Vulnerability Report Template
Here are some of the images for Vulnerability Report Template that we found in our website database.
Vulnerability assessment Report Template Lovely Vulnerability Report

Vulnerability Report Template Content Calendar Template
Vulnerability Assessment Report Template Fill Out Sign Online and

28 Vulnerability Report Template Vulnerability in Threat

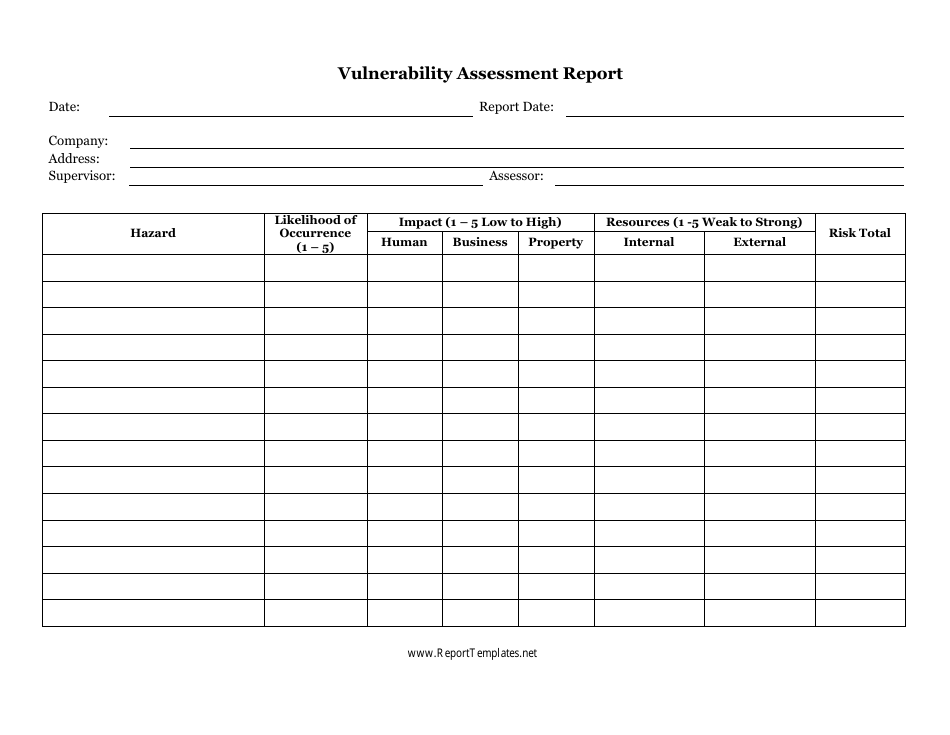
Vulnerability Assessment Report Template

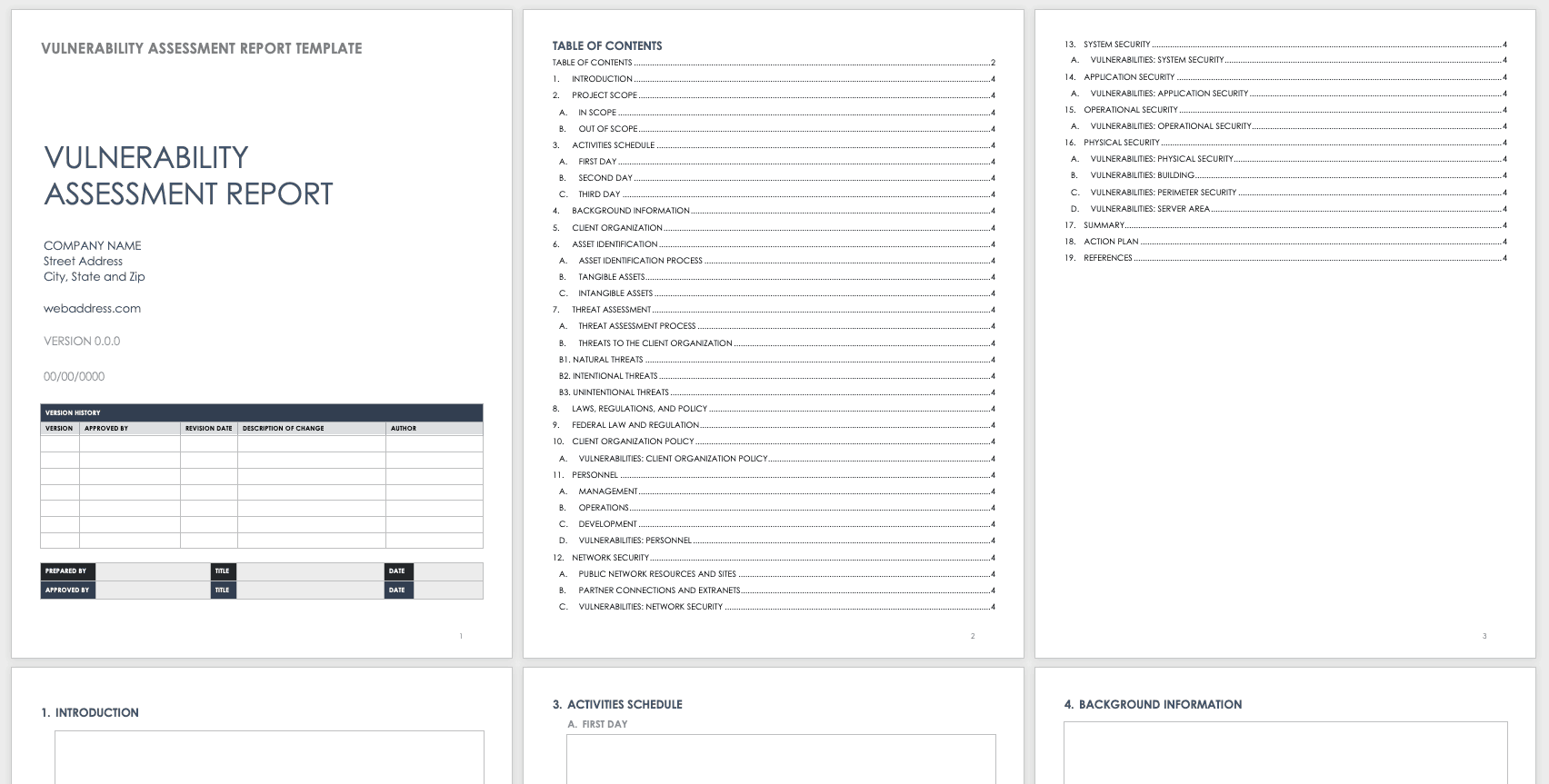
Vulnerability Report Template
Vulnerability Report Template

