Vulnerability Tracking Spreadsheet Template
Here are some of the images for Vulnerability Tracking Spreadsheet Template that we found in our website database.

Vulnerability Tracking Spreadsheet with Contract Tracking Spreadsheet
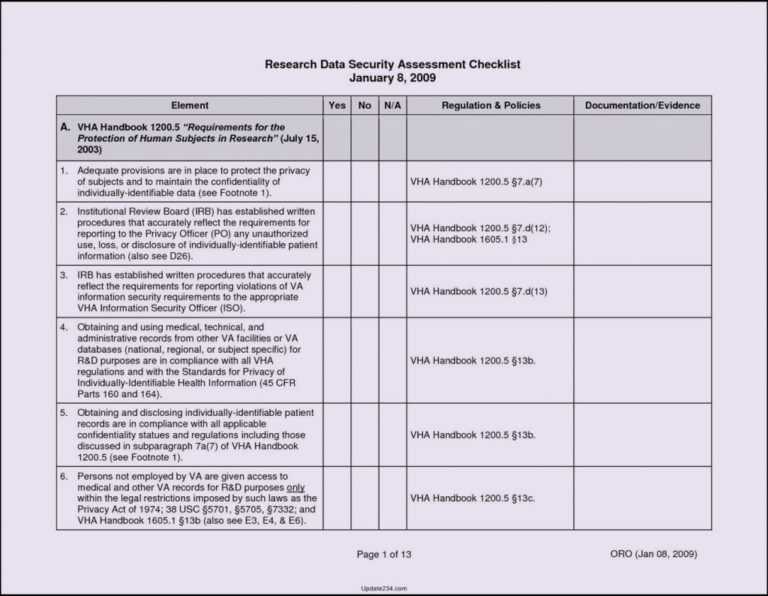
Vulnerability Tracking Spreadsheet pertaining to Network Vulnerability
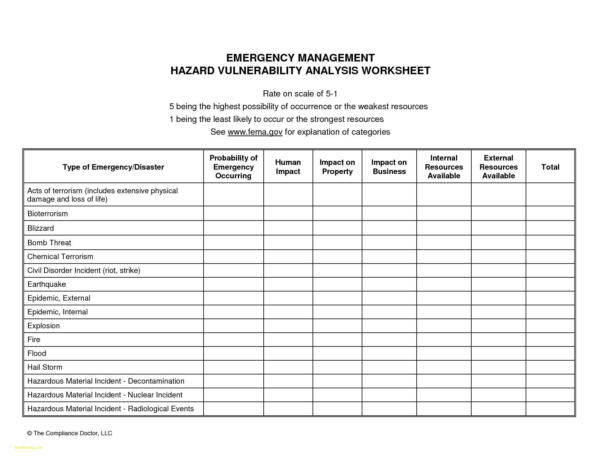
Vulnerability Tracking Spreadsheet inside Vulnerability Tracking
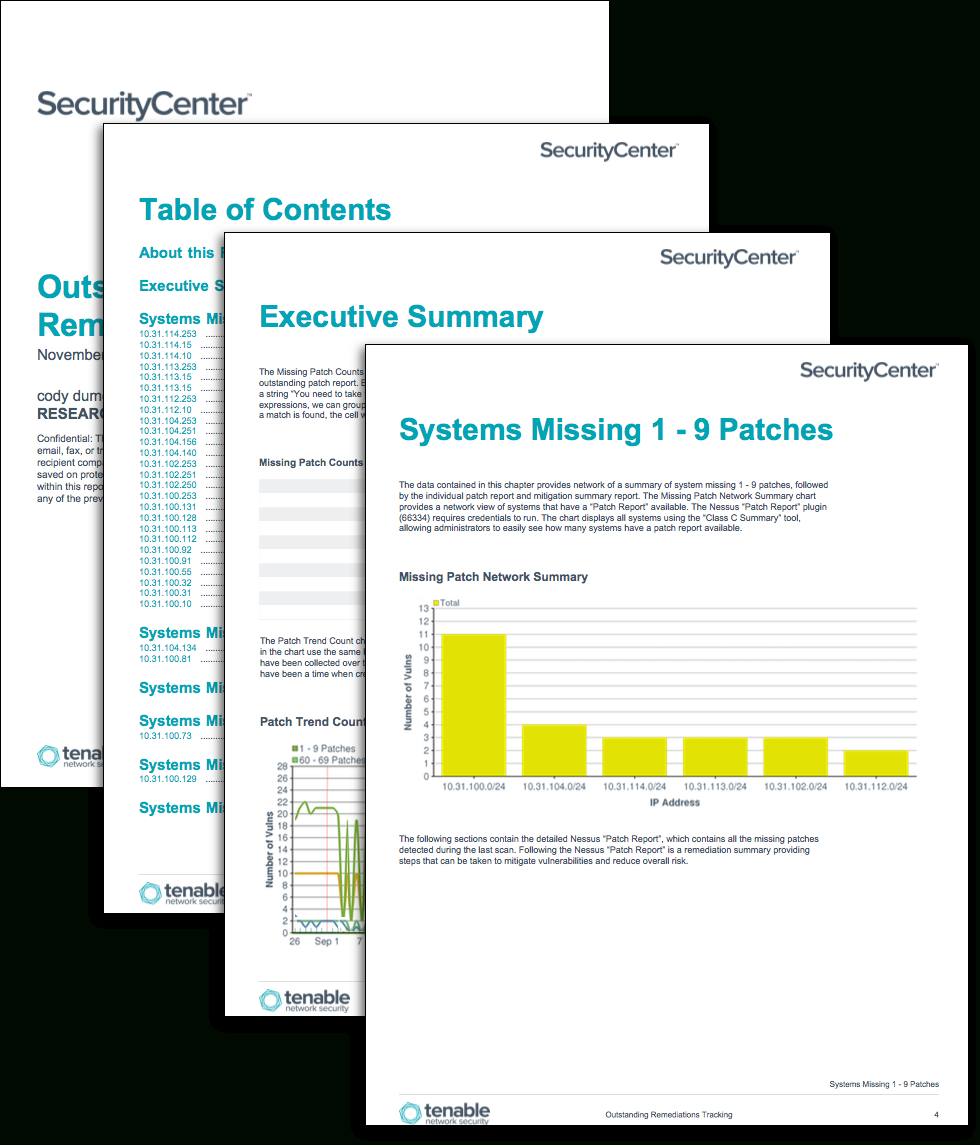
Vulnerability Tracking Spreadsheet in Outstanding Remediations Tracking

Vulnerability Tracking Spreadsheet in Outstanding Remediations Tracking
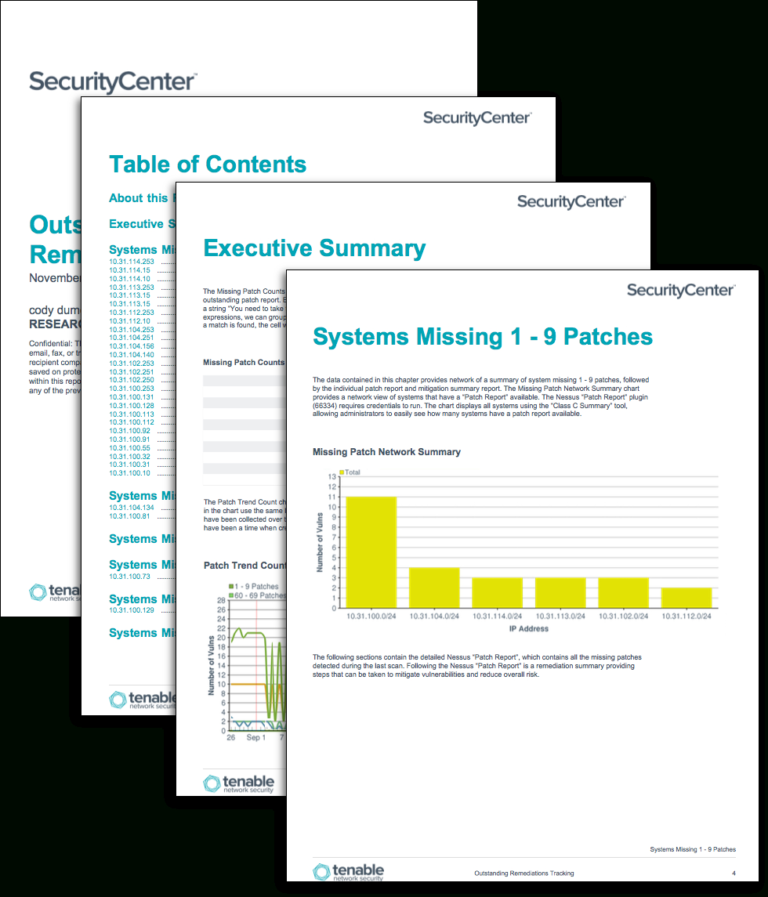
Vulnerability Tracking Spreadsheet in Outstanding Remediations Tracking
Vulnerability Tracking Spreadsheet intended for Vulnerability Tracking
Vulnerability Tracking Spreadsheet intended for Vulnerability Tracking
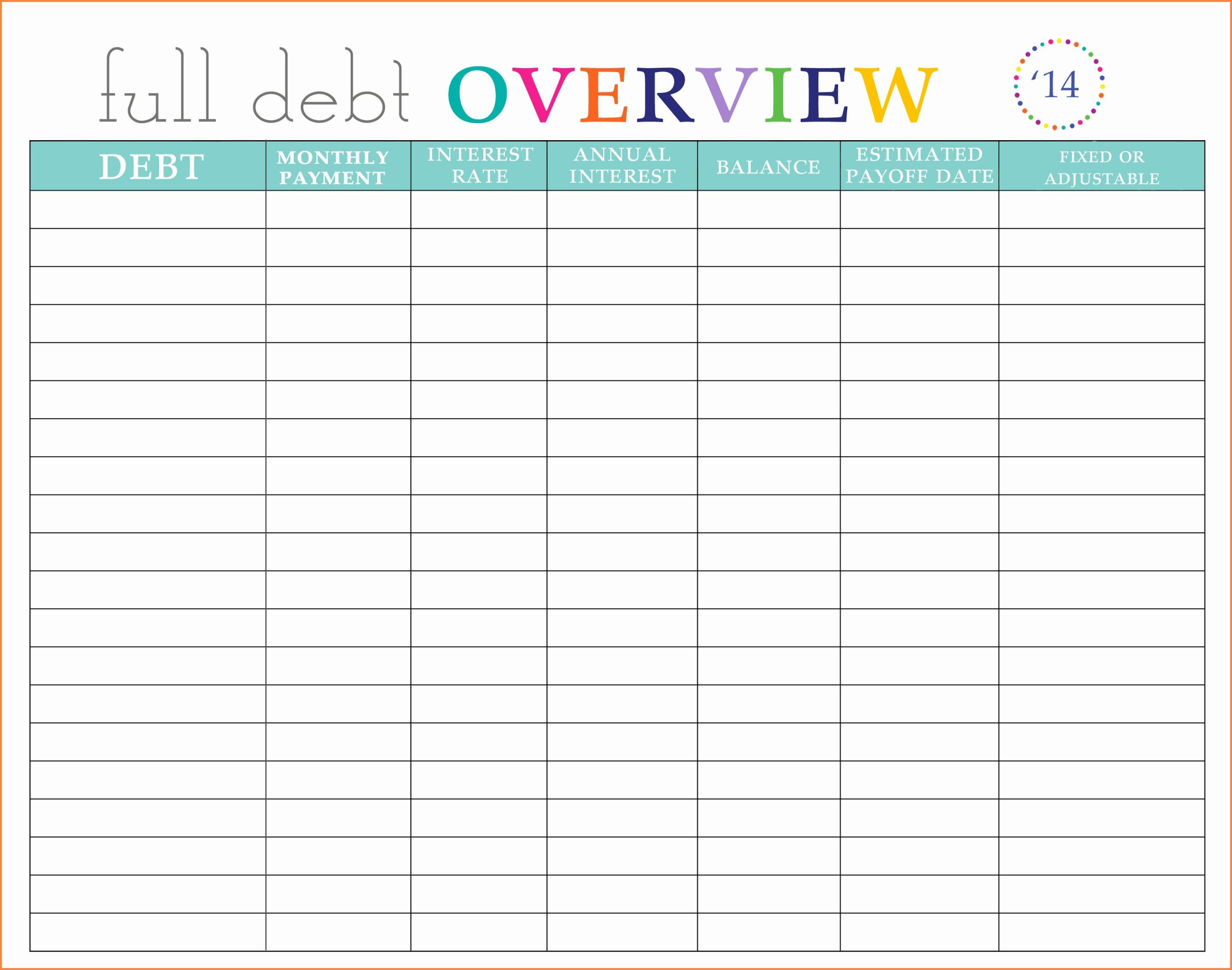
Vulnerability Tracking Spreadsheet for Debt Management Spreadsheet And
Vulnerability Tracking Spreadsheet regarding 11 Awesome Vulnerability

