Vulnerability Report Template Doc
Here are some of the images for Vulnerability Report Template Doc that we found in our website database.

Vulnerability assessment report template PDF Security Computer
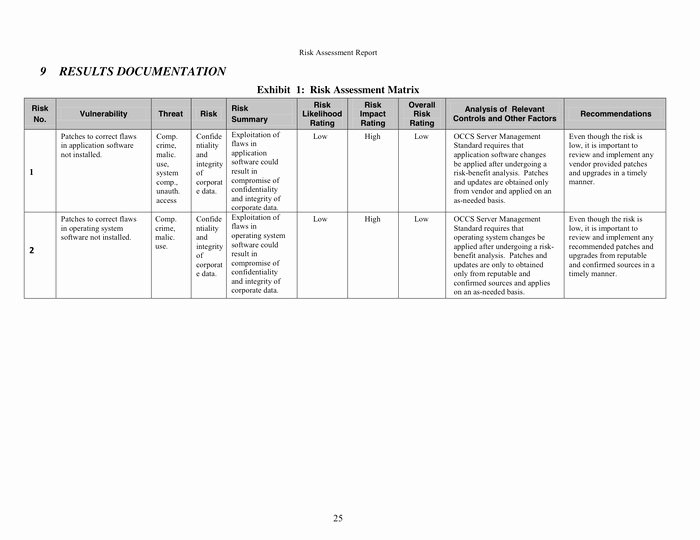
Vulnerability Assessment Report Template
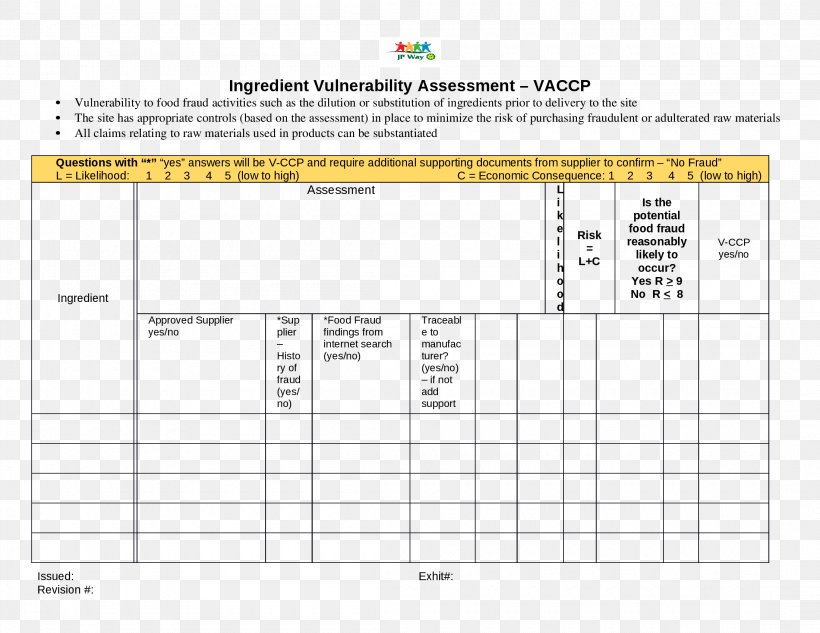
Vulnerability Report Template Doc
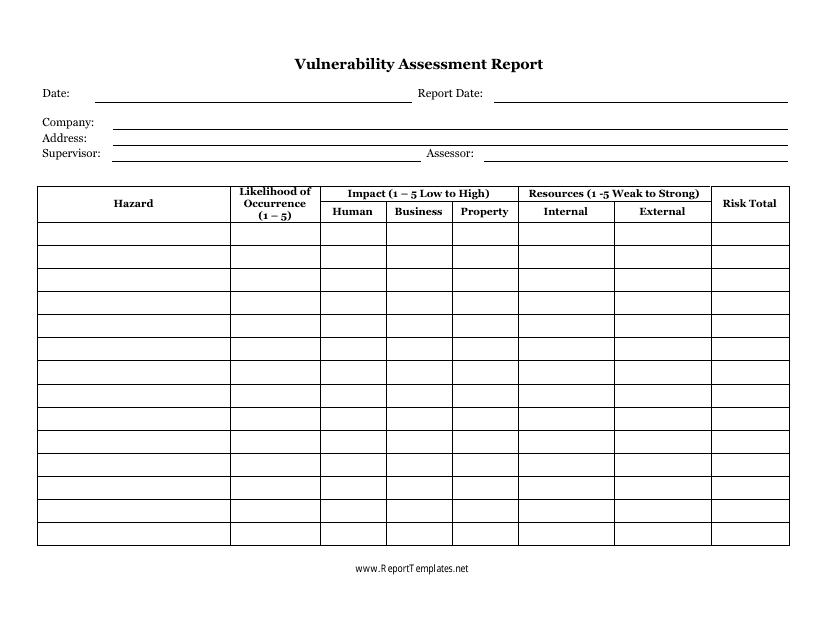
Vulnerability Assessment Report Template Fill Out Sign Online and

Vulnerability Report Template Content Calendar Template

Vulnerability Report Template
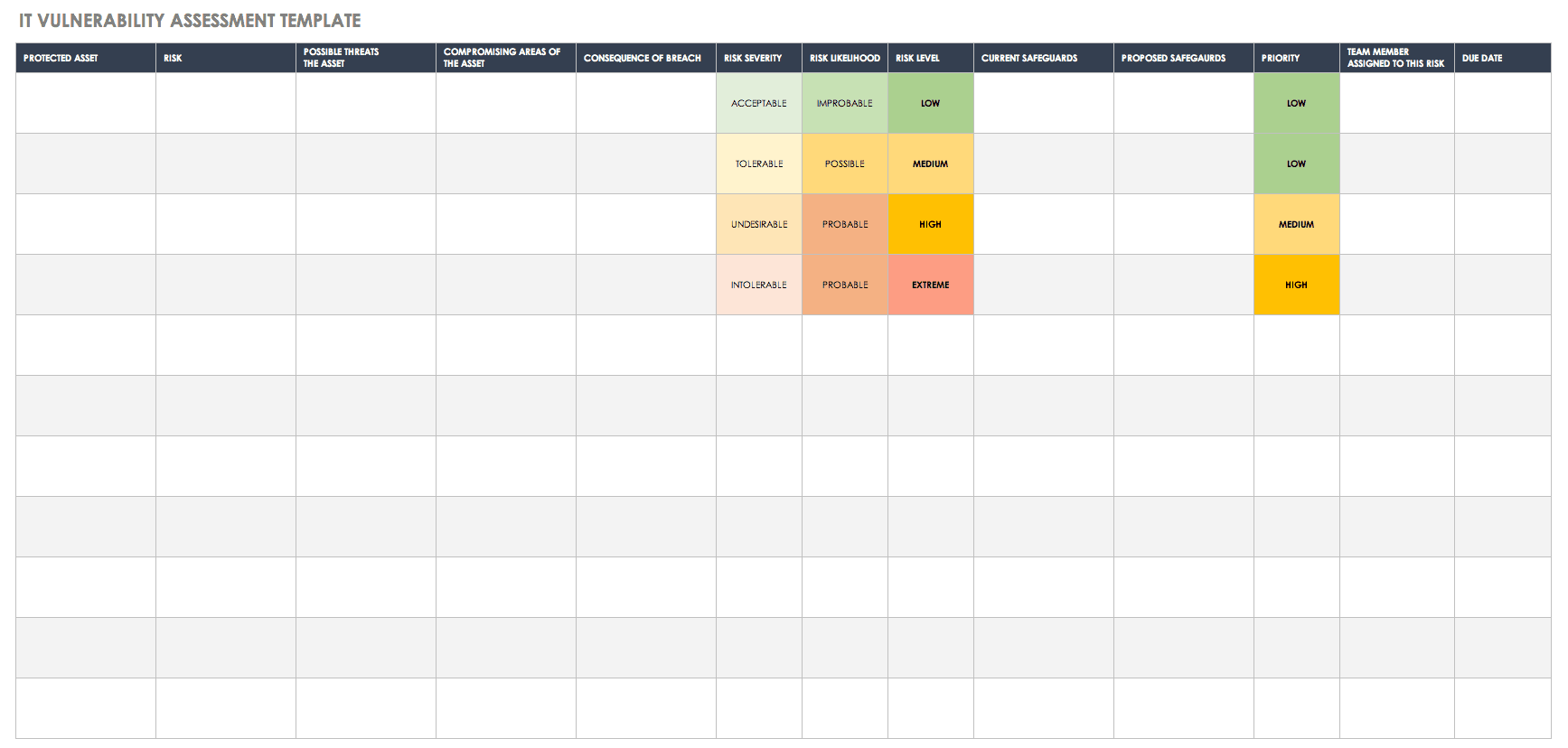
Vulnerability Report Template