Vulnerability Report Template
Vulnerability Report Template
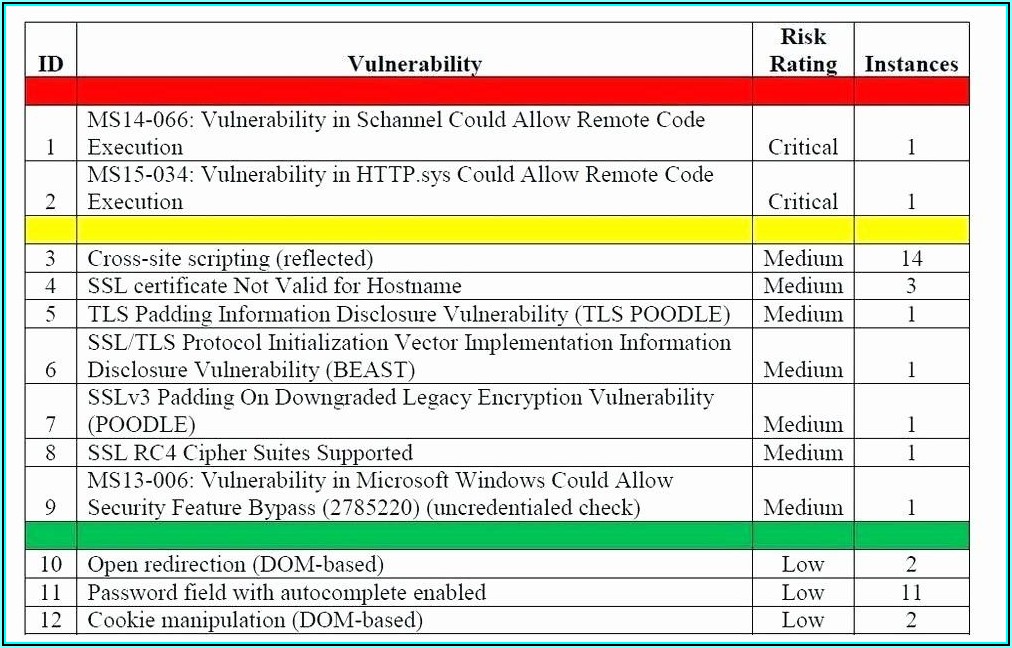
Vulnerability Report Template

Vulnerability Report Template Report template Templates Vulnerability

Vulnerability Report Template

Vulnerability Report Template
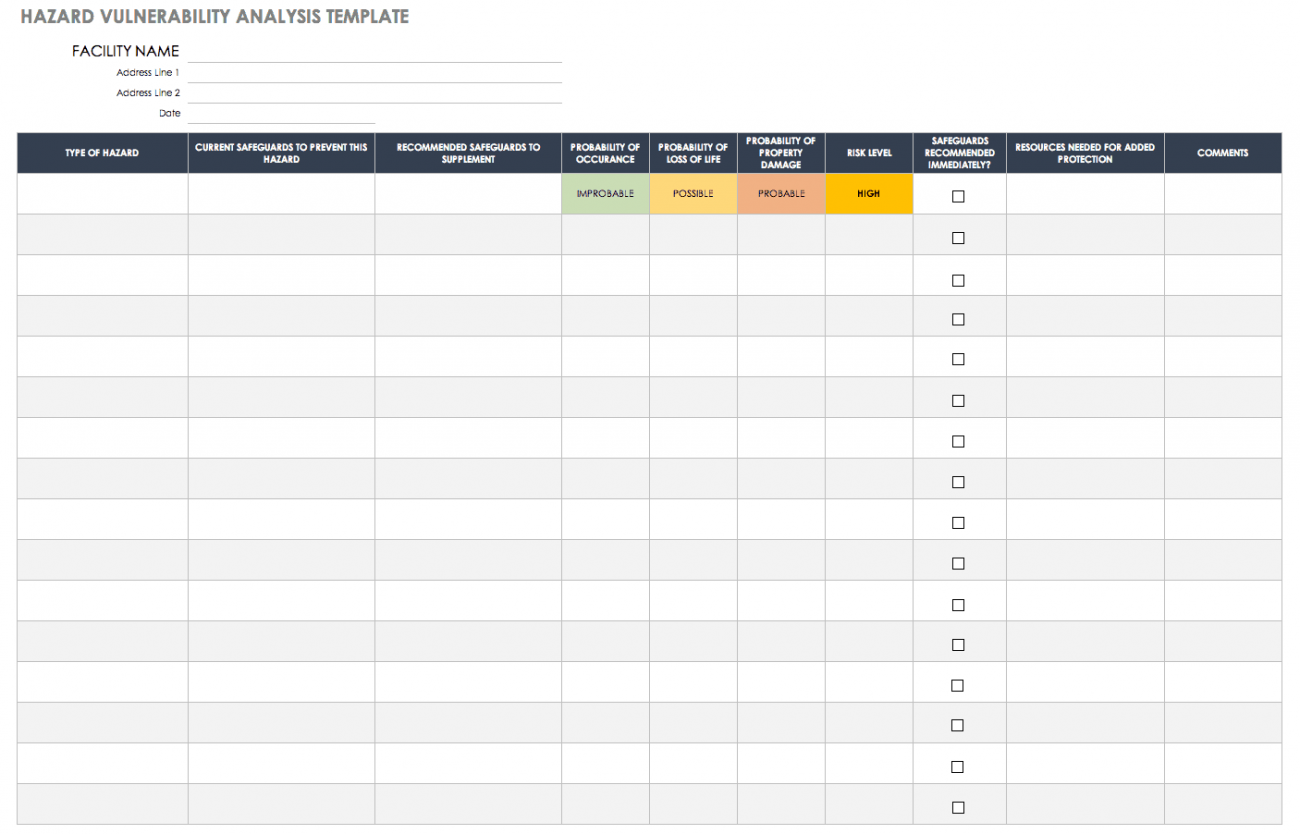
Vulnerability Report Template

Vulnerability Management Report Template
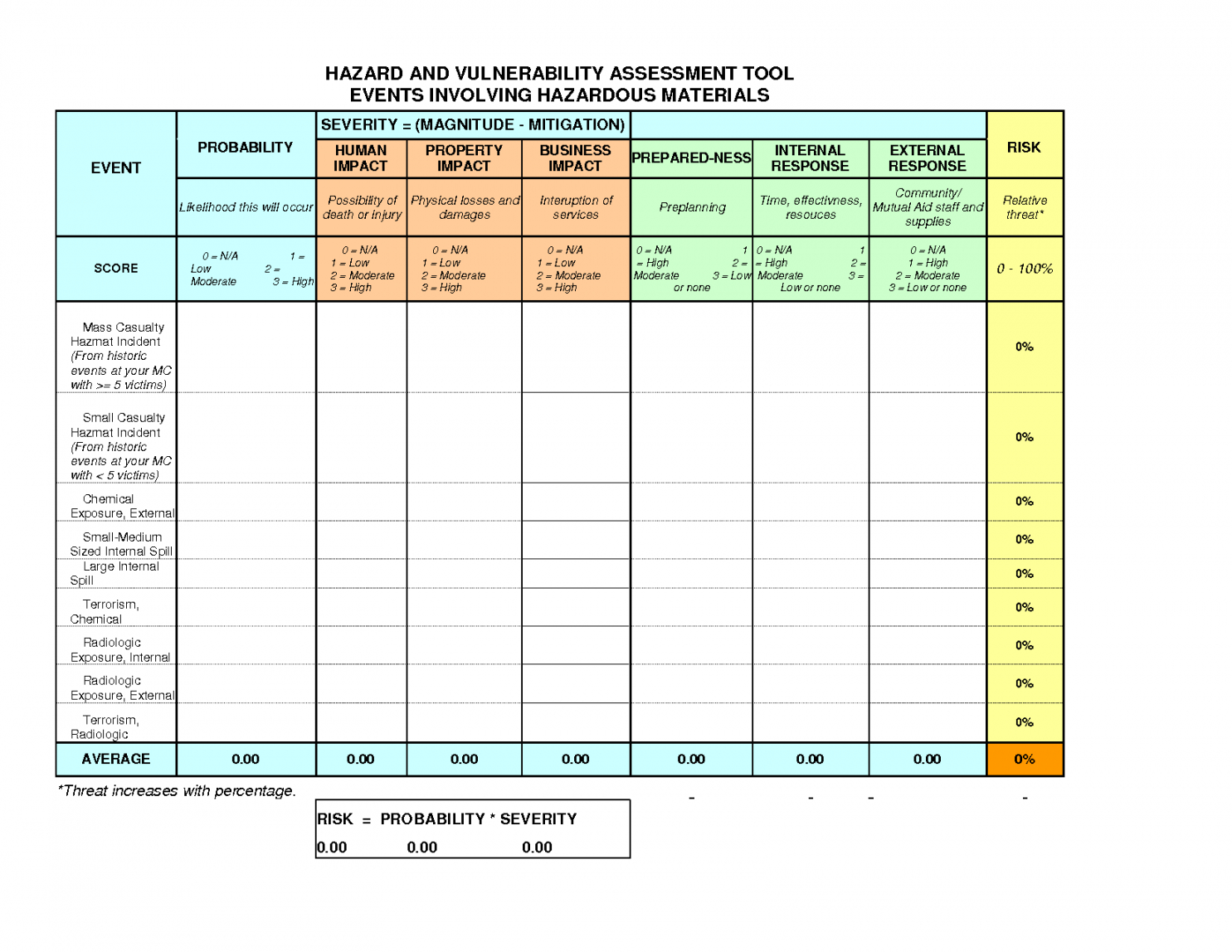
Vulnerability Management Report Template