Vulnerability Tracking Spreadsheet with Financial Planning Spreadsheet
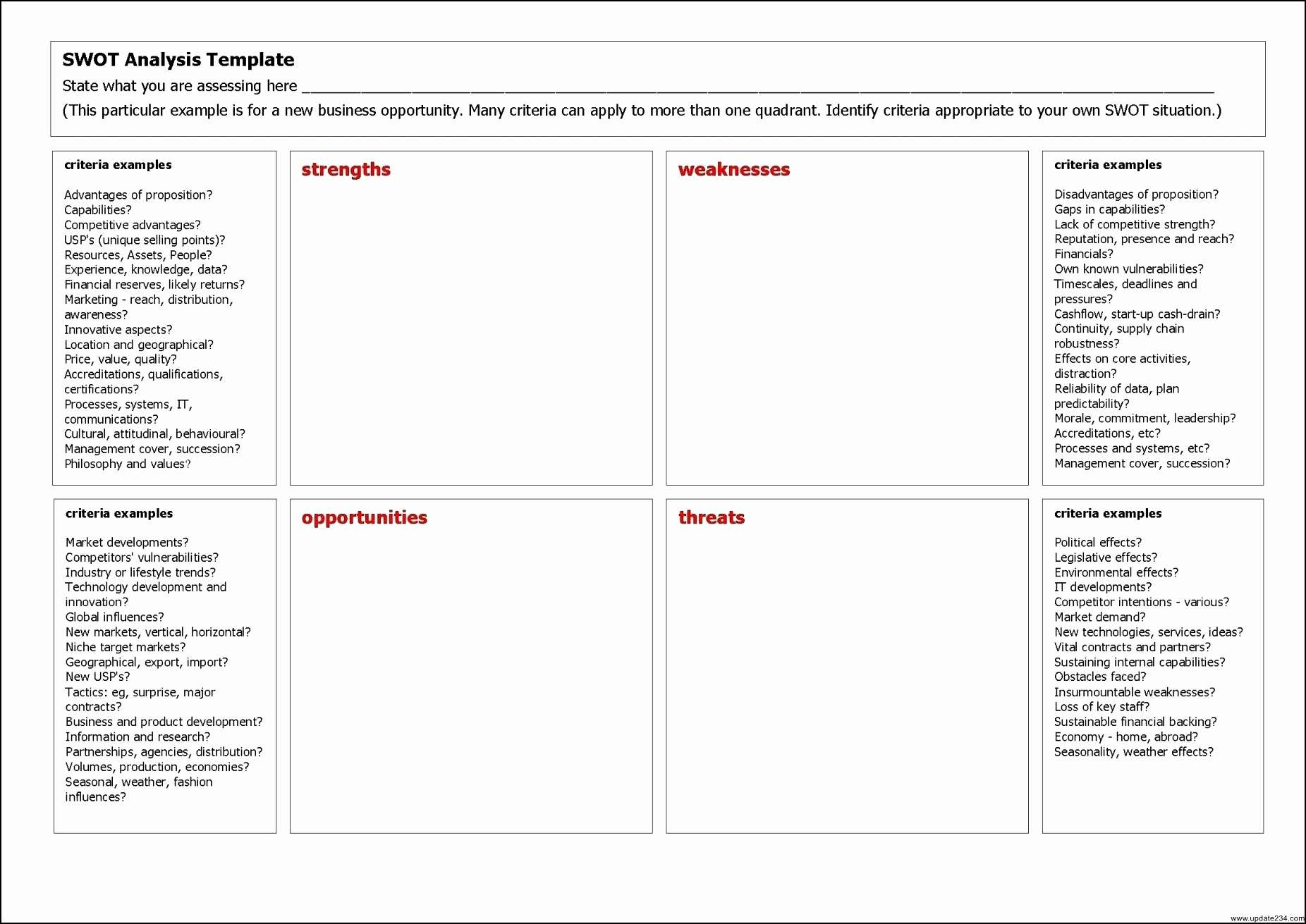
Vulnerability Tracking Spreadsheet with Financial Planning Spreadsheet
Vulnerability Tracking Spreadsheet db excel com
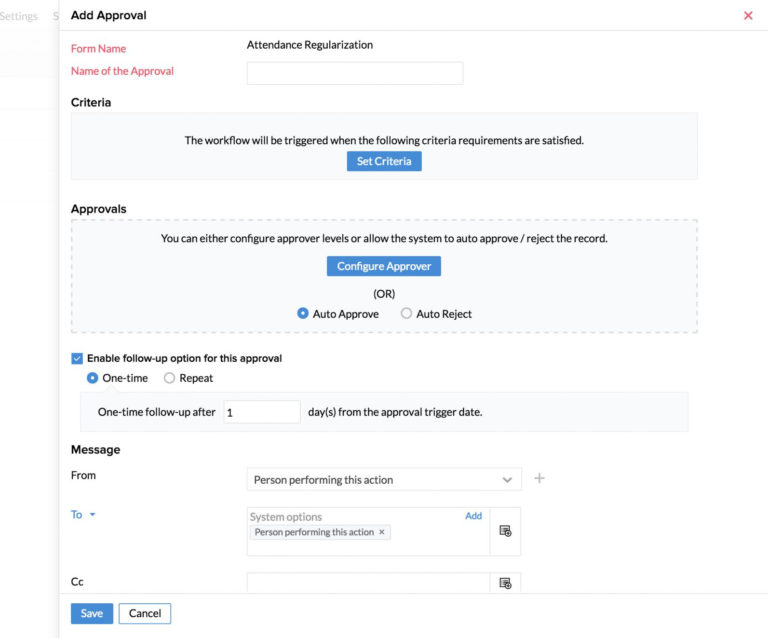
Vulnerability Tracking Spreadsheet db excel com
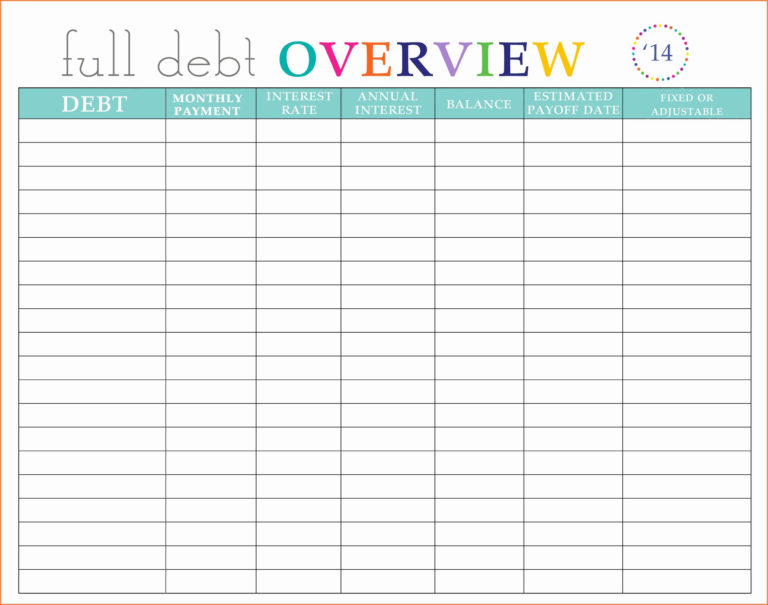
Vulnerability Tracking Spreadsheet db excel com

