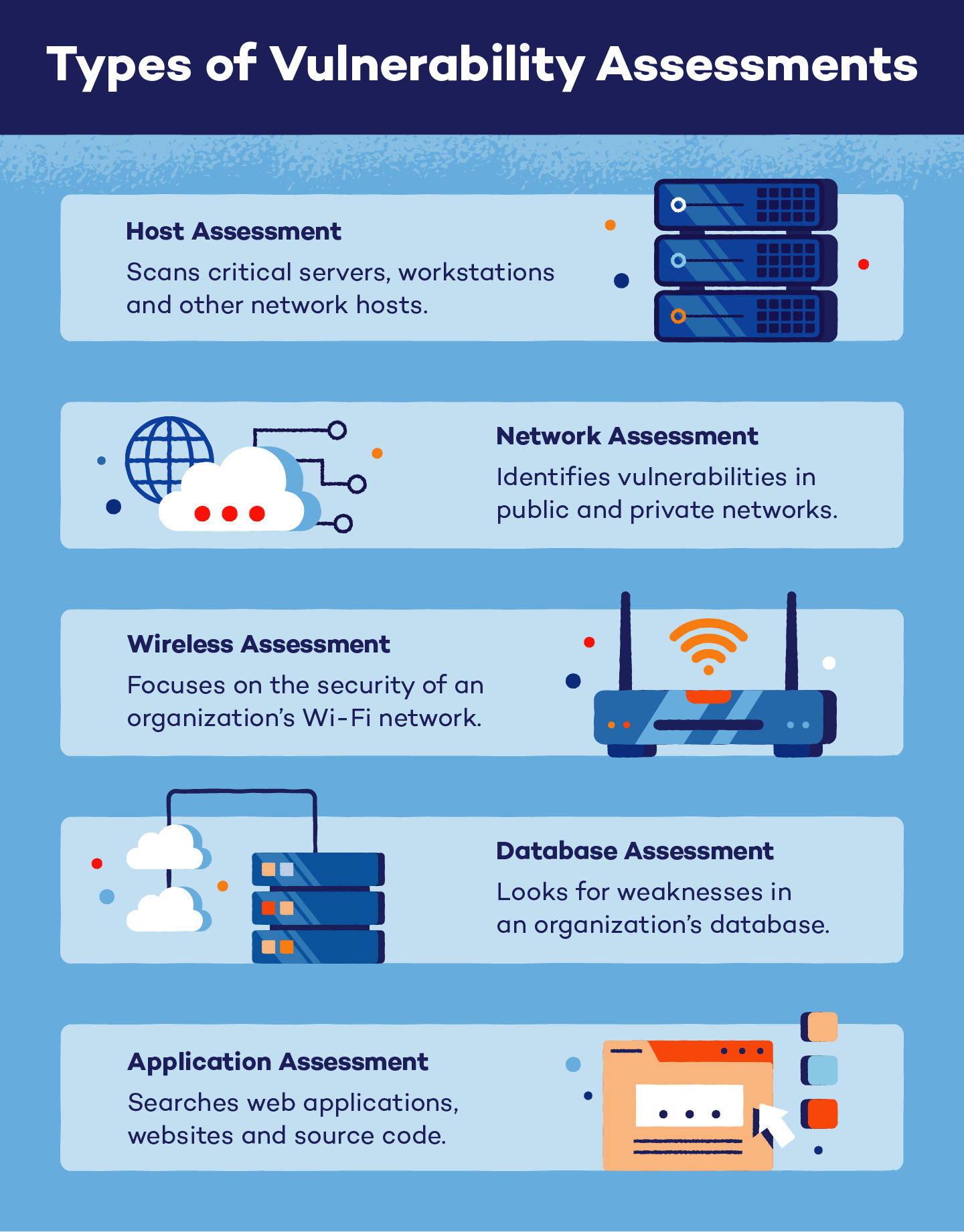
What is a Vulnerability Assessment? Panda Security
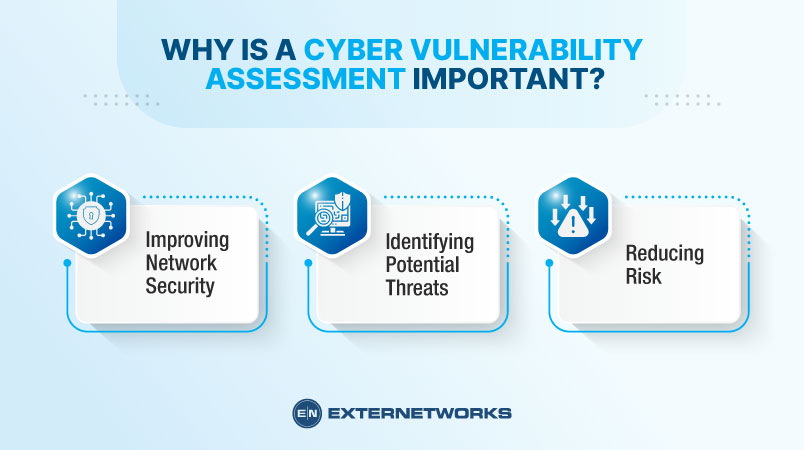
Vulnerability Assessment