Vulnerability Management Report Template

Vulnerability Management Report Template

Vulnerability Report Template Excel

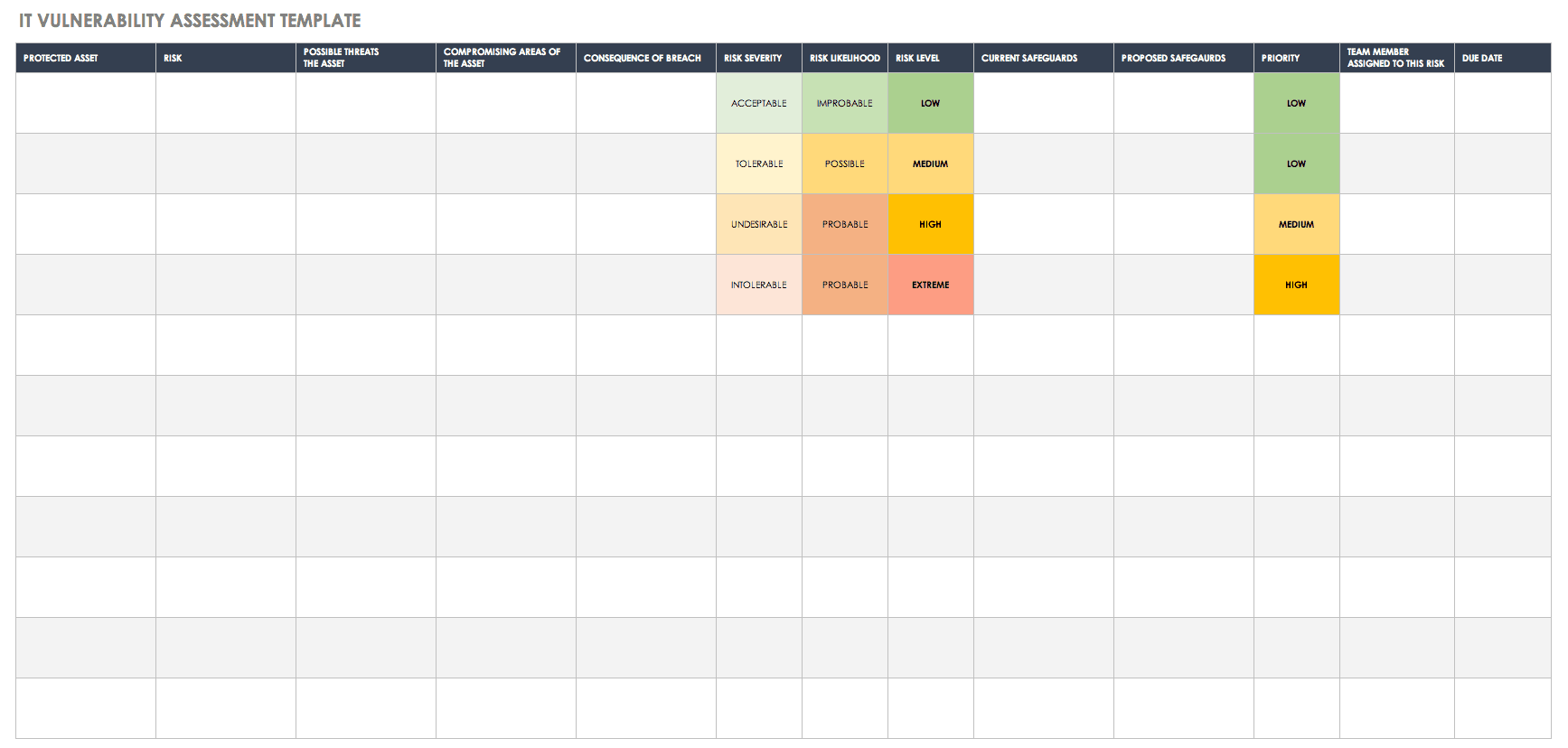
IT Security Vulnerability Assessment Template in Word PDF Google Docs

Vulnerability Scan Report Template
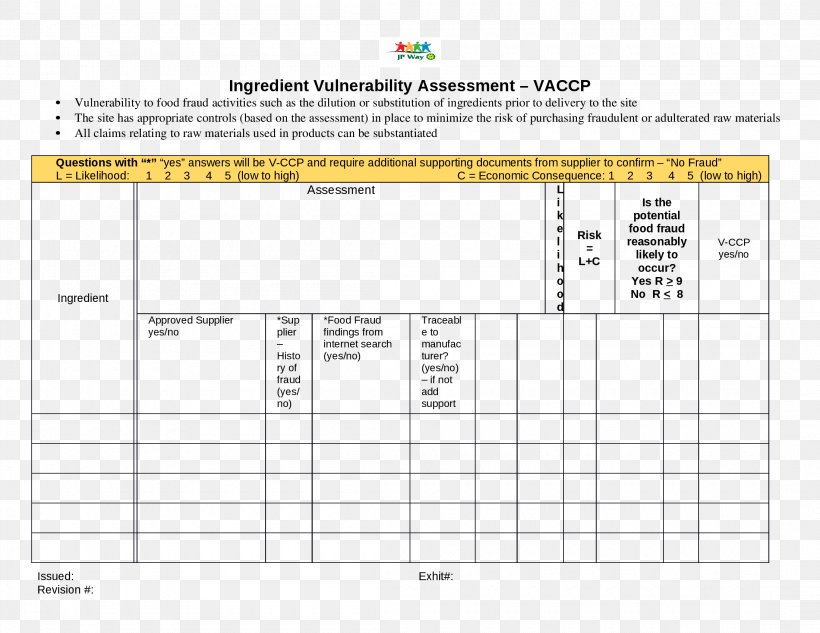
Vulnerability Report Template Doc