Vulnerability Tracking Spreadsheet db excel com
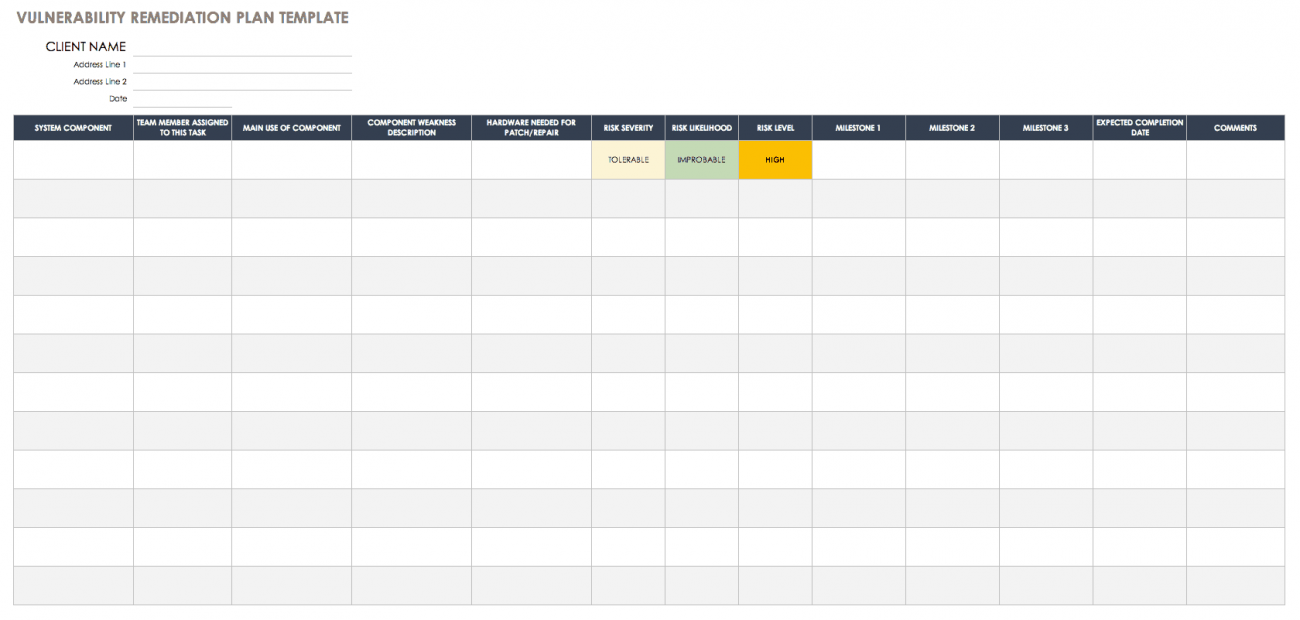
Vulnerability Tracking Spreadsheet db excel com
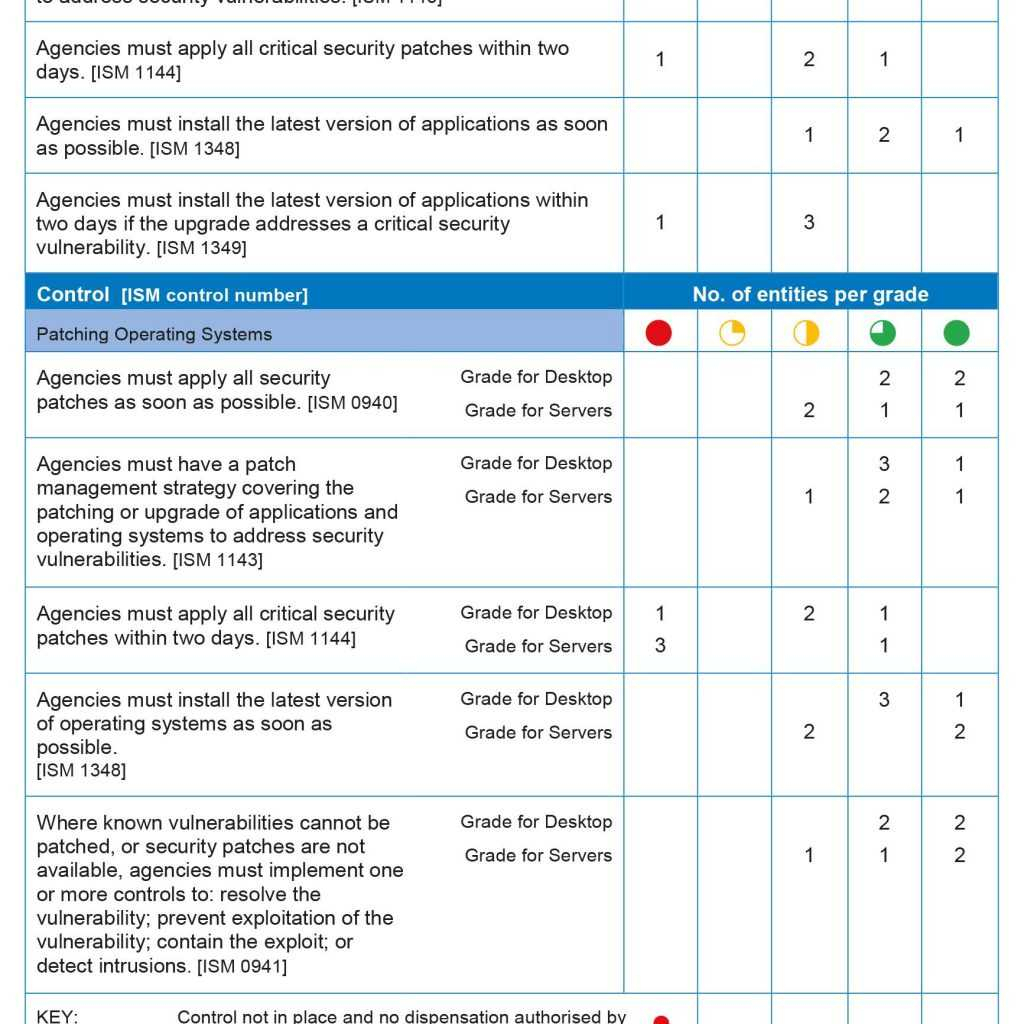
Vulnerability Tracking Spreadsheet db excel com
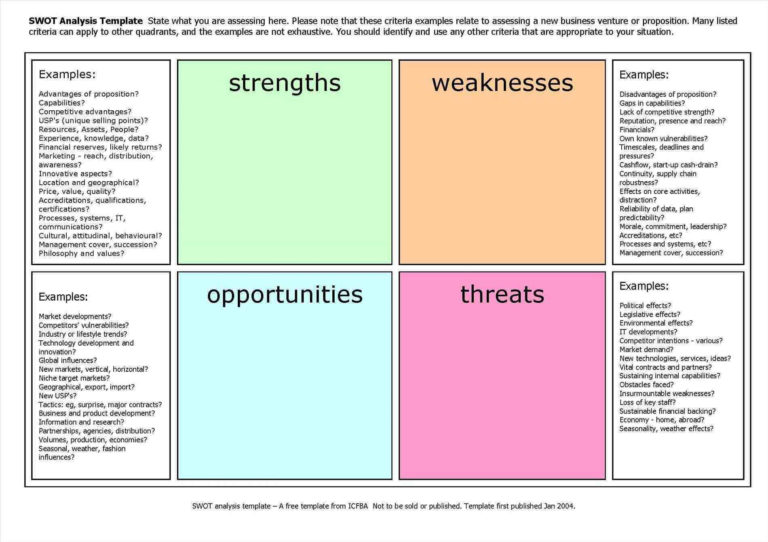
Vulnerability Tracking Spreadsheet Template
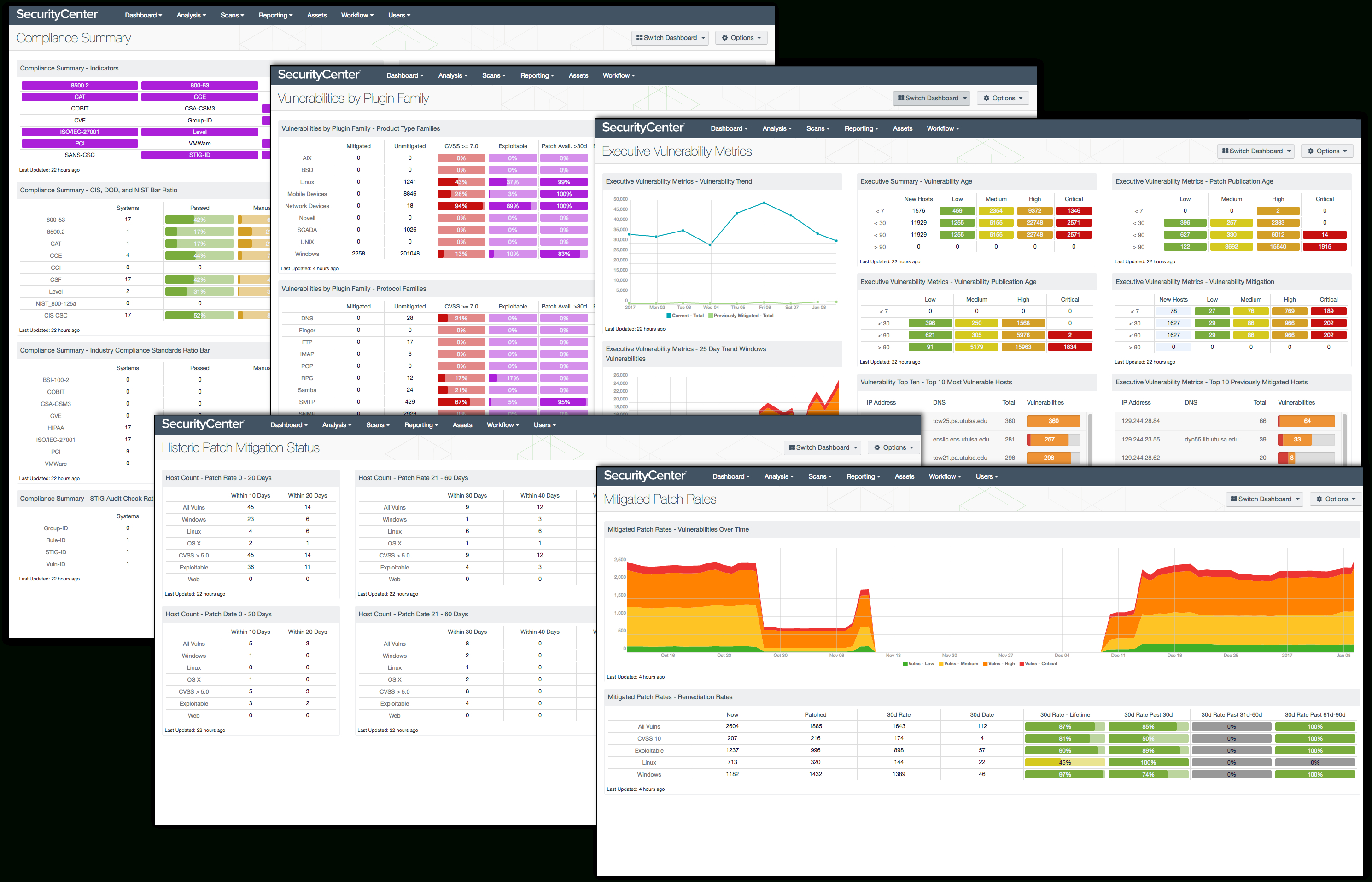
Vulnerability Tracking Spreadsheet Template

Vulnerability Tracking Spreadsheet Template

Vulnerability Tracking Record Sheet Excel Template And Google Sheets

Vulnerability Tracking Record Sheet Excel Template And Google Sheets

Vulnerability Tracking Record Sheet Excel Template And Google Sheets

Vulnerability Tracking Record Sheet Excel Template And Google Sheets
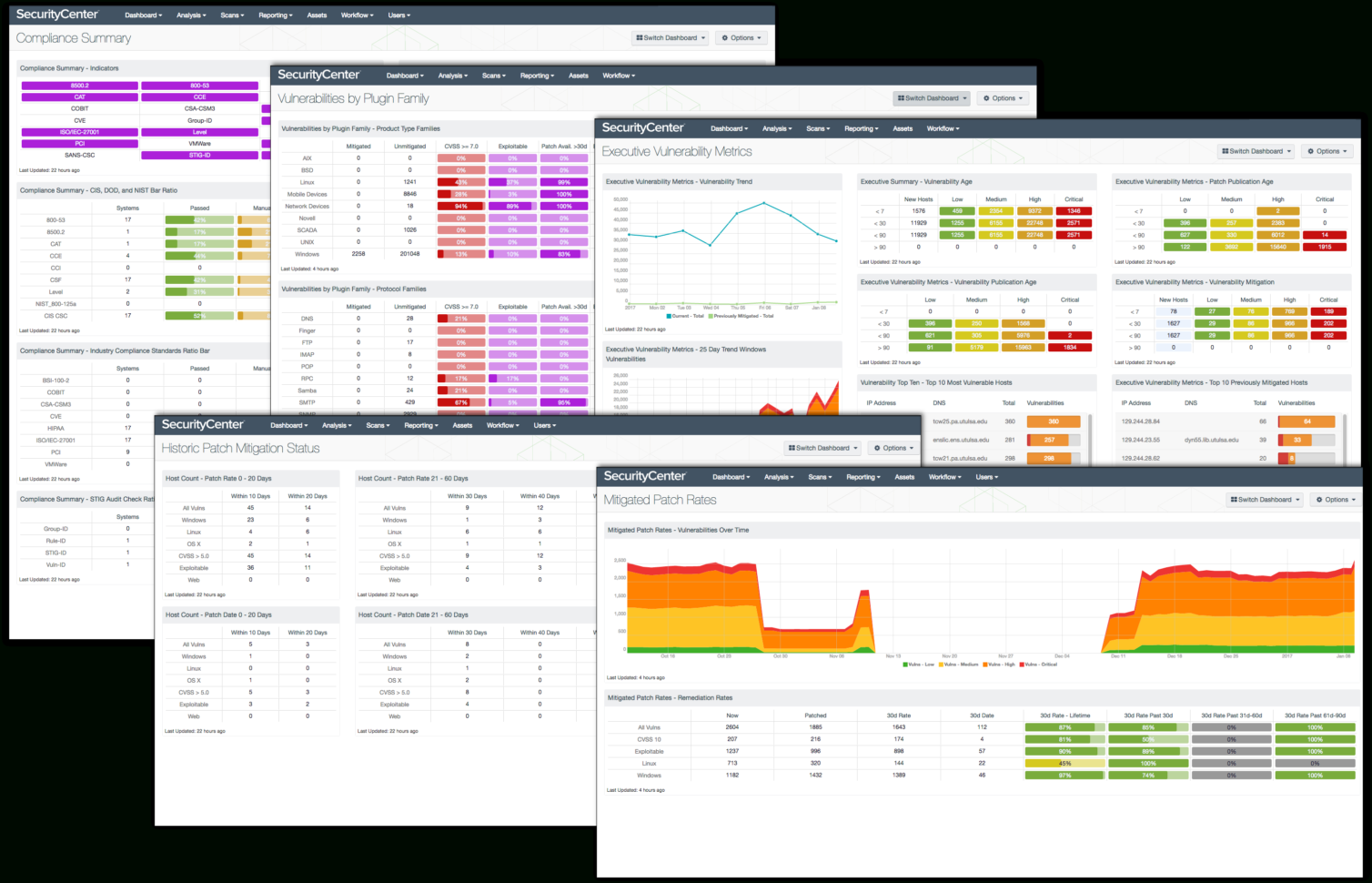
Vulnerability Tracking Spreadsheet for Vulnerability Management Metrics