Vulnerability Report Template
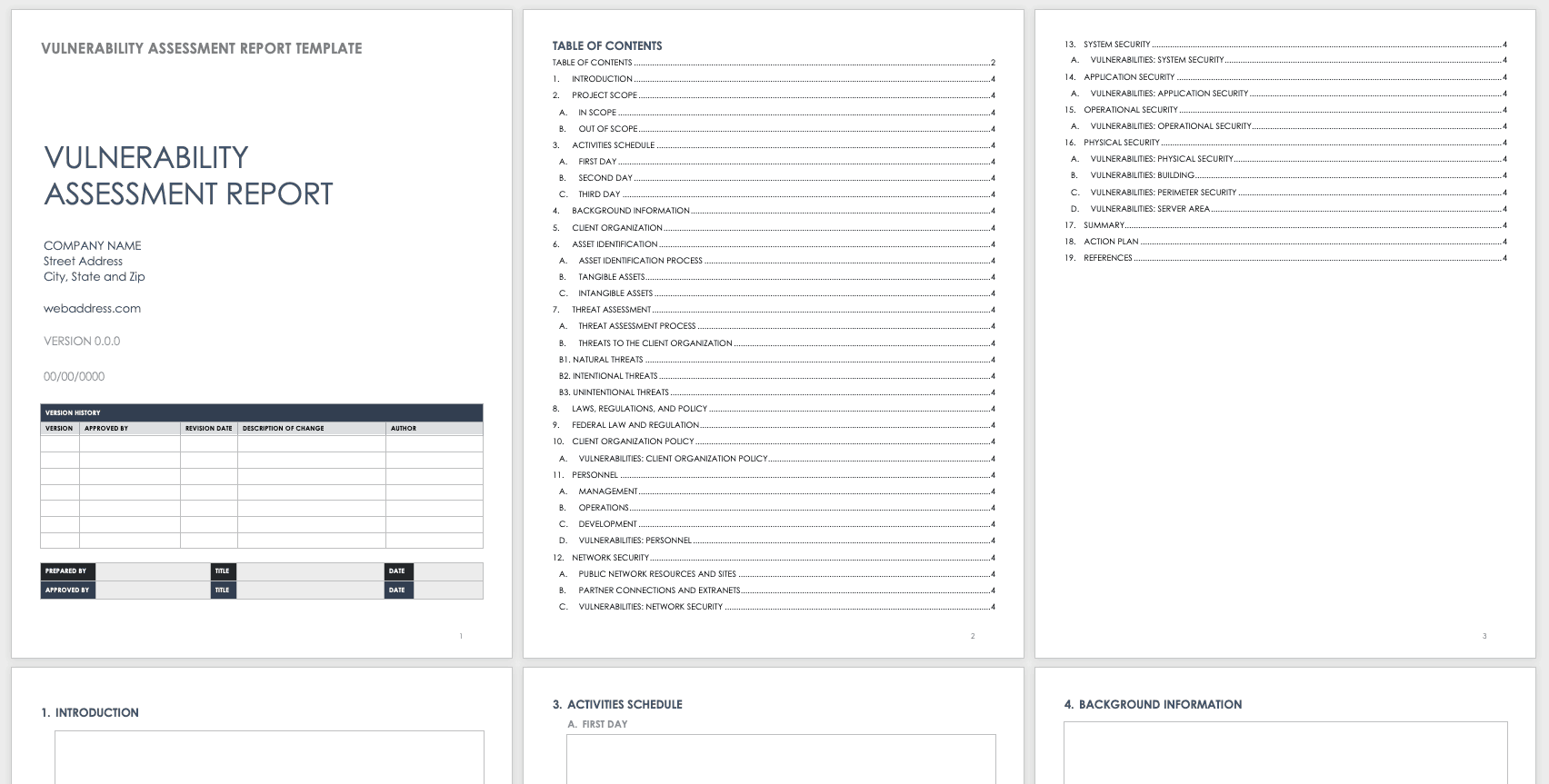
Vulnerability Report Template

Medical Report Template Doc Cardtemplate my id

14 Vulnerability Assessment Templates PDF DOC Pages

14 Vulnerability Assessment Templates PDF DOC Pages

14 Vulnerability Assessment Templates PDF DOC Pages

14 Vulnerability Assessment Templates PDF DOC Pages

14 Vulnerability Assessment Templates PDF DOC Pages

14 Vulnerability Assessment Templates PDF DOC Pages

Vulnerability Report Template Report template Templates Vulnerability

14 Vulnerability Assessment Templates PDF DOC Pages
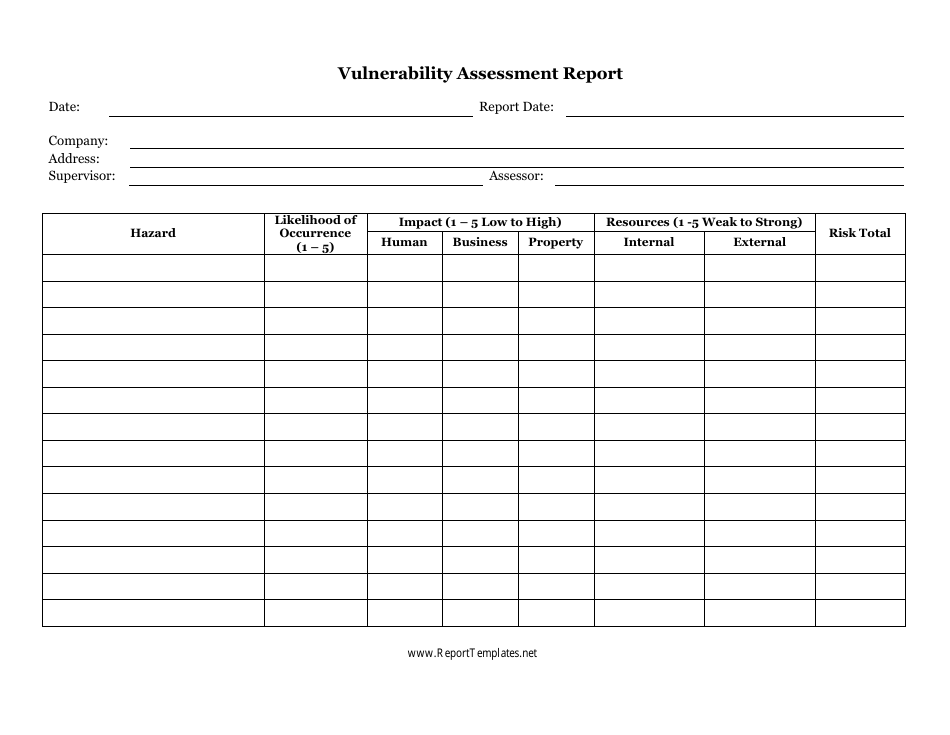
Vulnerability Report Template