Physical Security Vulnerability Assessment Template

Vulnerability Management Plan Template

Vulnerability Tracking Spreadsheet pertaining to Network Vulnerability
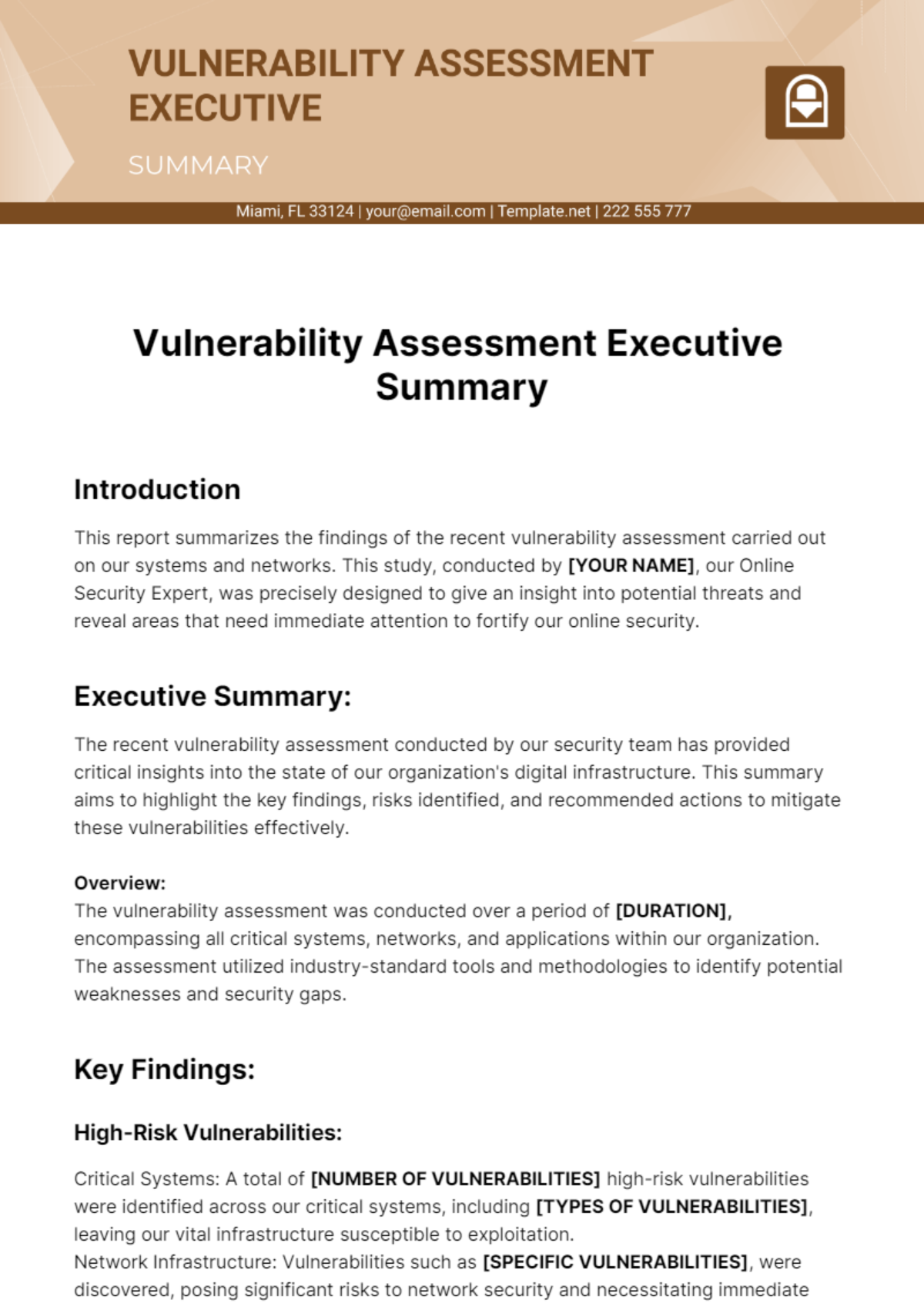
Free Vulnerability Assessment Executive Summary Template to Edit Online

Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Report Template prntbl
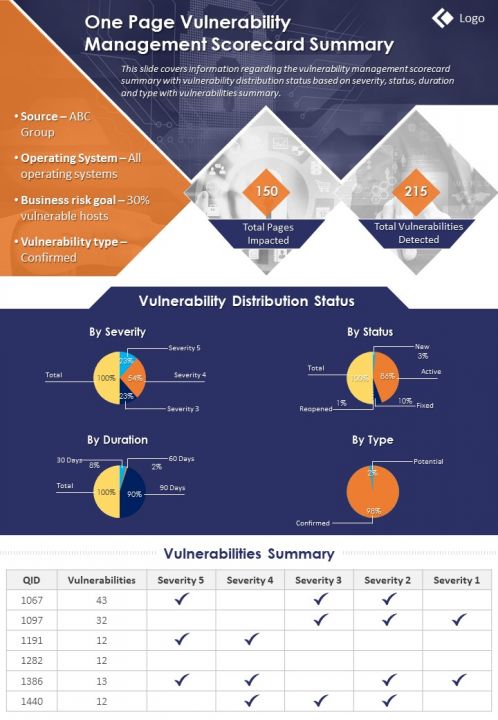
Vulnerability Assessment Report Template prntbl
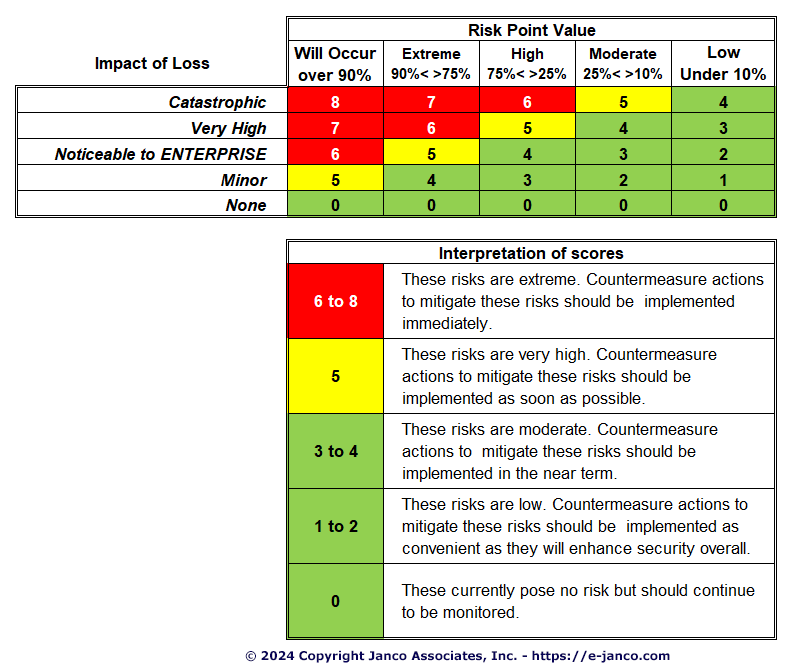
Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Report Template prntbl
Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Report Template prntbl
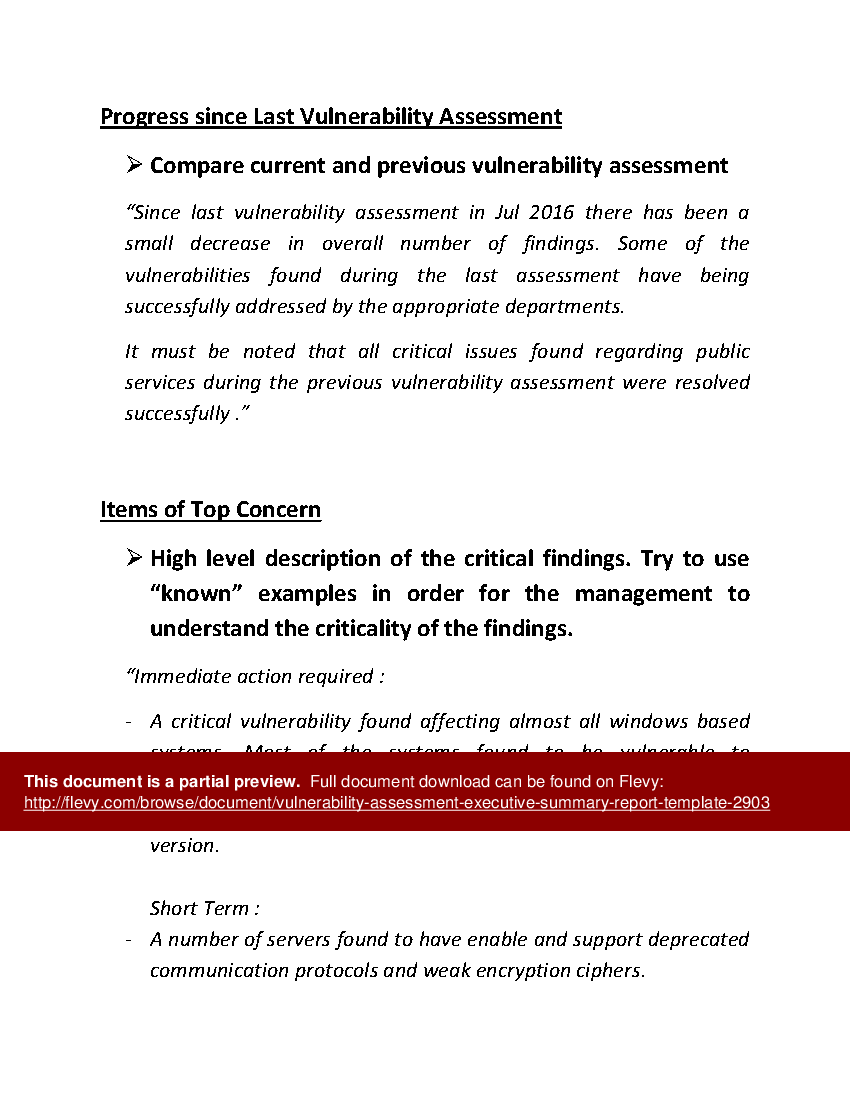
Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Template Free Word Excel Templates