Vulnerability Tracking Spreadsheet db excel com

Vulnerability Tracking Spreadsheet db excel com
Vulnerability Tracking Spreadsheet Awal Mula with Incident Tracking
Vulnerability Tracking Spreadsheet Spreadsheet Downloa vulnerability
Vulnerability Tracking Spreadsheet pertaining to Excel Spreadsheet
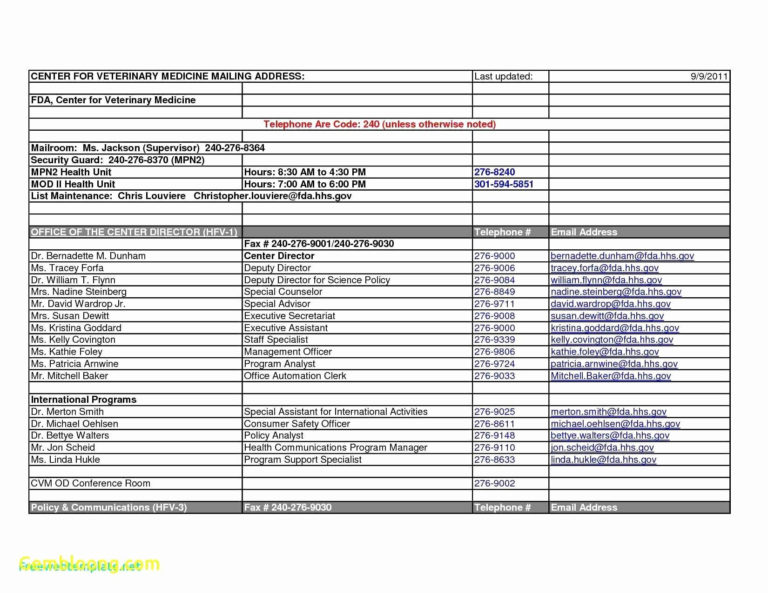
Vulnerability Tracking Spreadsheet intended for Security Report Example
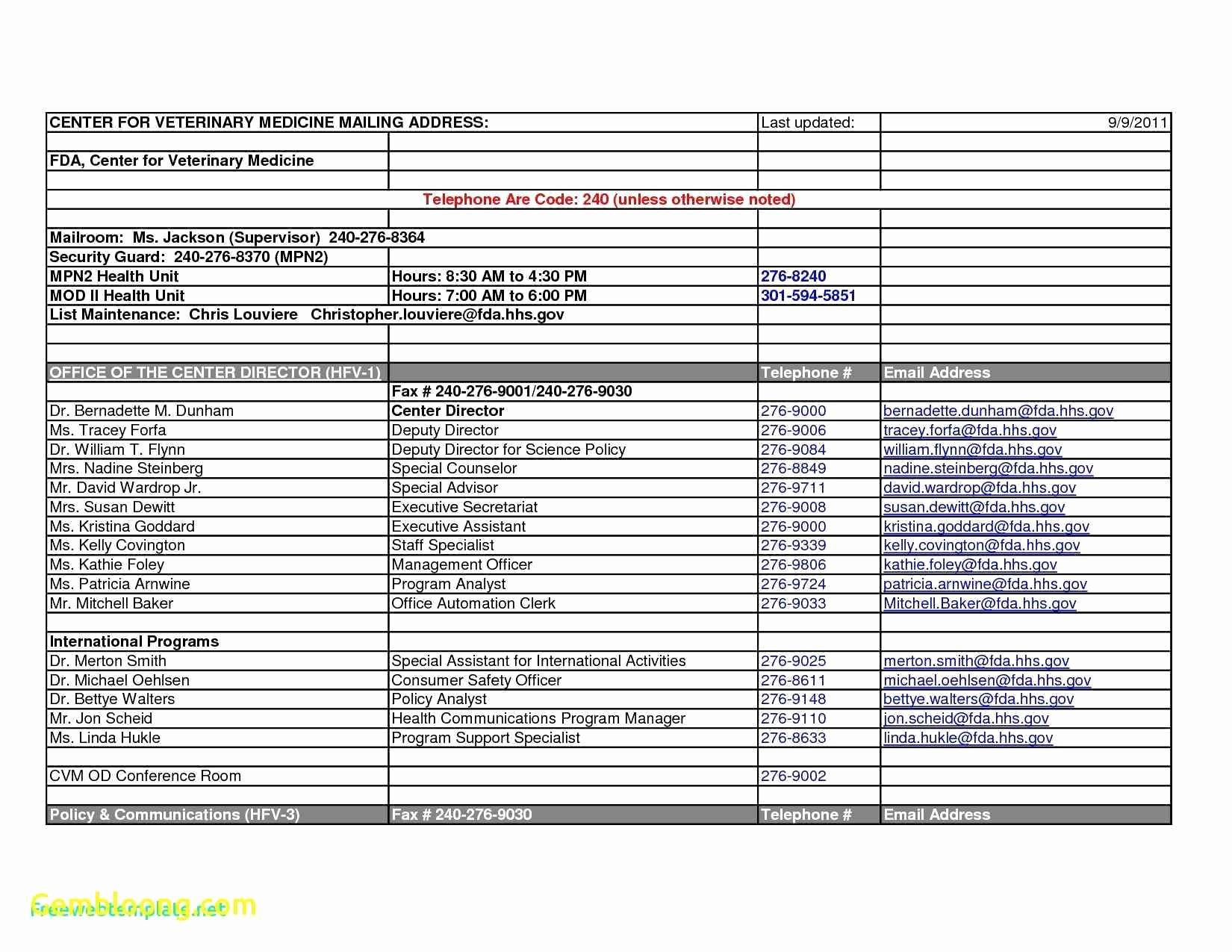
Vulnerability Tracking Spreadsheet intended for Security Report Example
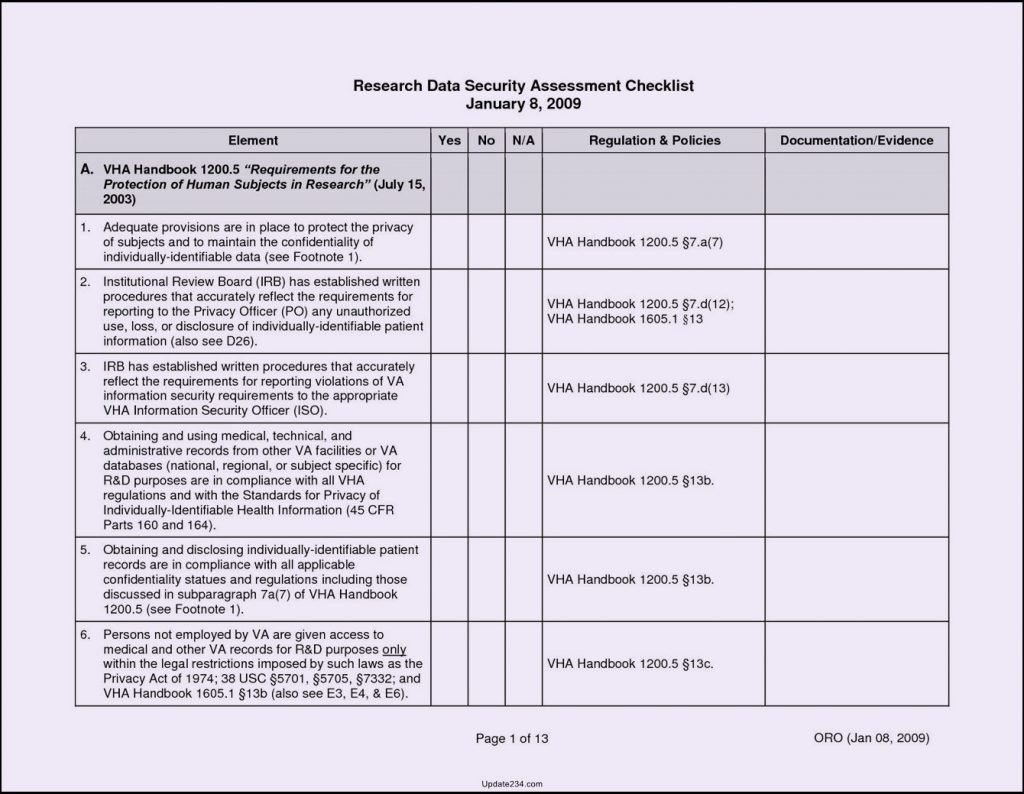
Vulnerability Assessment Report Template
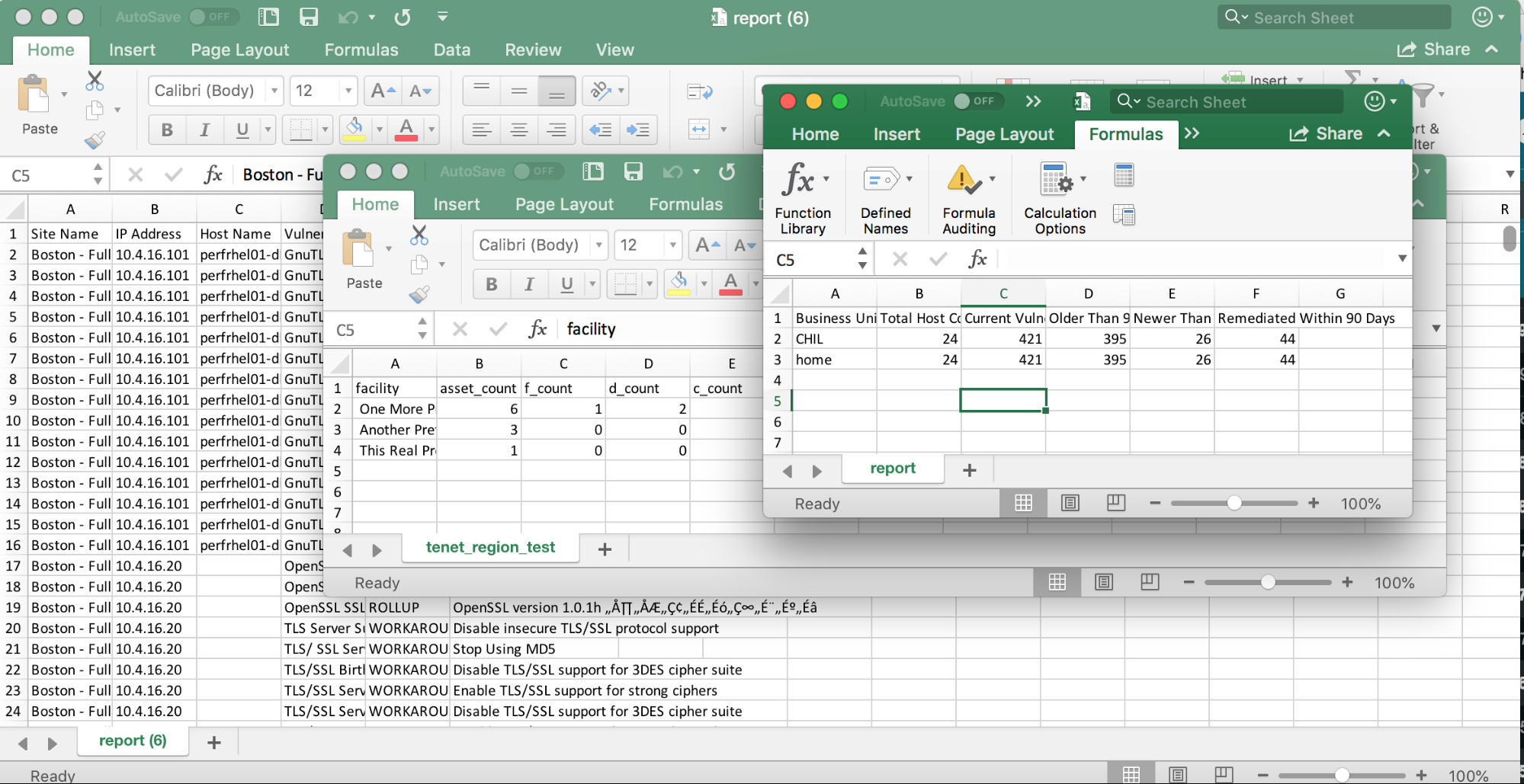
Patch Management Tracking Spreadsheet inside Streamlining Vulnerability