Vulnerability Report Template

Vulnerability Report Template
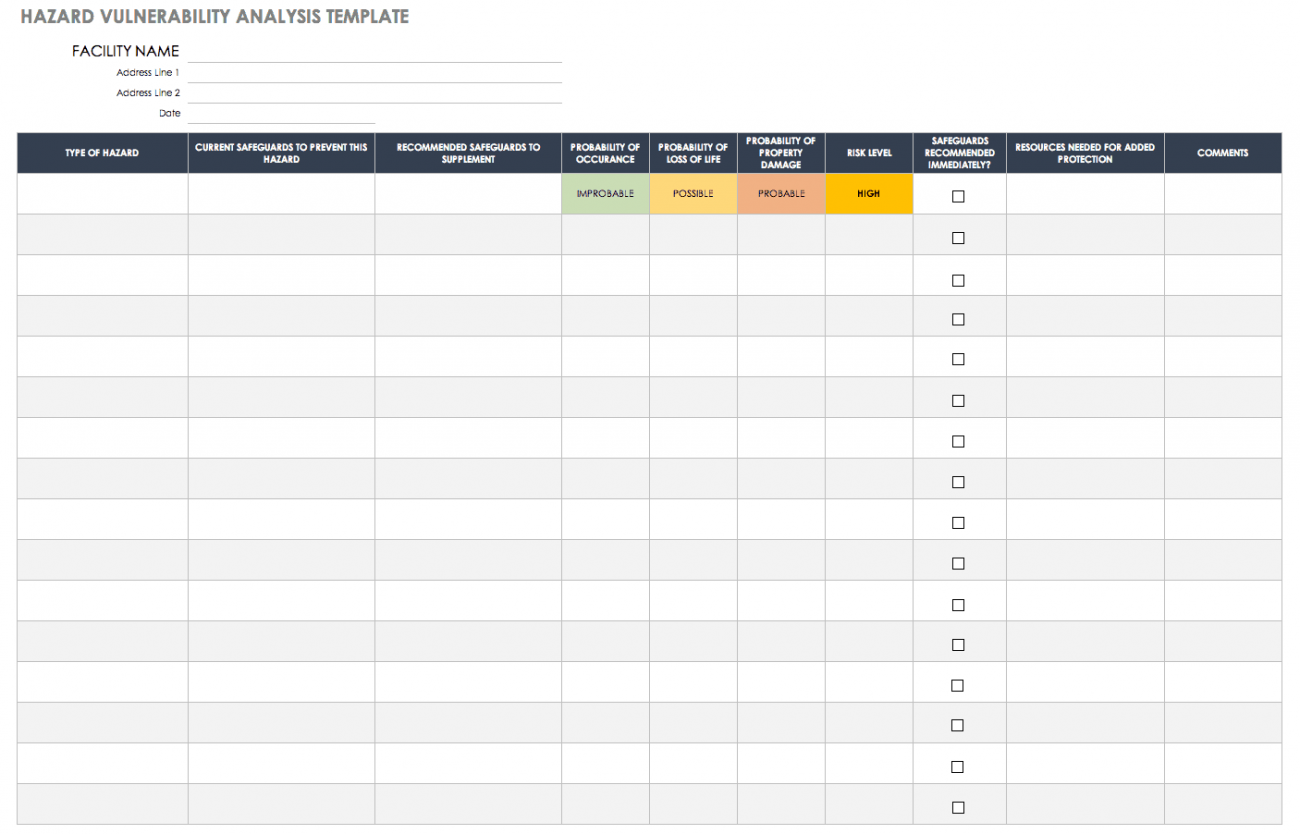
Vulnerability Report Template

Vulnerability Management Report Template

IT Security Vulnerability Assessment Template in Word PDF Google Docs

Vulnerability Scan Report Template
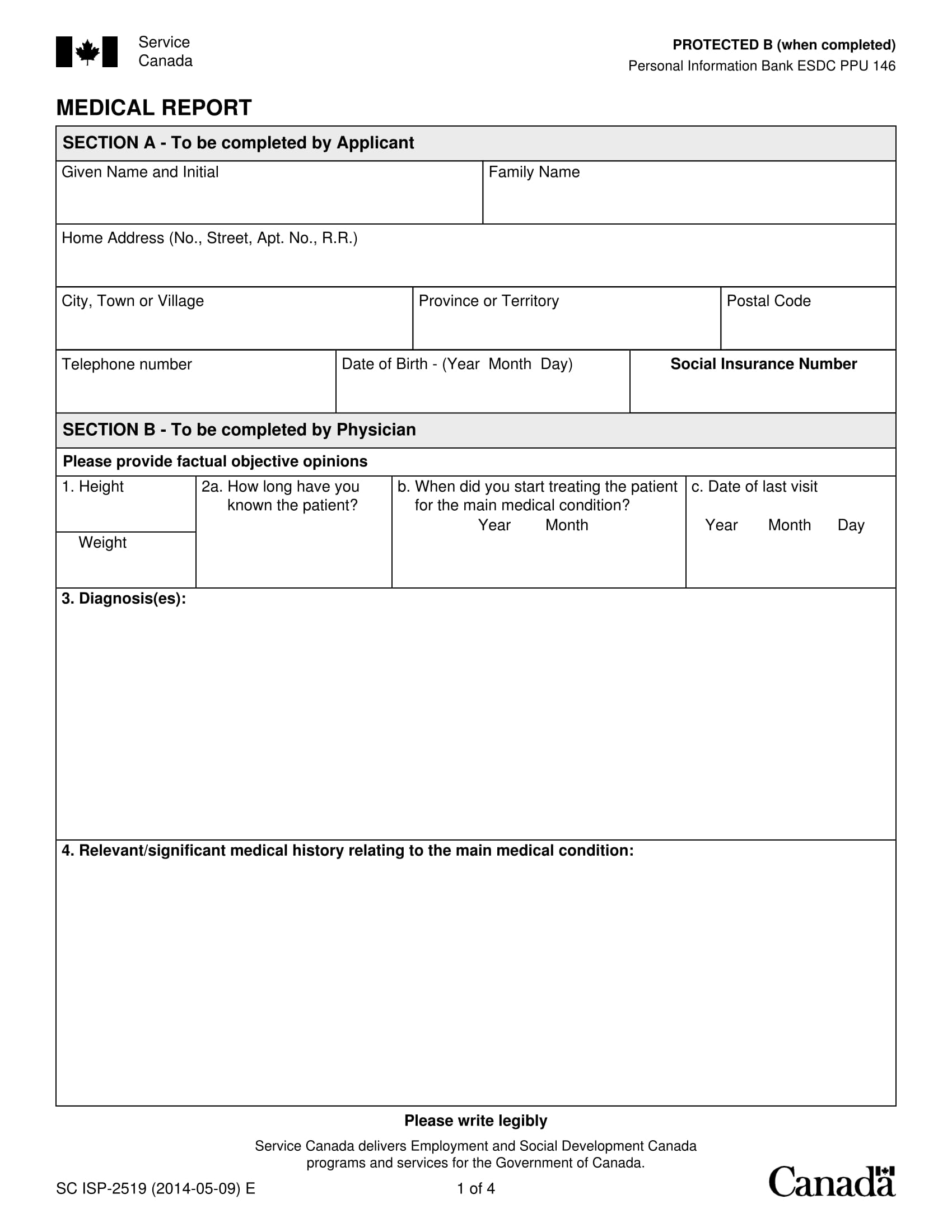
Medical Report Template Doc Ccalcalanorte com
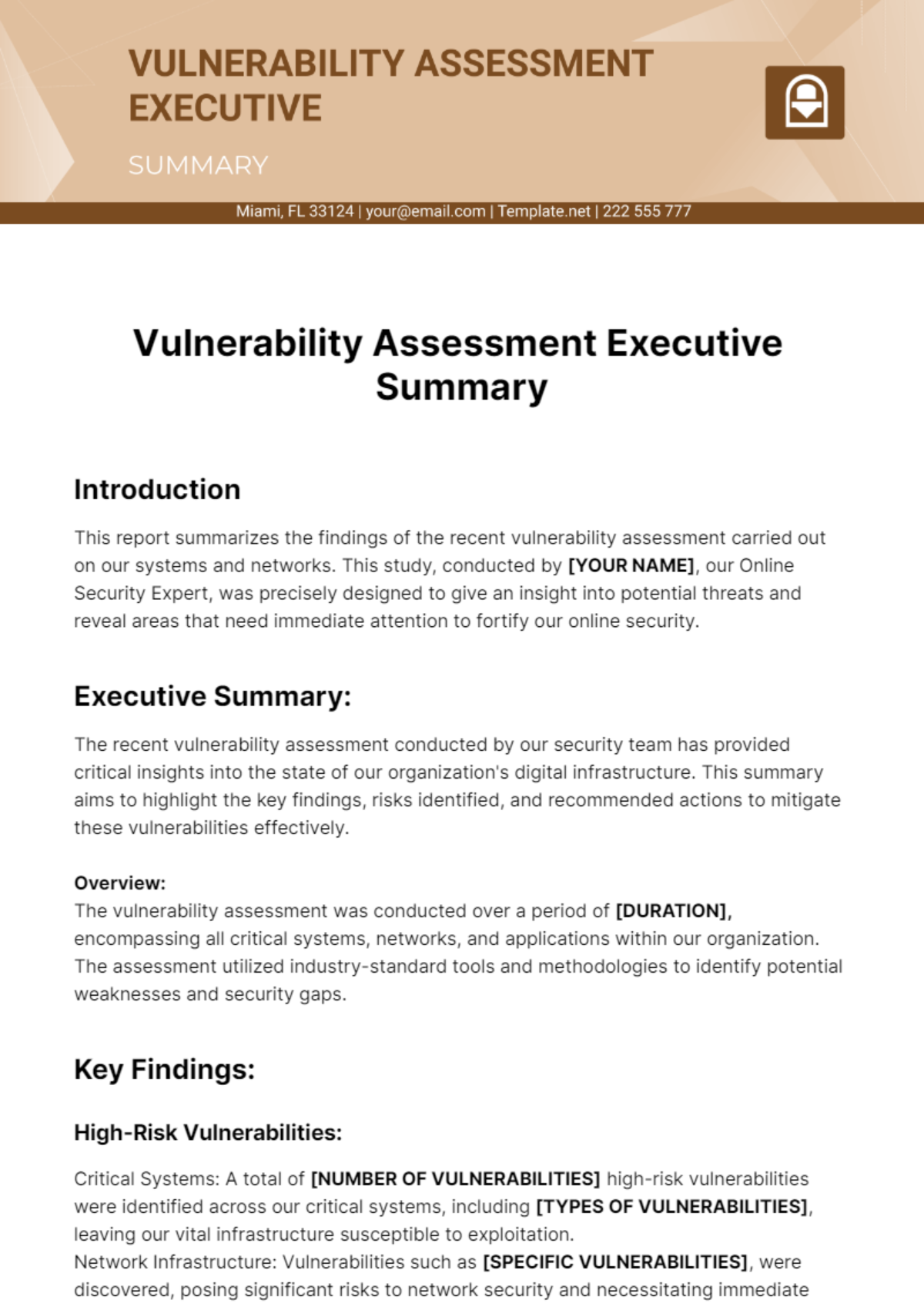
Free Vulnerability Assessment Executive Summary Template to Edit Online

Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Report Template prntbl
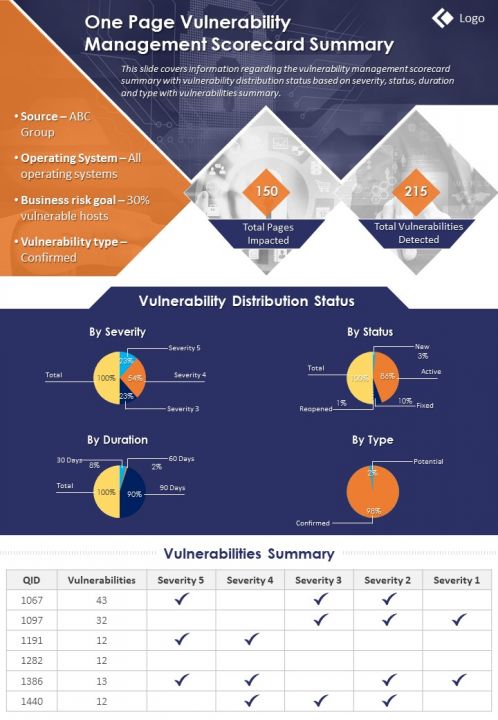
Vulnerability Assessment Report Template prntbl
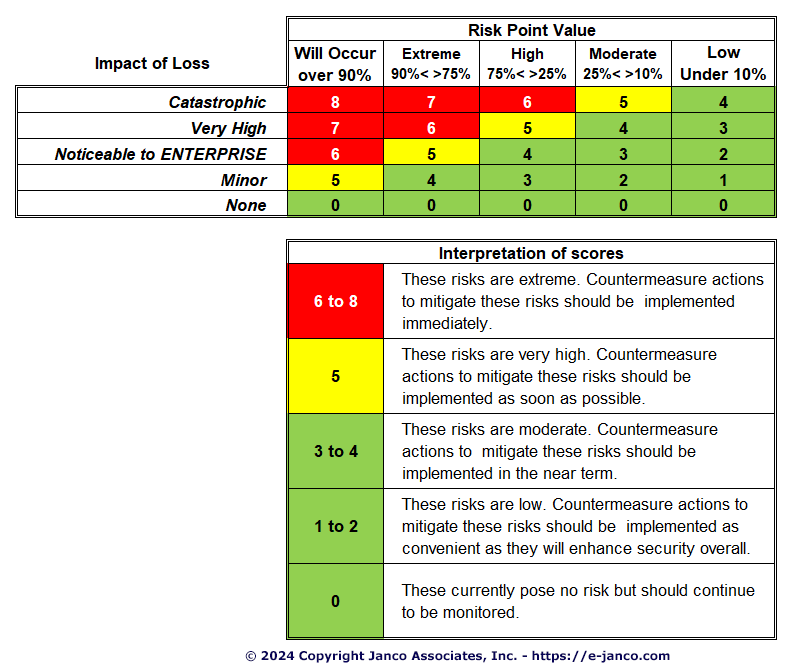
Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Report Template prntbl
Vulnerability Assessment Report Template prntbl
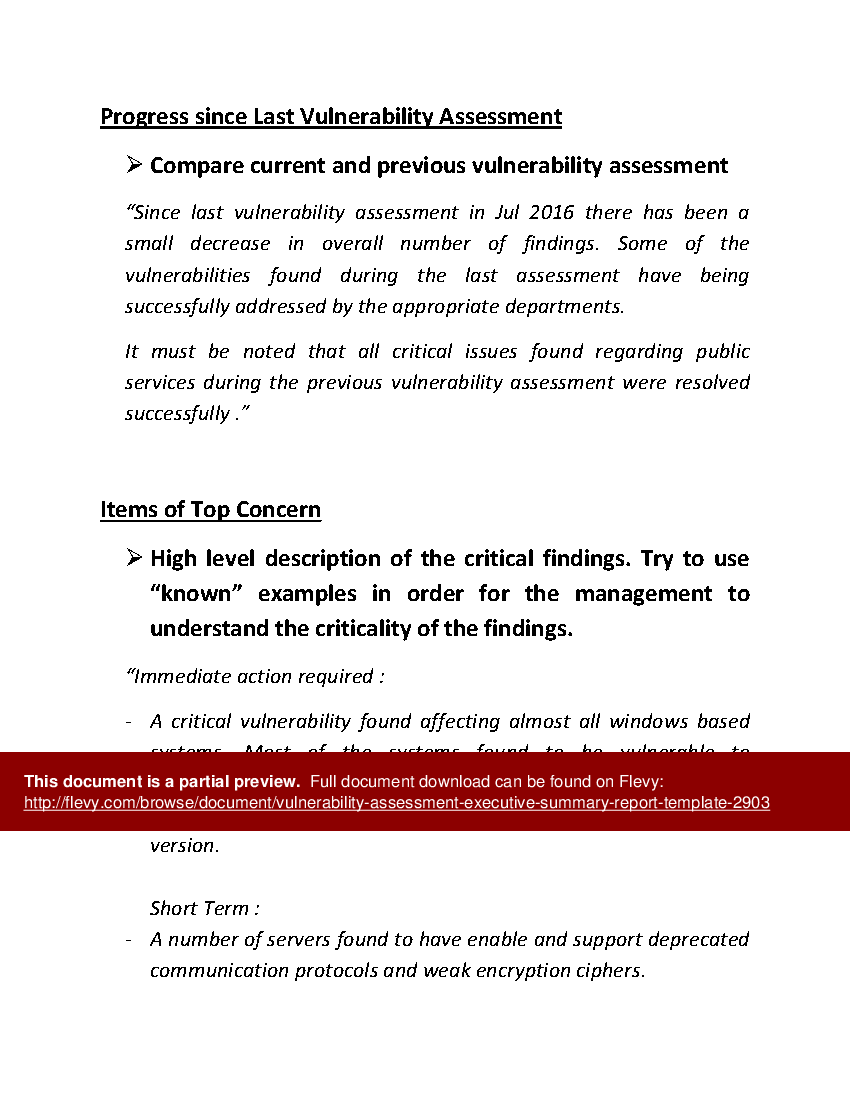
Vulnerability Assessment Report Template prntbl