Vulnerability Reporting Template
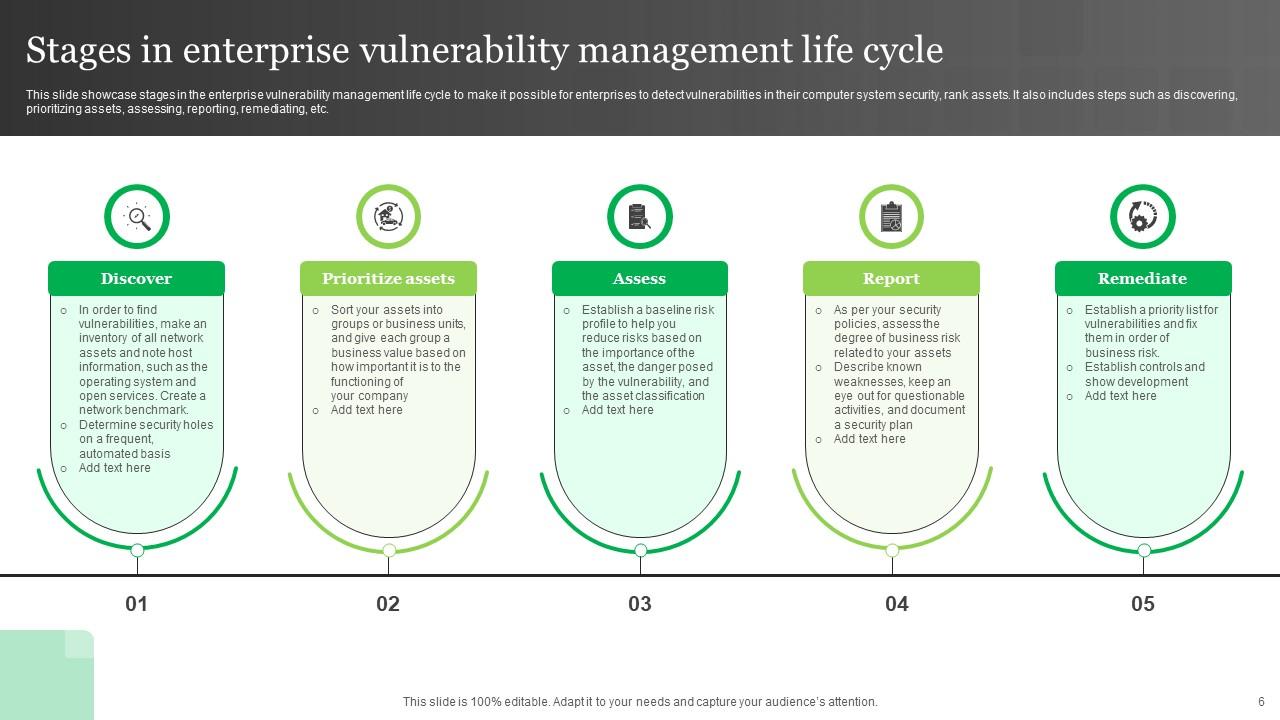
Enterprise Vulnerability Management Powerpoint PPT Template Bundles PPT