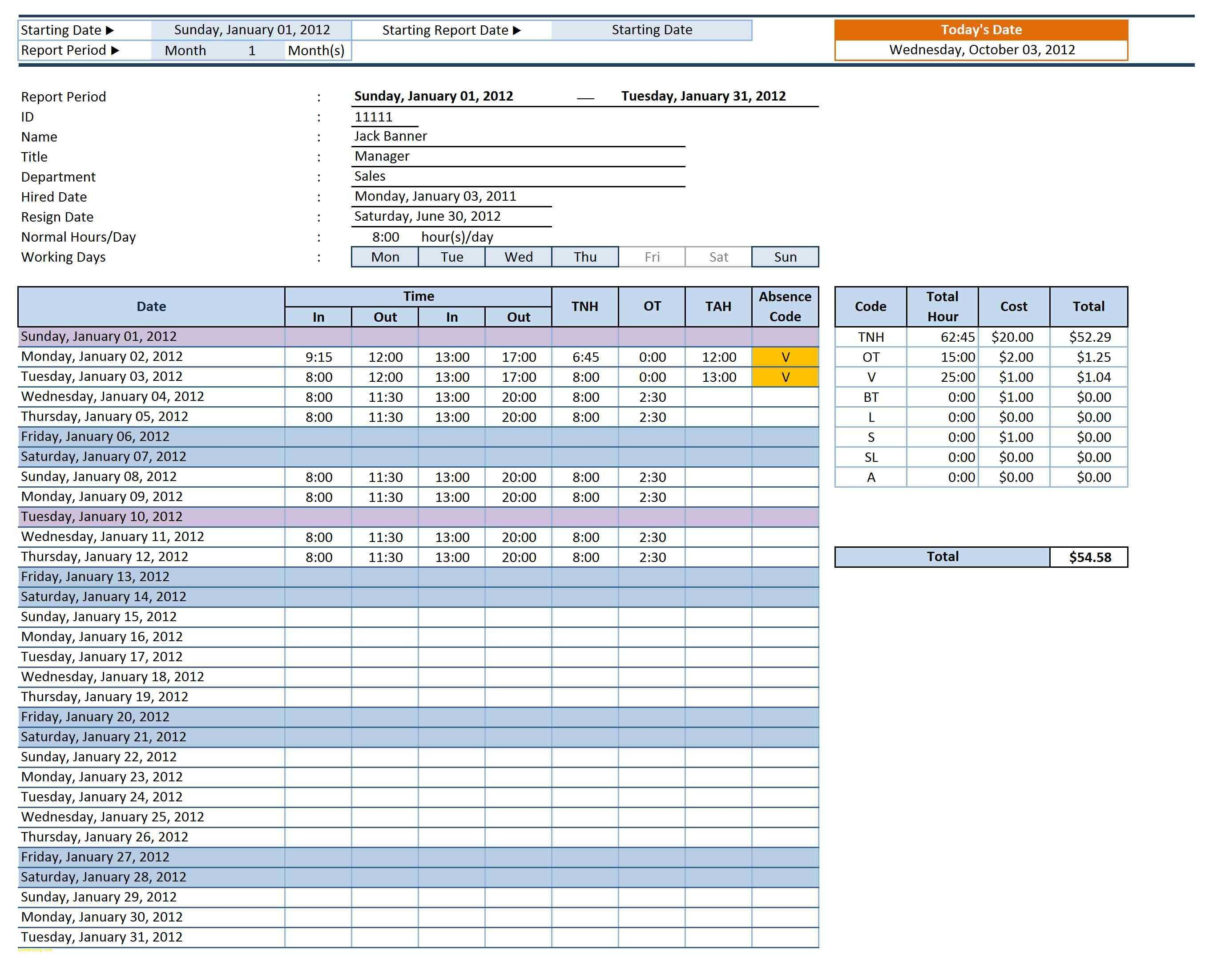
Fmla Leave Tracking Spreadsheet Template Excel Printable Word Searches

Vulnerability Management Tracking Spreadsheet Template ISO 42001 AIMS
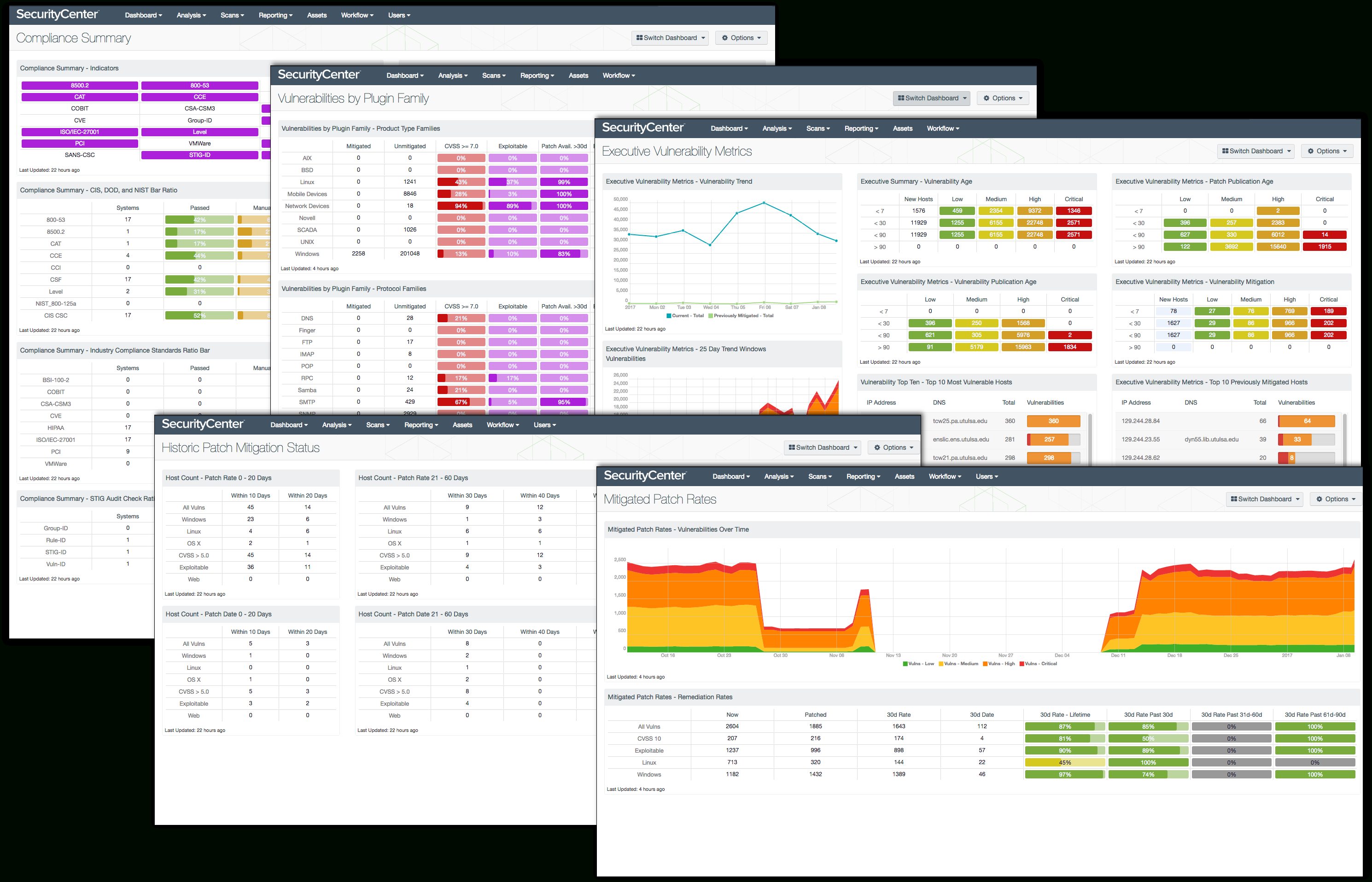
Patch Management Tracking Spreadsheet db excel com