Vulnerability Assessment Template Free Word Excel Templates

Vulnerability Tracking Record Sheet Excel Template And Google Sheets

Vulnerability Tracking Record Sheet Excel Template And Google Sheets
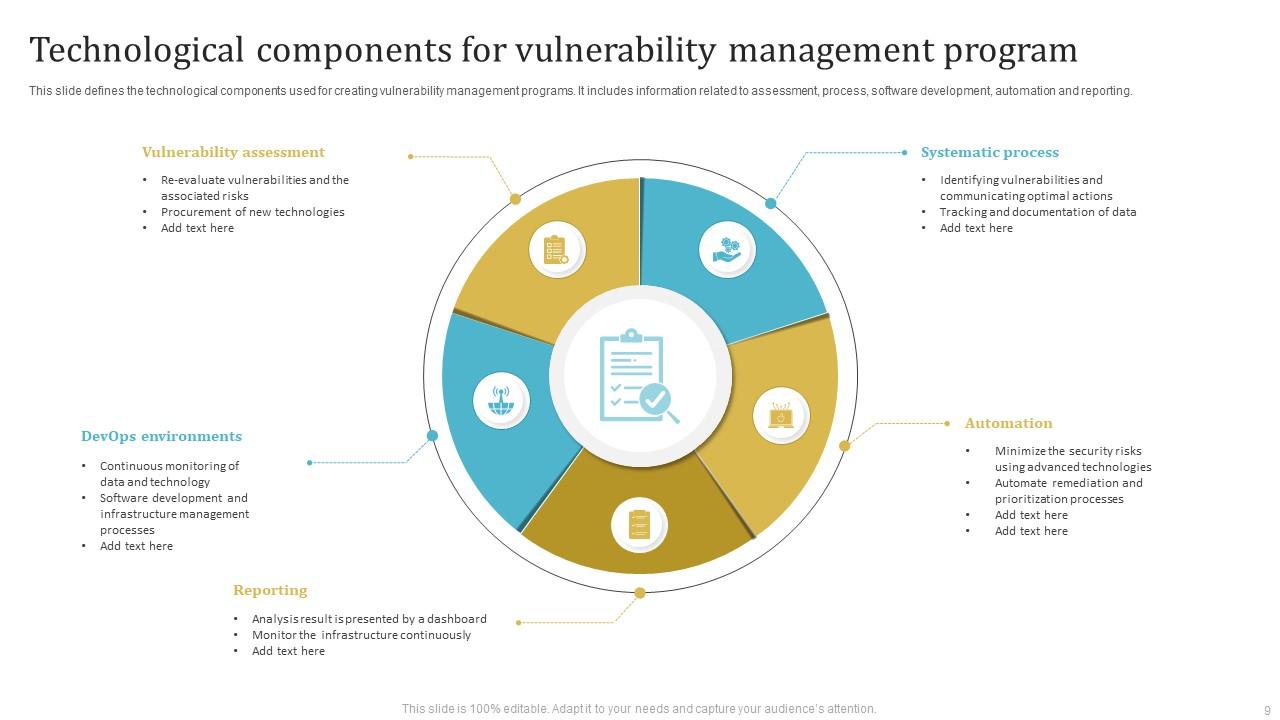
Vulnerability Management Program Powerpoint Ppt Template Bundles PPT Sample