Vulnerability Tracking Record Sheet Excel Template And Google Sheets

Free Security Shift Report Template to Edit Online

Vulnerability Tracking Record Sheet Excel Template And Google Sheets

Vulnerability Tracking Record Sheet Excel Template And Google Sheets
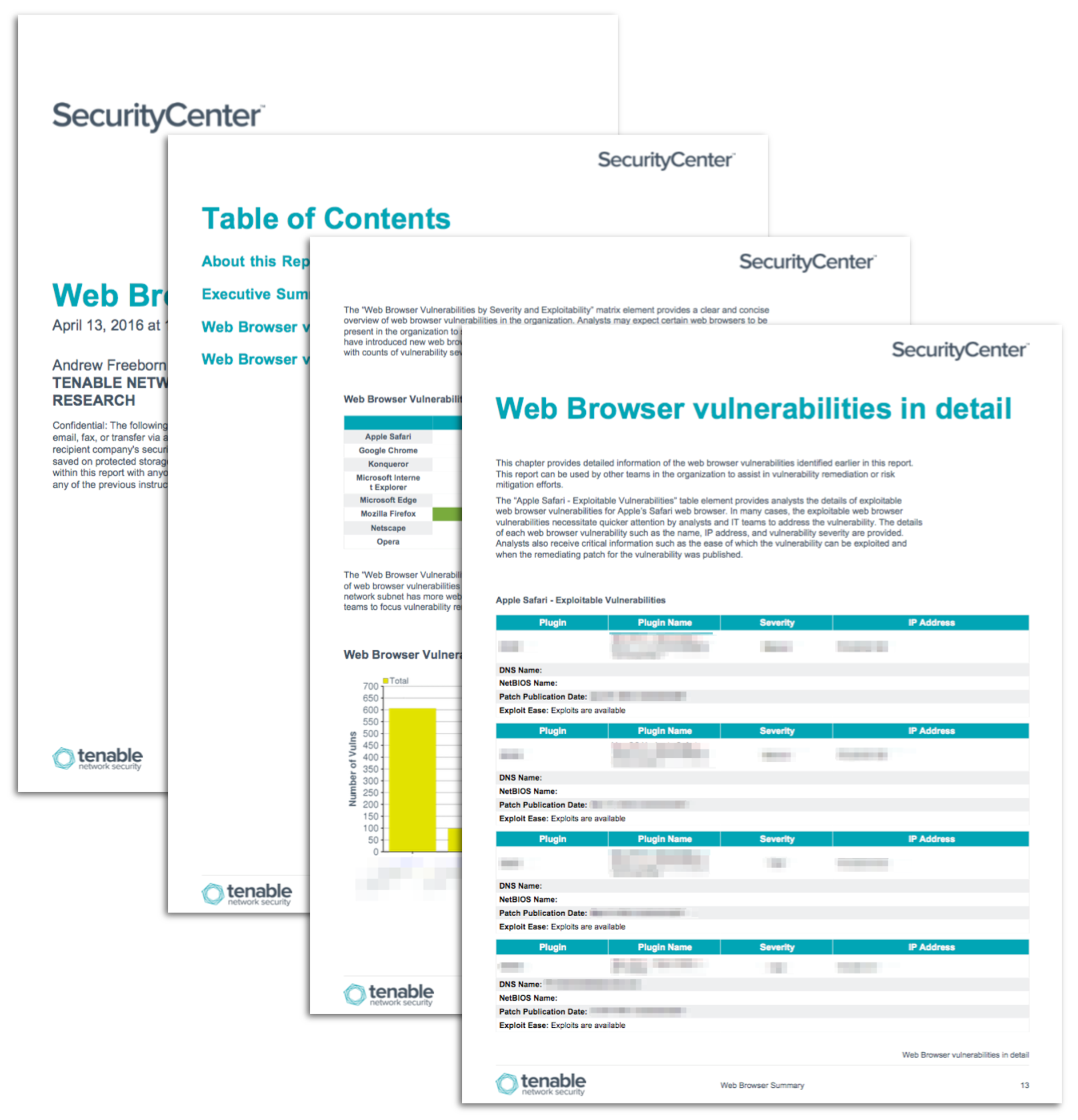
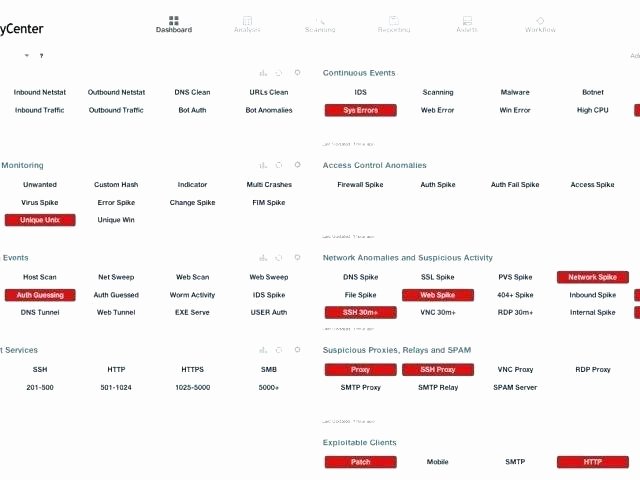
Web Browser Vulnerability Report SC Report Template Tenable®
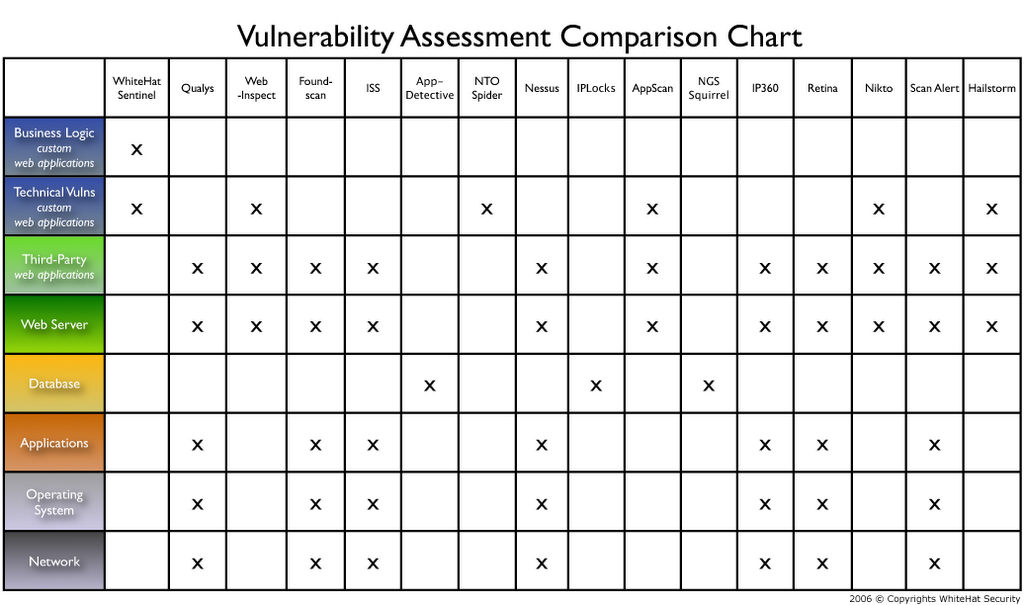
Security Vulnerability Assessment Template prntbl
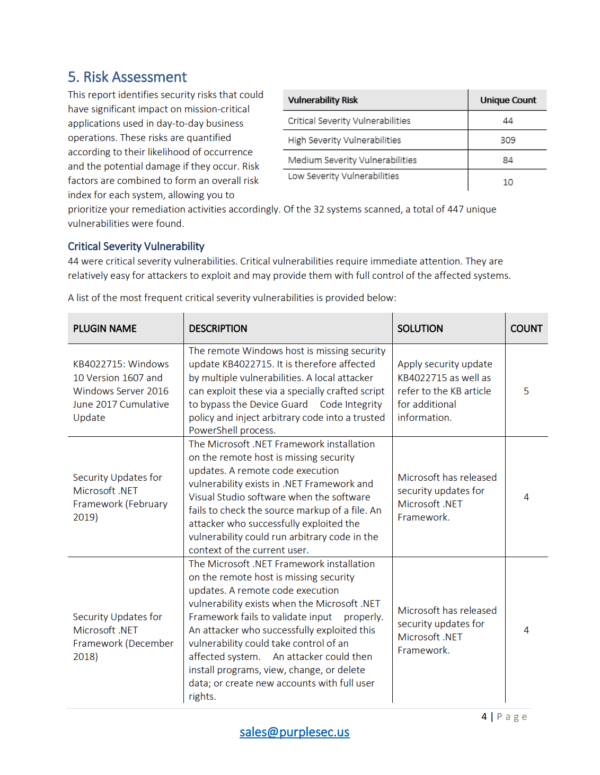
Beautiful Work How To Write A Vulnerability Report Memo