Vulnerability Management Tracking Spreadsheet Template ISO 42001 AIMS

Vulnerability Management Report Template
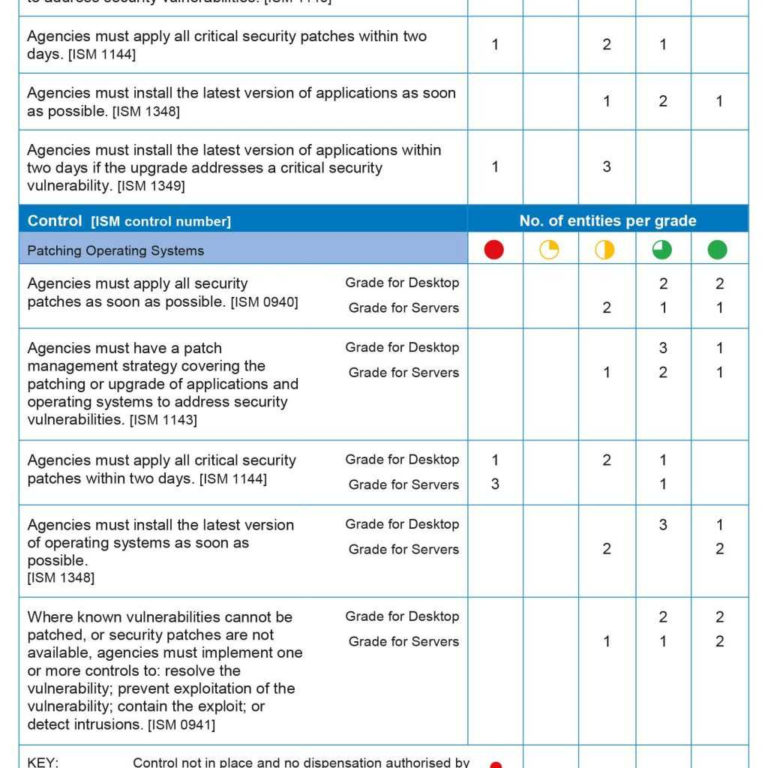
Patch Management Spreadsheet within Network Vulnerability Assessment
Vulnerability Assessment Report Template prntbl
Vulnerability Assessment Report Template prntbl
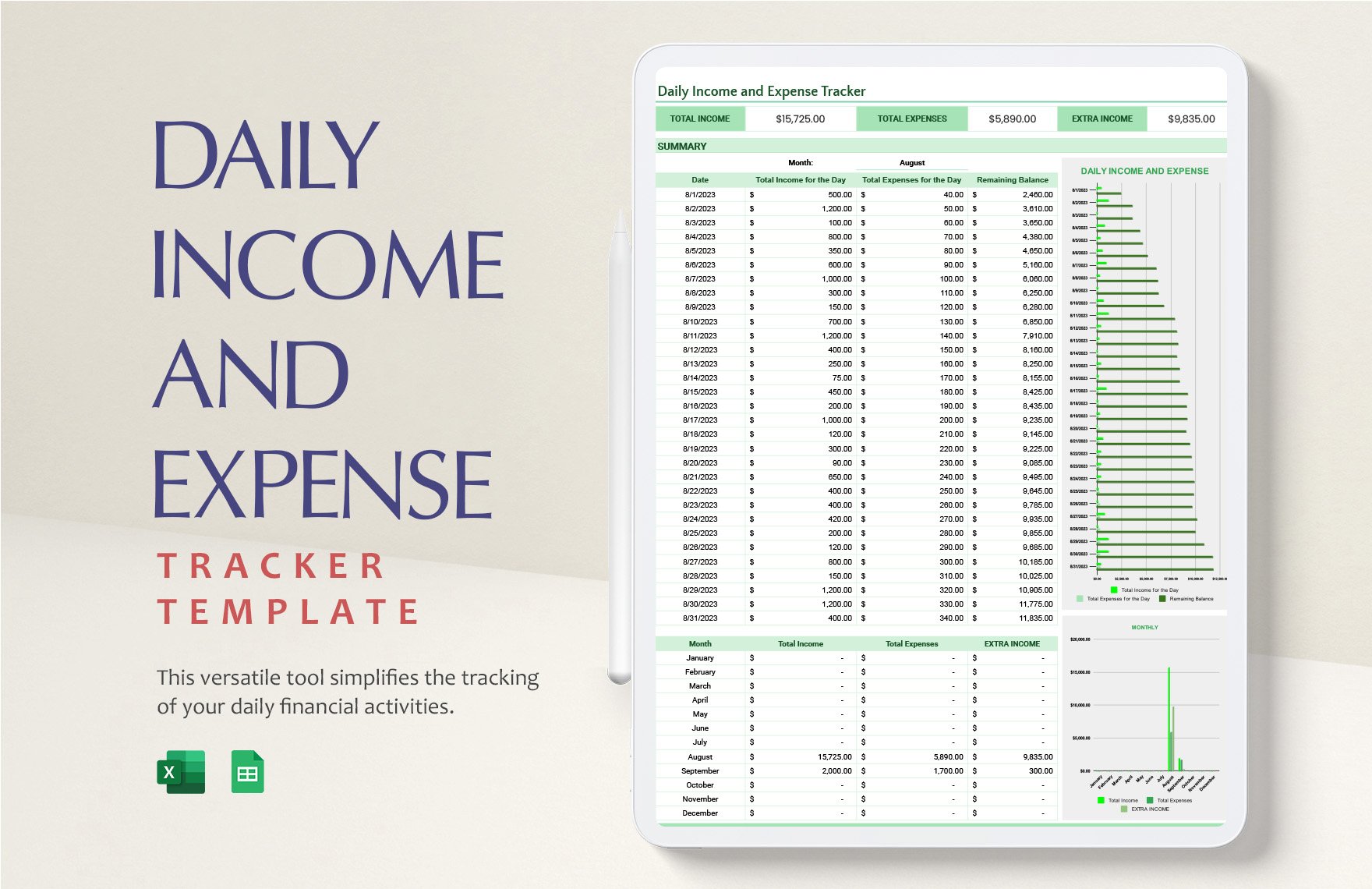
Editable Revenue Templates in Excel to Download
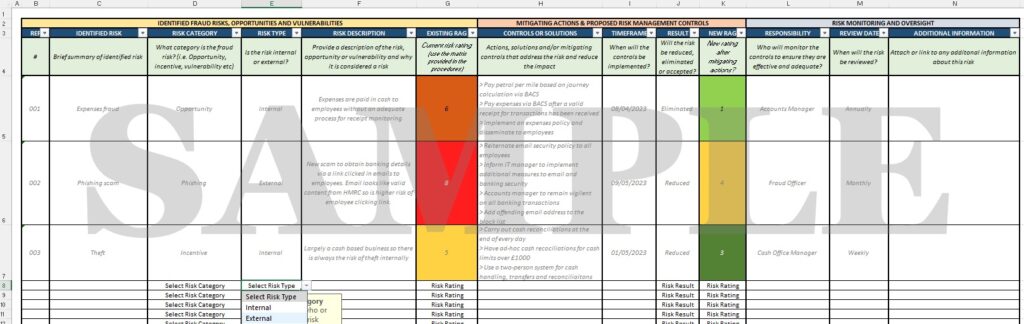
Food Fraud Vulnerability Assessment Template
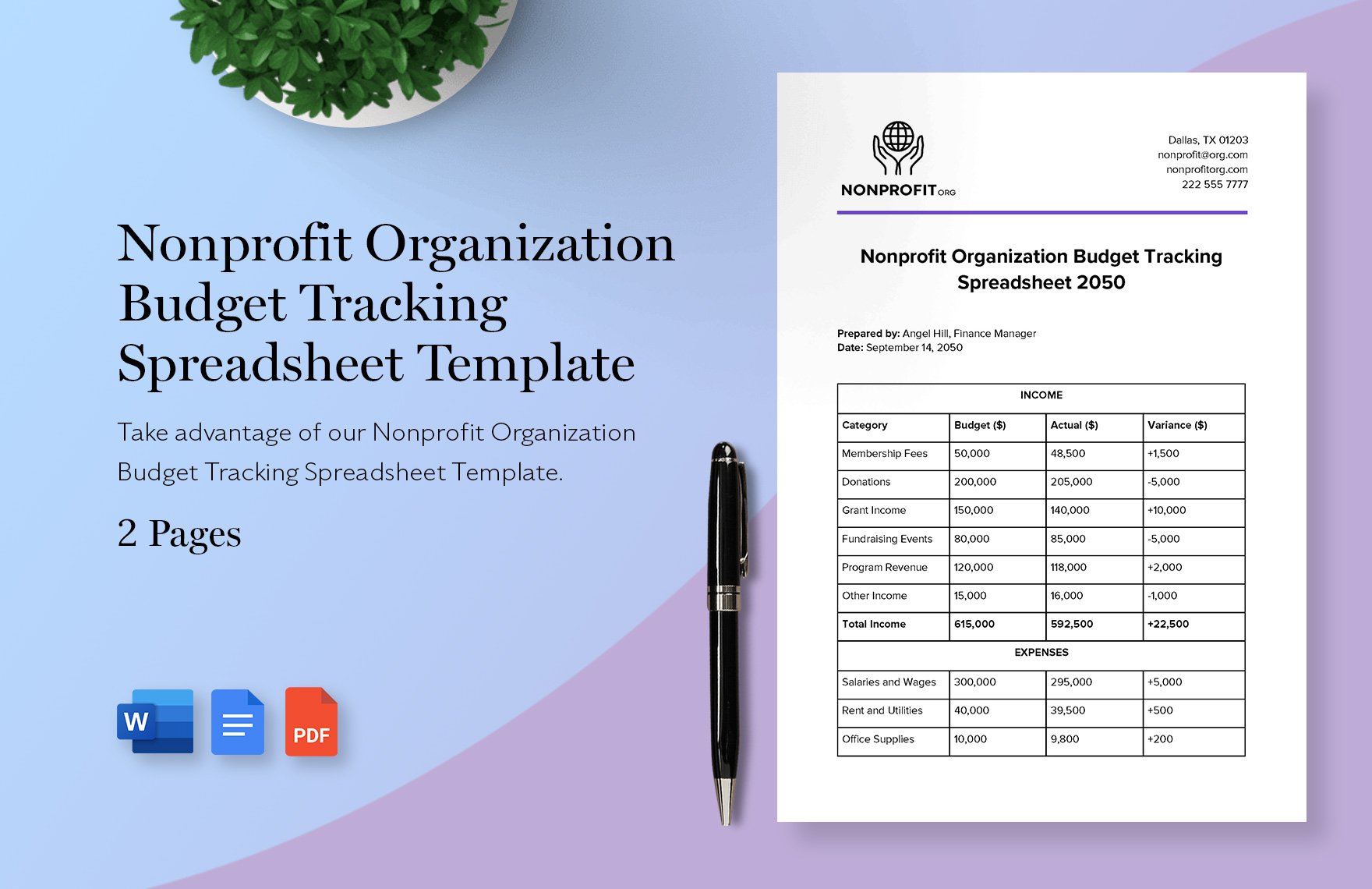
Production Cost Template in Excel Google Sheets Download Template net
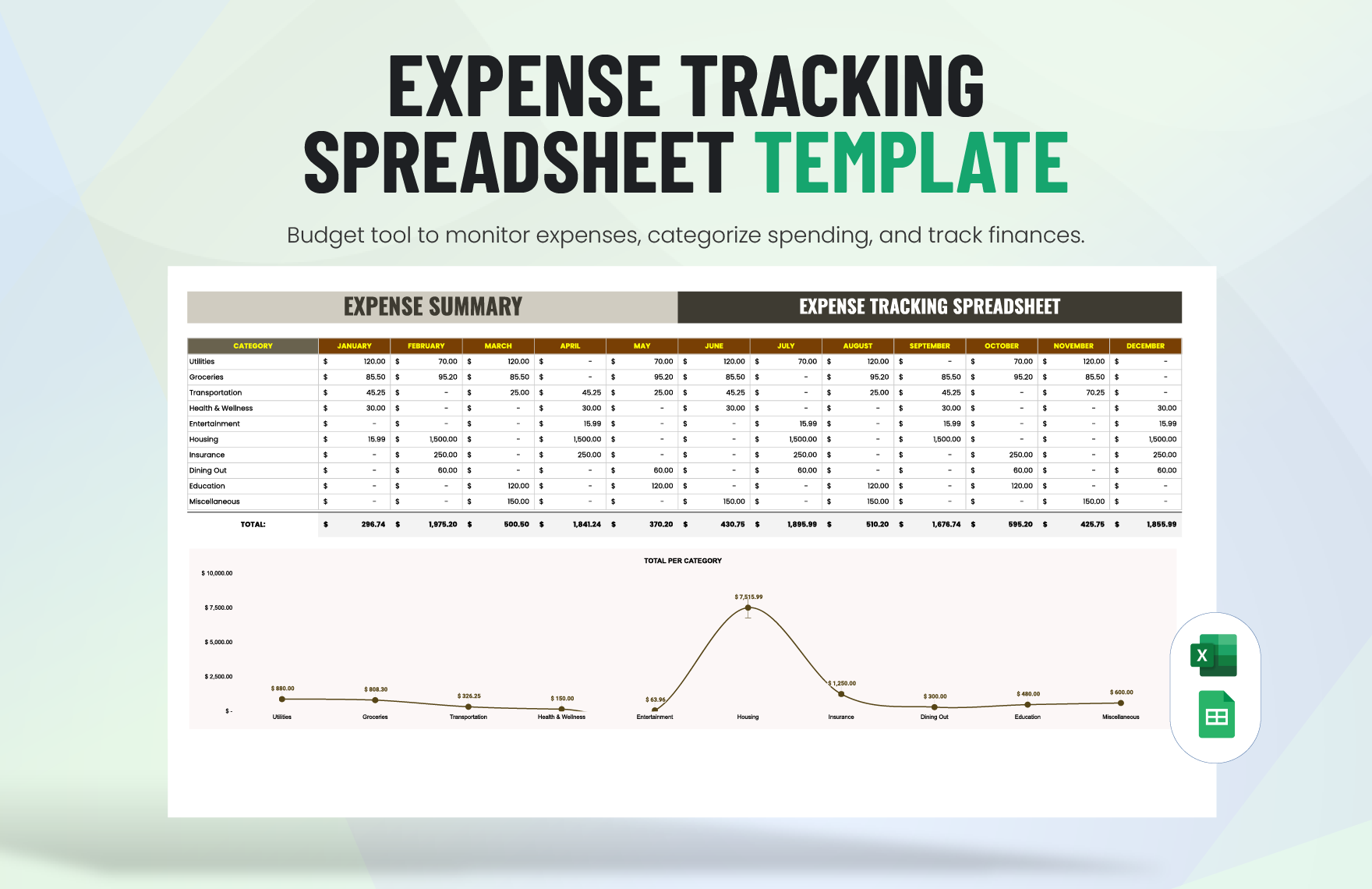
Production Cost Template in Excel Google Sheets Download Template net