Vulnerability Assessment: Types and Methodology Attaxion

Vulnerability Management: Processes and tools

Vulnerability Management Best Practices SOCRadar® Cyber Intelligence Inc

Vulnerability Scanner Vulnerability Scanning Tools
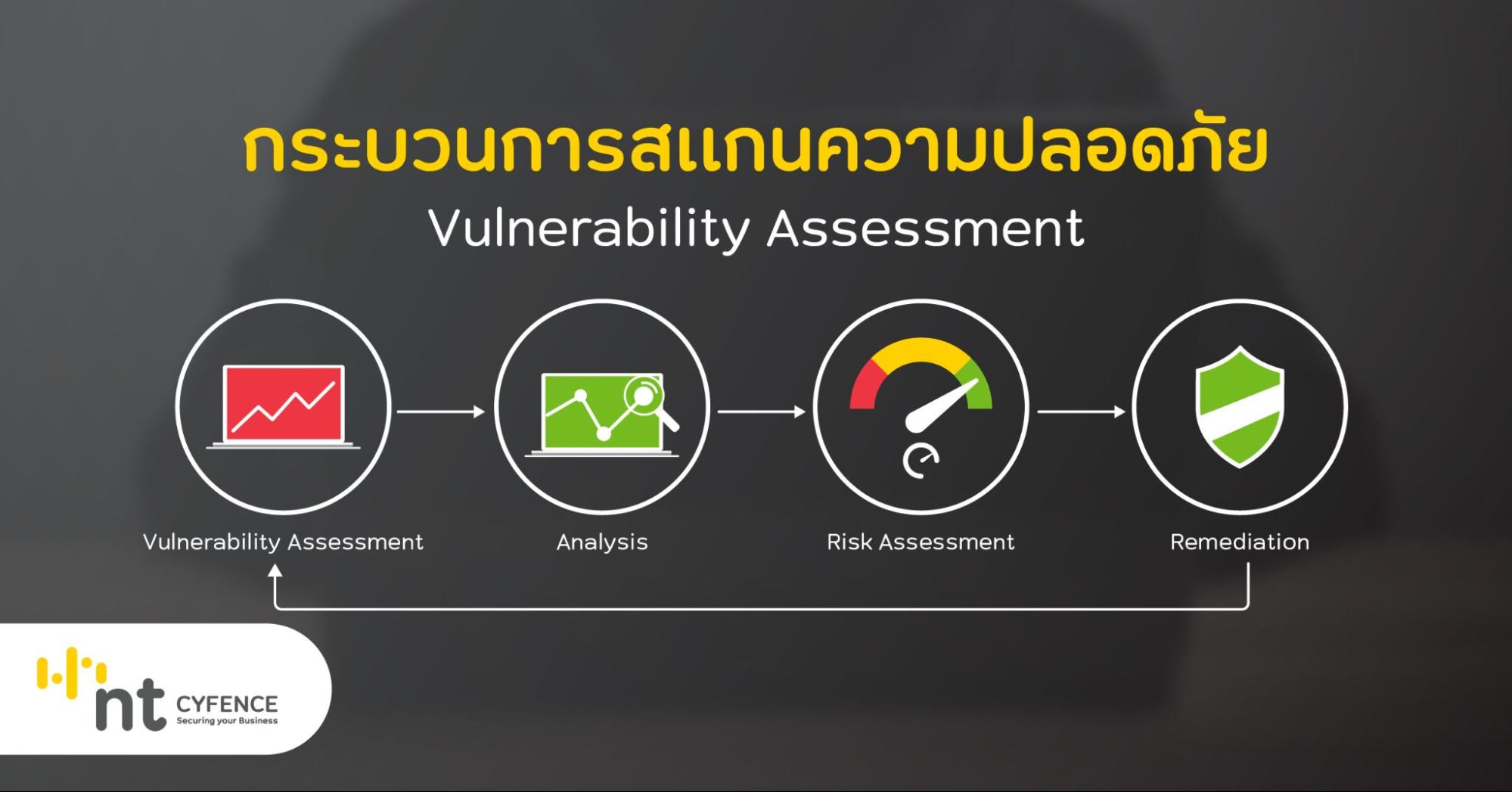
การทำ Vulnerability Assessment หรือ VA คืออะไร NT cyfence
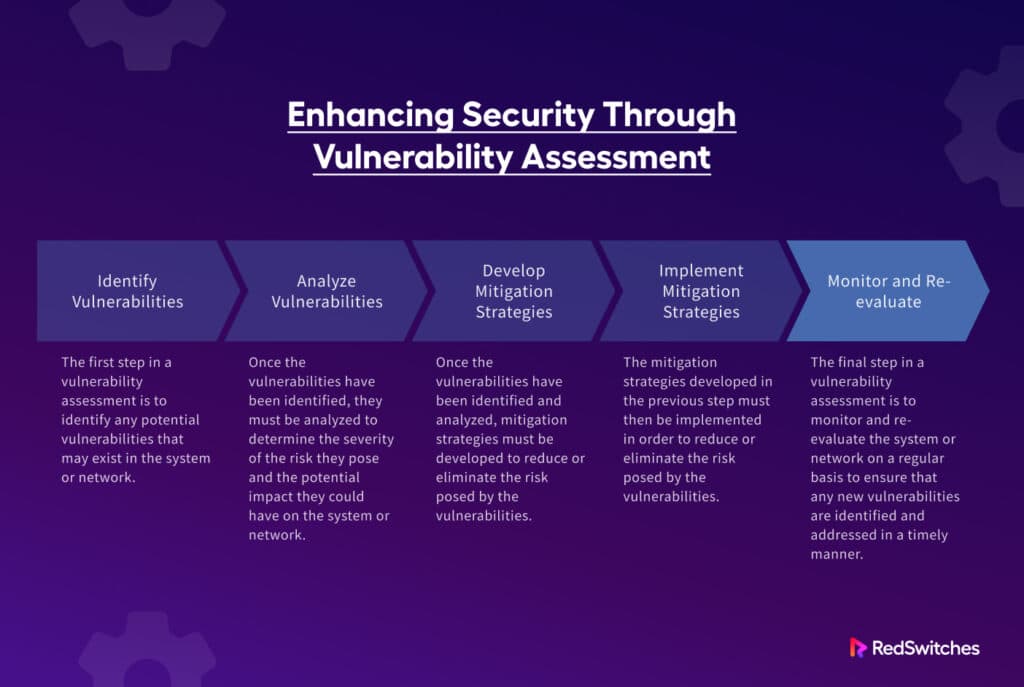
Comprehensive Vulnerability Assessment For ICT Assets
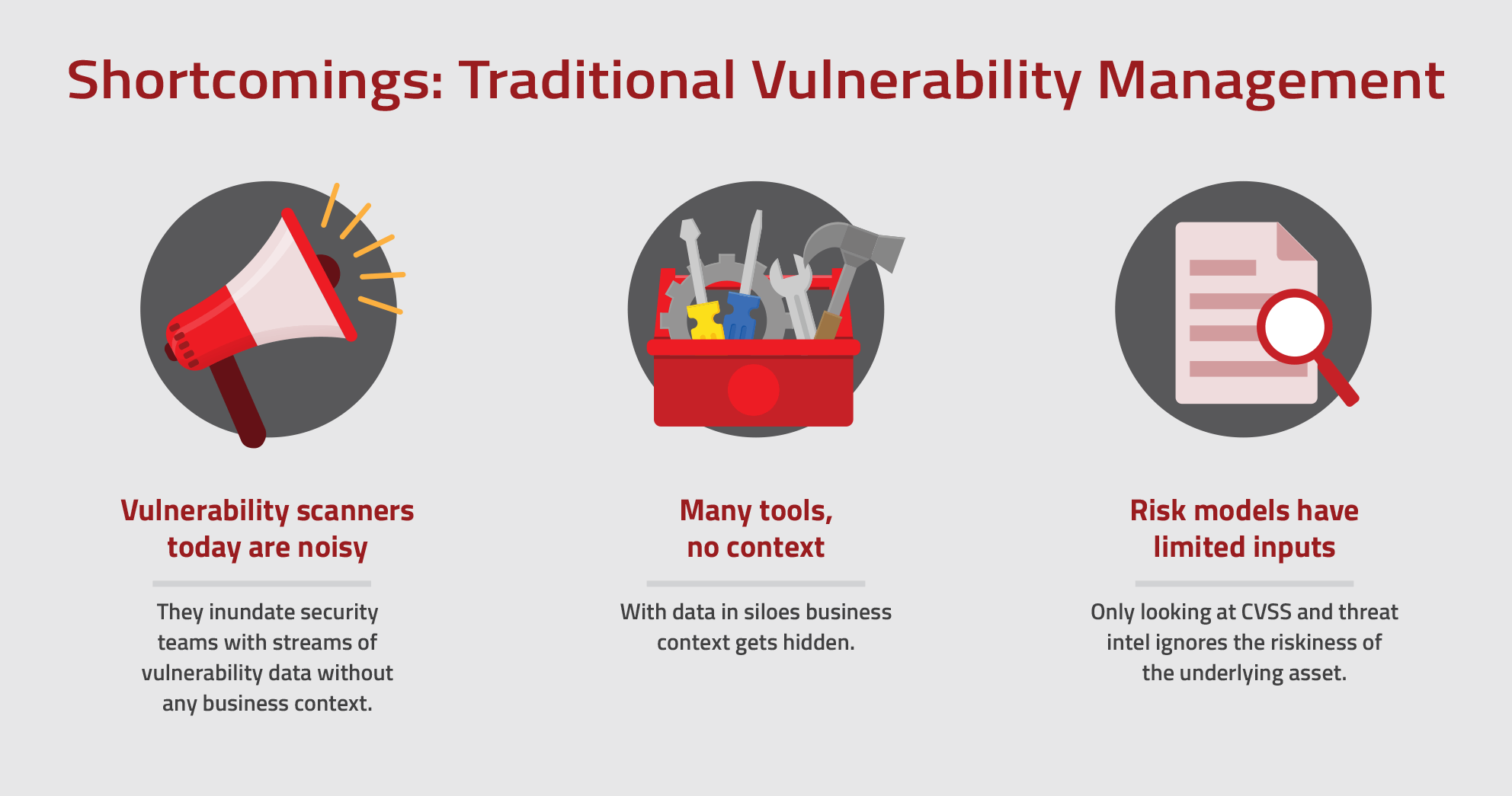
Leveraging CRQ to drive risk based vulnerability management Balbix