Vulnerability Top Ten Executive Report SC Report Template Tenable®
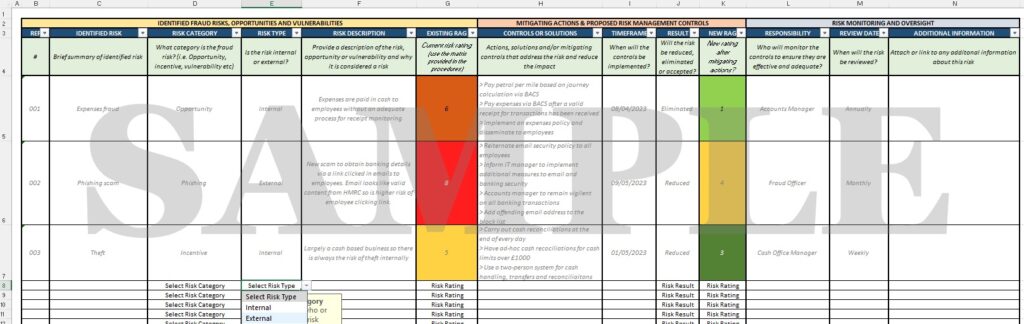
Food Fraud Vulnerability Assessment Template
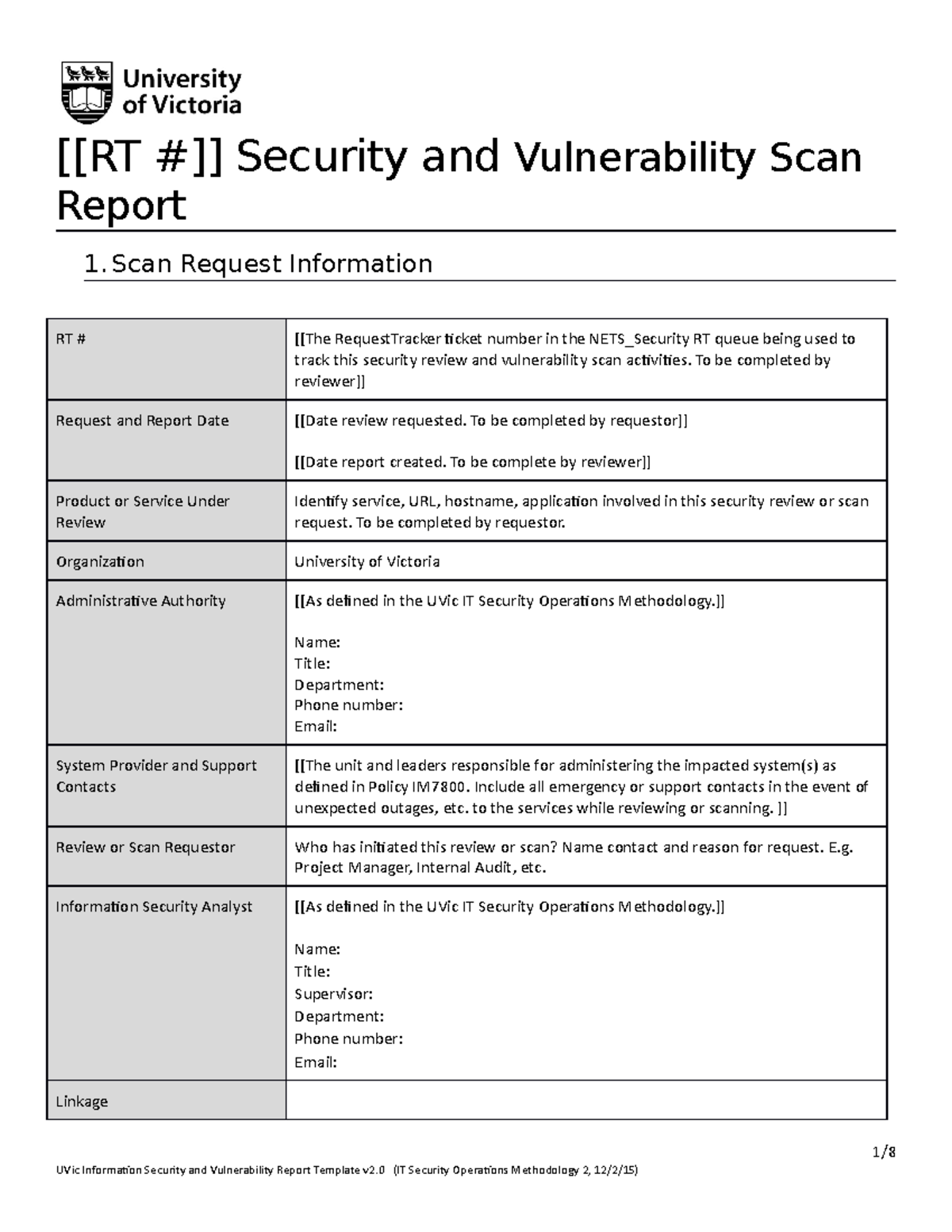
UVic Security and Vulnerability Scan Report Template v2 RT
Vulnerability Worksheets
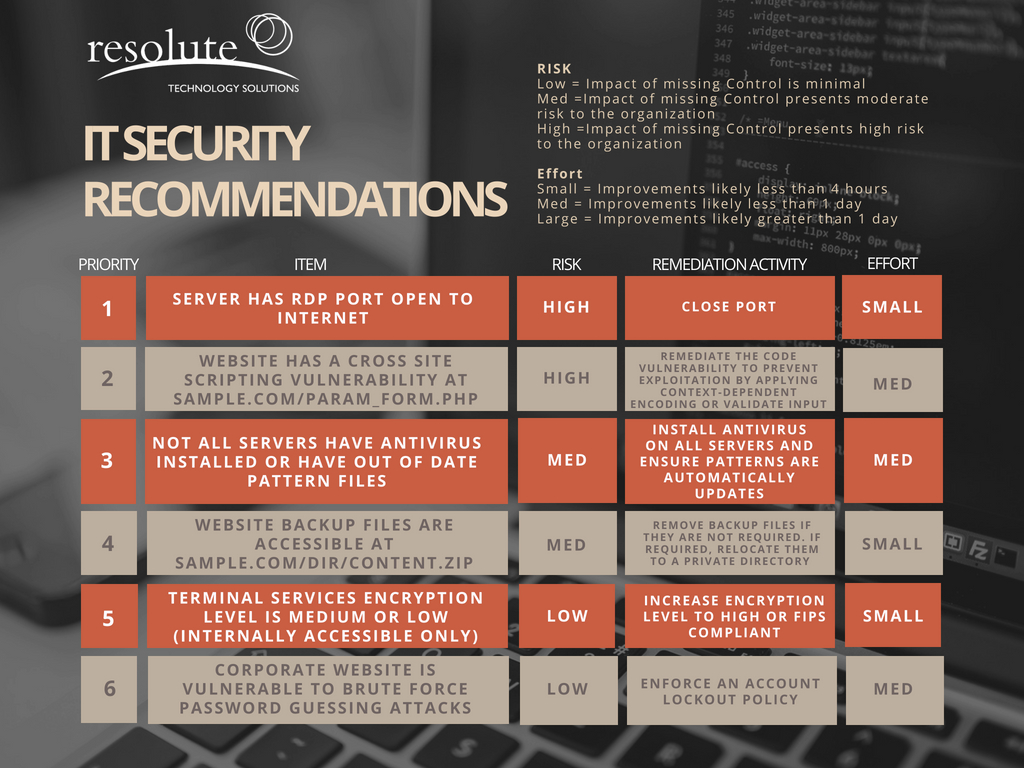
Cybersecurity Report Template