Task Management Template For Excel (2021) 54% OFF
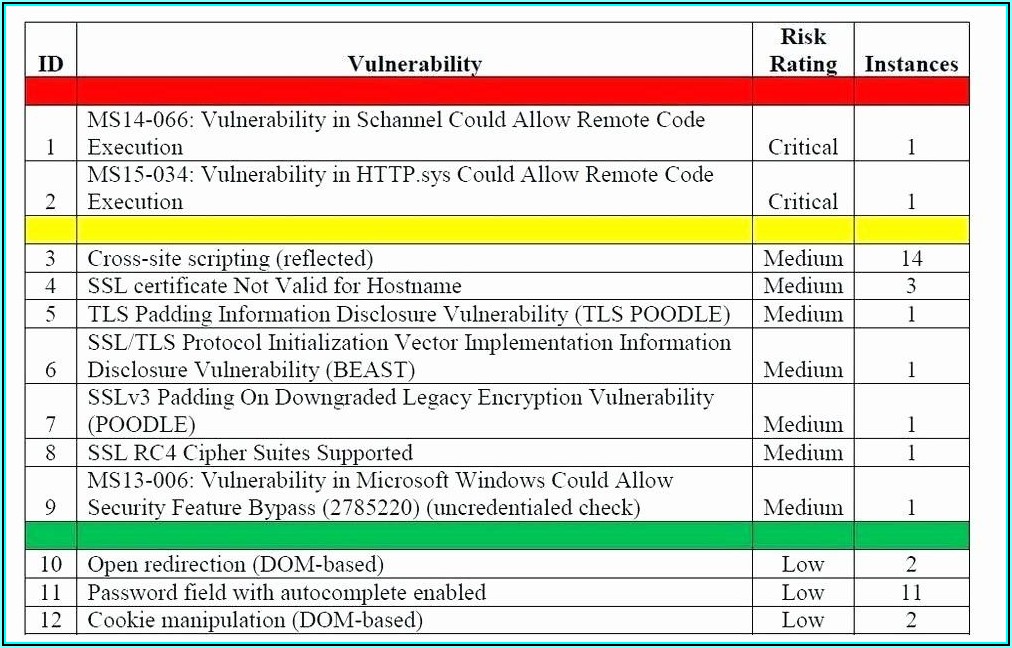
Vulnerability Assessment AndTesting Plan Templates
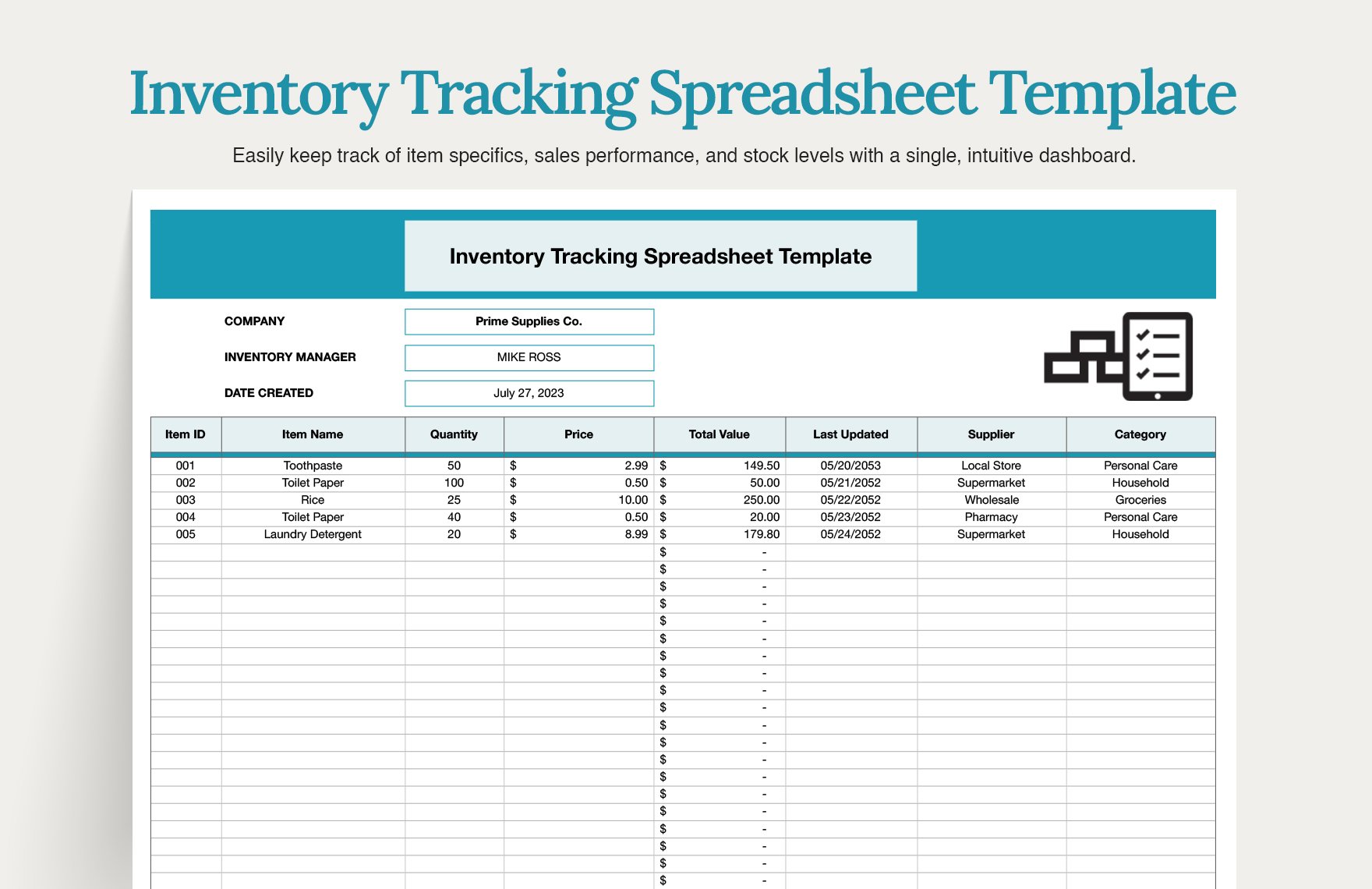
Inventory Tracking Template Excel
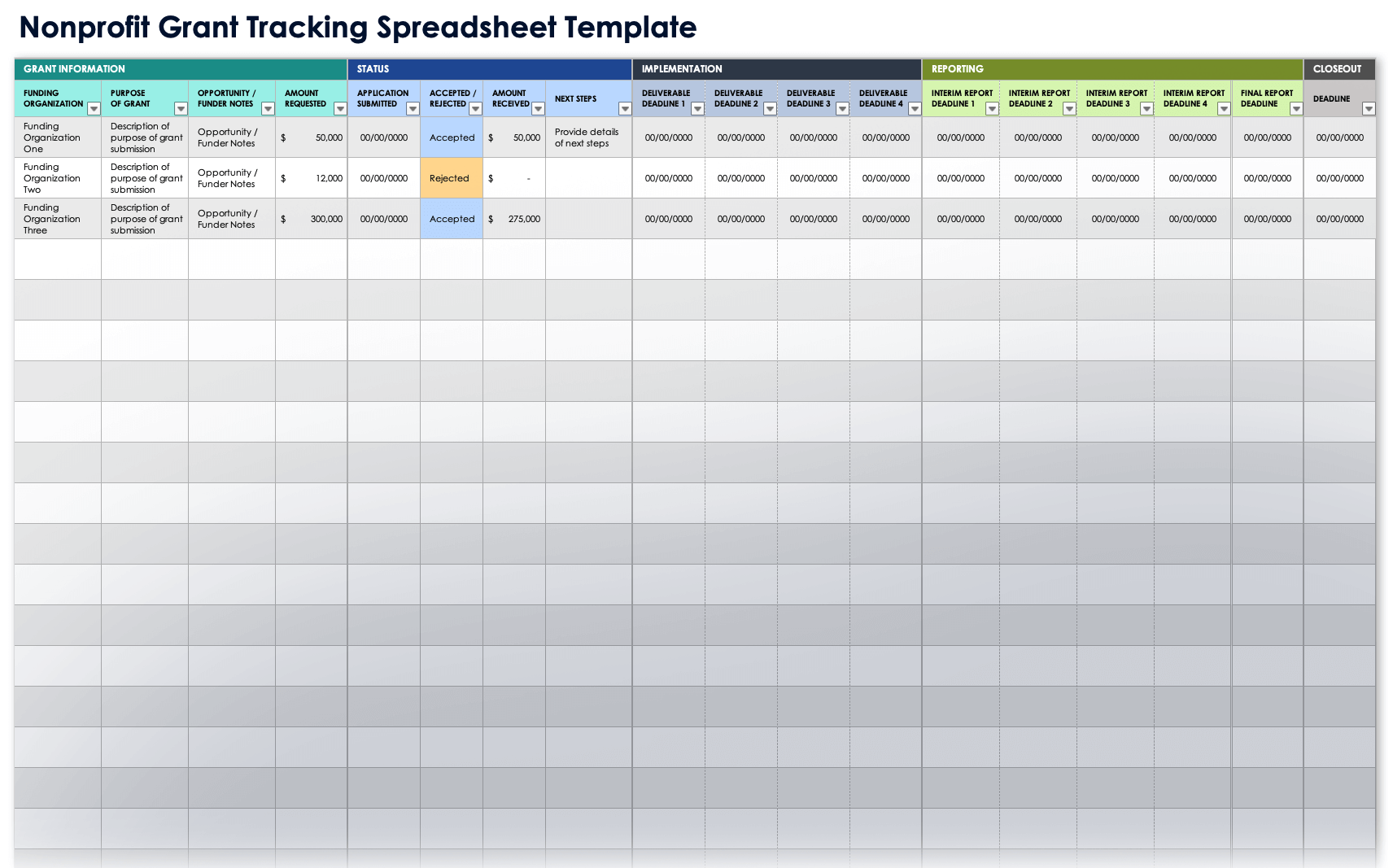
Free Grant Tracking Grant Management Templates
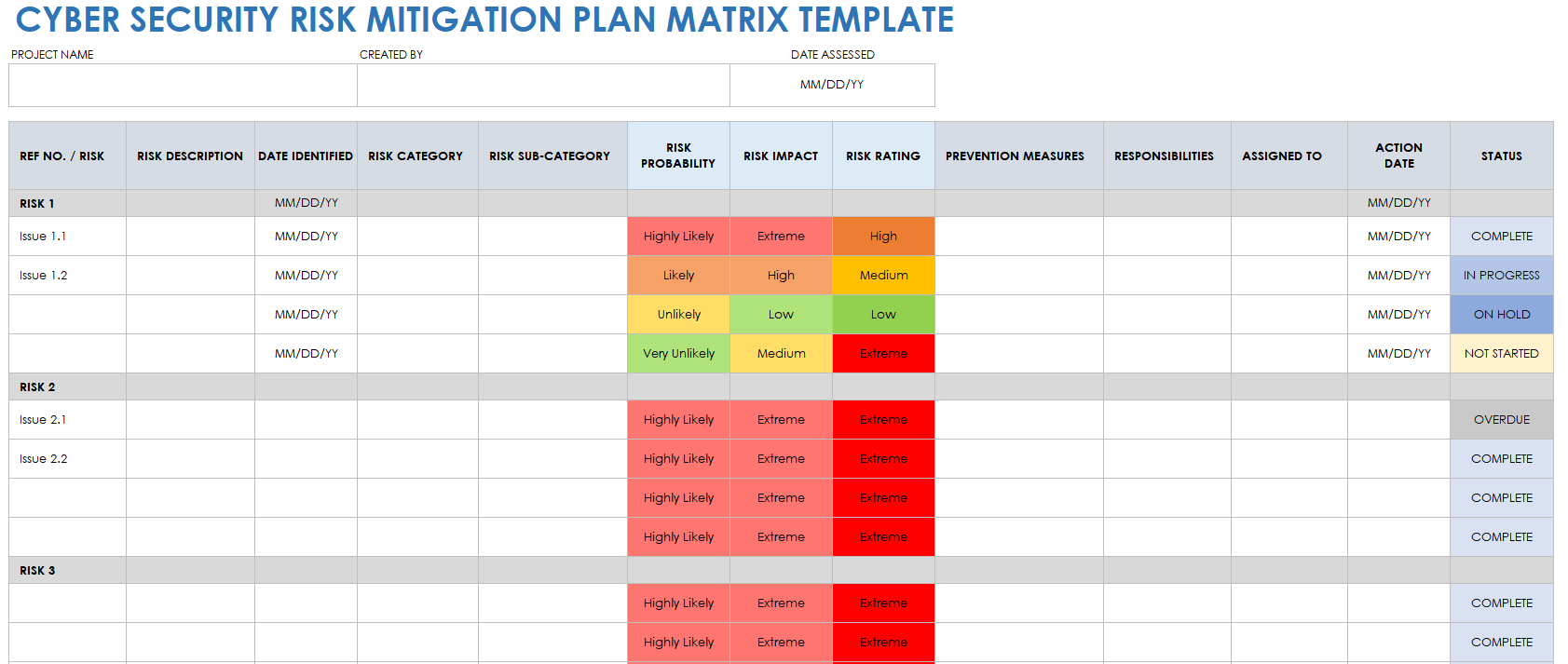
Developmental Test Plan Template
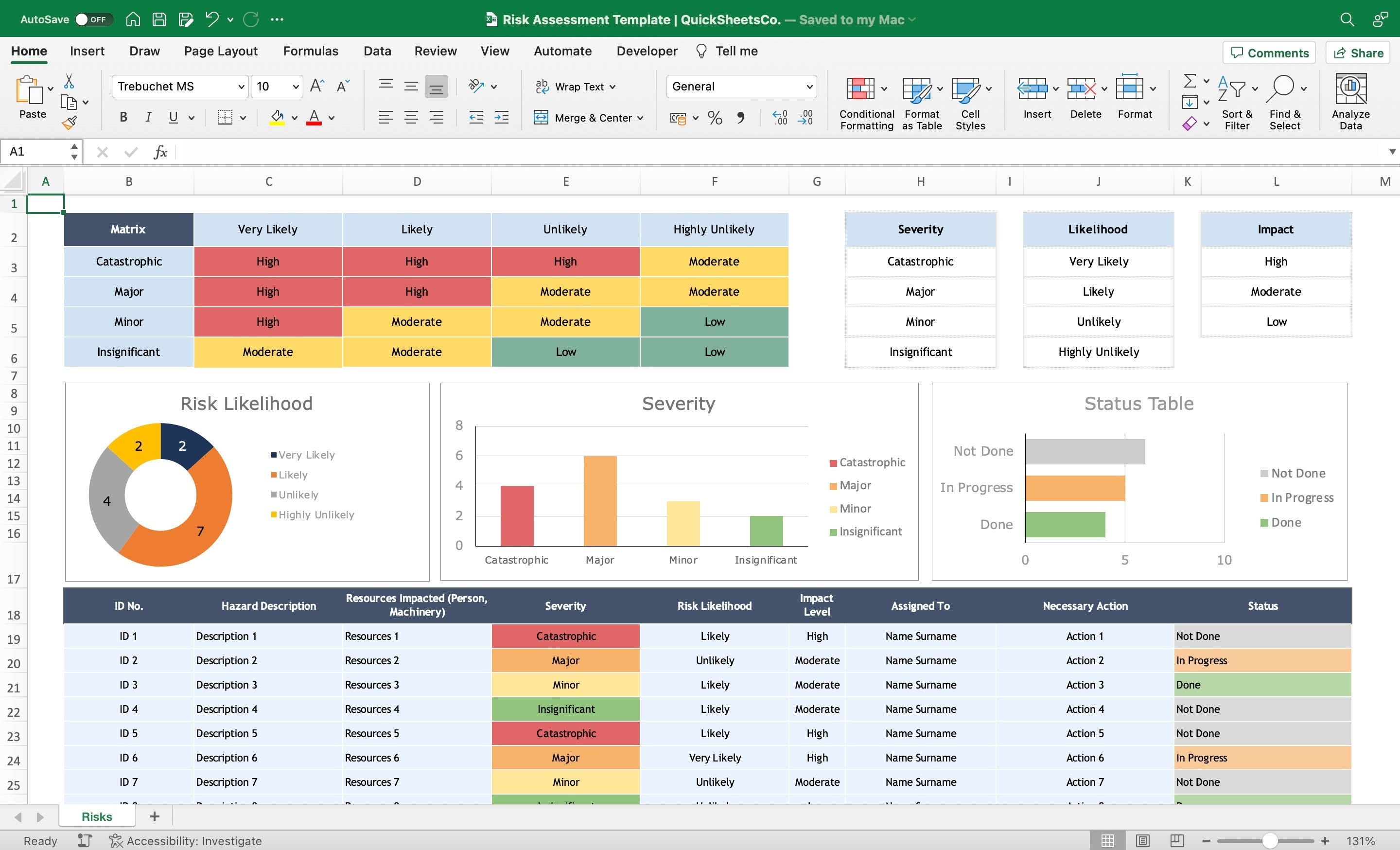
Risk Assessment Excel Template Business Spreadsheet Risk Management