Network Vulnerability Assessments: A Complete Guide

Vulnerability Assessment
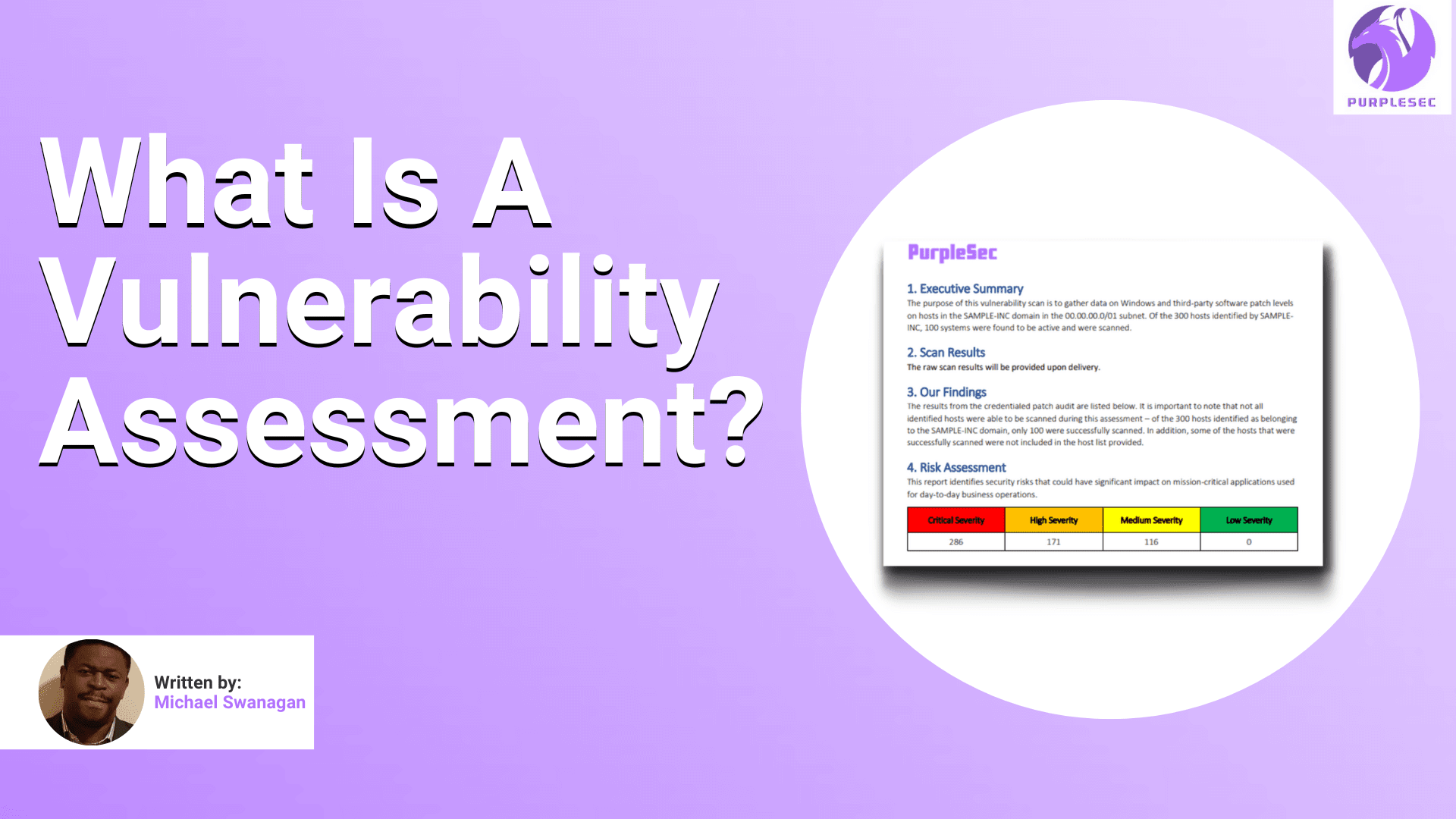
Vulnerability Assessment