Free Security Patrol Report Design Template to Edit Online

Information Security Report Template Templates maexproit com

Pentest Report Template Word
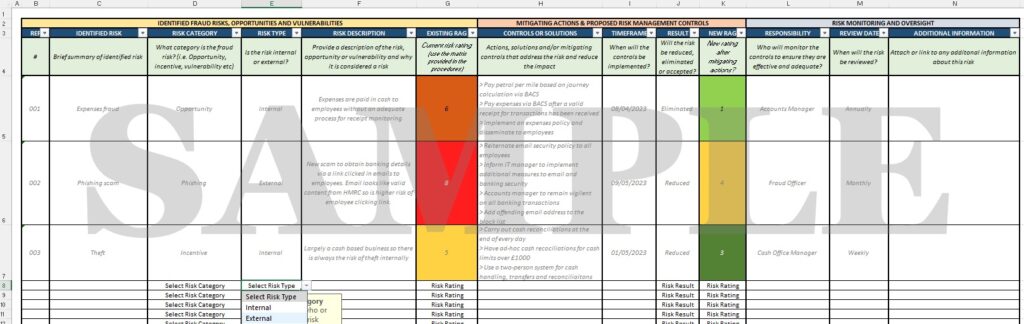
Food Fraud Vulnerability Assessment Template
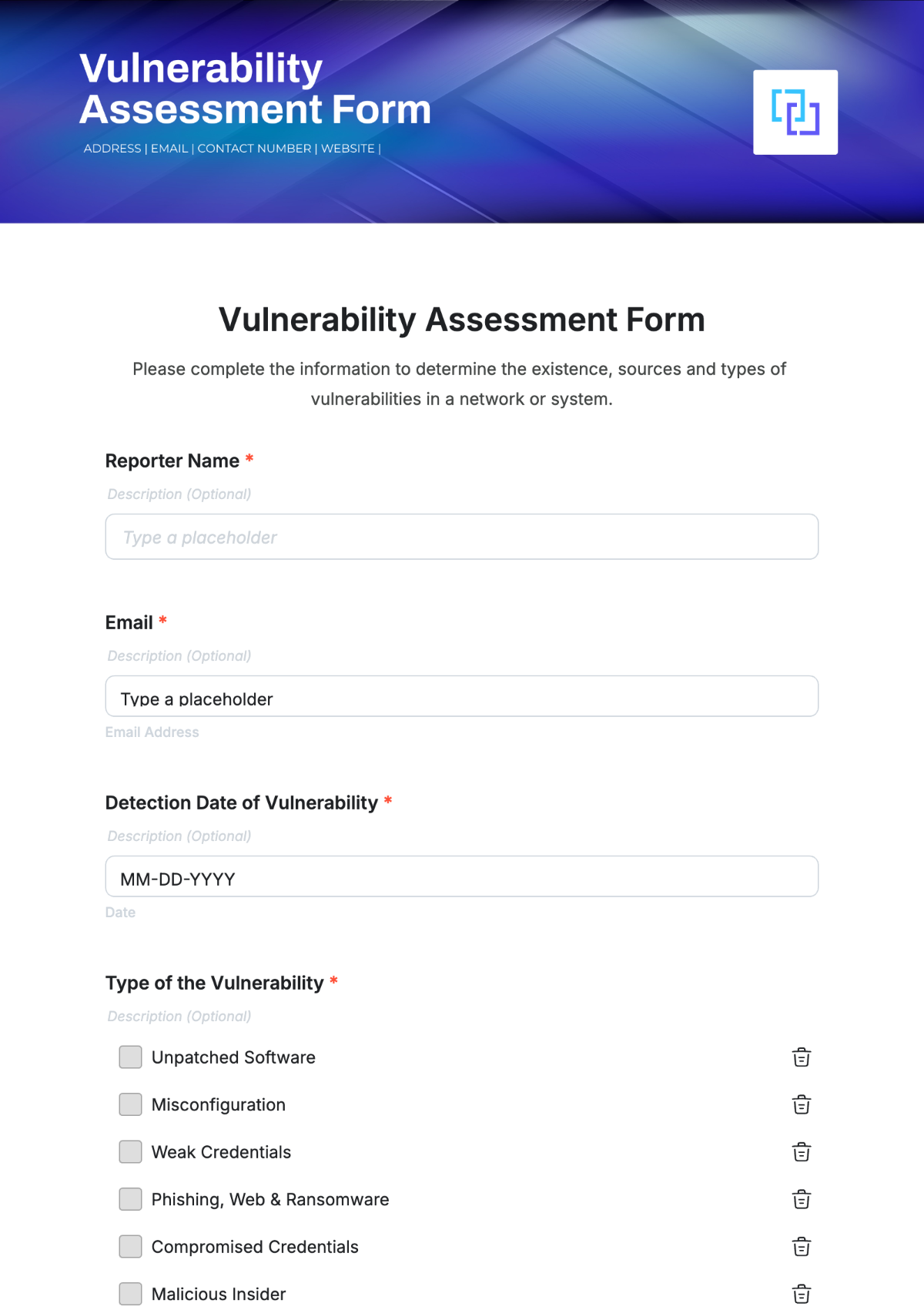
Free Assessment Form Templates to Edit Online
Vulnerability Worksheets
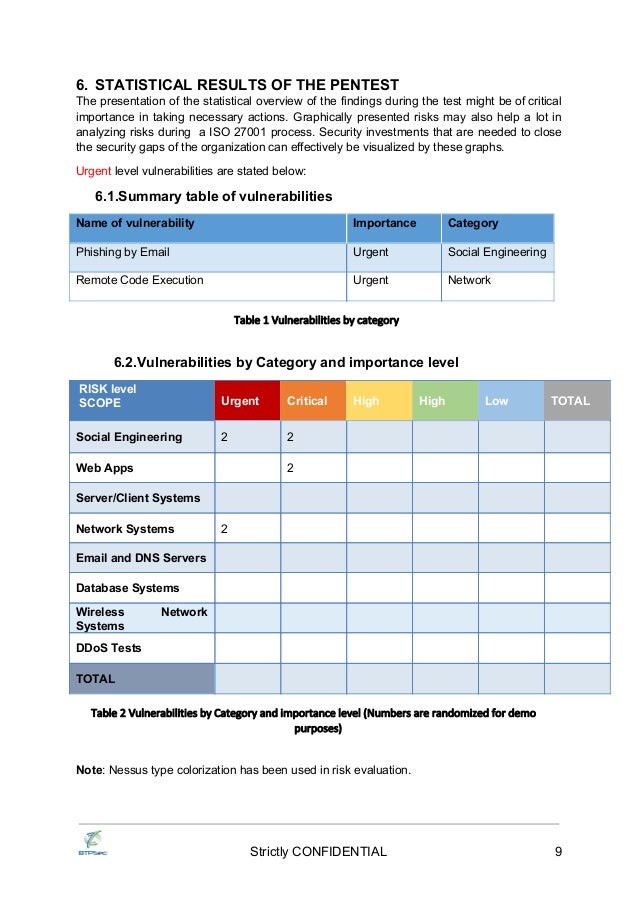
Pen Test Report Template
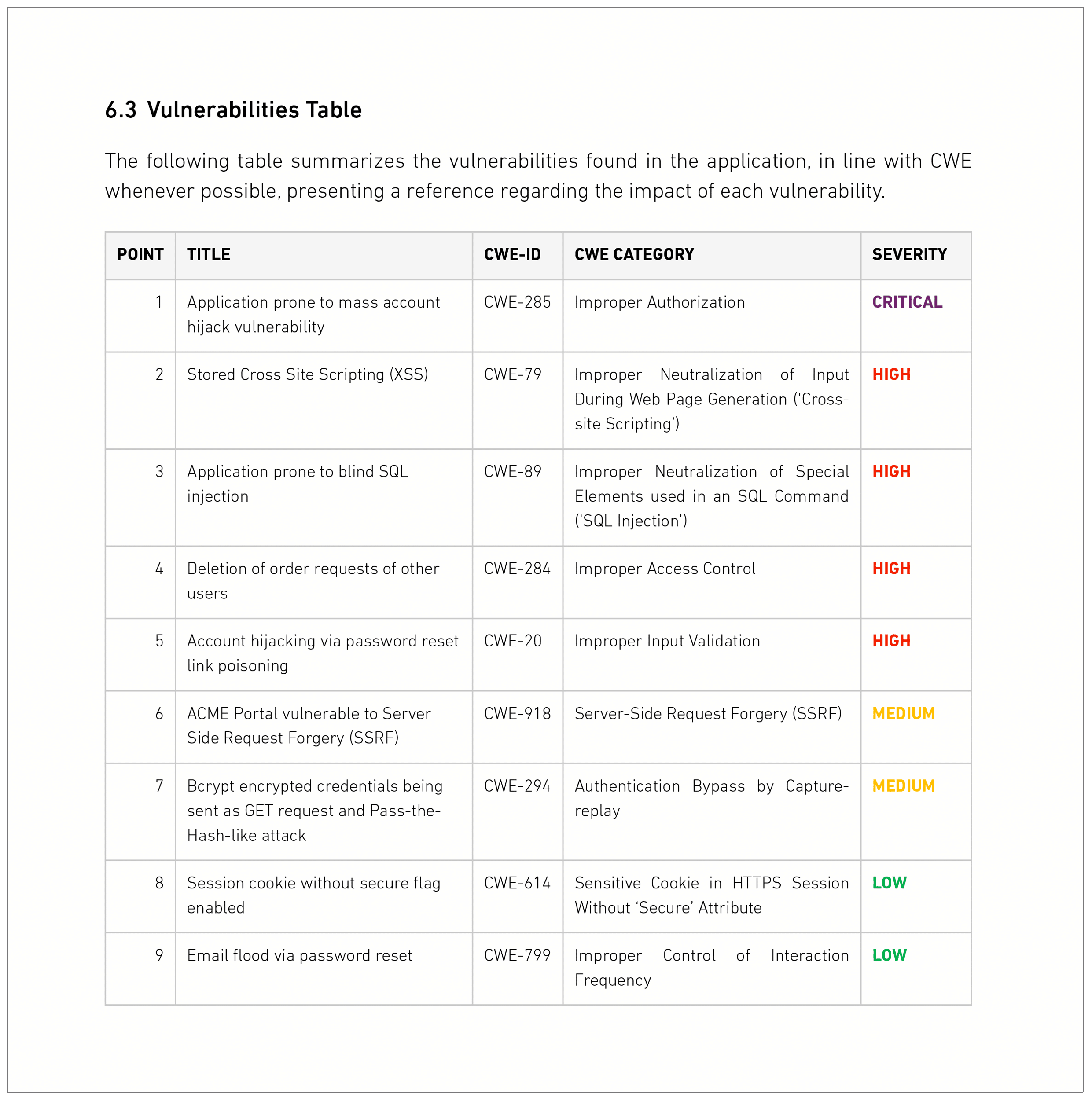
Test Report Template prntbl concejomunicipaldechinu gov co
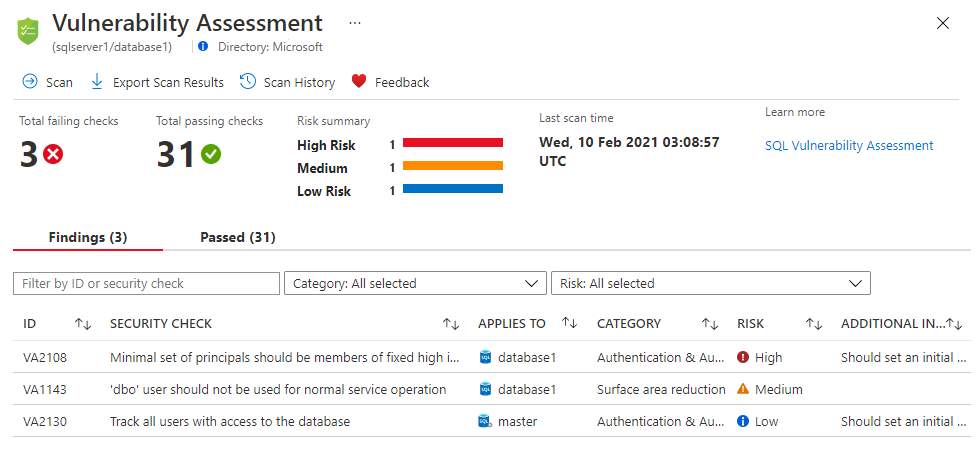
Vulnerability Assessment Report
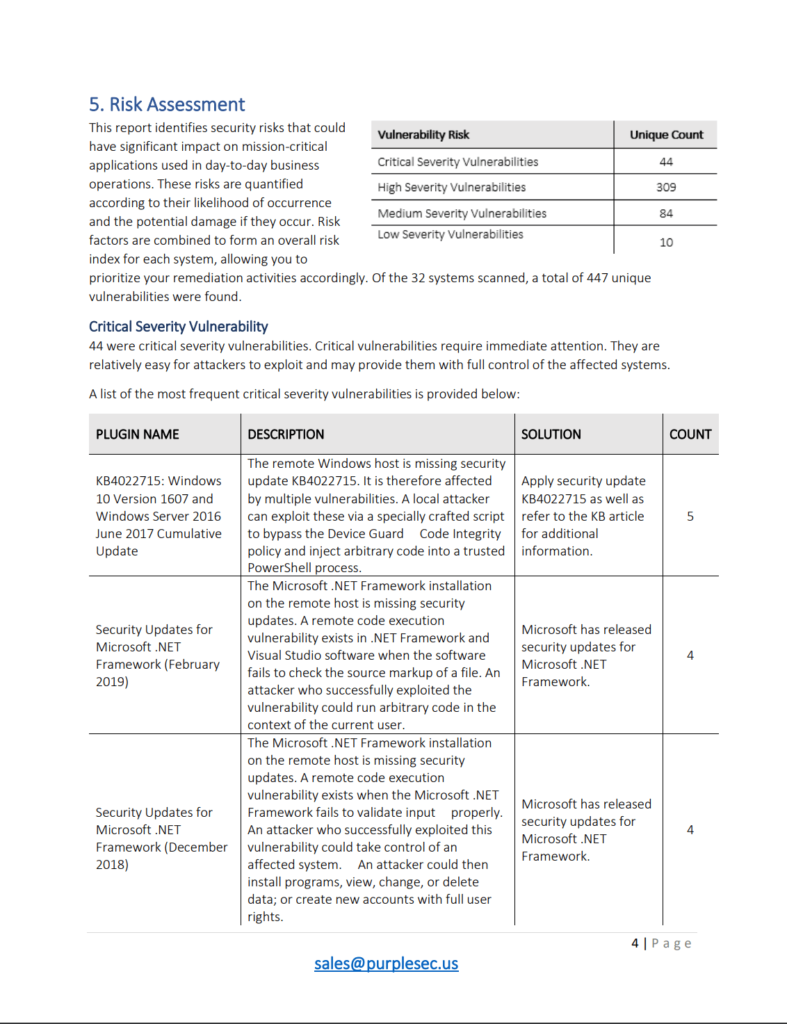
Security Risk Assessment Template Bioterrorism Security Risk
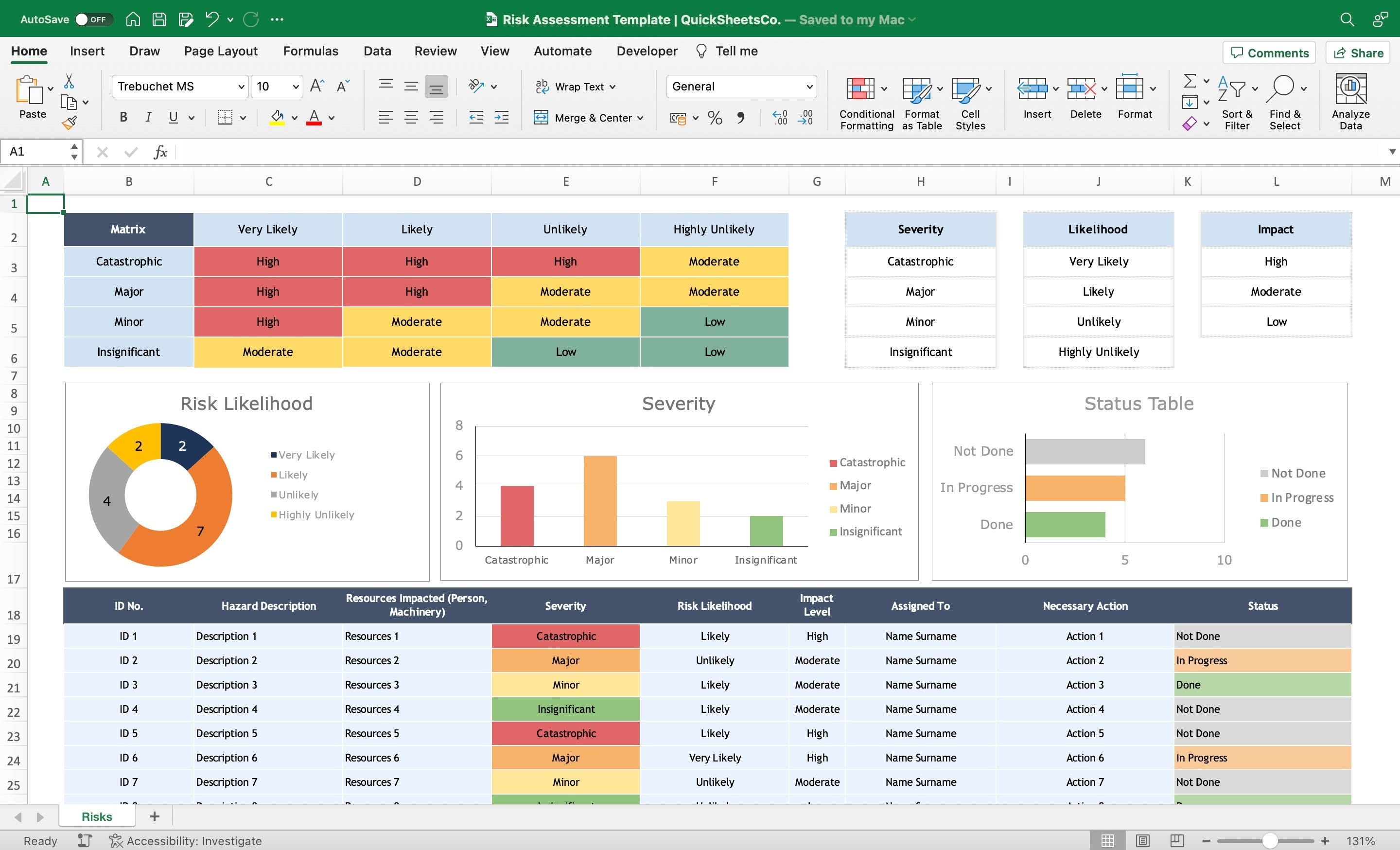
Risk Assessment Excel Template Business Spreadsheet Risk Management