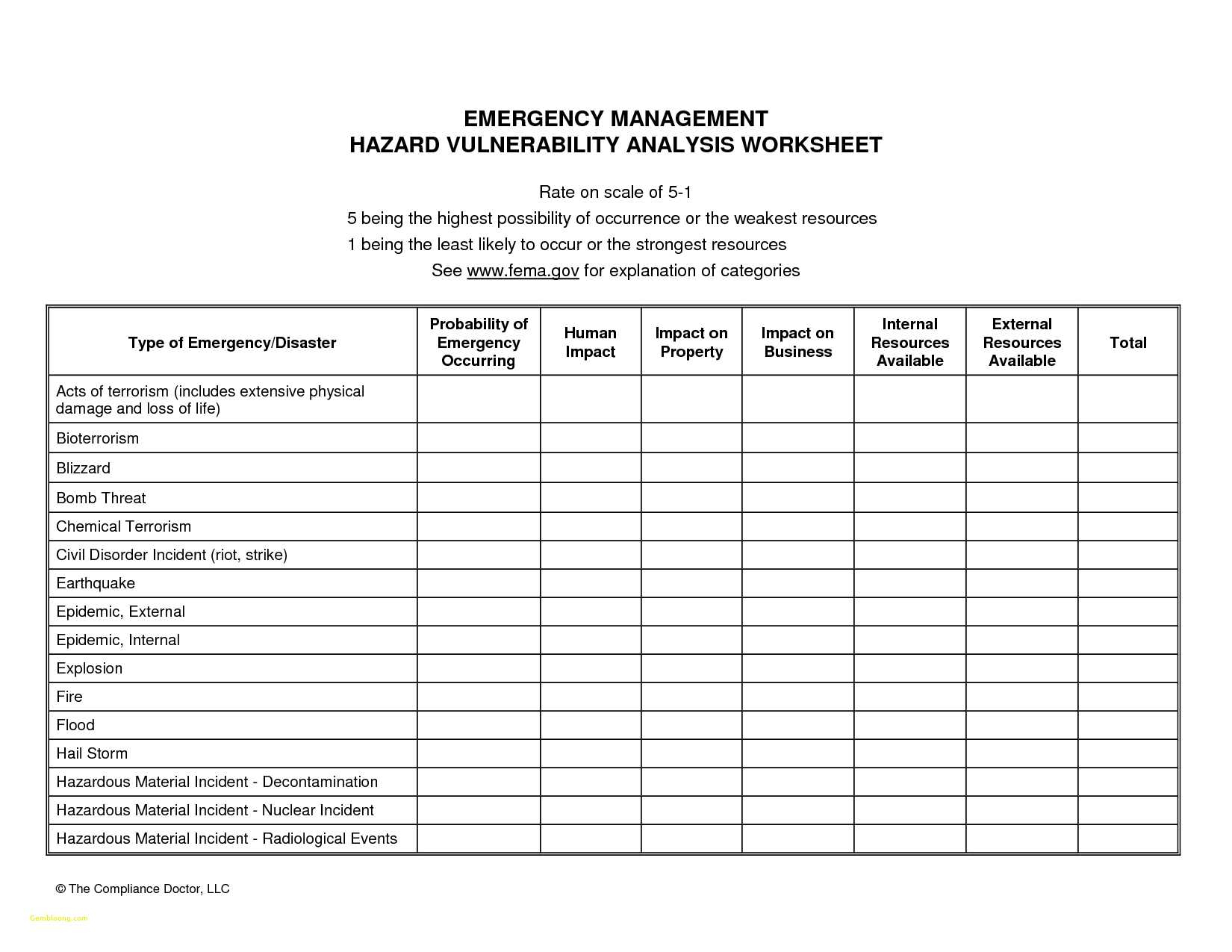
What Type of Tool is the Hazard Vulnerability Analysis?

Printable Nfr Back Number Template

Threat Analysis And Risk Assessment Template prntbl
PLC Data Spreadsheet and Tracker for Data Discussions Instructional

Dashboard Templates: HR KPI Dashboard 57% OFF
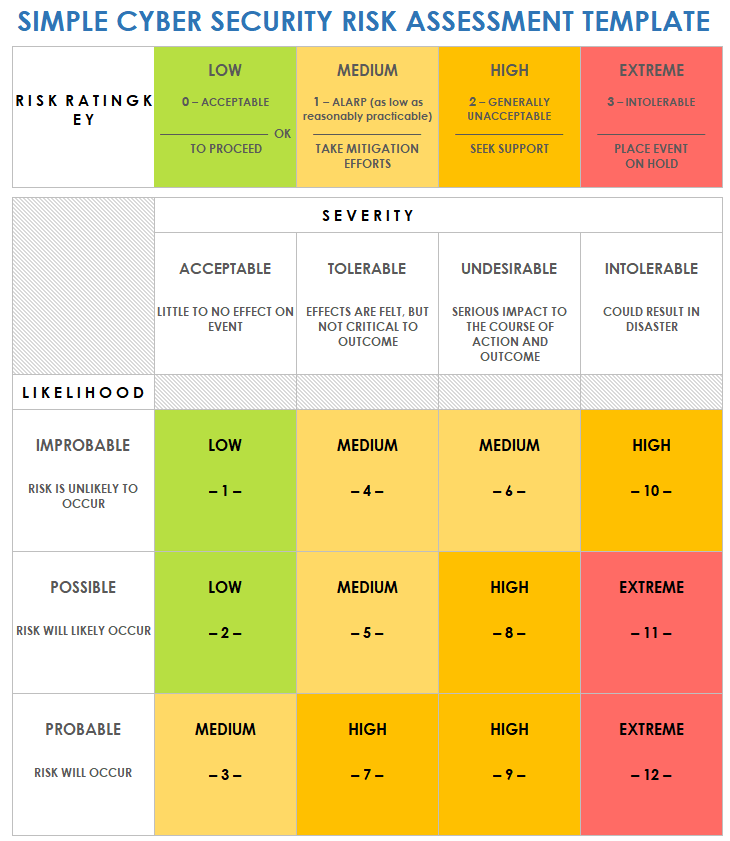
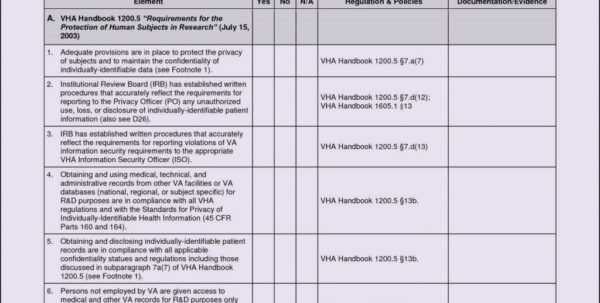
Free Cybersecurity Risk Assessment Templates Smartsheet

Information Systems Risk Assessment at Joanna Martin blog