Vulnerability Scanning Definition In Network Security at Karima Parker blog

What are the Main Elements of a Cyber Vulnerability Management Process

Vulnerability Prioritization: An Effective Security Approach

Automated Vulnerability Scanning Tools: Security Solutions

What Is Vulnerability Remediation? Process Automation
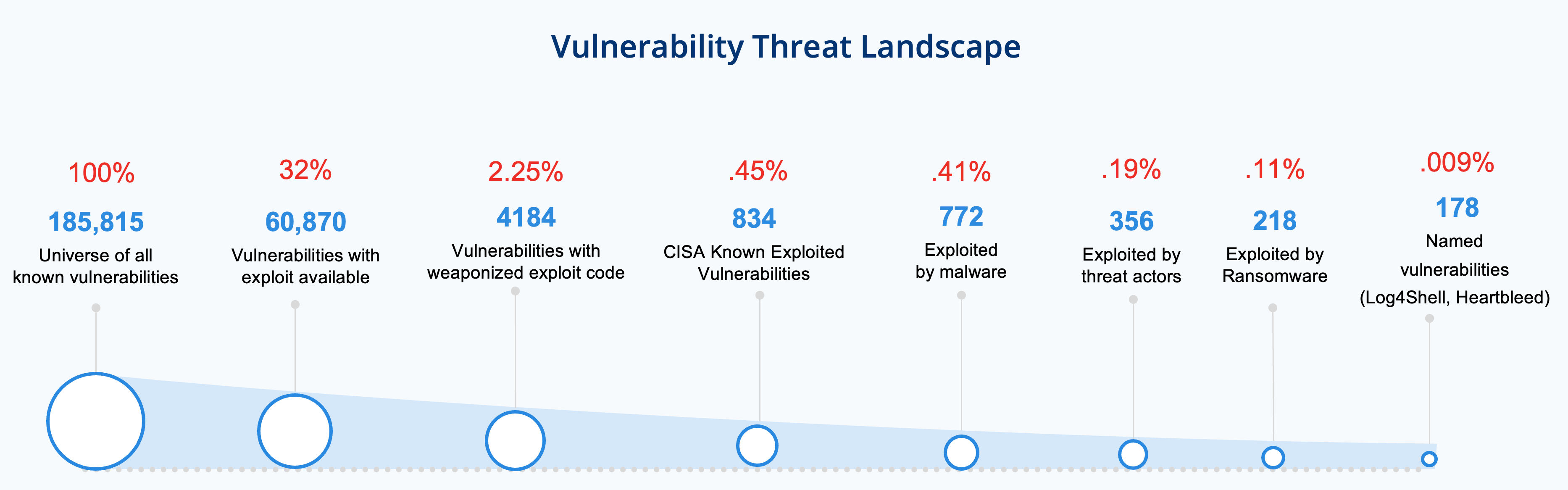
In Depth Look Into Data Driven Science Behind Qualys TruRisk Qualys
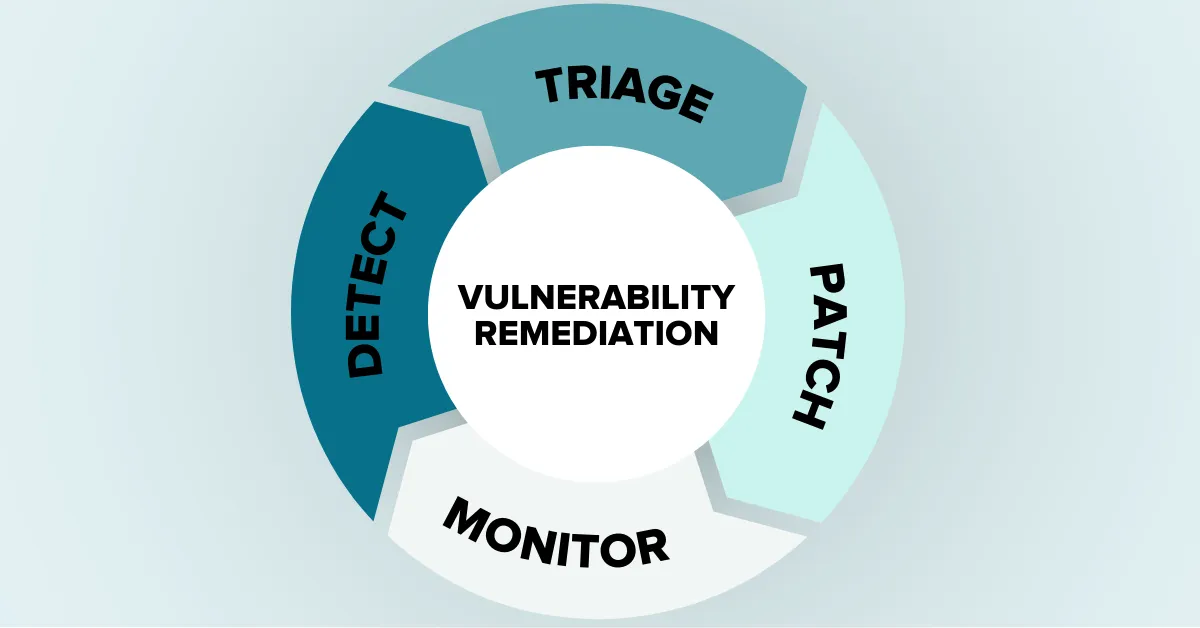
Vulnerability Remediation: How It Works Best Practices

Analysis of Consumer IoT Device Vulnerability Quantification Frameworks
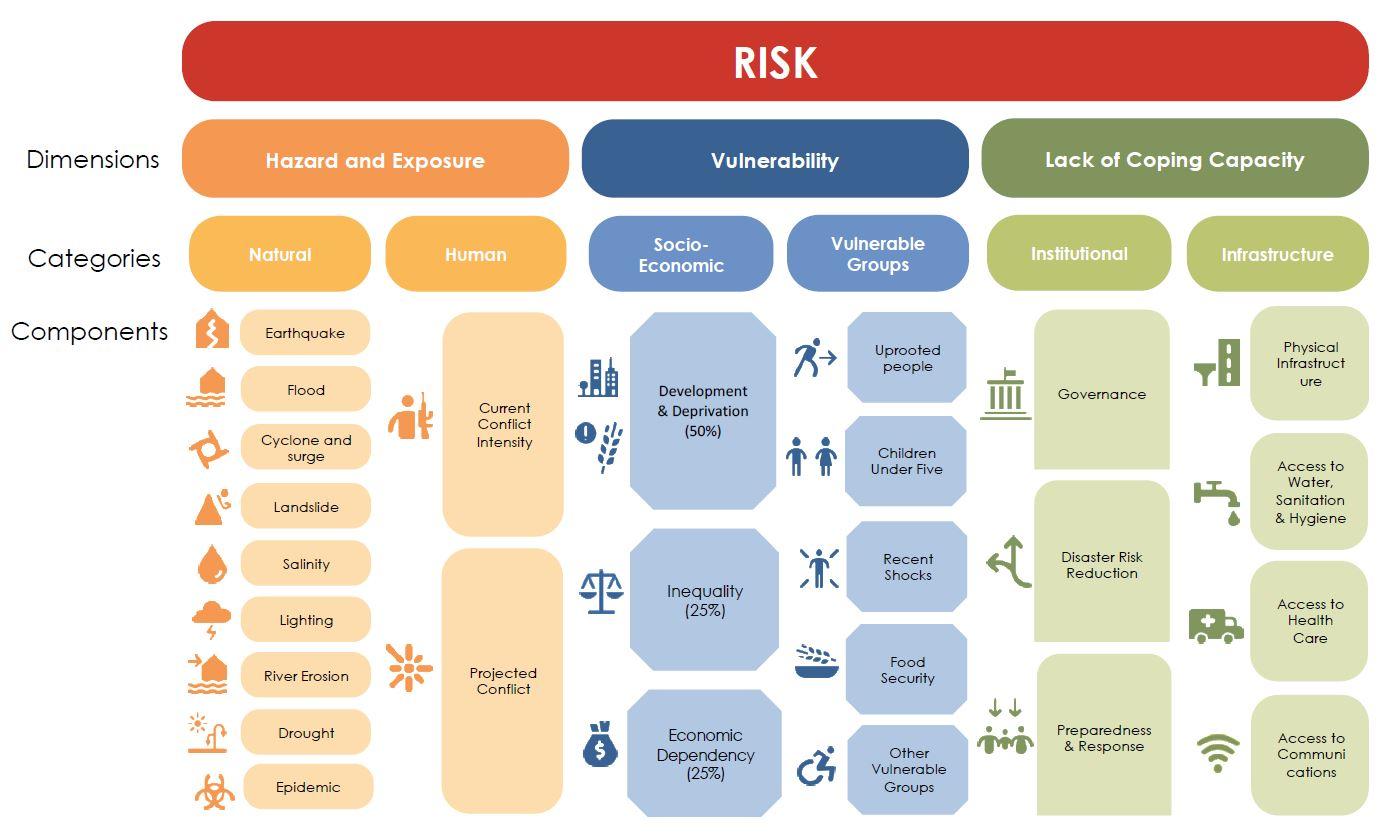
Vulnerability Disaster