Threat Analysis And Risk Assessment Template prntbl
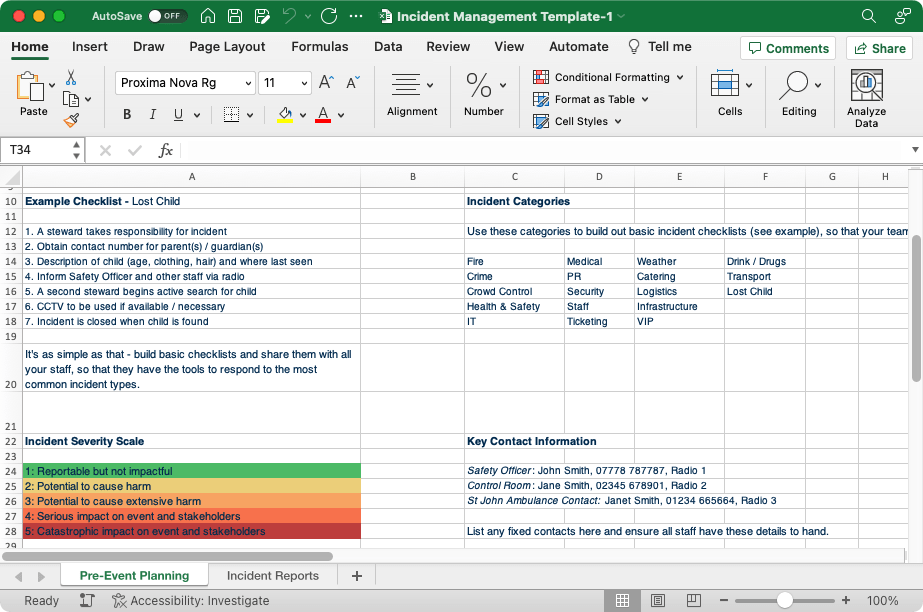
10 Free Incident Report Templates in ClickUp Docs Word and Excel
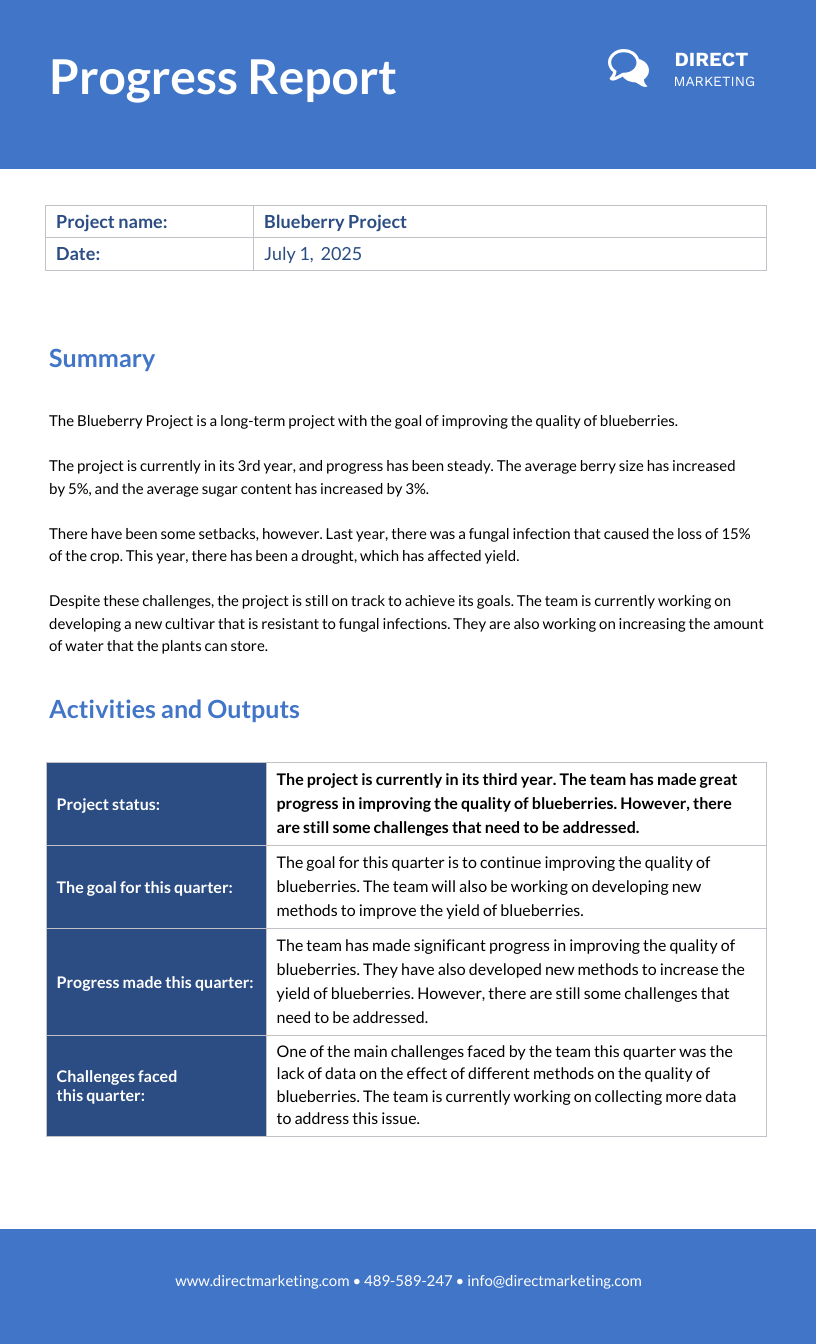
Modello di relazione sullo stato di avanzamento dei lavori Venngage