Risk Assessment Template Cyber Security astra edu pl
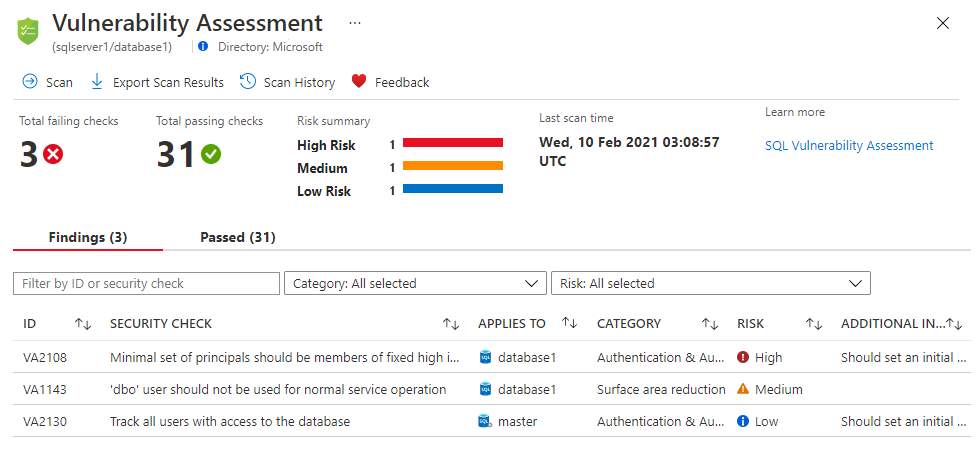
Vulnerability Assessment Report

Threat Analysis And Risk Assessment Template prntbl
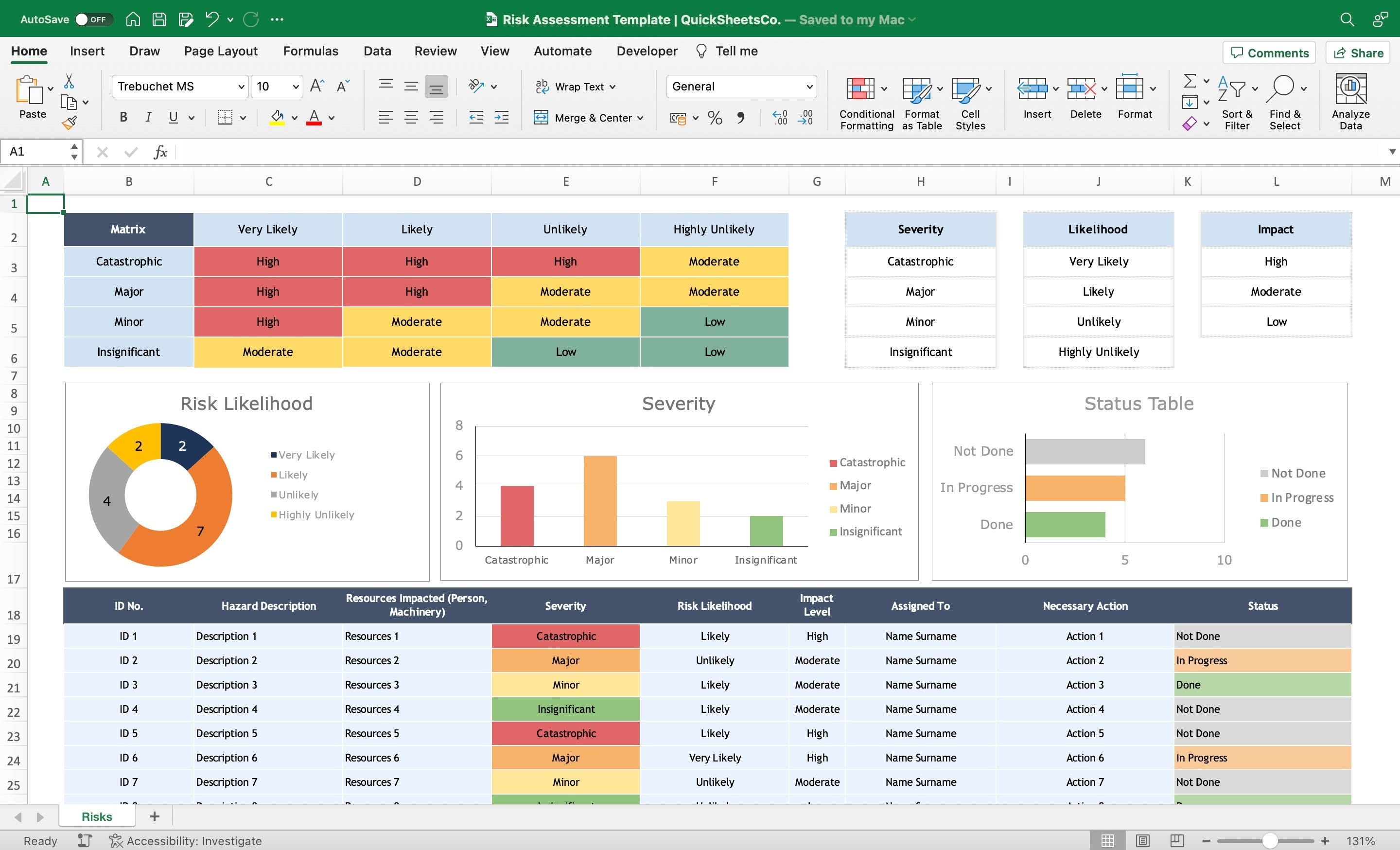
Risk Assessment Excel Template Business Spreadsheet Risk Management
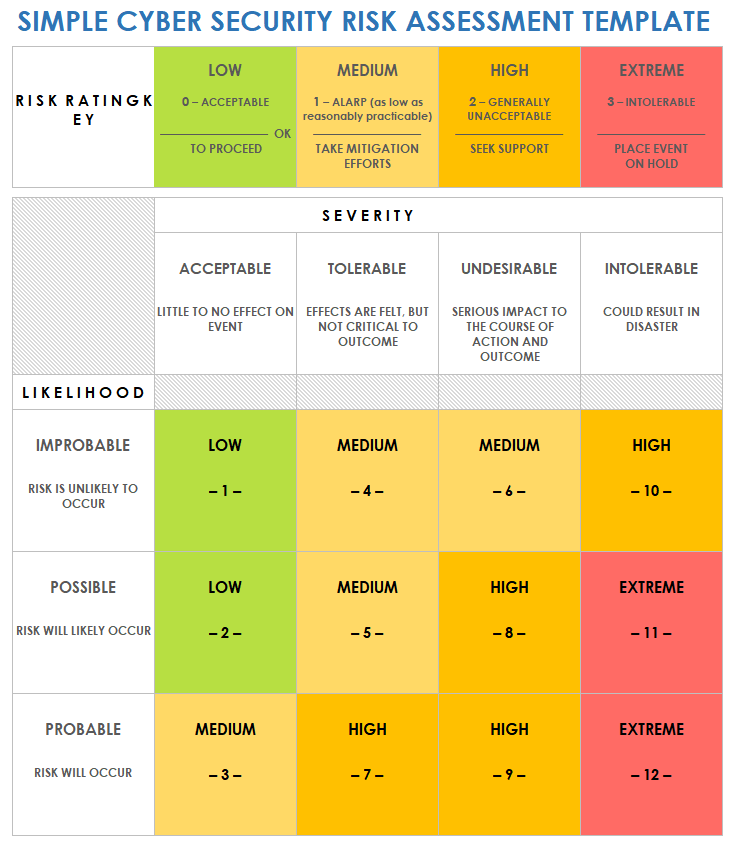
Free Cybersecurity Risk Assessment Templates Smartsheet

Top 10 Information Dashboard Templates with Samples and Examples