File Upload Vulnerability
:max_bytes(150000):strip_icc()/fear-of-vulnerability-2671820-Final-e6ee1795fd364dafa943934bc3b021cc.png)
How To Make Anxious Avoidant Relationship Work: 16 Practical Tips

Vulnerability Worksheets

Vulnerability Management Dashboard Visualinfinnity

Vulnerability Management
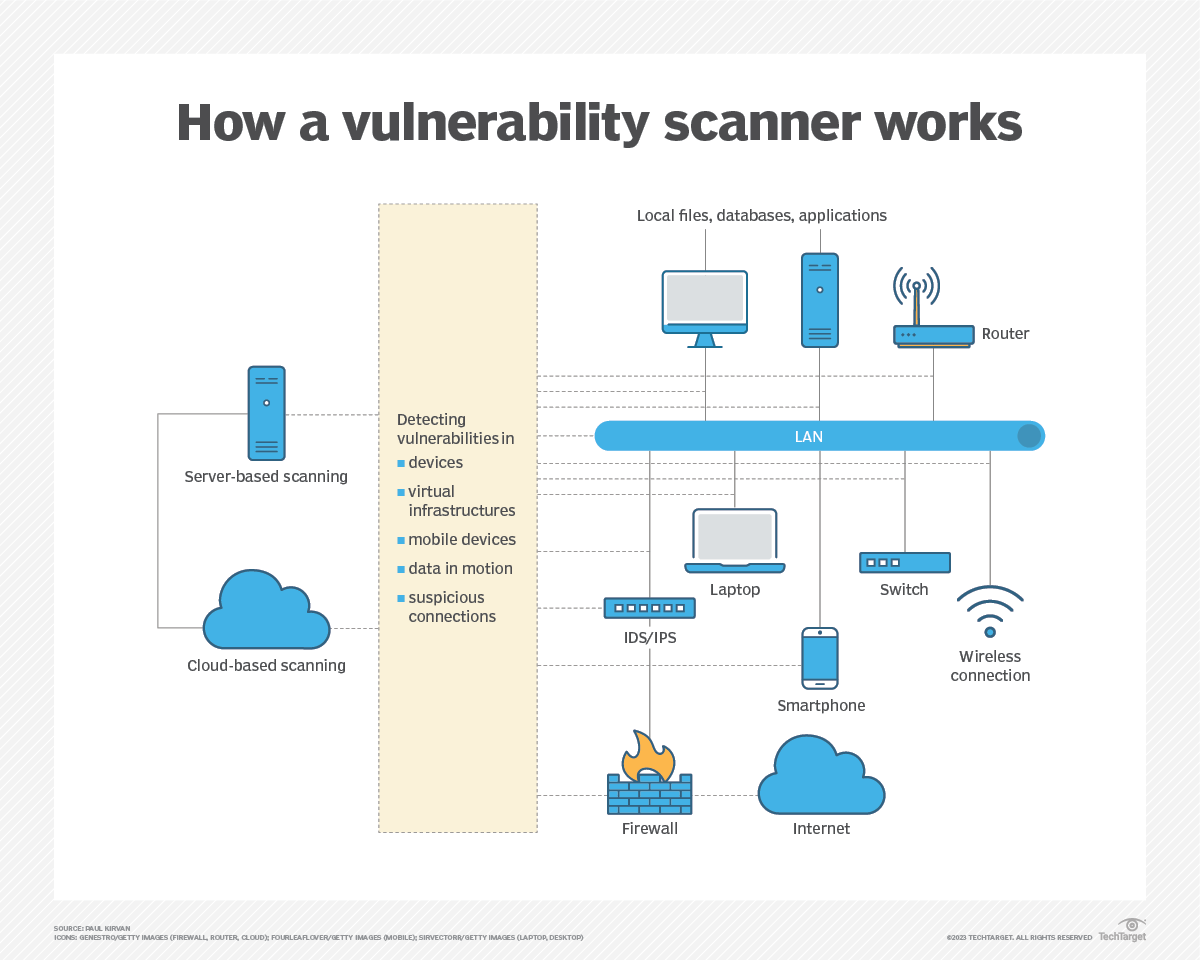
Types of vulnerability scanning and when to use each TechTarget