Employee Disciplinary Form Template Free

First Accident Report
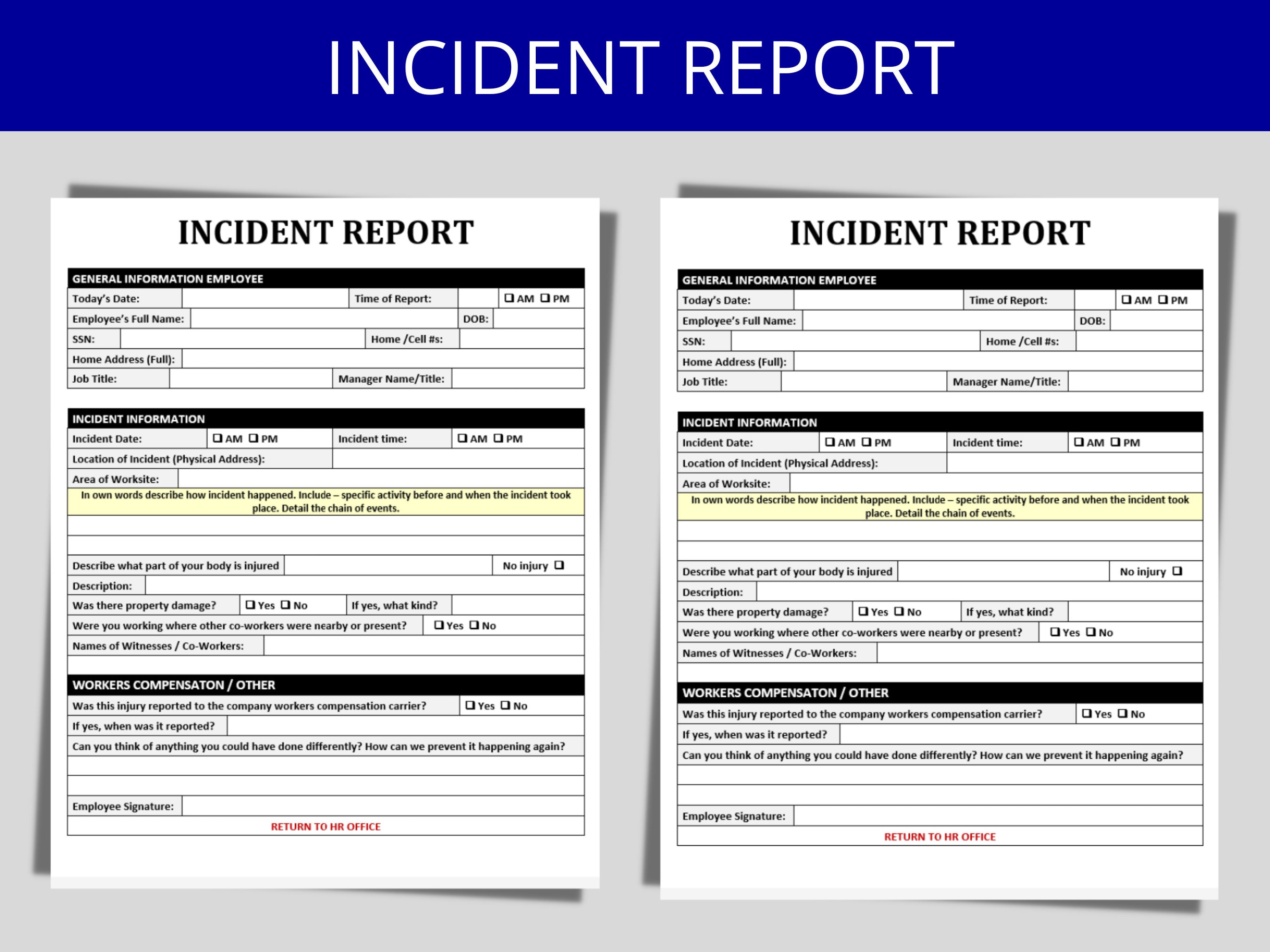
Generic Employee Incident Report Form