Vulnerability Scanning

Vulnerability Management Process Flow Powerpoint Ppt Template Bundles

What Is Vulnerability Management? Process Assessment Best Practices

Vulnerability Scanning
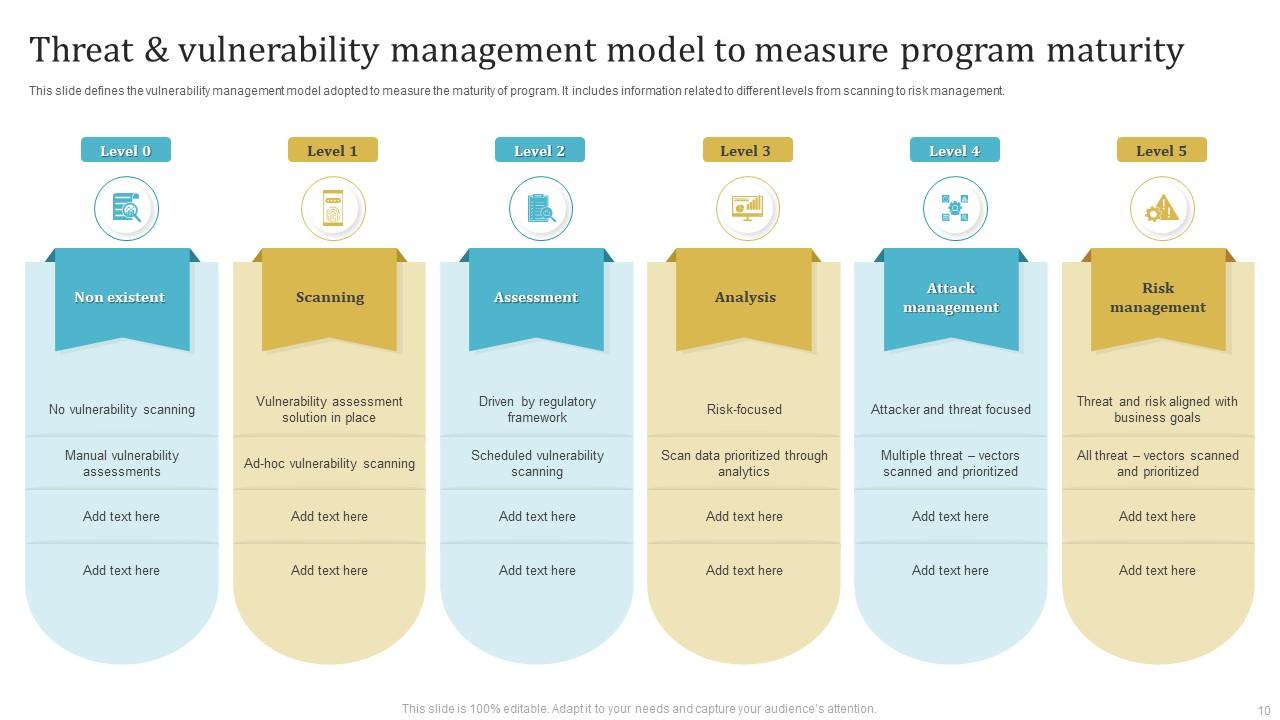
Vulnerability Management Program Powerpoint Ppt Template Bundles PPT Sample

Vulnerability Management: Processes and tools

Vulnerability Scanning: What is it and how does it work?
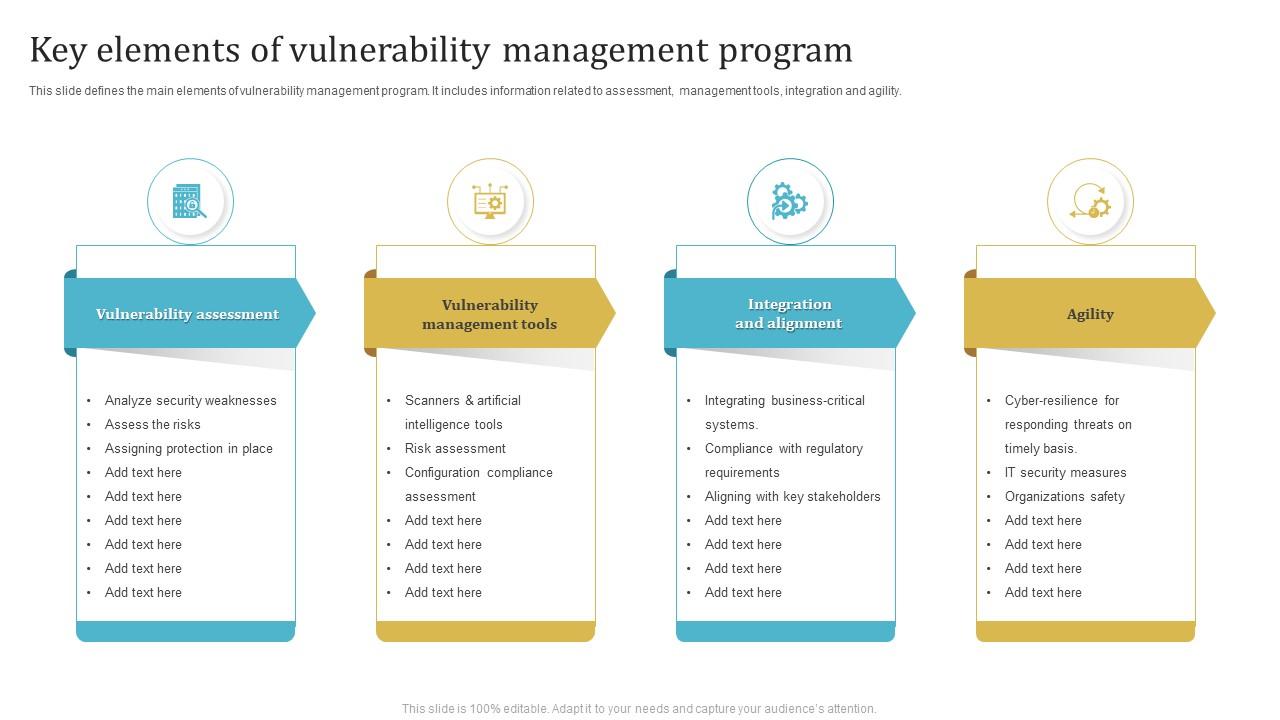
Key Elements Of Vulnerability Management Program PPT PowerPoint

Top 10 Vulnerability Scanning Tools

Vulnerability AssessmentTesting CSLBD
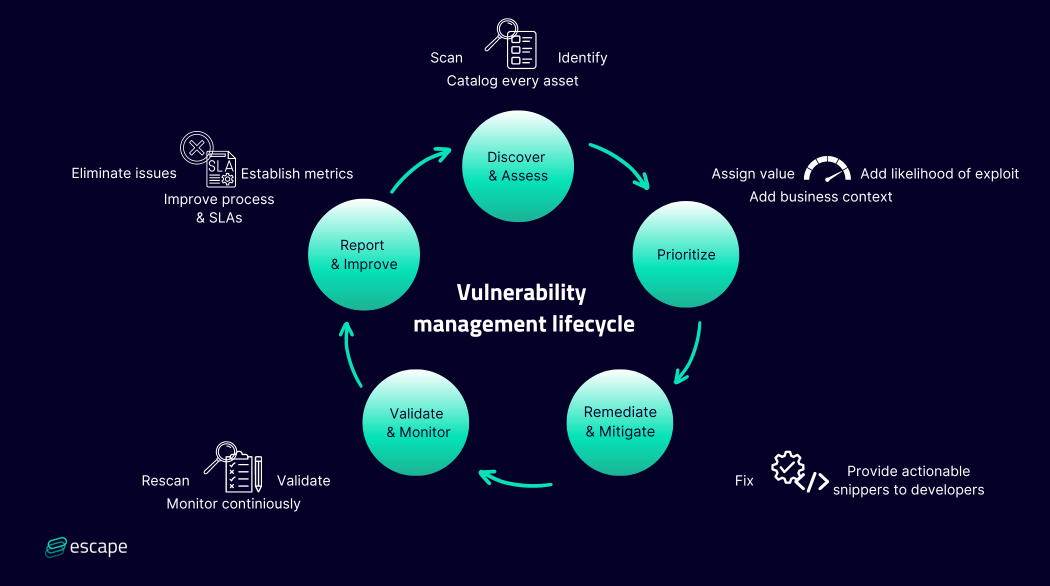
Vulnerability Management Lifecycle: A Comprehensive Guide

The reality of vulnerable leadership Duke Corporate Education

Difference Between Cybersecurity Risk and Vulnerability Cyber

Vulnerability Coding Colored Icon In Powerpoint Pptx Png And Editable

What is Vulnerability Management? Securing Your Digital Assets
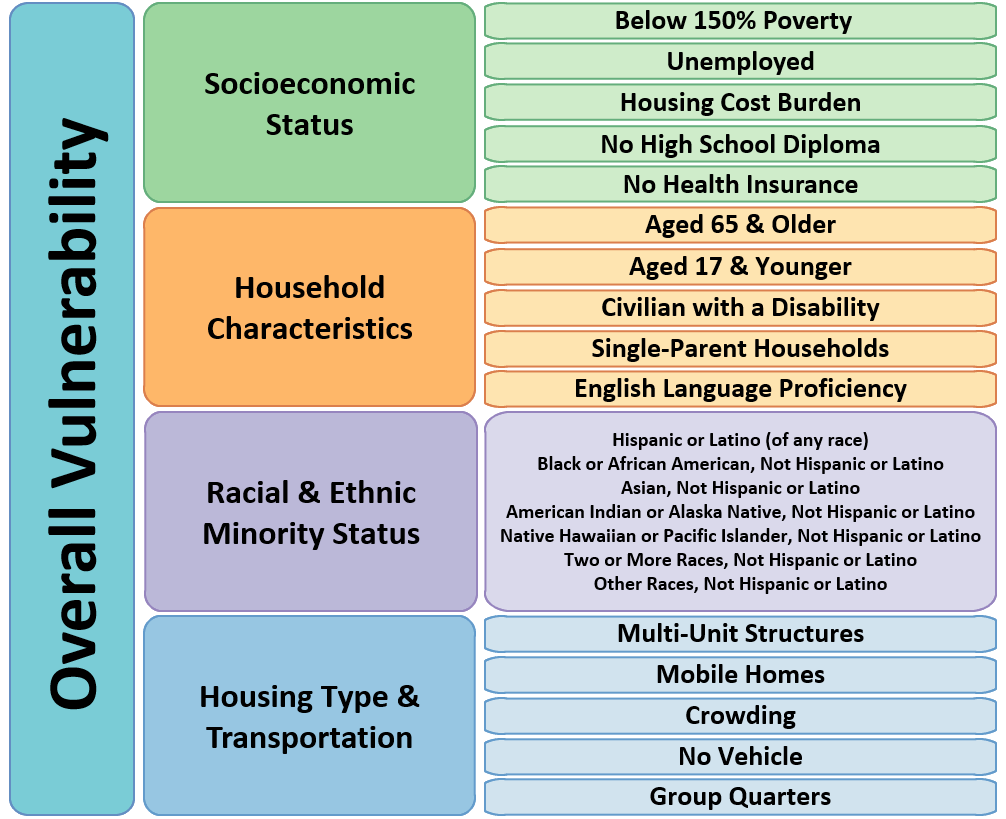
ArcGIS

ISO 14644 : Requirements for Cleanrooms

Gcp Vulnerability Scanner at Heriberto Barry blog

Shortening Your IoT Vulnerability Window Viakoo Inc
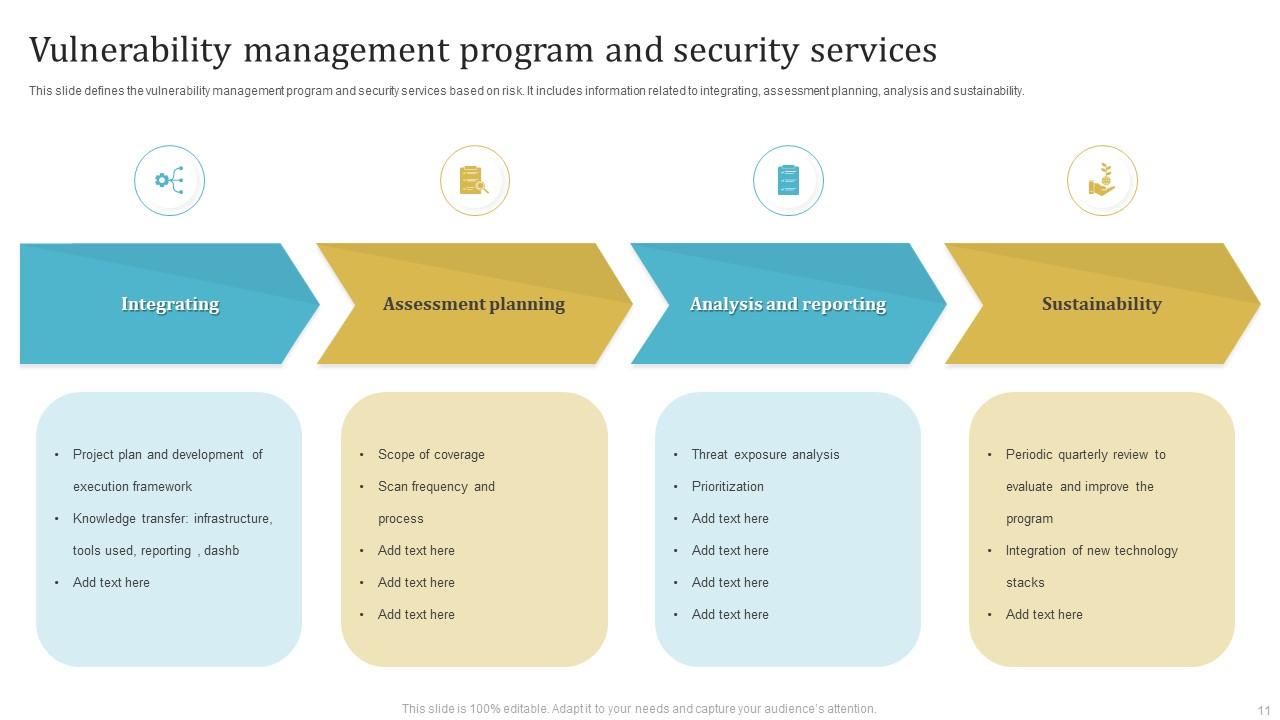
Vulnerability Management Program Powerpoint Ppt Template Bundles PPT Sample
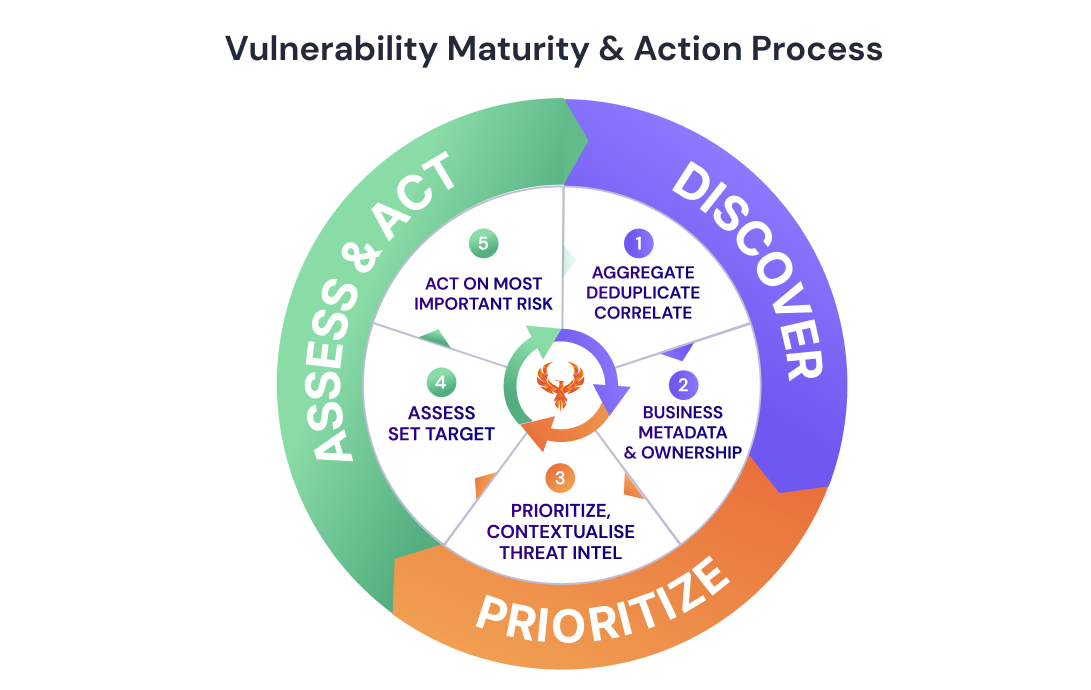
Vulnerability Managment Framework Application Security Code to Cloud
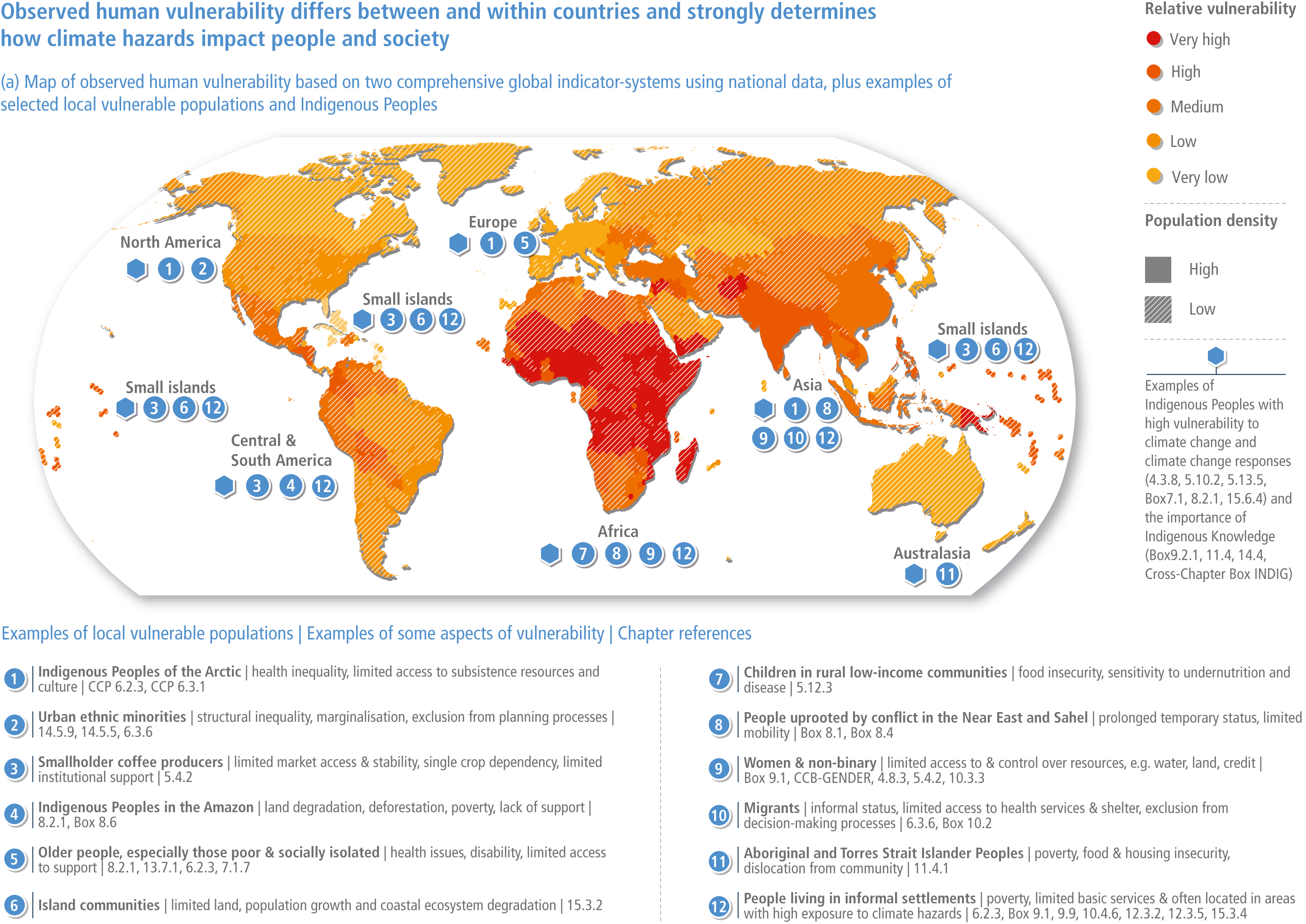
Technical Summary Climate Change 2022: Impacts Adaptation and